- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- ACS 5.2 Configuration Example - Stripping an user domain
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
10-28-2010 07:02 AM - edited 02-21-2020 09:57 PM
- Introduction
- Initial setup
- Proxy Configuration
- Creating the proxy
- Authentication configuration
- Conclusion
- Scenario 2:
- More Information
Introduction
Stripping an user domain with ACS 5.2: In this document we will see how to configure ACS as a proxy to itself to strip a part of the username.
In some cases, it is required to remove the DNS suffix to authenticate the user, and if it’s possible in LDAP configuration, there are no such options in other identity stores, but luckily there’s an option to rewrite the username when you are using ACS as a radius proxy.
Note: this is working only with pure radius request, not with EAP inside Radius.
Initial setup
I will use a catalyst 3560 to test user credentials using the test aaa group command.
The 3560 got the IP 10.48.76.4.
ACS is 10.48.76.48.
ACS version : 5.2.0.26
3560 Version : 12.2(50)SE3
Switch configuration:
!
interface Vlan1
ip address 10.48.76.4 255.255.255.128
!
ip radius source-interface Vlan1
radius-server attribute 8 include-in-access-req
radius-server dead-criteria time 60 tries 30
radius-server host 10.48.76.48 auth-port 1645 acct-port 1646 key cisco
radius-server vsa send authentication
!
A user bastien with password bastien has been created and can authenticate to the ACS server. bastien@stripthatdomain.com does not exist, as we can see in the following output.
3560#test aaa group radius bastien bastien legacy
Attempting authentication test to server-group radius using radius
User was successfully authenticated.
3560#test aaa group radius bastien@stripthatdomain.combastien legacy
Attempting authentication test to server-group radius using radius
User authentication request was rejected by server.
3560#
Proxy Configuration
To configure the proxy, we need to understand the process:
• The Switch will send the access-request to the ACS
• The access-request will match the proxy access rule and username will be translated, then ACS will proxy the modified access-request to itself
• The proxied access-request will match another rule which will indicate how to authenticate the user.
So we will need to create a proxy entry, then a rule to send traffic to this proxy, and then other rules to authenticate proxied traffic.
Creating the proxy
Go to network resources, and click external RADIUS servers, then click the Create button (figure 1).
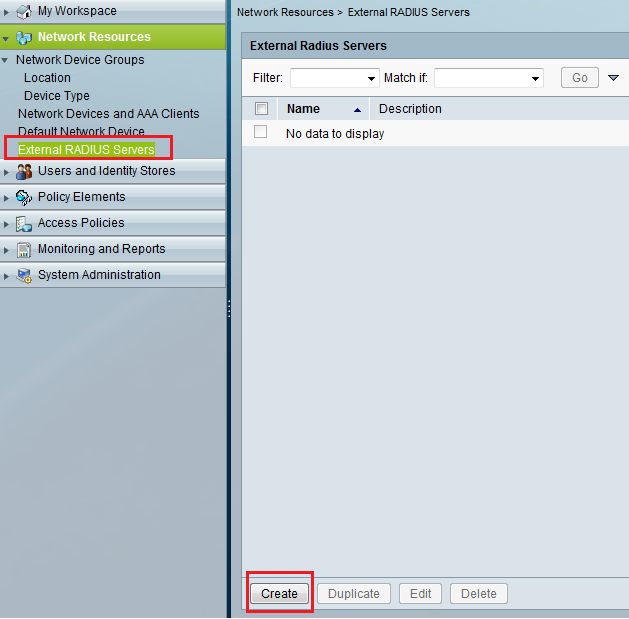
Figure 1
Create proxy with the ACS IP Address as hostname (I used the loopback, but you can use a DNS entry or the interface address, but notice that if you change the IP or that the DNS is down, the proxy configuration will be broke) and choose a shared secret (remember it).
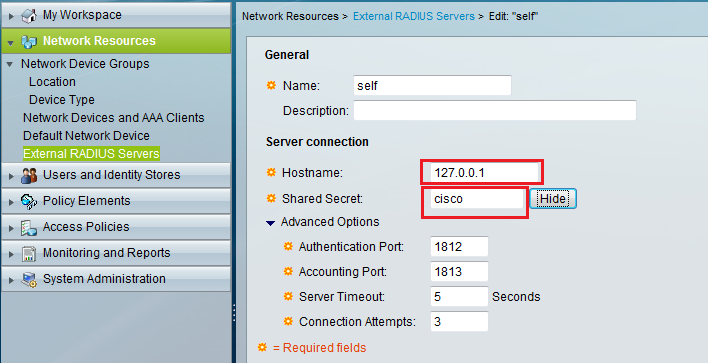
Figure 2
Then go to the “Network Devices and AAA Clients” and create a client with the ACS IP you used in the prior step (loopback or Eth0), and use the same radius shared secret as above.
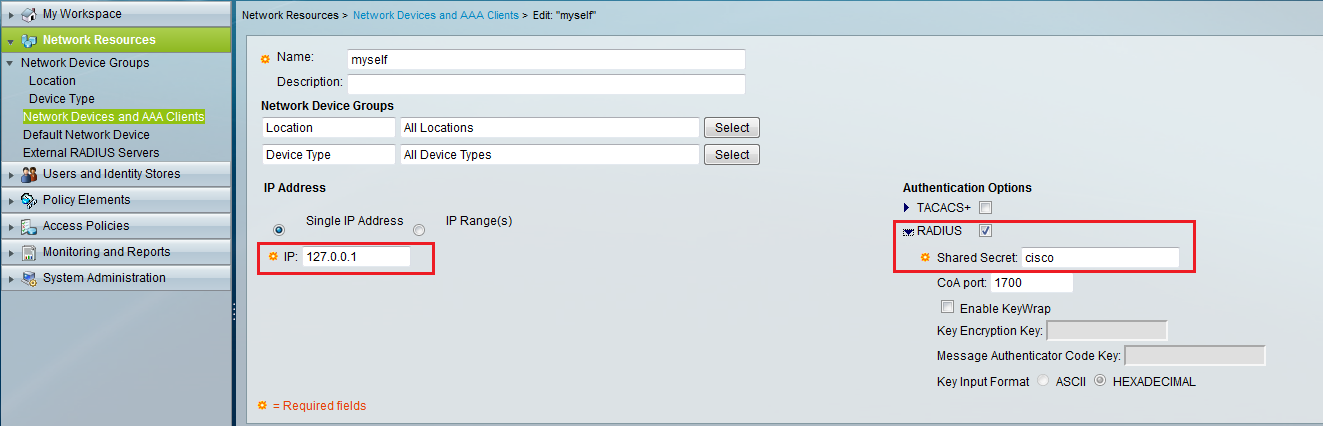
Figure 3
After that, go to the access policies menu and click on the access services link, then create an access service with ‘User selected service type’ as RADIUS Proxy, select your external radius server (which is, in fact, your ACS) and in the advanced drop down menu, you can choose the strips options you need, and click finish.
Refer to the figure 4.
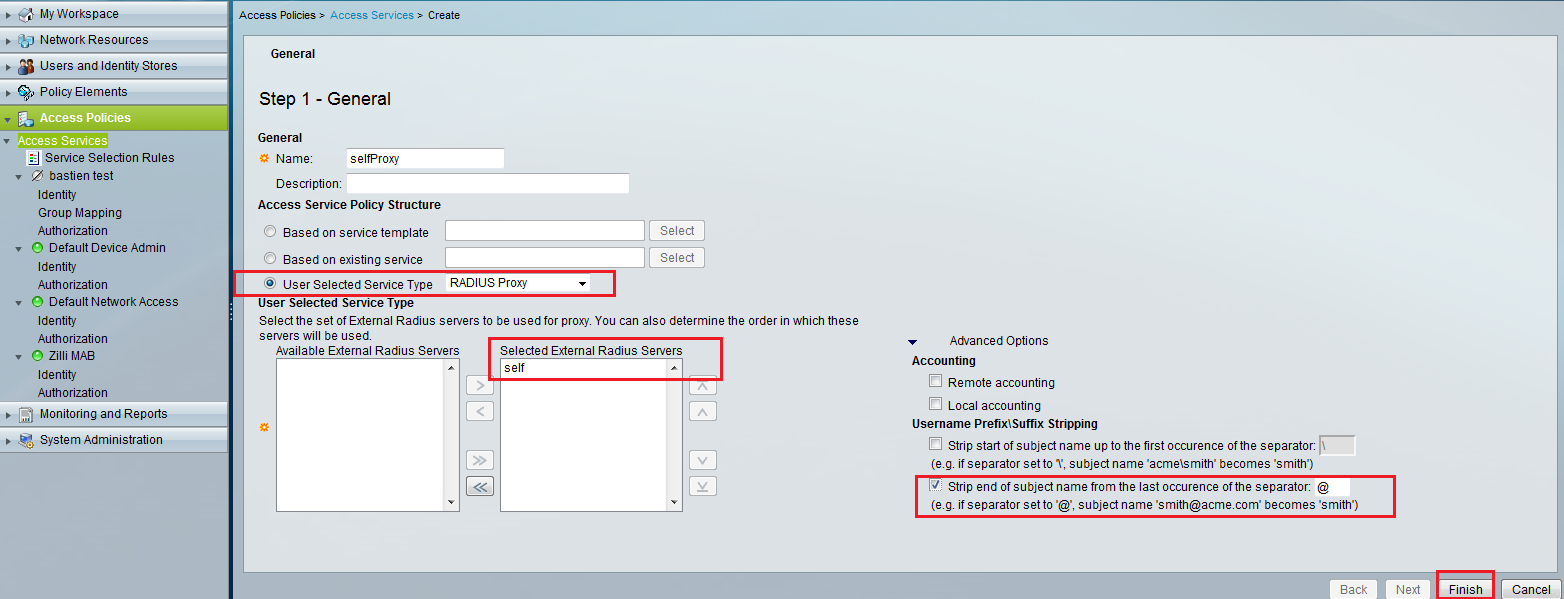
Figure 4
Now, create a Service Selection Rule to identify the Radius traffic that needs the username to be stripped and select the access rule that you have created which sends traffic to the proxy. I will match the radius traffic from my switch (see figure 6).
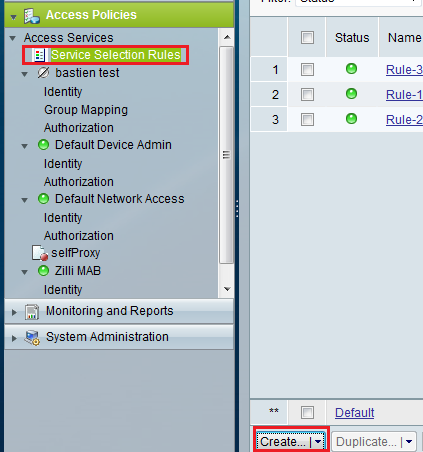
Figure 5
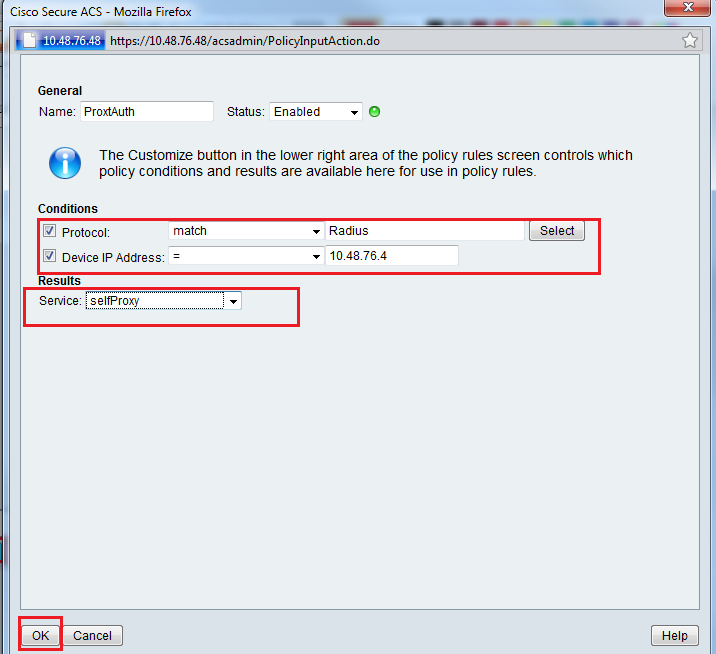
Figure 6
Don’t forget to move up the newly created rule so that the traffic does not match another rule before (see figure 7).
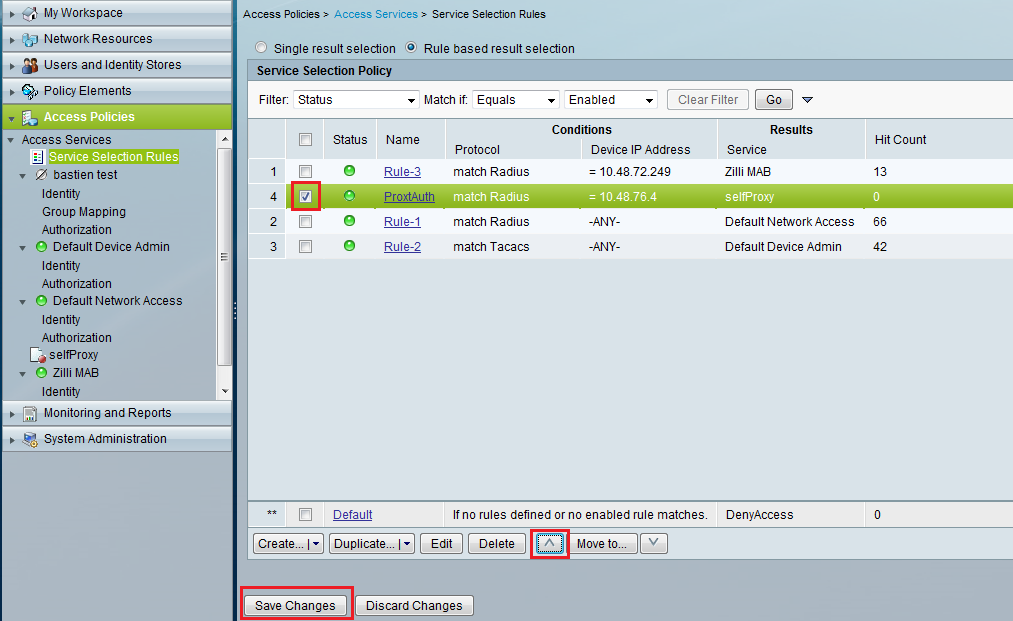
Figure 7
Authentication configuration
Now that we configured the ACS to strip domain name, and send back the authentication request to itself, we must configure it to handle this request.
Start by creating a new Access Service, and set the identity store of your choice (I use local store for testing purpose but you can set active directory or whatever you want).
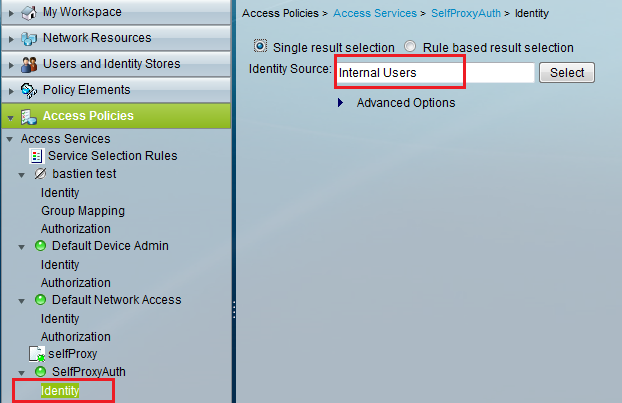
Figure 8
Then go back to the service selection rule, and create a rule that will match incoming radius traffic from ACS and send it to your Access Service (see figure 9).
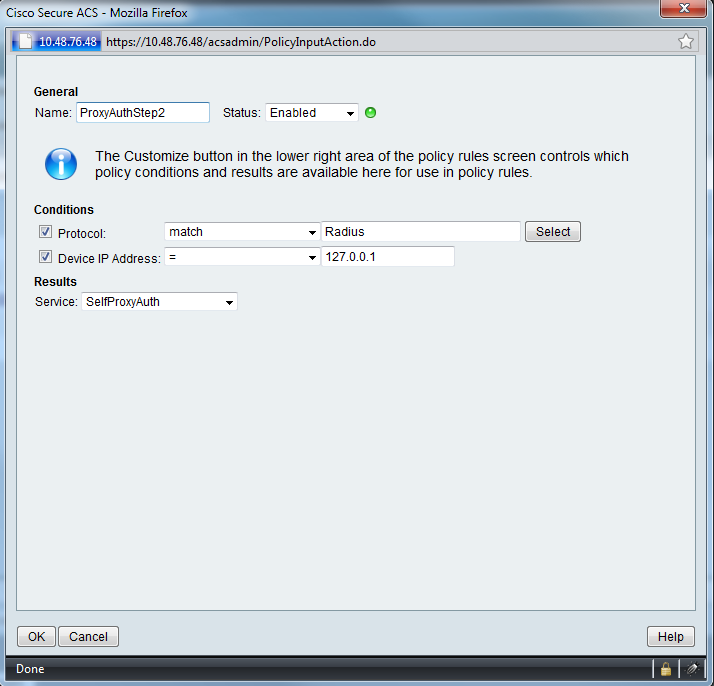
Figure 9
The final service section rules should look like figure 10.
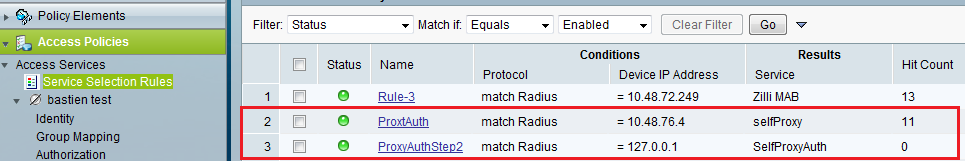
Figure 10
And now the final step, test! Normally you would see your stripped username in the ACS monitoring view (in radius authentication – see figure 11)
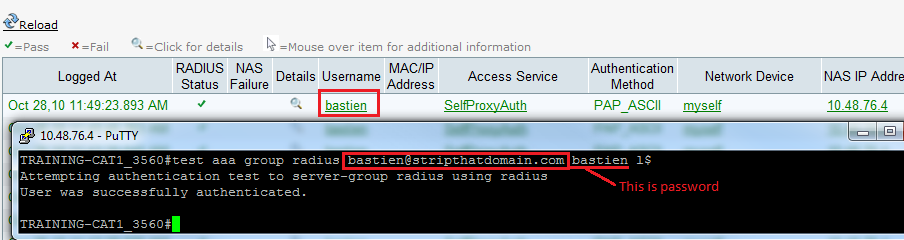
Figure 11
Conclusion
This document described the Configuration of ACS 5.X to strip a domain name or prefix name from an incoming radius request by proxying to itself. Same features should be available in ACS 4.X. Please note that the proxy feature can't modify the username from an EAP Request as each EAP Method has its own way to exchange the username and it might be ciphered.
Scenario 2:
Problem:
User wishes to disable auto complete for username and password on the ACS 5.3 GUI login page.
Solution:
Try to update to the patch 5.3.0.40.7
Resolved Issues in Cumulative Patch ACS 5.3.0.40.7
CSCub40498 : The password field in ACS 5.3 has the autocomplete operation enabled.
Sometimes it can be the browser issue also as the password has been saved in the browser cache you can clear the browser for history of passwords save.
More Information
User Guide for the Cisco Secure Access Control System 5.2
Migration Guide for the Cisco Secure Access Control System 5.2
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Please put the conclusion in the top, i just spend a long time trying the config, only to realise that this doesn't work with PEAP/MSCHAPV2 :-(
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Indeed, I modified the post. Thanks for your feedback.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
I have the same problem with PEAPv0/MSCHAPv2. Do you have already a solution?
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: