- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- ASA Anyconnect IKEv2 configuration example
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
10-10-2011 10:37 AM - edited 08-28-2017 02:30 AM
Introduction
Secure VPN remote access historically has been limited to IPsec (IKEv1) and SSL. These were supported using the "Cisco VPN client" for IPsec based VPN and Anyconnect for SSL based VPN. Each of those products only supported their own protocol however with the introduction of Anyconnect Secure Mobility Client 3.0, the client can now use IPsec (IKEv2) or SSL for the transport of the VPN connection.
For SSL based configuration of Anyconnect reference http://www.cisco.com/en/US/products/ps6120/products_configuration_example09186a00808efbd2.shtml
The remainder of this document will discuss the steps to configure an ASA to support Anyconnect clients using IKEv2.
Requirements
1) ASA running version 8.4.1 or later
2) Anyconnect Secure Mobility Client 3.0 or later
3) License for Anyconnect Peer (either "AnyConnect Essentials" or "AnyConnect Permium Peers")
It is possible to configure the setup either through ASDM or via the CLI. Using the former is the easiest and is listed below along with the CLI commands that are generated.
Configure via ASDM
1) Start ASDM
2) Wizards -> VPN Wizards -> AnyConnect Wizard
3) Configure a name for the tunnel group - RemoteAccessIKEv2
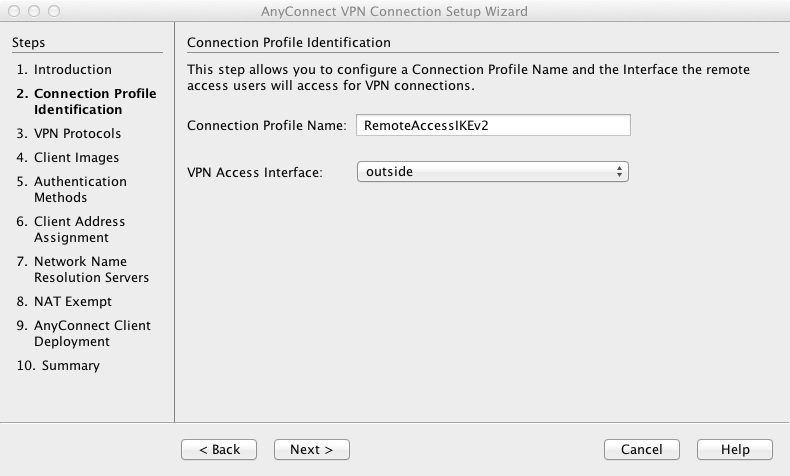
4) Configure the connection protocols. It is possible to have both SSL and IPsec connections on the same tunnel group however in this example only IPsec will be selected.
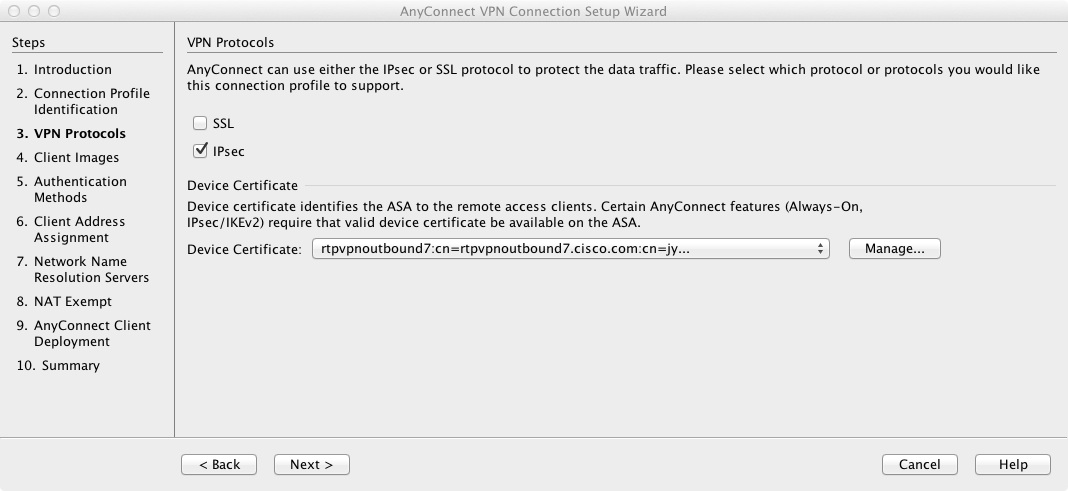
5) Upload Anyconnect images to the ASA for each platform that need supporting (Windows, Mac, Linux)
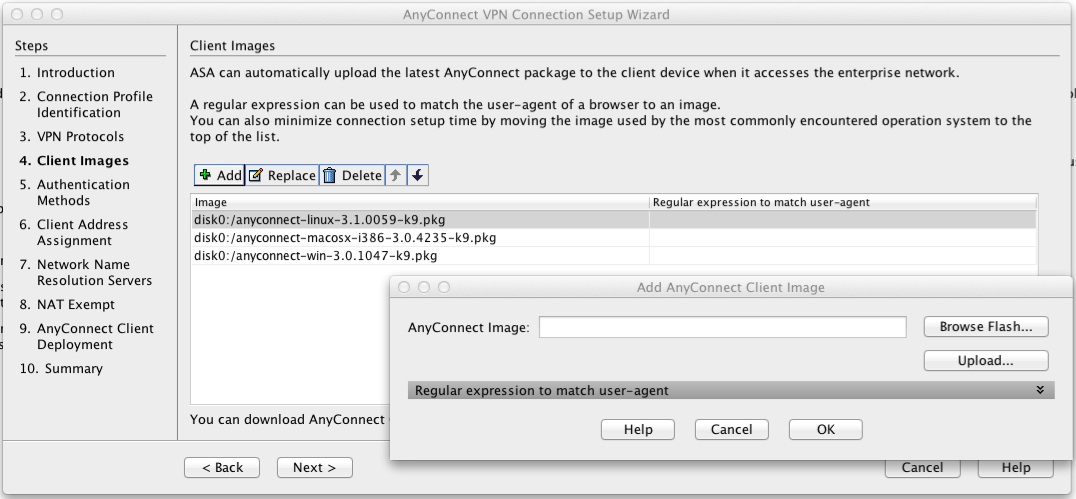
6) Configure the user database. If using the Local database users can be added/removed here. If using a remote authentication server configure a new "AAA Server Group" by clicking on the "New..." button.
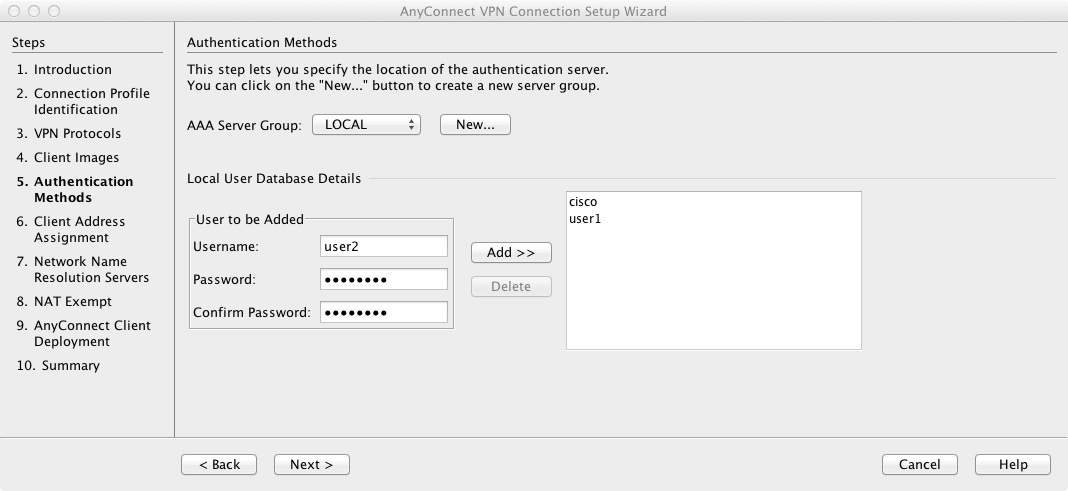
7) Create a pool of addresses that will get assigned to the vpn clients.
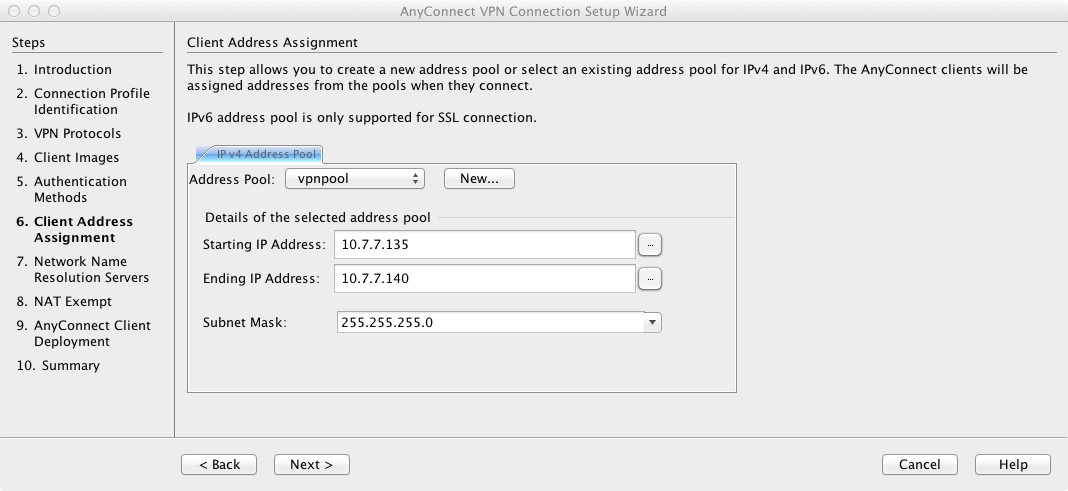
8) Define the default domain name for the virtual adapter on the client and the internal DNS servers
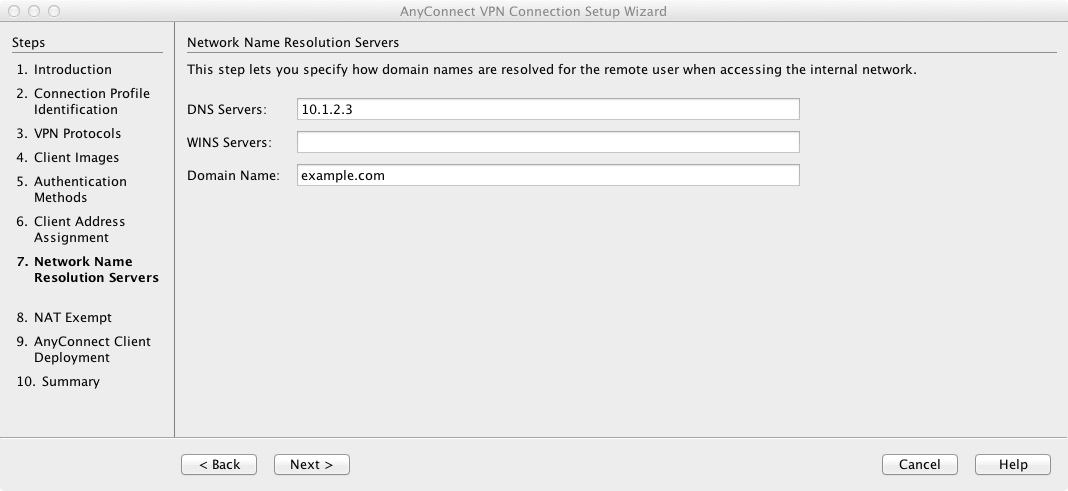
9) Allow the VPN traffic to be exempted from NAT when accessing the internal network.
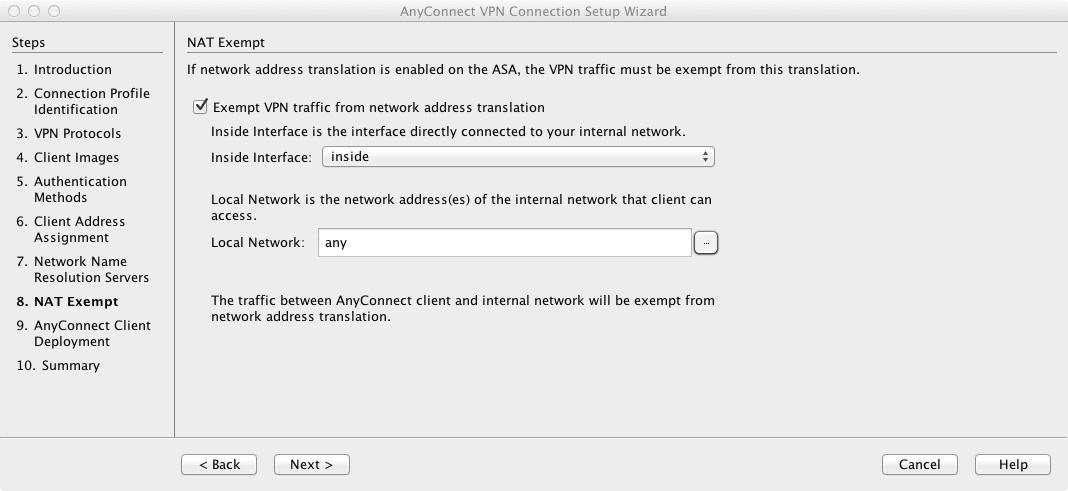
10) Turn off Web Launch. This is optional and would require the client to be pre-deployed (much in the same fashion as the Cisco VPN client).
If you wish to keep Web Launch on then SSL must also be checked on step 3.
11) Save and Apply the configuration
At this point the ASA will have these commands added:
CommandsFunction
crypto ikev2 policy 1 encryption aes-256 integrity sha group 5 2 1 prf sha lifetime seconds 86400 crypto ikev2 policy 10 encryption aes-192 integrity sha group 2 prf sha lifetime seconds 86400 crypto ikev2 policy 20 encryption aes integrity sha group 2 prf sha lifetime seconds 86400 crypto ikev2 policy 30 encryption 3des integrity sha group 2 prf sha lifetime seconds 86400 crypto ikev2 policy 40 encryption des integrity sha group 2 prf sha lifetime seconds 86400 crypto ikev2 enable outside client-services port 443 crypto ikev2 remote-access trustpoint rtpvpnoutbound7 | This is adding the IKEv2 Policies. It also specifiies the certificate the ASA uses for IKEv2. |
crypto ikev2 enable outside client-services port 443 ssl trust-point rtpvpnoutbound7 outside |
Enabling client-services on the outside interface. It also specifies the certificate the ASA uses for SSL. client-services run over SSL. |
crypto ipsec ikev2 ipsec-proposal DES protocol esp encryption des protocol esp integrity sha-1 md5 crypto ipsec ikev2 ipsec-proposal 3DES protocol esp encryption 3des protocol esp integrity sha-1 md5 crypto ipsec ikev2 ipsec-proposal AES protocol esp encryption aes protocol esp integrity sha-1 md5 crypto ipsec ikev2 ipsec-proposal AES192 protocol esp encryption aes-192 protocol esp integrity sha-1 md5 crypto ipsec ikev2 ipsec-proposal AES256 protocol esp encryption aes-256 protocol esp integrity sha-1 md5 | These define the transform sets that IKEv2 can use. |
crypto map out-map 65000 ipsec-isakmp dynamic out-dyn-map crypto map out-map interface outside crypto dynamic-map out-dyn-map 10 set ikev2 ipsec-proposal AES256 AES192 AES 3DES DES | This configures the crypto map to use the IKEv2 transform-sets |
webvpn anyconnect image disk0:/anyconnect-linux-3.1.0059-k9.pkg 1 anyconnect image disk0:/anyconnect-macosx-i386-3.0.4235-k9.pkg 2 anyconnect image disk0:/anyconnect-win-3.0.1047-k9.pkg 5 anyconnect profiles RemoteAccessIKEv2_client_profile disk0:/RemoteAccessIKEv2_client_profile.xml anyconnect enable | This configures the ASA to allow Anyconnect connections and the valid Anyconnect images. If Web Launch is allowed it will install the clients on the computers on first connect.
In addition there is the programming of the profile that will be used by the client. |
group-policy GroupPolicy_RemoteAccessIKEv2 internal group-policy GroupPolicy_RemoteAccessIKEv2 attributes vpn-tunnel-protocol ikev2 dns-server value 10.1.2.3 wins-server none default-domain value example.com webvpn anyconnect profiles value RemoteAccessIKEv2_client_profile type user | This configures the group-policy to allow IKEv2 connections and defines which Anyconnect profile for the user. |
ip local pool vpnpool 10.7.7.135-10.7.7.140 mask 255.255.255.0 | This defines a pool of addresses. |
tunnel-group RemoteAccessIKEv2 type remote-access tunnel-group RemoteAccessIKEv2 general-attributes default-group-policy GroupPolicy_RemoteAccessIKEv2 address-pool vpnpool tunnel-group RemoteAccessIKEv2 webvpn-attributes group-alias RemoteAccessIKEv2 enable | This ties the pool of addressess to the vpn connection. |
object network NETWORK_OBJ_10.7.7.128_28 subnet 10.7.7.128 255.255.255.240 | Defines an object (will be used later) |
nat (inside,outside) 8 source static any any destination static NETWORK_OBJ_10.7.7.128_28 NETWORK_OBJ_10.7.7.128_28 | Defines the NAT rule that exempts the vpn traffic from being NATted. |
<?xml version="1.0" encoding="UTF-8"?> <AnyConnectProfile xmlns="http://schemas.xmlsoap.org/encoding/"> <ServerList> <HostEntry> <HostName>vpn.example.com (IPsec)</HostName> <HostAddress>203.0.113.10</HostAddress> <PrimaryProtocol>IPsec</PrimaryProtocol> </HostEntry> </ServerList> </AnyConnectProfile> | This is the contents of the profile that gets written the ASA flash as RemoteAccessIKEv2_client_profile.xml |
Testing
If Web Launch was configured, on the client open up a web-browser and log into the ASA. The client will self download and install. It will connect with TLS/DTLS first. If you disconnect, quit the client, then restart the client there will be a drop down entry for the IKEv2 connection. Select it and the client will initate using IKEv2.
If Web Launch was not configured it will be necessary to manually install the client on the computer and to copy the
RemoteAccessIKEv2_client_profile.xml into the profile directory. Start the client and select the drop down. The connection will be initiated using IKEv2.
The packages to download are :
OSPackage
| Windows | anyconnect-win-X.Y.ZZZZ-pre-deploy-k9.iso |
| Mac OS X | anyconnect-macosx-i386-X.Y.ZZZZ-k9.dmg |
| Linux | anyconnect-predeploy-linux-X.Y.ZZZZ-k9.tar.gz or anyconnect-predeploy-linux-64-X.Y.ZZZZ-k9.tar.gz |
The profile locations are:
OSLocation
| Windows XP | %ALLUSERSPROFILE%\Application Data\Cisco\Cisco AnyConnect Secure Mobility Client\Profile |
| Windows Vista/7 | %PROGRAMDATA%\Cisco\Cisco AnyConnect Secure Mobility Client\Profile |
| Mac OS X | /opt/cisco/anyconnect/profile/ |
| Linux | /opt/cisco/anyconnect/profile/ |
Caveats and Implemention notes
Certificates:
- Although RFC 4809 states the Extended Key Usage (or the lack of) extension within the client and server certificate should not prevent successful IKE establishment the ASA has a set of requirements:
1) All client certificates must have the EKU extension with the value of "client authentication".
2) The ASA certificate must have the EKU extension with the value of "server authentication"
The ASA is deviating from the RFC in a more conservative manner. It was chosen to be stricter, because if EKU were ignored, then it would be possible to build a IKE connection using a certificate granted soley for the use of "email signing" (or any other usage). This effectively defeats the security controls added in PKI.
- Currently if client-services is used the certificate for SSL and IKEv2 must reference the same trustpoint. This is documented in CSCty43072 and will be fixed in AnyConnect version 3.1.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thanks for this excellent description of implementing IKEv2.
If I made a change on the XML file on the ASA and I force the client to reconnect, I receive the error message below:
***
Function: CHttpSessionWinInet::handleServerCertErrors
File: ..\Common\Utility\HttpSession_wininet.cpp
Line: 1382
The server certificate for the secondary connection is different than the (trusted) server certificate used for the primary connection. The server certificate for the secondary connection is not trusted.
Function: CManifestMgr::GetFile
File: .\ManifestMgr.cpp
Line: 510
Invoked Function: CFileDownloader::DoDownload
Return Code: -25821172 (0xFE76000C)
Description: FILEDOWNLOADER_ERROR_UNTRUSTED_CERTIFICATE
Failed to download from https://ASA-Public-IP/CHCHE/stc/profiles/nas_cp_default_client_profile.xml
to C:\Users\fhz\AppData\Local\Temp\9725.tmp\nas_cp_default_client_profile.xml
Failed to download AnyConnect VPN Profile because AnyConnect cannot confirm it is connected to your secure gateway. The local network may not be trustworthy. A VPN connection cannot be established.
***
There are two questions I have for the implementation, and my some one can explain this.
- Will the update only work if the FQDN for the ASA is in public DNS and also in the certificate. (I have in the webvpn configuration the FQDN none configured)
- What will the AnyConnect Client change on the clients hosts file
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Rene,
As you may have figured out. When you change the profile on the ASA the client detects that the local profile is different and it will try to grab a new copy. This is done over https/ssl using the "client services" feature. This obviously means that the ASA has a valid SSL certificate installed and configured to be used.
Can you confirm that the same trustpoint is configured for "ssl trustpoint" command as the "crypto ikev2 remote-access trustpoint" command.
1) The certificate used for the SSL should be the address of the ASA. This would be good to have it set to an FQDN. I believe this would be a necessity if getting a certificate from a 3rd party (like Verisign or GoDaddy) as they will only issue certs on a fqdn (and not IP address).
2) I do know that the Anyconnect does change the hosts file but don't actually know what it changes. Perhaps if you are interested make a copy before and after connecting. That way you can compare the differences. I believe it would only add an entry for the fqdn of the ASA.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi there .... I have followed these instructions, but I can't connect using IKEv2 ... my client connects to ASA and VPN is established, but all over SSL, not IKEv2
What can be wrong about it?
Also, I've found that the asdm client profile editor is different to the profile editos I got install on my PC through the annyconnect ISO. On ASDM, when I define the server list, it doesn't give me the option to select I want to use IPSEC
can you point me in any direction regarding what I'm doing wrong?
Thanks in advance.
I've attached the config snapshot of my ASA regarding IKEv2
crypto ikev2 policy 10
encryption aes-256
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 20
encryption 3des
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 remote-access trustpoint ASDM_TrustPoint2
crypto ipsec ikev2 ipsec-proposal AES256
protocol esp encryption aes-256
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal 3DES
protocol esp encryption 3des
protocol esp integrity sha-1 md5
crypto dynamic-map External_dyn_map 1 set ikev2 ipsec-proposal AES256 3DES
crypto dynamic-map External_dyn_map 1 set security-association lifetime seconds 28800
crypto dynamic-map External_dyn_map 1 set security-association lifetime kilobytes 4608000
crypto map External_map 65535 ipsec-isakmp dynamic External_dyn_map
group-policy GroupPolicy_TestIKEv2 internal
group-policy GroupPolicy_TestIKEv2 attributes
wins-server none
dns-server value 192.168.208.29 192.168.208.32
vpn-tunnel-protocol ikev2
webvpn
anyconnect profiles value TestIKEv2 type user
tunnel-group TestIKEv2 general-attributes
address-pool SSLVPNCLIENTPOOL
authentication-server-group LDAP_servers LOCAL
authorization-server-group LOCAL
default-group-policy GroupPolicy_TestIKEv2
tunnel-group TestIKEv2 webvpn-attributes
group-alias IKEv2Test enable
tunnel-group TestIKEv2 ipsec-attributes
ikev1 pre-shared-key *****
tunnel-group TestIKEv2 general-attributes
address-pool SSLVPNCLIENTPOOL
authentication-server-group LDAP_servers LOCAL
authorization-server-group LOCAL
default-group-policy GroupPolicy_TestIKEv2
tunnel-group TestIKEv2 webvpn-attributes
group-alias IKEv2Test enable
tunnel-group TestIKEv2 ipsec-attributes
ikev1 pre-shared-key *****
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Larry,
The editor on ASDM uses the xml schema pulled from the anyconnect package that exists on the ASA. You will need to make sure anyconnect 3.0 is uploaded to the ASA. Once that is done close ASDM and then open it up again. You should be able to see the drop down after that.
-Jay
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
thanks for the answer ... to be clear ... just loading annyconnect on ASA is enough, or should I publish it through configuration?
I am not ready for my users to get annyconnect 3.0 downloaded. We are still using 2.5 as standard solution. I just want to test 3.0 before making it the standard option for everyone
Thanks
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Larry,
The anyconnect image needs to be selected for ASDM to pick it up the schema. If you use the editor within the ISO that you downloaded you can create the xml file. After that you can manually transfer it up to the ASA and then apply it to the group policy. The ASDM does the xml validation when trying to configure it. This process doesn't happen when doing it manually in the command line.
-Jay
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thanks Jay ... I managed to get it working doing everything from CLI, instead of using ASDM, without uploading the distribution package for Anyconnect 3.0.5
I see tunnel now to be built using IKEv2 instead of SSL
I have a new question now, though
In the past, when using IKEv1 (with Cisco VPN Client), each connection consume a license of "Other VPN Peers"
Now, even using IKEv2, it consumes a license for Annyconnect Premium, which is same license consume when tunnel is built using SSL
a) what's the benefit of building IKEv2 tunnel over SSL if license used is the same?
b) what's the difference between Anyconnect Essentials and Anyconnect Premium licenses?
Thanks
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Larry,
A) You are correct, the license used is the same. Generally for most enterprise deployments SSL is better and more flexible. The IKEv2 feature was primarily added not as a migration path from the EzVPN client but to meet many customer's legal/PCI/HIPPA/etc requirements that stated IKEv2 must be used. As you can tell it is a little more complex to setup. Unless you have a specific requirement to use IKEv2 it is probably better just to stick with TLS/SSL.
B) The Anyconnect Essentials license will just allow you use Anyconnect (for IKEv2 or TLS/DTLS). The other features like clientless (Portal based) and CSD will be disabled. This was made as cheap license for people who were only using the ASA as VPN tunnel termination points. The Premium licenses are per-seat where-as the Essential license will allow upto the hardware limit.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thanks Jay for tremendous help!!!
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Any way to setup AnyConnect on a 5585-X without having to get a cert from a CA? Would really, really prefer self-signed ...
Steve
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Steve,
You can absolutely use a self-signed certificate for AnyConnect. The problem, however, you will see error messages when trying to connect. The error messages will say that the server is untrusted since the issuer is not within the computer's browser cert store. We recommend a 3rd party cert (or an internal PKI server whose CA cert has been pre-deployed) so that the user doesn't see the security error messages.
-Jay
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thanks, Jay!
We understand about the nagging warnings. Might someday get a "real" cert, but right now I'm just trying to learn AnyConnect and don't have time to get a real one.
I can't seem to find the ADSM option to create a self-signed cert. Also spent several hours searching Cisco docs with no luck. Can you point me in the correct direction? We are running 8.4.(2)13 and ASDM 6.4(5)204
Also, I could not find the ASDM option to create the Certificate Signing Request for the day when we want to get a "real" cert. Again, this seems to be buried and can't find it in the docs. By contrast, creating the CSR was easy in ACS 5.3 ...
Steve
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Steve, the closest thing to what you're looking for is:
http://www.cisco.com/en/US/products/ps6120/products_configuration_example09186a00808efbd2.shtml
This is for older ASA versions as well as AC versions, but the process shouldn't have changed that much. We're working on getting these older docs updated to reflect the changes in the more recent code versions.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thanks!
Atri, seeing as how you are MUCH better than I am at finding things in the Cisco docs, could I impose on you one more time ... is this info also available for the ASDM? I'm comfortable with CLI, but my brain has mostly converted to >= 8.3 mode and with the GUI, there is less need to worry about pre-8.3 vs >= 8.3 syntax.
Thanks again,
Steve
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Atri, one more thing ...
This thread shows a step via the GUI where one has to select a device certificate. The link you sent seems to mostly deal with creating a permanent self-signed cert that is not regnerated each time the ASA boots. If I follow the procedure in the link, will I be able to see the self-signed cert in the GUI step where I have pick it from the drop-down? Right now I can't get past that step because my Device Certificate drop-down is empty.
Thanks,
Steve
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: