I just wanted to share a configuration I have been working on. There are two internet circuits to two different Internet service providers (ISPs). Say we want to do BGP between the two ISPs and place a firewall between our boundary routers and our inside routers.
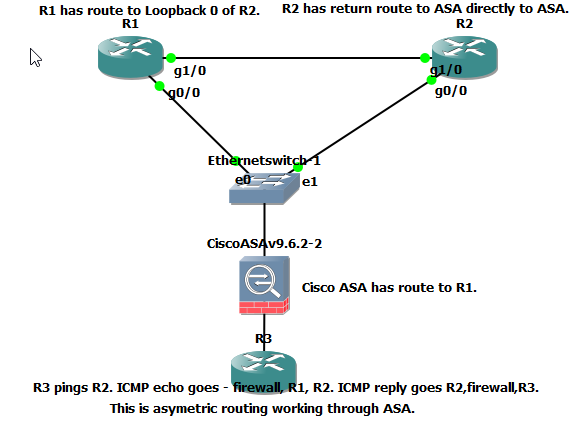
R3 is an inside router with a default route to the firewall. The firewall has a default route to R1, this is for testing purposes. R1 has a route to a loopback interface configured on R2. R2 has the loopback interface configured and a route back directly to the firewall.
Here is a packet coming in on Gi1/0 from R1.
*Oct 14 18:02:15.751: IP: s=192.168.3.3 (GigabitEthernet1/0), d=192.168.4.1, len 100, input feature
*Oct 14 18:02:15.759: IP: s=192.168.3.3 (GigabitEthernet1/0), d=192.168.4.1, len 100, rcvd 2
Here is the reply going directly to the firewall from R2.
*Oct 14 18:02:15.767: ICMP: echo reply sent, src 192.168.4.1, dst 192.168.3.3, topology BASE, dscp 0 topoid 0
*Oct 14 18:02:15.771: FIBipv4-packet-proc: route packet from (local) src 192.168.4.1 dst 192.168.3.3
*Oct 14 18:02:15.775: FIBfwd-proc: packet routed by adj to GigabitEthernet0/0 192.168.1.1
This confirms the packet takes one route out to the internet and returns on a different path, the firewall allows the traffic through.
If we placle a default route to both ISPs on the firewall, we should be able equal cost load balance traffic to either outside boundary router, let BGP do its thing, and it should not matter which side the return traffic comes back in on. I hope this article sparks some conversation and I look forward to comments.
Please mark this as helpful if you find it helpful.
