- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- Alcatel 8068S VPN configuration with FTD 6.4
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
on 03-28-2020 03:48 PM
Purpose of this article is to share our experience during that Covid-19 period where we were able to successfully setup a VPN configuration for remote worker using Alcatel 8068S phones with FTD 2110 running 6.4.0.8.
I would like to thank all of my colleagues that helped in solving that problem : Alain TREMBLAY, Benjamin HUBERT, Robert NELTA, Bertrand NGALO, Sebastien DA SILVA, Luis MARQUES and Rodolphe VALIDIRE. I would like also to thank Nidhi S. from the TAC who pointed out CSCvr53363 which was the big part of our problem.
The bug is not public yet, but, part of the problem was the fact that we were already doing site-to-site VPN and anyconnect on the "outside" interface, and we had to create another "outside" interface for hub-to-spoke with dynamic public IP address setup.
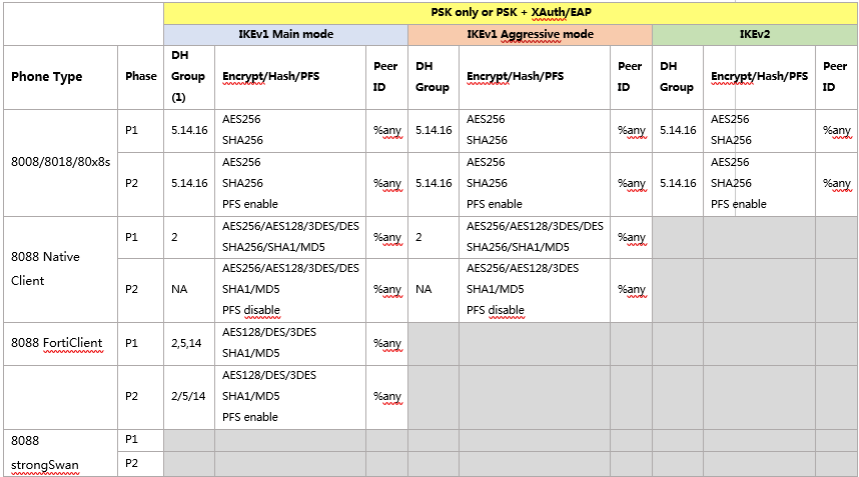
The 8068s supports only site-to-site configuration with very limited options :
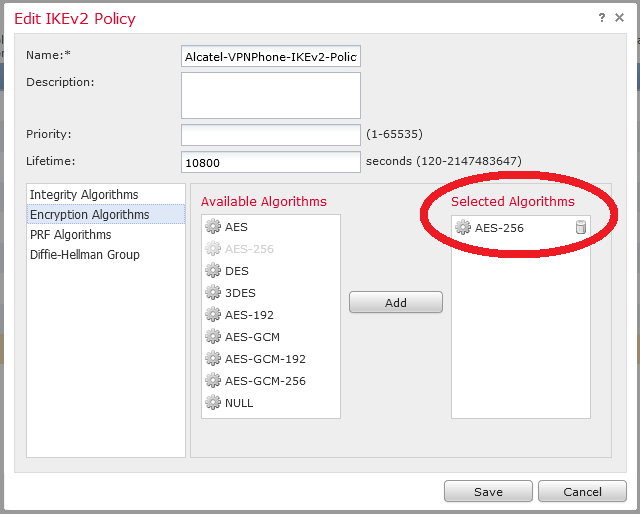
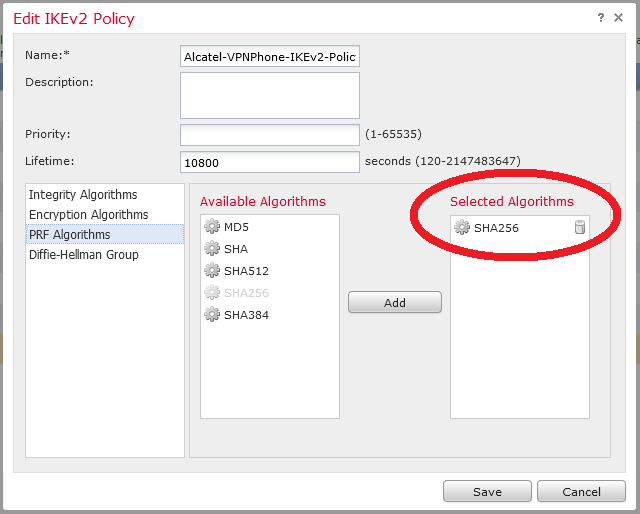
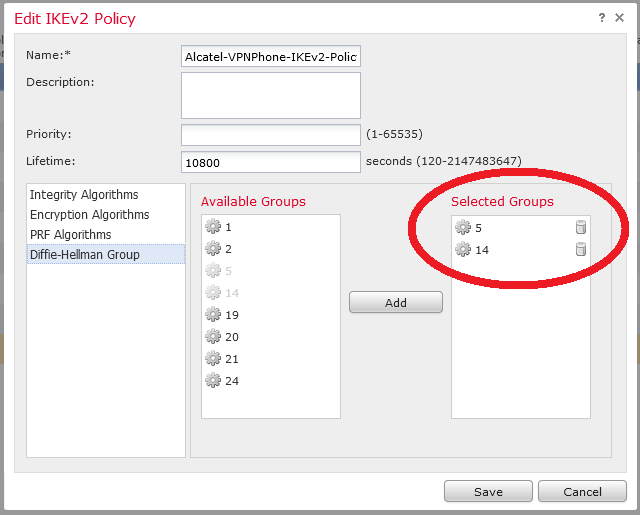
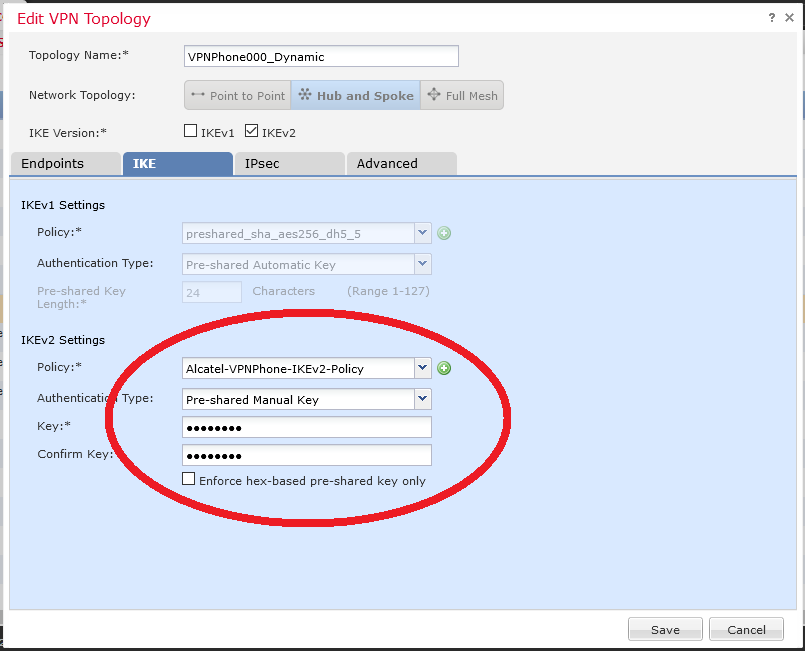
So first is to create IKEv2 sets for the hub-to-spoke tunnel configuration :
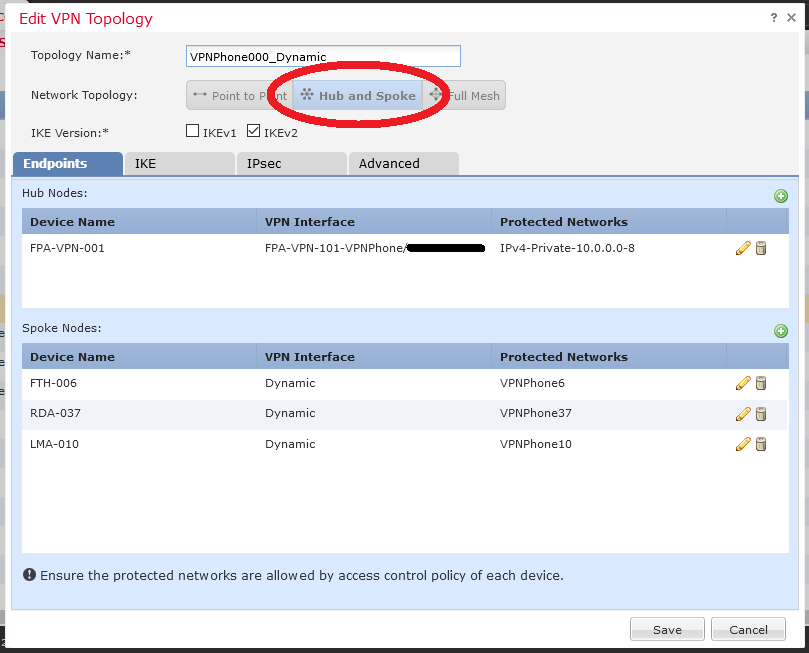
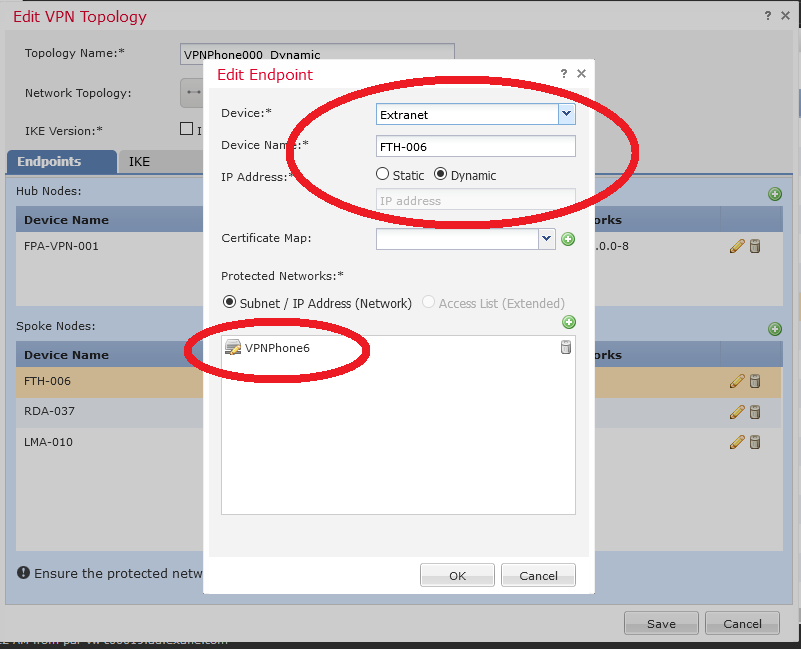
Now we are ready to configure the hub-to-spoke topology :
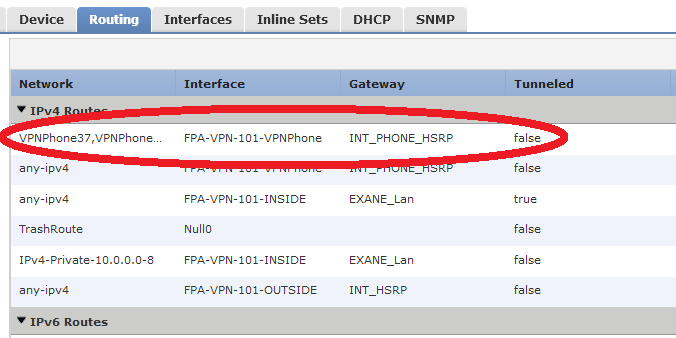
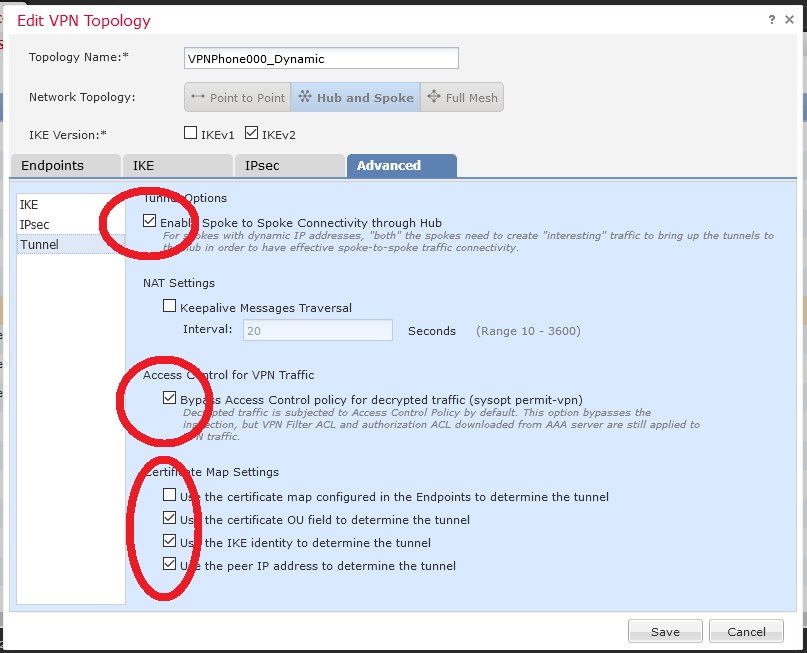
The important part is here : we began to add VPN phones one-by-one so the protected network (which is an IP address in a dedicated VPN network) needs a particular route through the "new outside" interface :
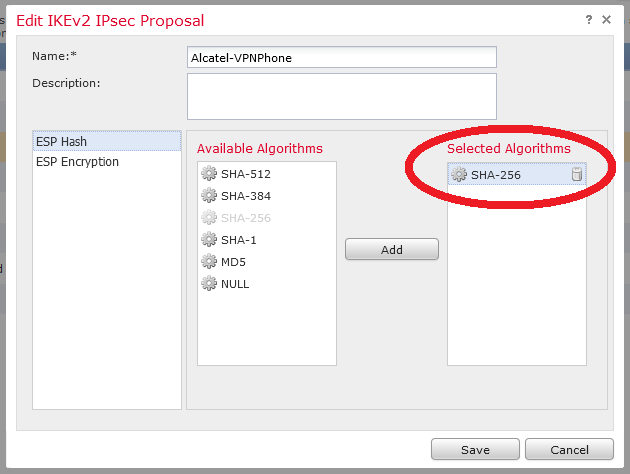
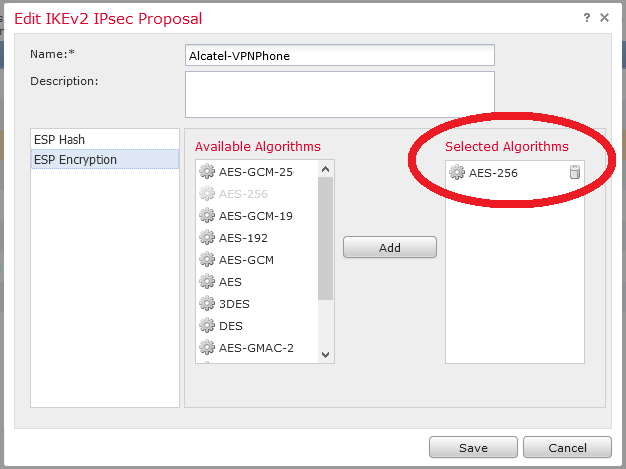
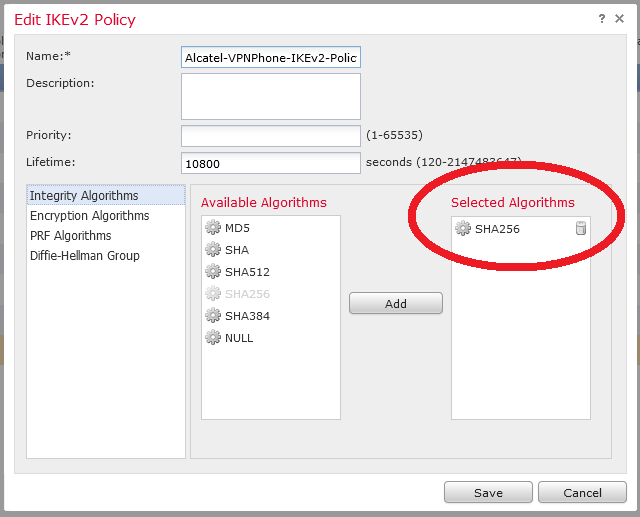
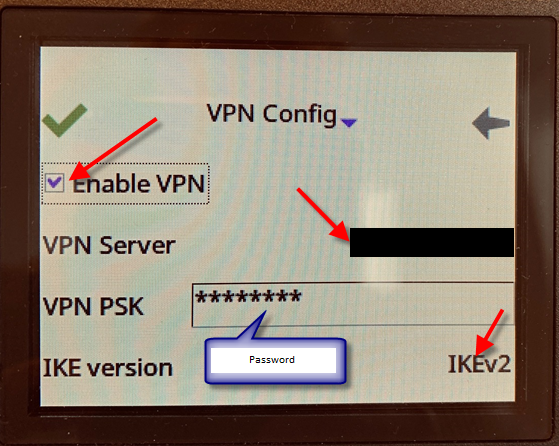
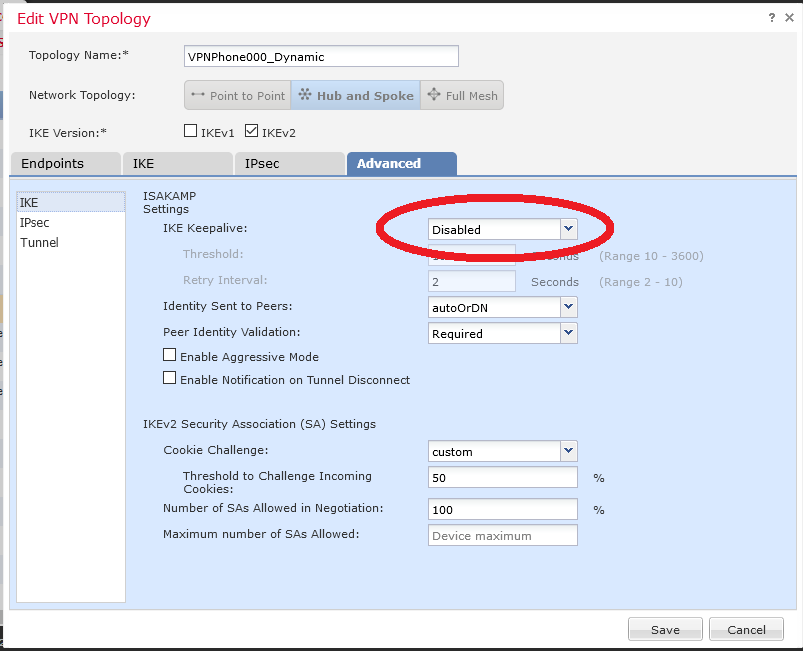
Then configuration continues with Alcatel 8068S specific values :
This password is the one shared on the Alcatel 8068S side :
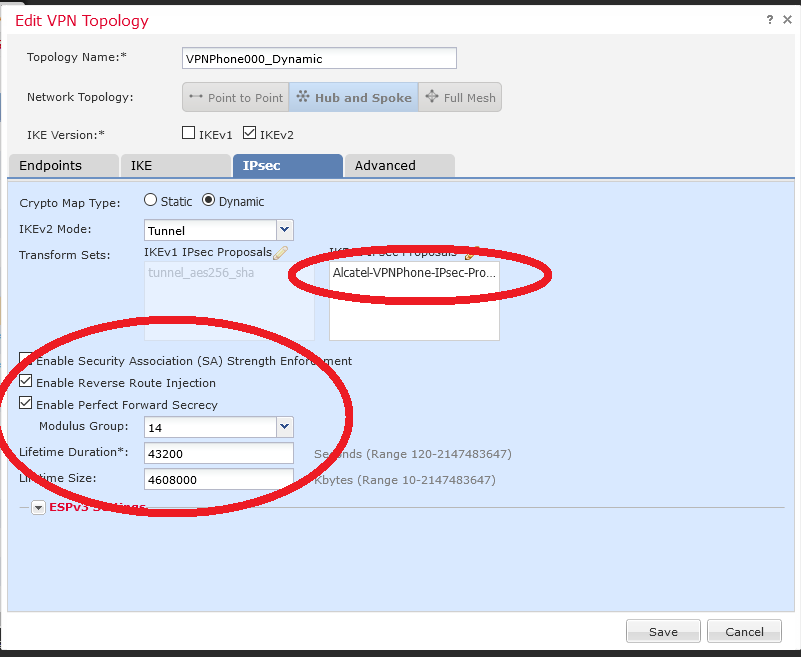
Be careful of PFS, DH Group and lifetime :
Push, and enjoy !
Stay safe, and take care guys.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Good tricks!!
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi fthiel92
Thanks for posting this, we are experiencing what seems to be the exact same scenario and have followed your steps with the new outside interface and settings etc. Our FTD is on 6.4.0.9
We cannot seem to get past Phase1 however. Our Firewall seems to be rejecting it due to DH-Group 16 and as you know yourself 16 is not an option of these firewalls.
IKEv2-PROTO-4: (1992): Sending invalid ke notification, peer sent group 16, local policy prefers group 14
I am just curious if you guys had to make any changes on the Phone side to get this working or if you experienced something similar yourself in troubleshooting.
The phone seems to send 3 proposals but always 16 first and our firewall rejects in without going down to 14 or 5.
Debug below
If you have any pointers it would be much appreciated.
IKEv2-PROTO-4: Received Packet [From x.x.x.x:500/To x.x.x.x:500/VRF i0:f0]
Initiator SPI : 3F08D05F2651EA7E - Responder SPI : 0000000000000000 Message id: 0
IKEv2 IKE_SA_INIT Exchange REQUESTIKEv2-PROTO-5: Next payload: SA, version: 2.0 Exchange type: IKE_SA_INIT, flags: INITIATOR Message id: 0, length: 808
Payload contents:
SA Next payload: KE, reserved: 0x0, length: 136
last proposal: 0x2, reserved: 0x0, length: 44
Proposal: 1, Protocol id: IKE, SPI size: 0, #trans: 4 last transform: 0x3, reserved: 0x0: length: 12
type: 1, reserved: 0x0, id: AES-CBC
last transform: 0x3, reserved: 0x0: length: 8
type: 3, reserved: 0x0, id: SHA256
last transform: 0x3, reserved: 0x0: length: 8
type: 2, reserved: 0x0, id: SHA256
last transform: 0x0, reserved: 0x0: length: 8
type: 4, reserved: 0x0, id: DH_GROUP_4096_MODP/Group 16
last proposal: 0x2, reserved: 0x0, length: 44
Proposal: 2, Protocol id: IKE, SPI size: 0, #trans: 4 last transform: 0x3, reserved: 0x0: length: 12
type: 1, reserved: 0x0, id: AES-CBC
last transform: 0x3, reserved: 0x0: length: 8
type: 3, reserved: 0x0, id: SHA256
last transform: 0x3, reserved: 0x0: length: 8
type: 2, reserved: 0x0, id: SHA256
last transform: 0x0, reserved: 0x0: length: 8
type: 4, reserved: 0x0, id: DH_GROUP_2048_MODP/Group 14
last proposal: 0x0, reserved: 0x0, length: 44
Proposal: 3, Protocol id: IKE, SPI size: 0, #trans: 4 last transform: 0x3, reserved: 0x0: length: 12
type: 1, reserved: 0x0, id: AES-CBC
last transform: 0x3, reserved: 0x0: length: 8
type: 3, reserved: 0x0, id: SHA256
last transform: 0x3, reserved: 0x0: length: 8
type: 2, reserved: 0x0, id: SHA256
last transform: 0x0, reserved: 0x0: length: 8
type: 4, reserved: 0x0, id: DH_GROUP_1536_MODP/Group 5
KE Next payload: N, reserved: 0x0, length: 520
DH group: 16, Reserved: 0x0
66 6e 26 c8 86 3a e3 e4 b6 00 4b f6 3c 06 c7 b6
4c b4 a8 38 1d a6 0f e7 54 d5 7a 88 6b 18 81 eb
07 12 ab db 63 2f 2c 3a 59 c2 44 d8 5d 08 a7 9c
9a fc 96 bf 41 98 2c a3 5f 5d 2f 69 d1 ad 19 5f
f1 9d 2d 22 35 0d b5 cd 32 f7 d3 de 00 4e 47 1e
f8 77 b0 1d f4 8b e6 8f eb 3f 4f c6 d6 fc e3 73
5b 39 90 2c f4 72 14 dd ad c0 22 7d e5 5e 74 ff
b3 d8 09 38 98 81 68 ac 2f a8 80 42 71 9e fe 86
eb ea c8 6f b9 32 2f dc a5 c4 57 42 a6 e7 66 f5
c8 6a 6b 45 75 80 0b 41 a0 84 54 a3 fd 54 87 17
51 9e bf cf d0 6d 10 77 34 ed d6 49 97 0e ab 9f
2c 19 cc b9 12 56 c2 70 44 6f c7 39 d2 d0 86 e3
ac ac 1e 4e 5e 60 76 ff 4d 27 a6 9e 95 09 3f b6
6a f9 fc ba 94 98 57 88 a7 57 33 4f e1 ed a5 90
d8 aa d9 00 5c 23 10 d5 87 2c 0c 8b 9d aa 32 1b
a8 f0 99 85 c2 92 f7 d1 d6 6b a1 1a 3d c2 b6 0f
54 40 b1 19 48 29 4d 6a 1c 2c 24 78 66 90 04 72
a2 46 4c d6 85 b9 70 26 e9 3c 7a f3 27 e2 09 fe
71 43 df 9a e3 63 f9 4a 85 ad df 4d 53 5e 29 61
0a 4a 1b ec 84 8f 04 dc b0 29 0d d4 bb 2d 46 cb
2b 80 b2 92 dd dd d2 27 d6 5f dc 8d 4e d6 16 17
e1 5d a0 37 7e b6 bd 7f 49 1b c1 94 16 49 de 55
3b f5 62 e6 40 f4 33 cb 4c bc 8b 0c e8 93 b5 04
25 a9 ef 0b 9f a8 b2 3d 70 e8 65 70 3e 35 8d 78
c3 73 1c 55 a3 18 57 ff 58 1f be c4 31 fc 69 bd
c5 fc ba 64 f0 f7 5e d2 3f aa 80 f7 63 98 44 84
16 e0 67 29 de 23 9d 80 8e c6 86 59 2e 28 79 70
60 b9 5c da 02 ca 7b 50 90 d0 b0 2a 9c d7 f6 f1
83 7e 12 1b 9d 0a 27 3c ef 67 59 61 d6 d4 c5 08
95 97 5f e3 23 b8 04 aa c4 4b 46 56 fe 26 4a 48
6e 34 1f 34 a1 a9 45 f0 b7 97 41 73 35 bc 60 ae
8f e6 80 33 34 24 67 37 dd d8 76 03 dc e4 e0 ec
N Next payload: NOTIFY, reserved: 0x0, length: 36
5d 70 eb 7d 4d 93 6b 28 b4 29 42 7e 41 2d b5 27
b4 e3 c4 63 35 2b 20 cf 2b 44 b8 58 ab da cb 4d
IKEv2-PROTO-7: Parse Notify Payload: NAT_DETECTION_SOURCE_IP NOTIFY(NAT_DETECTION_SOURCE_IP) Next payload: NOTIFY, reserved: 0x0, length: 28
Security protocol id: Unknown - 0, spi size: 0, type: NAT_DETECTION_SOURCE_IP
0e 87 b8 42 85 3f 16 d7 20 0f db 65 af 9d 5f c4
7d 44 ea 43
IKEv2-PROTO-7: Parse Notify Payload: NAT_DETECTION_DESTINATION_IP NOTIFY(NAT_DETECTION_DESTINATION_IP) Next payload: NOTIFY, reserved: 0x0, length: 28
Security protocol id: Unknown - 0, spi size: 0, type: NAT_DETECTION_DESTINATION_IP
50 a7 19 66 8a e8 34 77 d6 1b 96 dc af 24 cd bb
a7 b9 10 a0
IKEv2-PROTO-7: Parse Notify Payload: IKEV2_FRAGMENTATION_SUPPORTED NOTIFY(IKEV2_FRAGMENTATION_SUPPORTED) Next payload: NOTIFY, reserved: 0x0, length: 8
Security protocol id: Unknown - 0, spi size: 0, type: IKEV2_FRAGMENTATION_SUPPORTED
IKEv2-PROTO-7: Parse Notify Payload: Unknown - 16431 NOTIFY(Unknown - 16431) Next payload: NOTIFY, reserved: 0x0, length: 16
Security protocol id: Unknown - 0, spi size: 0, type: Unknown - 0
00 02 00 03 00 04 00 05
IKEv2-PROTO-7: Parse Notify Payload: REDIRECT_SUPPORTED NOTIFY(REDIRECT_SUPPORTED) Next payload: NONE, reserved: 0x0, length: 8
Security protocol id: Unknown - 0, spi size: 0, type: REDIRECT_SUPPORTED
Decrypted packet:Data: 808 bytes
IKEv2-PROTO-7: (1992): SM Trace-> SA: I_SPI=3F08D05F2651EA7E R_SPI=78AFC7271B80A46B (R) MsgID = 00000000 CurState: IDLE Event: EV_RECV_INIT
IKEv2-PROTO-4: (1992): Checking NAT discovery
IKEv2-PROTO-7: (1992): SM Trace-> SA: I_SPI=3F08D05F2651EA7E R_SPI=78AFC7271B80A46B (R) MsgID = 00000000 CurState: IDLE Event: EV_CHK_REDIRECT
IKEv2-PROTO-7: (1992): Redirect check is not needed, skipping it
IKEv2-PROTO-7: (1992): SM Trace-> SA: I_SPI=3F08D05F2651EA7E R_SPI=78AFC7271B80A46B (R) MsgID = 00000000 CurState: IDLE Event: EV_CHK_CAC
IKEv2-PLAT-7: New ikev2 sa request admitted
IKEv2-PLAT-7: Incrementing incoming negotiating sa count by one
IKEv2-PLAT-7: INVALID PSH HANDLE
IKEv2-PLAT-7: INVALID PSH HANDLE
IKEv2-PROTO-7: (1992): SM Trace-> SA: I_SPI=3F08D05F2651EA7E R_SPI=78AFC7271B80A46B (R) MsgID = 00000000 CurState: IDLE Event: EV_CHK_COOKIE
IKEv2-PROTO-7: (1992): SM Trace-> SA: I_SPI=3F08D05F2651EA7E R_SPI=78AFC7271B80A46B (R) MsgID = 00000000 CurState: IDLE Event: EV_CHK4_COOKIE_NOTIFY
IKEv2-PROTO-7: (1992): SM Trace-> SA: I_SPI=3F08D05F2651EA7E R_SPI=78AFC7271B80A46B (R) MsgID = 00000000 CurState: R_INIT Event: EV_VERIFY_MSG
IKEv2-PROTO-4: (1992): Verify SA init message
IKEv2-PROTO-7: (1992): SM Trace-> SA: I_SPI=3F08D05F2651EA7E R_SPI=78AFC7271B80A46B (R) MsgID = 00000000 CurState: R_INIT Event: EV_INSERT_SA
IKEv2-PROTO-4: (1992): Insert SA
IKEv2-PROTO-7: (1992): SM Trace-> SA: I_SPI=3F08D05F2651EA7E R_SPI=78AFC7271B80A46B (R) MsgID = 00000000 CurState: R_INIT Event: EV_GET_IKE_POLICY
IKEv2-PROTO-7: (1992): SM Trace-> SA: I_SPI=3F08D05F2651EA7E R_SPI=78AFC7271B80A46B (R) MsgID = 00000000 CurState: R_INIT Event: EV_PROC_MSG
IKEv2-PROTO-4: (1992): Processing IKE_SA_INIT message
IKEv2-PROTO-7: (1992): SM Trace-> SA: I_SPI=3F08D05F2651EA7E R_SPI=78AFC7271B80A46B (R) MsgID = 00000000 CurState: R_INIT Event: EV_INV_KE
IKEv2-PROTO-4: (1992): Sending invalid ke notification, peer sent group 16, local policy prefers group 14
IKEv2-PROTO-7: Construct Notify Payload: INVALID_KE_PAYLOADIKEv2-PROTO-7: (1992): SM Trace-> SA: I_SPI=3F08D05F2651EA7E R_SPI=78AFC7271B80A46B (R) MsgID = 00000000 CurState: R_INIT Event: EV_ENCRYPT_MSG
IKEv2-PROTO-7: (1992): SM Trace-> SA: I_SPI=3F08D05F2651EA7E R_SPI=78AFC7271B80A46B (R) MsgID = 00000000 CurState: R_INIT Event: EV_TRYSEND
(1992):
IKEv2-PROTO-4: (1992): Sending Packet [To x.x.x.x:500/From x.x.x.x:500/VRF i0:f0]
(1992): Initiator SPI : 3F08D05F2651EA7E - Responder SPI : 0000000000000000 Message id: 0
(1992): IKEv2 IKE_SA_INIT Exchange RESPONSEIKEv2-PROTO-5: (1992): Next payload: NOTIFY, version: 2.0 (1992): Exchange type: IKE_SA_INIT, flags: RESPONDER MSG-RESPONSE (1992): Message id: 0, length: 38(1992):
Payload contents:
(1992): NOTIFY(INVALID_KE_PAYLOAD)(1992): Next payload: NONE, reserved: 0x0, length: 10
(1992): Security protocol id: IKE, spi size: 0, type: INVALID_KE_PAYLOAD
(1992):
(1992): 00 0e
(1992):
IKEv2-PLAT-5: (1992): SENT PKT [IKE_SA_INIT] [x.x.x.x]:500->[x.x.x.x]:500 InitSPI=0x3f08d05f2651ea7e RespSPI=0x0000000000000000 MID=00000000
IKEv2-PROTO-7: (1992): SM Trace-> SA: I_SPI=3F08D05F2651EA7E R_SPI=78AFC7271B80A46B (R) MsgID = 00000000 CurState: INIT_DONE Event: EV_FAIL
IKEv2-PROTO-4: (1992): Failed SA init exchange
IKEv2-PROTO-4: (1992): Initial exchange failed
IKEv2-PROTO-7: (1992): SM Trace-> SA: I_SPI=3F08D05F2651EA7E R_SPI=78AFC7271B80A46B (R) MsgID = 00000000 CurState: EXIT Event: EV_ABORT
IKEv2-PROTO-7: (1992): SM Trace-> SA: I_SPI=3F08D05F2651EA7E R_SPI=78AFC7271B80A46B (R) MsgID = 00000000 CurState: EXIT Event: EV_CHK_PENDING_ABORT
IKEv2-PLAT-7: Negotiating SA request deleted
IKEv2-PLAT-7: Decrement count for incoming negotiating
IKEv2-PROTO-7: (1992): SM Trace-> SA: I_SPI=3F08D05F2651EA7E R_SPI=78AFC7271B80A46B (R) MsgID = 00000000 CurState: EXIT Event: EV_UPDATE_CAC_STATS
IKEv2-PROTO-4: (1992): Abort exchange
IKEv2-PROTO-4: (1992): Deleting SA
IKEv2-PLAT-4: (1992): PSH cleanup
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi there,
Completely missed this post .. sorry for that !
With our telephony team, we went through many software releases on the Alcatel side, and the setup is extremely sensitve to 8068S software version.
Since this setup, we moved production VPN FTDs to 6.6.1 and we have to stop there because 6.7 is removing DH groups needed by our current configuration.
However, telephony team is working on a new 8068S release that should enable more flexibility ...
Regards
/FTH
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: