- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- AnyConnect MTU
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
on 10-06-2014 06:38 AM
The MTU value for VPN Client or SVC Client, used to connect to the VPN network, was set to 1300 bytes.With AnyConnect Client, the initial value is set to 1406 bytes. While it considers the transfer efficiency, various individual customizations are included to make the Settings more Complex.This Document Describes Basic Settings and Operations of AnyConnect MTU, as well as the major failure Cases Associated with it. This Article IS based on the operation verification of ASA 9.1 (4) and AnyConnect 3.1.05152.Please Note that this unofficial content is merely an explanation of the current implementation, and does not guarantee that it will be the same operation in future.
Contents 2. AnyConnect MTU Operation Overview 3. Case Study |
1. Configure basic settings on the AnyConnect MTU
1-1. Settings from DfltGrpPolicy and Custom Group Policy
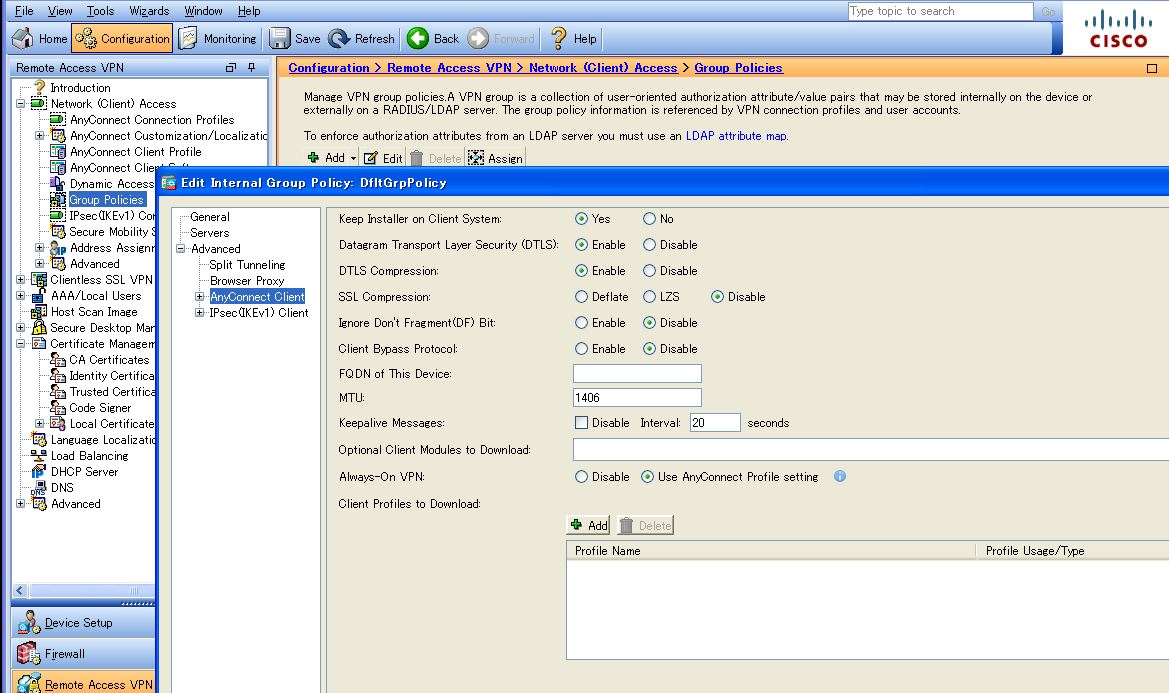
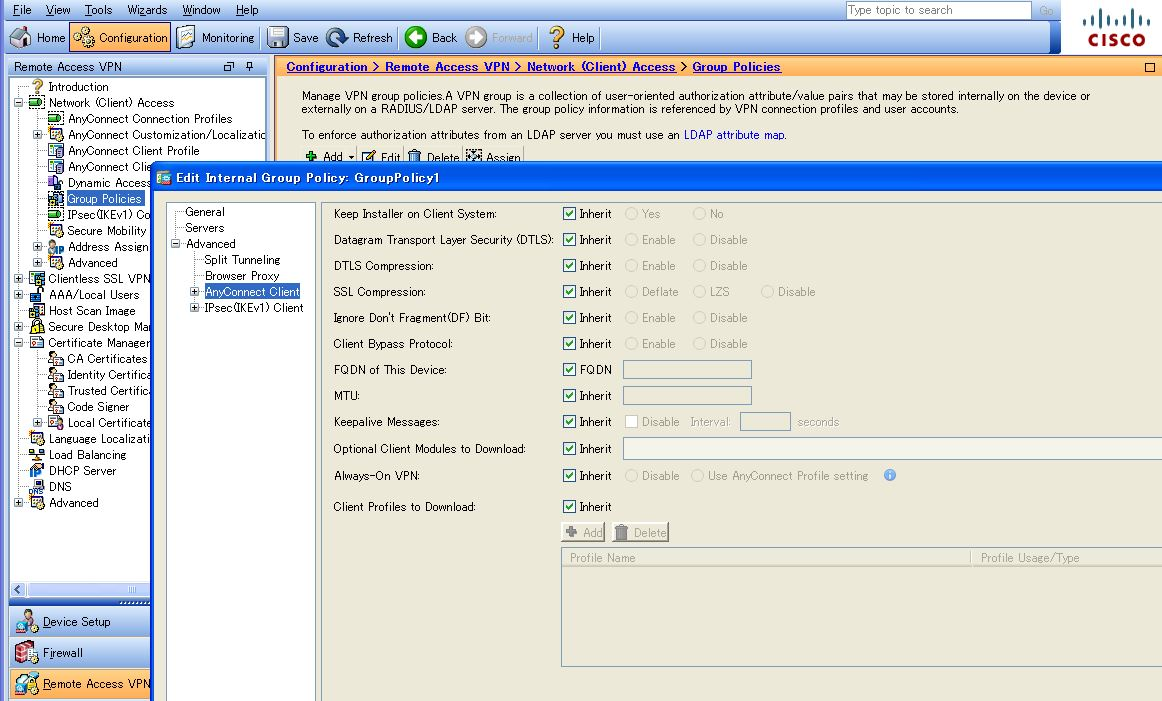
To configure a different MTU value from DfltGrpPolicy to the Custom Group Policy, access AnyConnect Client from ASDM as follows: [Configuration]> [Remote Access VPN]> [Network (Client) Access]> [Group Policies]> [Edit Target Custom Group policy]> [Advanced]> [AnyConnect Client]. Inherit IS checked as the initial state, as shown in the figure Below. This Means That the MTU setting value of DfltGrpPolicy Will BE Inherited.To Apply an Original MTU value to the Custom Group Policy, uncheck the Inherit field and enter the value you want to configure.
|
1-2. Settings Using Radius Attribute
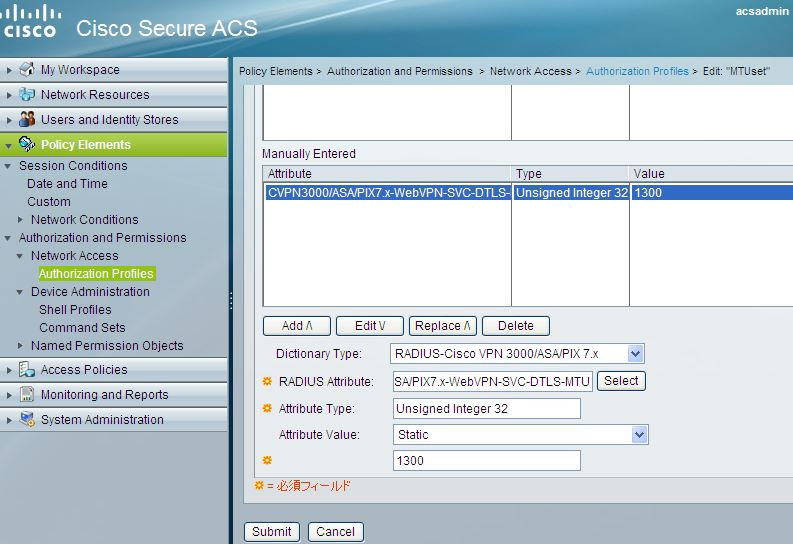
Here is a configuration example of adding an attribute using Cisco Secure ACS 5.x, provided that the authentication server for AnyConnect users uses the Radius.
2. Go to [Users and Identity Stores]> [Internal Identity Stores]> [Users] .Select target users and click [Edit]. Peg the Group created at step 1 to [Identity Groups]. 3. Go to [Policy Elements]> [Authorization and Permissions]> [Network Access]> [Authorization Profiles] and create a Profile.See the figure below for the configuration example of an attribute. 4. Go to [Access Policies]> [Access Service] (used ASA) .Click [Authorization] and create an Authorization Policy.Set the Group created at step 1 as Identity Groups to Conditions. Select the Profile created at step 3 as Authorization Profiles.
In this configuration example, MTU 1300 will be applied only to the users stored in the Group created at step 1. |
Note: You can configure MTU per user by selecting [VPN Policy]> [AnyConnect Client] even when you are using a local user database.
2. AnyConnect MTU Operation Overview
2-1. Calculating the Overhead (DTLS)
|
2-2. Reflecting to AnyConnect VA
When the connection starts using AnyConnect, the MTU value applied to the AnyConnect virtual adapter (VA, hereinafter) will be negotiated between AnyConnect and ASA. Please note that the MTU value configured by DfltGrpPolicy or Custom Group Policy will not be automatically reflected.The MTU value of the physical NIC of the PC will also be considered as the element of determining the MTU.To be specific, If AnyConnect MTU <MTU of physical NIC - Overhead ,
Processing CSTP header line: 'X-CSTP-Protocol: Copyright (c) 2004 Cisco Systems, Inc.'
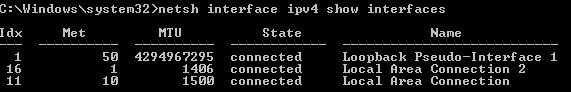
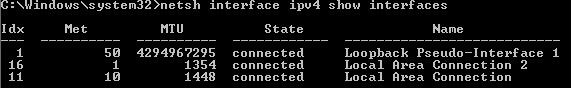
By applying the calculation formula of 2-1, you can see that the AES block size is 16 and the Padding is 3.As a result, the overhead is 82 and the value 1418, computed by subtracting 82 from 1500, is the MTU value .However, please Remember That the maximum value for AnyConnect configurable MTU IS 1406.Since 1418 IS Larger than 1406, it Will BE overridden by 1406, Which IS the MTU value assigned to the AnyConnect Client VA. Shown Below IS the output of the assigned MTU Confirmed by Windows 7. * Local Area Connection 2 IS the AnyConnect VA.
Here is another example.Shown below is a debug output example when the MTU of physical NIC is 1448, AnyConnect MTU is 1406, with DTLS enabled using aes128-sha1. Processing CSTP header line: 'X-CSTP-Protocol: Copyright (c) 2004 Cisco Systems, Inc.' By applying the calculation formula of 2-1 to this example again, you can see that the AES block size is now 16 and the Padding is 15.1354, which is computed by subtracting the overhead value 94 from the MTU of physical NIC, is the MTU Calculated.Since 1354 IS Smaller than 1406, 1354 IS the MTU assigned to the VA. Shown Below IS the output of the assigned MTU Confirmed by Windows 7. * Local Area Connection 2 IS the AnyConnect VA.
The table below contains reference information.This is how the MTU value will be assigned to the AnyConnect VA while decreasing the MTU of physical NIC. The overhead calculation of DTLS turned out as expected.
* 1 The value subtracting the overhead is 1418. However, it is larger than 1406, so the MTU is 1406. The MTU of DTLS Will BE applied to VA in the environment USING DTLS. Therefore, this Article Focuses on the DTLS Operations.In Addition, the overhead Calculation of TLS / SSL IS shown in black in the debug output Above. the When you See the debug output described above including the MTU value of TLS, you can see that there are two scenarios: 1. the MTU of DTLS and TLS will be overridden by the setup value of AnyConnect MTU, and then both of them are the same value; 2. DTLS and TLS Have Different MTU values Respectively. Latter In the Scenario, if the connection method WAS switched from DTLS to TLS VPN During Communication, the MTU value of TLS Will BE reassigned to the MTU of VA. THUS, a reconnect with AnyConnect and OCCURS the Communication Will BE affected Momentarily. On the Other hand, WHEN the MTU value of DTLS and TLS IS the same, as shown in the Former Scenario, the MTU Reassignment Will not Occur even in Case of a fallback. Situation In this reconnect a Will not occur. |
2-3. MTU Discovery Process
AnyConnect Client sends out the maximum transferable DPD ping from VA to ASA once DTLS has been established.As a result, in the case of no response received from ASA, AnyConnect Client repeats the operation of executing DPD ping after reducing the MTU size by 32 bytes . the When it RECEIVEs a response from ASA, it Reapplies the size Received at That point as the optimal MTU to VA. This implementation IS Introduced at the Following Links: Optimal MTU (OMTU) Http://Www.Cisco.Com/c/ en / us / td / docs / security / vpn_client / anyconnect / anyconnect31 / administration / guide / anyconnectadmin31 / ac13managemonitortbs.html # pgfId-1058579 MTU Automatically Adjusted the When Using DTLS
This function IS Implemented with DTLS to TLS only and IS not Applicable to IKEv2.As pointed out in the release Note Above, it IS recommended for IKEv2 to DECREASE the MTU value as needed for the Adjustment. OMTU Note That Works only on the network where the large-size packets are discarded without being fragmented on the path.No adjustment will be made in the network where DPD ping packets are fragmented on the path, and will reach ASA because ASA returns a response.
|
3. Case Study
3-1. A Reconnect Occurs Only After One Minute Following Connection to AnyConnect
[Phenomenon Overview] A reconnect occurs only after one minute following connection to AnyConnect.A reconnect will not occur again, but if you connect to AnyConnect again after disconnecting, the same phenomenon persists.Although the AnyConnect status shows Connected during that time, the actual communication is not established until a reconnect occurs.
[Cause] The following article has been released as an example of where this happens frequently. http://www.cisco.com/en/US/products/ps10884/products_tech_note09186a0080c1fadf.shtml
Make sure that there is no device, such as a firewall, configured on the path that prevents DTLS from being established (blocks UDP 443), then secure the accessibility of UDP 443. As a temporary workaround, prepare a Group Policy that does not use DTLS and apply users that are affected to that group. You can also disable DTLS per user if a local user database is used for authenticating the users. Note that this phenomenon will not occur when the MTU value is the same for TSL and DTLS, because the MTU will not be re-applied to VA during the DTLS / TLS switchover process. Therefore, another effective workaround would be configuring the settings that the MTU of DTLS and TLS will be overridden by the value of AnyConnect MTU (in other words, set a smaller value for AnyConnect MTU).
A case where a reconnect occurs
Related InformationOriginal Document: https://supportforums.cisco.com/ja/document/12067766
|
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
A very nice informative documents and clears much of my understadning. However the last para is not correct as the TLS and DTLS MTU are same 1300 so no reconnect is requires in this case where as from the chines version (Original Document:) it is different and reconnect is necessary.
A case where a reconnect occurs
overide computed tls-mtu = 1327 with conf-mtu = 1300
DTLS enabled for intf = 2 (outside)
overide computed dtls-mtu = 1306 with conf-mtu = 1300
tls-mtu = 1300 dtls-mtu = 1300 [they are the same] see chines version to clear this.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello,
I have same issue where users are reconnecting after 1 min around.
A case where a reconnect occurs
overide computed tls-mtu = 1327 with conf-mtu = 1300
DTLS enabled for intf = 2 (outside)
overide computed dtls-mtu = 1306 with conf-mtu = 1300
tls-mtu = 1300 dtls-mtu = 1300
How I can validate above and where to change. I am looking for a workaround for a specific Group of VPN Users , so I want to fix from endpoint side.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello,
Want to ask what if the host's NIC physical mtu changed to 576? Tested in that case, the anyconnect client reconnects stops. However, based on calculation the TLS and DTLS mtu should still be different per explanation above and should still causing reconnect... Is physical NIC 576 a special case in the anyconnect client?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Issue was resolved while configuring or allowing DTLS ( udp 443 ) at Pass Through Firewall. DTLS is by default enabled on VPN Firewall. Here my Problem was upstream Firewall was blocking DTLS.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: