- Cisco Community
- Technology and Support
- Security
- Security Blogs
- Cognitive Alert Fusion Early Access Release Notes
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
User Experience Enhancements

As part of the Cisco Common User Experience program, we are working towards a more uniform user experience and terminology alignment. This program runs across all Cisco security products.
Early Access to Cognitive Alert Fusion
The Cognitive Intelligence team has enabled early access to Cognitive Alert Fusion - the most significant overhaul of Cognitive Threat Analytics in the last five years. Since launching Cognitive Threat Analytics back in 2014, we took all we learned back to the drawing board to reimagine the security analyst’s experience from the ground up.
Our primary goal was to increase the relevancy of Cognitive security alerts while reducing the alert fatigue caused by the number of alerts security response teams need to handle. We achieved that goal by raising the level of abstraction and creating a curated list of aggregated contextual alerts, which are incrementally tuned to be highly relevant for the incident response team in each organisation.
Table of Content:
Cognitive Alert Fusion 101 (Introduction)
The goal of Cognitive Alert Fusion is to provide the security analyst with a single, prioritized list of security alerts. A security alert represents a natural unit-of-work for investigation and subsequent remediation and ideally enables 1-1 promotion of security alerts into security incidents.
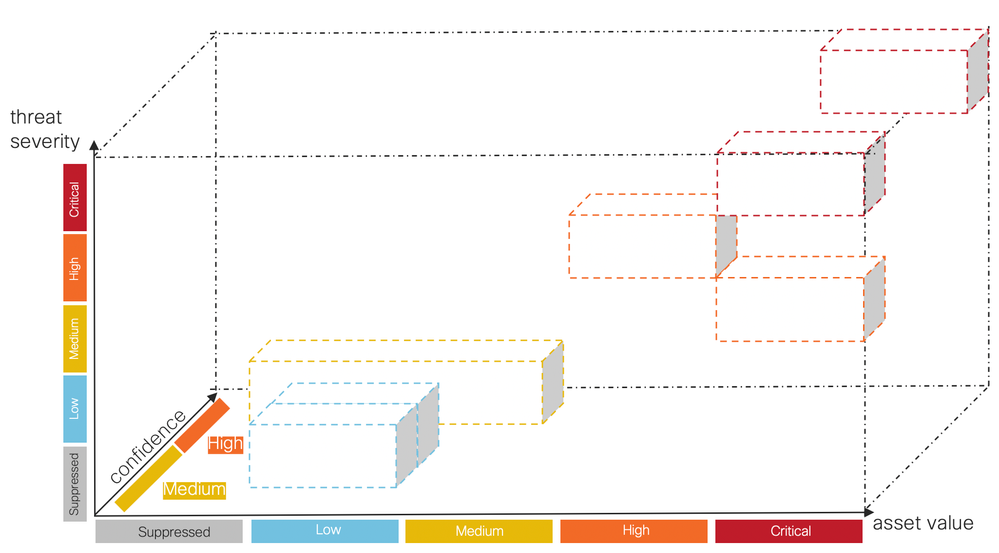
To achieve this goal, we implemented a unique 3D security analytics engine which applies machine learning to incoming data streams and projects the detections to a 3-dimensional space:
- Threats dimension. Building on the heritage of Cognitive Confirmed Threats, we revamped our threat catalog to provide rich, contextual information for the security analyst. Moreover, the users can adjust the pre-defined threat severity of individual threats to better align with their organization’s risk profile towards individual threat types.
- Assets dimension. This is a newly introduced dimension that allows us to capture the fact that not all devices connected to the enterprise network are equally important from the business perspective. Not only do we show how different groups of devices are affected by threats we detect, but users can adjust the business value of individual asset groups to prioritize detections for more important devices.
- Confidence dimension. This dimension reflects the confidence about verdicts our algorithms are making about individual instances of threats we observe in the customer environment. While in some instances, we observe enough behavioral indicators that our verdict is almost certain, in some other instances, despite the similar symptoms, the actual evidence might be sketchy. Therefore, the margin for error increases.
The Cognitive Alert Fusion algorithm takes a set of threat detections, anchored in the 3-dimensional space, as its input and identifies clusters of similar threat detections. These clusters of detections are presented to the user as security alerts. Each alert refers to one or more assets (devices) of comparable business value, each of them infected by the same set of threats exhibiting similar symptoms, thus resulting in verdicts of similar confidence.
Cognitive Alert Fusion in Practice
A new way to experience the Cognitive Intelligence web interface is opening for early access.
Available to all customers under the Early access option, the new Cognitive console presents information in a smarter manner and will be able to group threats in one alarm based on these parameters:
- Concurrent threats: Different threats that are occurring together.
- Asset groups value: This group of threats is occurring for endpoints that belong to asset groups with similar asset value.
How do we know which asset groups have similar asset value?
One of the novelties of this approach is we will automatically import host groups defined on Stealthwatch Enterprise and use them to display alerts in a more optimal manner.
You will be able to determine how important this asset group is for your organization. This category will influence the grouping and prioritization of detections on these assets. You can even tune down alarms in specific asset groups.
Threat severity is no longer set in stone
Because different organizations have security concerns specific to their vertical and their own business needs, it is also possible now to select the threat severity that is relevant to your network.
Alert fusion will make threat hunting and network monitoring easier:
- It works out of the box
- Provides customer-specific threat severity, maintaining an industry-specific threat-severity baseline
- Single, prioritized list of security alerts
- Alerts are a natural unit of work, for investigating and subsequent remediation
Let’s deep dive into the different screens of the new console, where you can obtain and customize information.
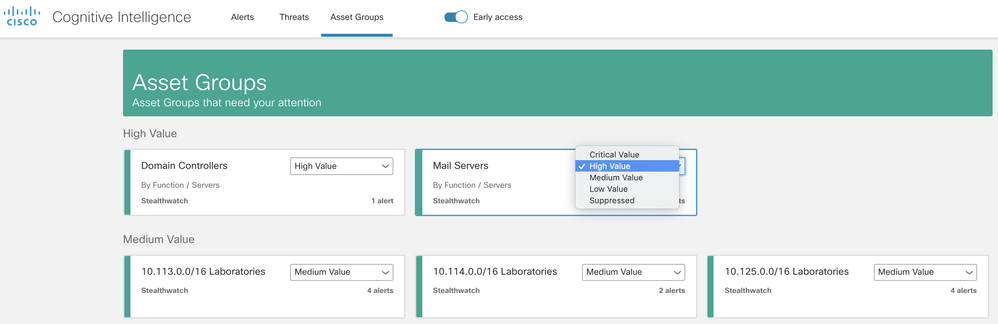
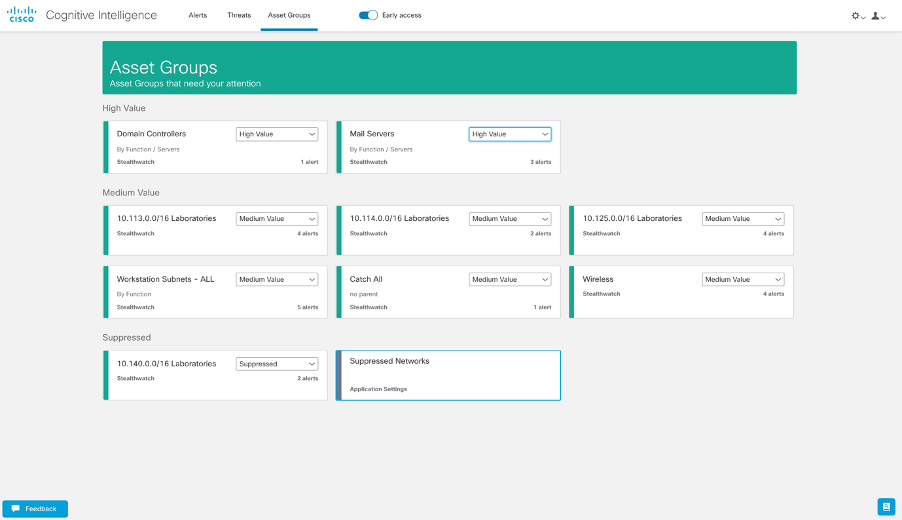
Asset Groups tab
In this tab, you will be able to see all your asset groups that have traffic sent to Cognitive Intelligence. They will be imported automatically from Stealthwatch Enterprise.
- Each card represents a group of assets for which Cognitive Intelligence is reporting at least one alert.
For customers that are sending traffic from WSA and don’t send any traffic from Stealthwatch Enterprise, there will be only one asset group for now, called Uncategorized.
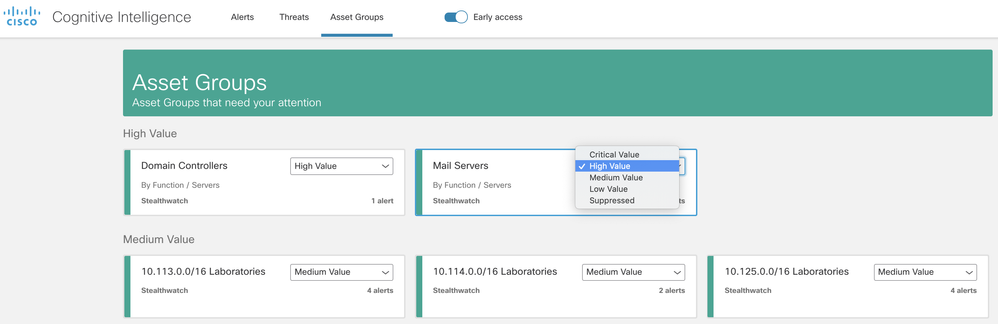
- The business value of each asset group can be changed by the user. This will be considered for prioritization, grouping, and risk assigned to security alerts.
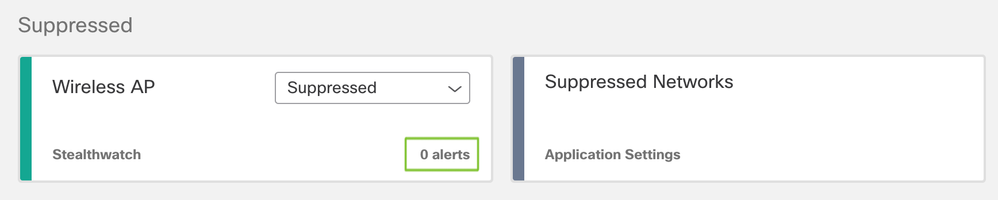
- It’s also possible to suppress asset groups. Threats that are detected on an asset that belong a suppressed group will no longer raise alerts.
- Suppressed asset groups will continue to be visible in the Asset Groups tab.
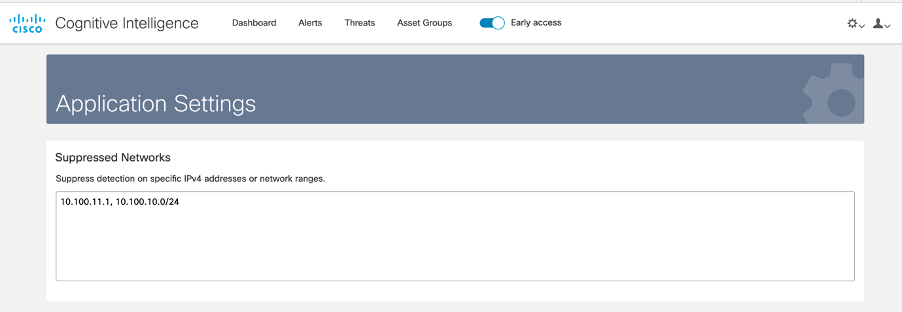
- You can manually define entire subnets or assets that will be suppressed. by clicking on Suppressed Networks. The Suppressed Networks works also for the customers, who rely exclusively on a web proxy as a data source and do not have any Stealthwatch host groups imported.
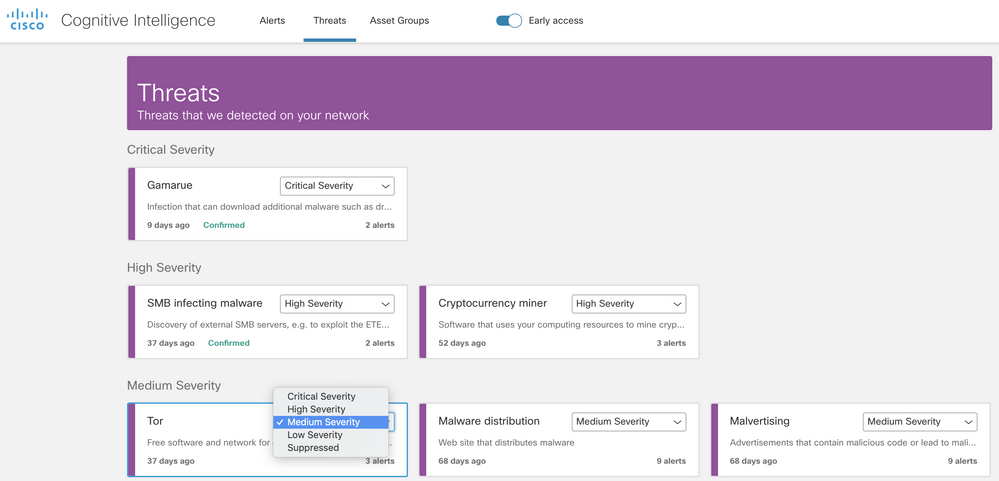
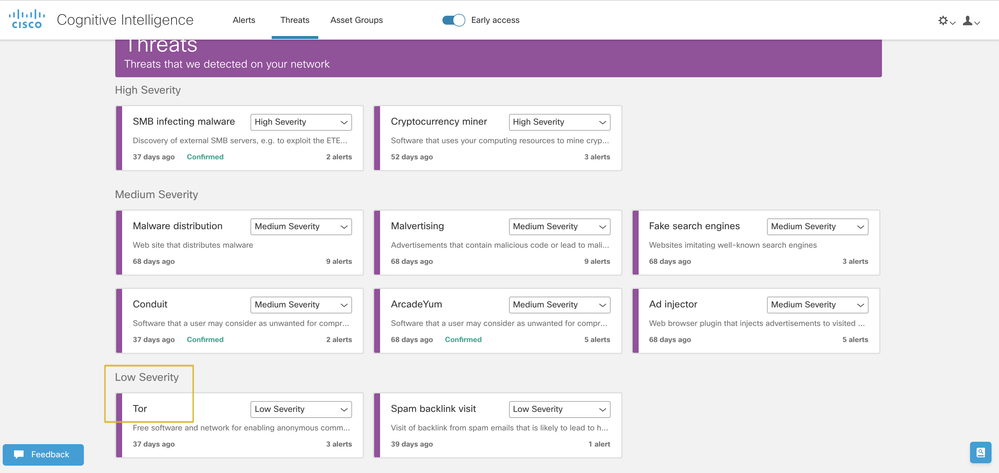
Threats tab
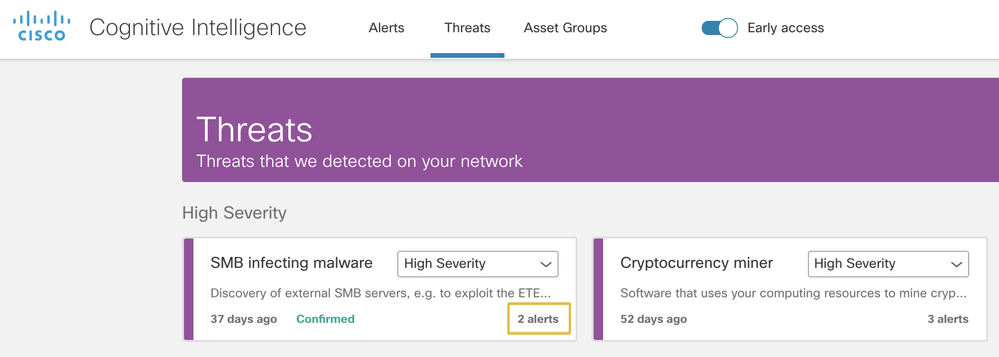
In this tab, you will be able to see the entire threat portfolio that has been detected in your network in the past 45 days.
- Each card represents a different threat that will be grouped in the alerts section.
- A specific type of threat might be involved in several alerts. You can see a counter at the bottom right of the card indicating the number of alerts in which this specific type of threat is involved with.
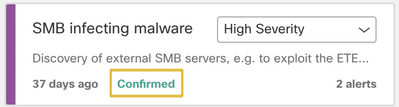
- A threat card labeled "Confirmed" means that we have high confidence in the threat and its severity. The additional descriptions that you can find in threats marked as “Confirmed”, will allow you to understand the implications of this alert to your business.
For a threat to be labeled as confirmed, we have seen at least one indicator of compromise (IoC) in the traffic that is related to a specific malicious behavior. This IoC has been confirmed by a team of threat researchers.
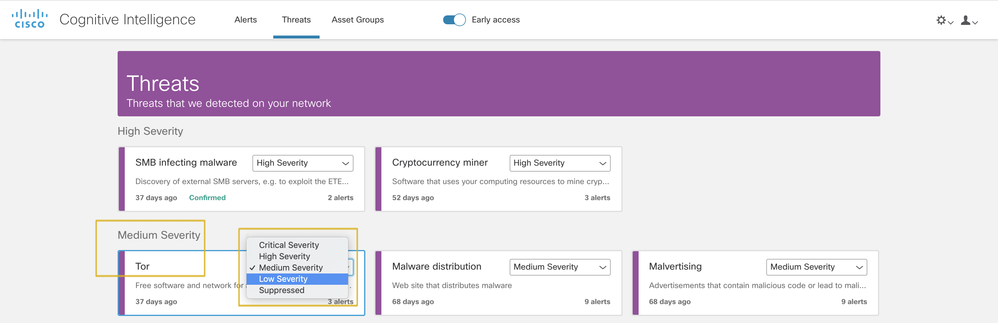
- You can change the default severity assigned to the specific threat type according to your network-specific conditions and business needs. This will affect the relative ordering of alerts and risk results.
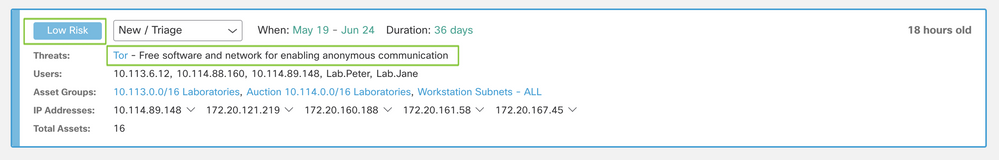
You can see the “Tor” threat card with its severity changed to “Low severity:”
Consequently, all alerts that contain this type of threat will have their risk recomputed. Risk will be calculated weighting the new severity assigned to the threat, asset value and confidence:
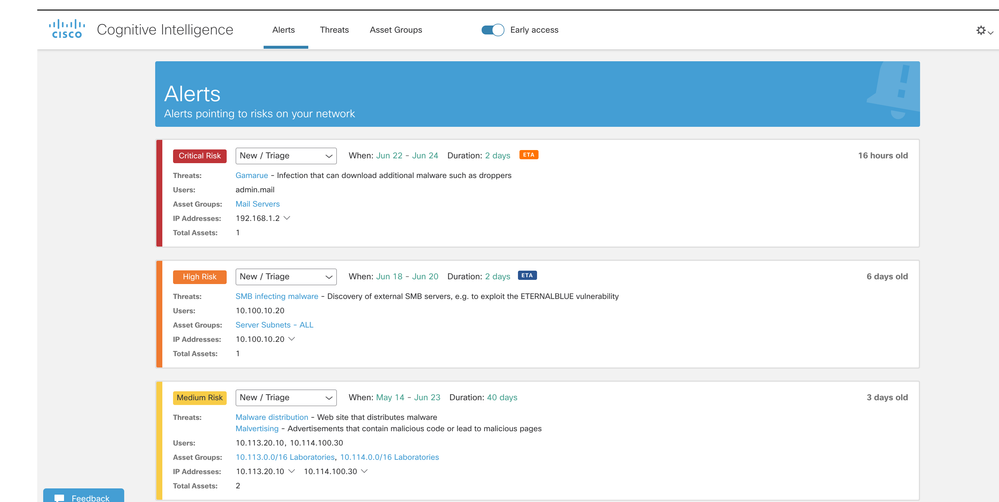
Alerts tab
In this tab, you will be able to see all the active alerts for your deployment. Each alert will be displayed on a different card.
One alert card aggregates one or more threats affecting concurrently a set of assets of comparable business value.
The risk of one alert card will be calculated based on the severity level of the threat and business value asset groups a particular asset belongs to. Alert cards with higher risk are shown at the top of this tab.
Alert cards will be dynamically changed when either new threats are added to the grouping or the associated asset group business value and threat severity value is changed.
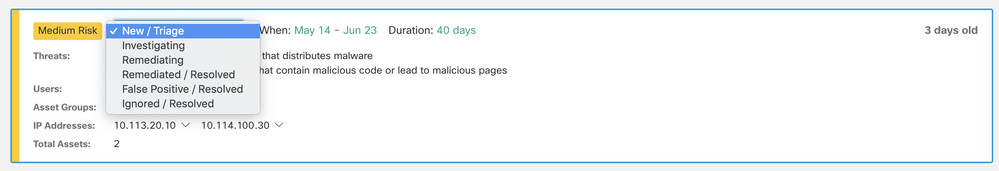
However, if the investigation state of an alert changes from New/Triage (Possible investigation states are: New/Triage, Investigating, Remediated, False Positive, Ignored), the alert card will remain stable and unchanged, to ease investigation.
To change the investigation status of one alarm, click on the following menu:
This will open a dropdown menu with all the possible options:
Let’s look at a couple of alert examples:
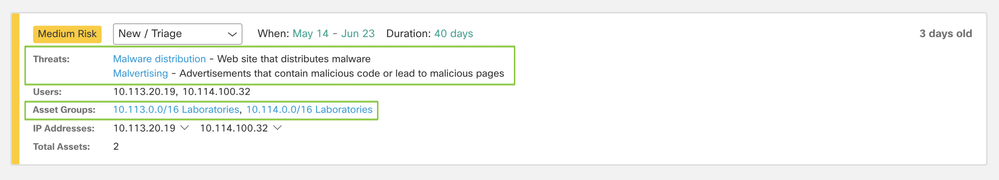
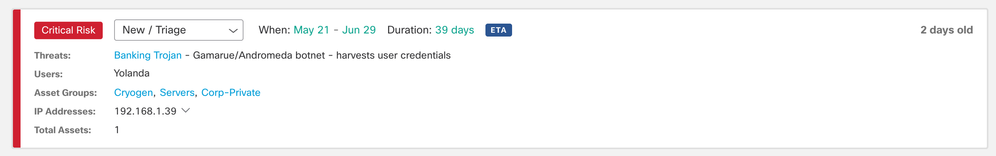
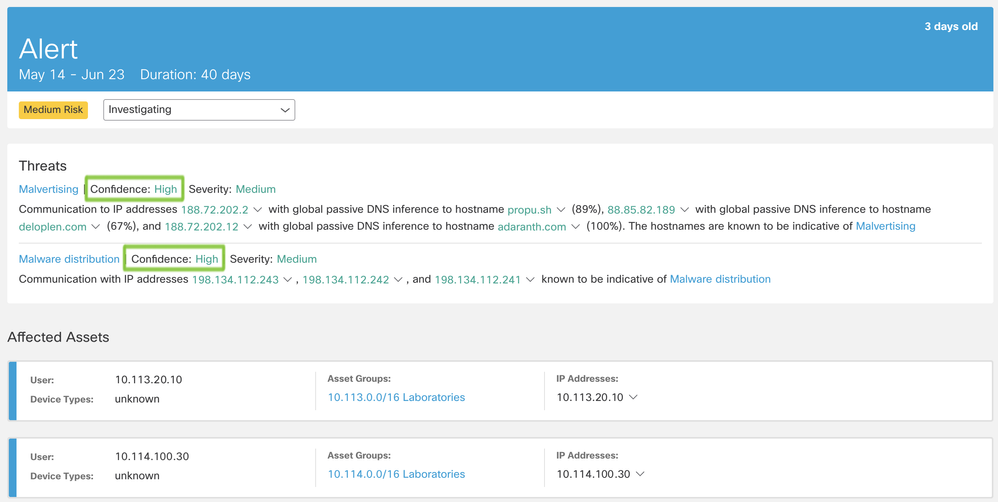
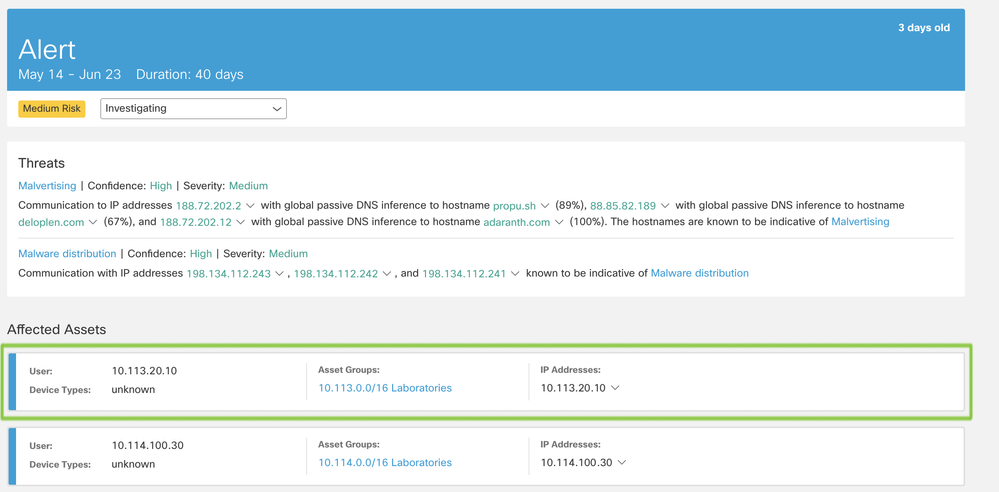
In this alert card, a “Banking Trojan” threat has been identified for user Yolanda, with an IP address of 192.168.1.39. This IP address belongs to three asset groups: Cryogen, Servers, and Corp-private.
The alarm has a critical risk assigned to it because the threat has a high severity, and the business value of at least one of the asset groups has a high severity, too.
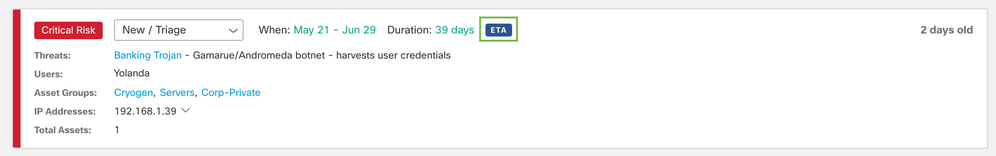
We can see a blue ETA tag (Encrypted ETA Based Detection) in this card, which means at least one of the flows used to identify this threat was using enhanced telemetry, and the traffic was encrypted.
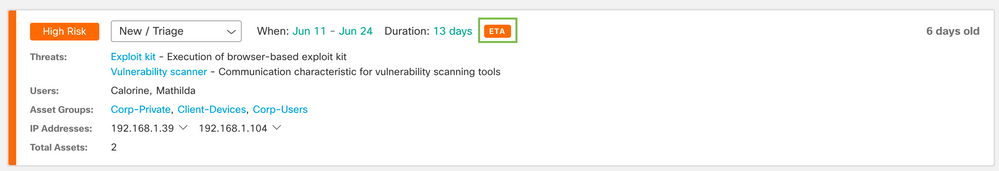
In our second example, there are two different threats (“Exploit kit” and “Vulnerability scanner”) occurring on both assets (users are Caroline and Mathilda, and their IP addresses are shown, too). Those users belong to asset groups that have the same business value assigned. Therefore, as both assets are affected by the same threats, all this information was shown in a single alarm card.
We can see that the alert is tagged with an orange ETA keyword (ETA based detection), which means that at least one of the flows used to identify one of the threats was enriched with enhanced telemetry, and it was not encrypted.
By clicking on the alert card, you navigate into the alert detail. In this view, you can investigate additional content about each specific threat: anomalies that were triggered and led to identification of this threat, IP addresses and domains that the assets communicated with, and which specific IoCs were indicative of that malicious behavior.
You can also see the level of confidence that the machine learning algorithm has assigned to this specific detection:
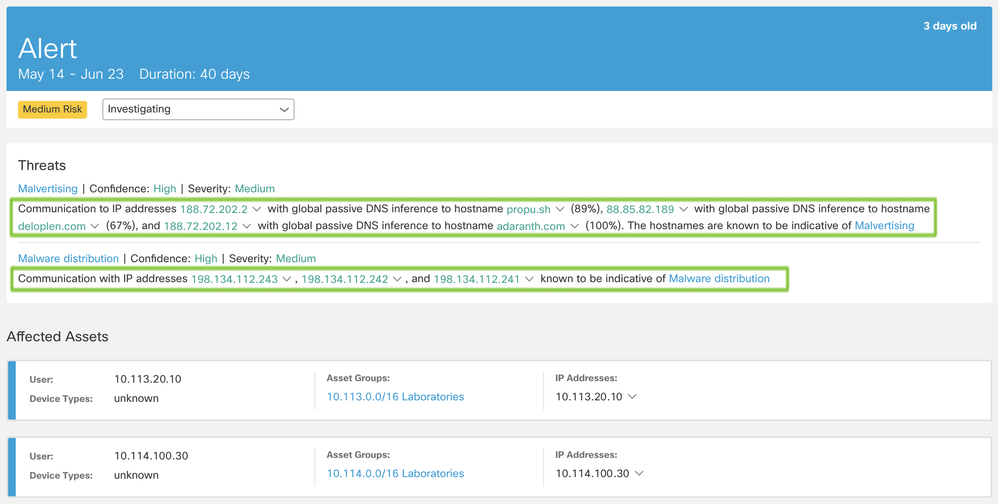
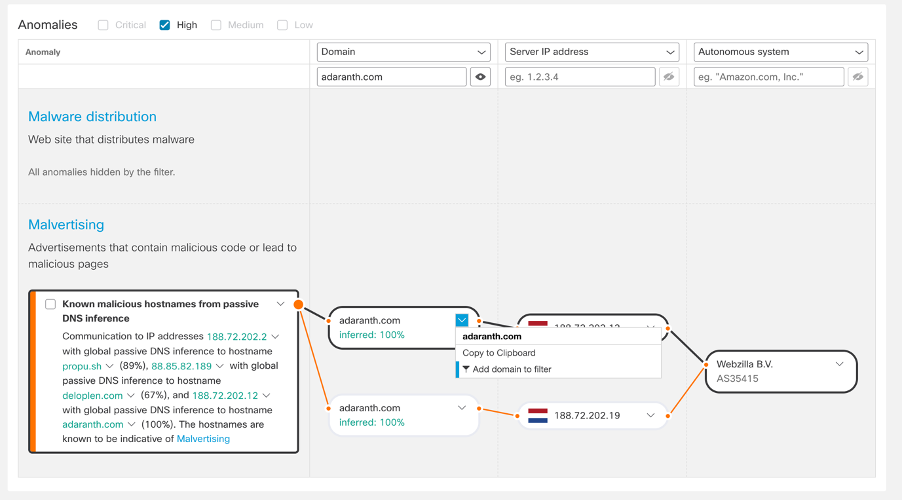
Selecting one of the specific events for one user allows you to pivot to the anomalies view.
Here you see a detailed context of the specific events that triggered the malicious detection. In this case, there was communication from the affected asset to three IP addresses: 188.72.202.2, 88.85.82.189, and 188.72.202.12. Hostnames of these three IP addresses are being inferred by a global passive DNS algorithm, with a confidence of 89%, 67%, and 100%, respectively.
Click the drop-down arrow and copy this IoC to your clipboard, to ease your next steps in investigation.
By increasing the relevance of alerts through smart grouping, and allowing asset and threat severity customization to fit the business needs of your organization, the powerful combination of Stealthwatch Enterprise, Web Security Appliance or a 3rd party web proxy, and Cognitive Intelligence allows you to cut through complexity and act on key threats affecting your network.
Enjoy our new capabilities and share your observations using the feedback button located in the lower-left side of the GUI.
You can also give us feedback and debate with other customers and experts in the discussion forum that we have prepared for early access to Cognitive Alert Fusion.
Leveraging Cognitive Intelligence
Cognitive Intelligence capabilities are available to AMP customers with a compatible web proxy such as the Cisco Web Security Appliance, and all Stealthwatch Enterprise customers. Reach out to your account executive to learn how to turbocharge your existing cybersecurity investment with Cognitive.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: