- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- AnyConnect: Azure AD SAML SSO
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
02-26-2019 07:02 AM - edited 02-21-2020 10:03 PM
Preface: I had a hard time locating documentation for configuring AnyConnect with Azure AD as a SAML IdP - So I took some notes and thought I'd share. I hope it helps someone.
Azure Setup
Login to Azure Portal (https://portal.azure.com)
Click Azure Active Directory
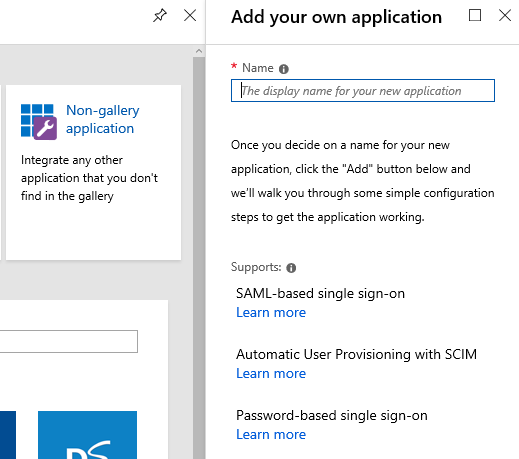
Click Enterprise Applications -> New Application -> Non-Gallery Application
Give it a Name (I'll use AnyConnect-SAML) and click Add at the bottom.
Click the Single sign-on menu Item.
Select SAML
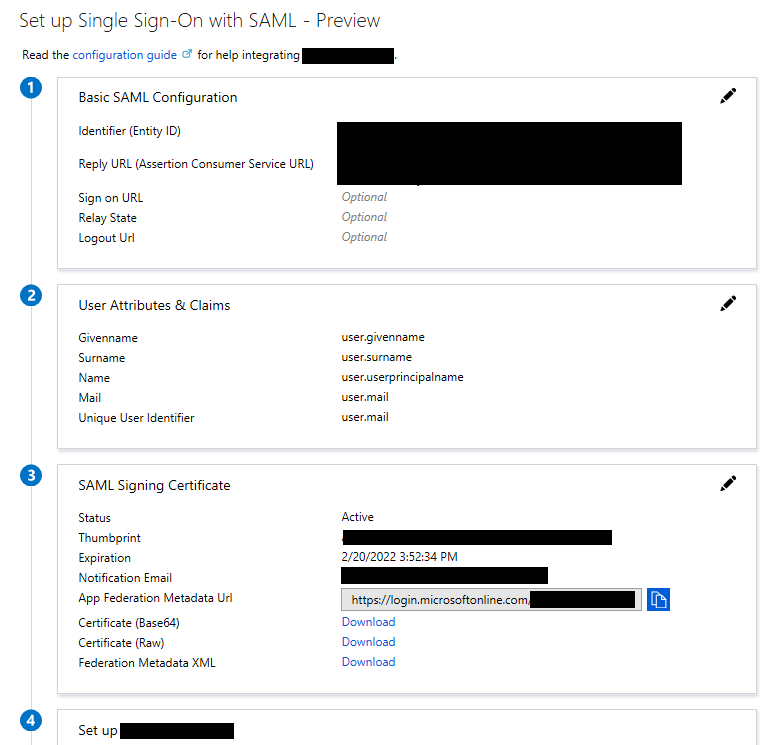
Download the Certificate Base64 from section 3 (We'll install this later)
Make note of the following from Section 4:
Azure AD Identifier - This will be the saml idp in our VPN configuration.
Login URL - This will be the url sign-in
Logout URL - This will be the url sign-out
At this point you have the Data Required to begin configuring the VPN Appliance.
We will need to come back here after configuring the VPN Tunnel-Group and grabbing the metadata.
VPN Configuration - CLI
Alright, we're going to do this on the CLI first, I might come back through and do an ASDM walk-through at another time.
Connect to your VPN Appliance, we're going to be using an ASA running 9.8 code train, and our VPN clients will be 4.6+
Please note there are SAML 2.0 minimum requirements (I believe they are ASA 9.7+ and AC 4.5+ otherwise SAML 2.0 isn't supported or you need to use external browser config… this is outside the scope of this walk-through)
First we'll create a Trustpoint and import our SAML cert.
config t
crypto ca trustpoint AzureAD-AC-SAML
revocation-check none
no id-usage
enrollment terminal
no ca-check
crypto ca authenticate AzureAD-AC-SAML
-----BEGIN CERTIFICATE-----
…
PEM Certificate Text from download goes here
…
-----END CERTIFICATE-----
quit
The following commands will provision your SAML IdP
webvpn
saml idp https://sts.windows.net/xxxxxxxxxxxxx/ (This is your Azure AD Identifier from SSO Section 4 of Azure App)
url sign-in https://login.microsoftonline.com/xxxxxxxxxxxxxxxxxxxxxx/saml2 (Login URL: SSO Section 4 of Azure App)
url sign-out https://login.microsoftonline.com/common/wsfederation?wa=wsignout1.0 (Logout URL)
trustpoint idp AzureAD-AC-SAML
trustpoint sp (Trustpoint for SAML Requests - you can use your existing external cert here)
no force re-authentication
no signature
base-url https://my.asa.com
Now you can apply SAML Authentication to a VPN Tunnel Configuration.
(Configuration of a VPN Tunnel Group or Group Policy is beyond the scope of this document)
tunnel-group AC-SAML webvpn-attributes
saml identity-provider https://sts.windows.net/xxxxxxxxxxxxx/
authentication saml
end
write mem
*Note: There's a feature with the SAML IdP configuration - If you make changes to the IdP config you need to remove the saml identity-provider config from your Tunnel Group and re-apply it for the changes to become effective.
Finishing up with the Azure AD App
We're now ready to grab the meta-data for our tunnel config and finish the Azure application configuration.
You can use a URL similar to below to view the SP metadata.
my.asa.com = the address at which my ASA is reachable
AC-SAML is the tunnel group name configured for SAML auth.
SP Metadata:
https://my.asa.com/saml/sp/metadata/AC-SAML (Also your Entity ID - Azure App Section 1)
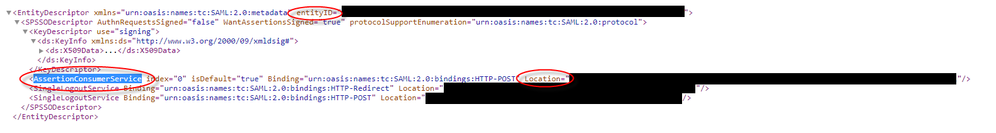
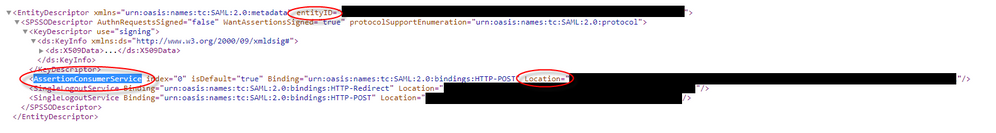
In the metadata XML look for AssertionCustomerService, the Location field in this tag is the Reply URL for the Azure App In SSO Section 1.
Edit the Basic Configuration Section by clicking on the pencil in the top right.
Add the Entity ID & Reply URL
Click Save in the SAML Basic Configuration.
You should now have the basic communication between the ASA and Azure AD wired up.
You may need to add user permissions to the app in Azure AD and conditional access policy for multi-factor, etc.
All beyond the scope of this walk-through, but highly recommended.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
I suppose the real cool part is that when you point AnyConnect's built-in web browser at Azure AD's authentication page you take advantage of all the great security features of Azure AD like Microsoft's MFA using their "Authenticator" app, their "Conditional Access", and their "Azure AD Identity Protection". Also since the authentication happens in Azure AD you don't need an on premise MFA server you use theirs as a service.
SSO is the other obvious cool part. Once user's connect to VPN they have a SAML token for Azure AD and can use that to access any other resources secured by Azure AD authentication. So they get SSO to outlook.office.com, any Azure AD App Proxy pages or other web applications you've published from Azure AD.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Ah, yes, that was exactly what I was trying to understand.
I am being asked to setup SSO using AnyConnect. At this point, we don't use outlook.office.com, any Azure AD App Proxy pages or other web applications published in Azure, so I was getting really confused as to how this would be beneficial to our company.
Thanks!
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Can someone confirm if this solution requires AnyConnect Apex license and the WebVPN feature? Does this process only secure the WebVPN page with Azure MFA? Is it possible to apply this to AnyConnect client based connections?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
I have a few dumb questions. In the configure Basic SAML portion, where does one find the Identifier (entity ID) and the reply URL? If we have already generated the certificate, created the trustpoint, and uploaded it to the ASA without the Identifier and reply URL being configured will we need to regenerate the cert and reupload it?
Thank you,
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@bartlettdn @he enityID is just the name you give the Enterprise Application in Azure AD. It has to be the same in Azure AD and on your ASA, but it can be anything you want.
The reply URL is gathered from the XML response when you visit your ASA in a browser at this example URL:
SP Metadata:
https://my.asa.com/saml/sp/metadata/AC-SAML (Also your Entity ID - Azure App Section 1)
In the metadata XML look for AssertionCustomerService, the Location field in this tag is the Reply URL for the Azure App In SSO Section 1.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi
I have a customer(at about 100 remote workers) wanting to use Azure AD as idp and is looking for a solution like this. I dont have a lot of Cisco experience and need advice on which appliance to look at. Is this supported on all ASA Firewalls, how about FirePower series and so on?
I appreciate any advice.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Here a manual (with many of the restrictions of FTD) for VPN on FTD: https://www.cisco.com/c/en/us/support/docs/network-management/remote-access/212424-anyconnect-remote-access-vpn-configurati.html
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
I can confirm that FirePower with FTD OS doe NOT support Azure MFA integration. FTD does not support SAML yet, which is required. However I have heard you can still integrate AzureMFA with FTD AnyConnect if you use an intermediate RADIUS server that support Azure integration. You have several options in the RADIUS space, such as Cisco ISE, Microsoft NPS. Just make sure what ever RADIUS you pick support Azure integration (SAML).
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
I have added Cisco ISE into the mix as well.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
We currently have Windows NPS server assigning group policy through RADIUS, based on AD security group membership. We are testing Azure MFA with NPS extension installed on the NPS server. I wonder if the Azure AD SAML SSO setup can replaces the NPS server. Are we better off with the NPS server?
We also have DAP enforcing policies based on group-policy and hostscan posture assessment of the remote client. I hope this setup will continue working since this happens after the MFA authentication.
I will appreciate your reply.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
For those who need it/asked about it, @lynne.meeks commented here with the solution to applying different group policies through LDAP Attribute Mapping after switching to SAML from LDAP:
In short, in ASDM, in your Connection Profile, go to Authorization and select your LDAP Server Group. As long as your LDAP Server Group is set to use UPN as the Naming Attribute, then the LDAP Mapping will work as normal. The CLI instructions are also there. This is assuming that you previously used LDAP Attribute Mapping with LDAP Authentication with your AnyConnect Profile to assign different Group Policies, and switched it over to using SAML authentication with the instructions on this thread from the OP @Sloanstar
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thank you for this great post!
Unfortunately it does not work for me. I have some issues:
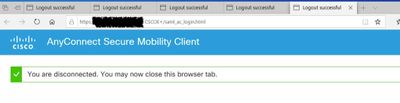
1. User (Windows 10) connects via AnyConnect (Version 4.8) to Cisco ASA
2. Default browser opens and redirection to O365 portal page to login
3. User enters Username/Password and then MFA follows
4. The browser shows a page from AnyConnect Secure Mobility Client with message "You are disconnected. You may now close this browser tab"
5. Then the browser opens a new tab with the same page mentioned at 4 again and again in a loop until the user cancels the connection attempt.
On the Azure App the login protocols it shows successful authentication of the user. It seems that the browser does not forward the authentication result back to the Cisco ASA to progress the login attempt.
Anyone faced the same issue or have any clue?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi all,
Does anyone know if we can use one(1) Enterprise Application with multiple "Entity ID" & "Reply URL" pairs ?
For example, if we have the same remote-access tunnel group named "CompanyVPN" in three(3) different locations (USA/EU/APAC), can we have one(1) unified Enterprise Application in order to authenticate the users instead of three(3) individual Apps (one per location) ?
Something like:
https://<USA>.domain.com/saml/sp/metadata/CompanyVPN
https://<USA>.domain.com/+CSCOE+/saml/sp/acs?tgname=CompanyVPN
https://<EU>.domain.com/saml/sp/metadata/CompanyVPN
https://<EU>.domain.com/+CSCOE+/saml/sp/acs?tgname=CompanyVPN
https://<APAC>.domain.com/saml/sp/metadata/CompanyVPN
https://<APAC>.domain.com/+CSCOE+/saml/sp/acs?tgname=CompanyVPN
I am concerned though by the "Default" option that is mandatory when adding "Entity ID" & "Reply URL" into the Enterprise Application.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: