- Cisco Community
- Technology and Support
- Security
- Security Analytics
- Re: Stealthwatch TACACS
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-08-2019 08:21 AM
I would like to use TACACS for logging into Stealthwatch's webUI. Per the user guide, I added ISE servers as authentication servers in the Stealthwatch Management Console. Also, I added the Stealthwatch server as a network device into ISE and configured a minimal policy set. After several login attempts, I never see the authentications hit the ISE TACACS logs. I tested against another non-ISE TACACS server to be sure it wasn't an ISE issue and do not see the authentication there, either. It seems as though Stealthwatch needs additional config to tell it to use the TACACS servers that were specified. Is there some other configuration required in Stealthwatch that tells it to do so?
Solved! Go to Solution.
- Labels:
-
Stealthwatch
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-09-2019 07:39 AM
When you add ISE servers in the SMC console web UI, that is for using ISE as an identity source (i.e. mapping flows' IP addresses to users).
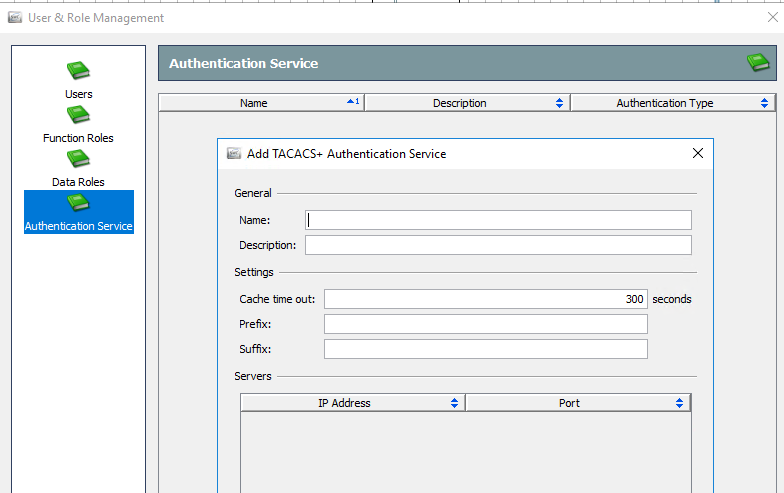
To use ISE as your TACACS (or RADIUS) authentication server, you need to do it from the Swing client (the Java desktop applet). Select your SW domain and then Configuration > Users and Role Management. Select the Authentication Service icon and then add your TACACS server there. Once successfully added, create a user in Stealthwatch and tell Stealthwatch to use this newly added Authentication service for that user.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-09-2019 07:39 AM
When you add ISE servers in the SMC console web UI, that is for using ISE as an identity source (i.e. mapping flows' IP addresses to users).
To use ISE as your TACACS (or RADIUS) authentication server, you need to do it from the Swing client (the Java desktop applet). Select your SW domain and then Configuration > Users and Role Management. Select the Authentication Service icon and then add your TACACS server there. Once successfully added, create a user in Stealthwatch and tell Stealthwatch to use this newly added Authentication service for that user.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-09-2019 07:56 AM - edited 07-10-2019 05:08 AM
Thanks Martin! I apologize as my post wasn't very clear. I added the ISE servers under the Authentication Service, as pictured in you screenshot, but I did not add the user in the Stealthwatch WebUI, which was the missing piece of information. I just added the TACACS user in the WebUI, told it to use the ISE servers from the Authentication Service for this user, and now TACACS works. Thanks for the helpful advice!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-09-2019 07:44 PM
You're welcome. I'm glad it helped.
That actual process is very sparsely documented in the SW configuration guide. I had to dig deep for it, so I learned something myself in the process.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-10-2019 05:19 AM
It would be great if the second step of adding the user manually to the webUI wasn't necessary for TACACS to function, just like it's unnecessary to do on a switch, router, etc.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-10-2019 06:05 AM
I agree - it's kind of an add-on afterthought. Just like is done with FMC.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-09-2019 06:17 AM - edited 12-09-2019 06:18 AM
Now configuring users manually on SMC WebUI won't be necessary anymore, starting in SMC 7.1.2 version, that will be released on December this year. Plus you will be able to perform authorization also with TACACS+, so the roles can be configured and pushed from ISE side.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-25-2019 06:05 AM
Hi
"Once successfully added, create a user in Stealthwatch and tell Stealthwatch to use this newly added Authentication service for that user."
When authentication 10 users or more with tacacs+, do you have to create each and every user in Stealthwatch too?
Is there no Tacacs / Radius attributes the Radius (ISE) server can send back to Stealthwatch SMC to automaticaly assign the Role ?
Regards
Jarle
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-25-2019 06:16 AM
HI,
each and every user has to be created, no role assignment. The integration is for user authentication only as of now.
Regards
Hanna Jabbour
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-15-2019 06:27 AM
Do you possible know if the Flow Sensors can be integrated into TACACS.
From what I could find so far it seems that TACACS configuration is only valid for the SMC?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-16-2019 06:22 AM
Correct - it is only for the SMC.
It's ironic that a security product doesn't leverage external authentication services.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-21-2022 01:14 AM
Thank you, made my day.
At 7.4 you can configure die ISE as a RADIUS in the WebGUI. But still need to configure the user. But instead of choose a password, you use ISE as the identity source
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: