- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- Best Practices for Configuring an RNA Policy on a Sourcefire 3D System
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
07-22-2014 12:02 PM - edited 03-08-2019 06:56 PM
This article describes the basic steps and best practices for creating and configuring an RNA policy in 4.10. Before you can begin to generate RNA events, or gather RNA data, you need to make sure you have done the following:
1) The sensor must be managed by a Defense Center (DC), and the DC must have a valid RNA license. To check if there is a valid RNA license, navigate to Operations > System Settings. On this page, click on License in the menu on the left. This page displays the current licenses on the Defense Center. The following shows a DC with a valid RNA license:
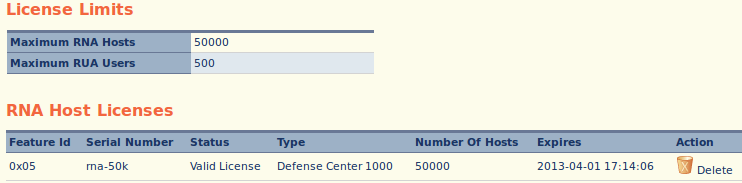
In the screenshot above, there is a valid RNA license on the DC with a host limit of 50000. The host limit is the amount of hosts that are allowed to be stored on the DC at one time. If you run out of hosts, the DC will either remove old hosts to allow for new hosts, or keep the current hosts, depending on how you configure the settings.
2) You need to make sure you have an interface set created. To view the interface sets, from the web interface, navigate to Operations > Configuration > Interface Sets. On this page, you can view the configured interface sets, edit them, delete them, or create new ones. If there are no configured interface sets, you will need to create a new one by clicking on the Create Interface Set button, located at the top right of the page. You can use RNA to monitor the traffic that passes through any of the three types of interface sets (Passive, Inline, and Inline with Fail-Open).
3) There needs to be an RNA Detection Engine configured on the sensor(s) that will be used for RNA. To view the available detection engines, from the webUI, navigate to Operations > Configuration > Detection Engines. On this page, you can view the configured detection engines, edit them, delete them, or create new ones. If there are no configured RNA detection engines, you will need to edit an existing one and configure it for RNA, or create a new one by clicking on the Create Detection Engine button, located at the top right of the page.
Note: You can use one interface set for multiple detection engines. For example, if you are using one interface set for IPS, you can create a detection engine and use that same interface set for RNA.
4) After you have configured your RNA Detection Engine(s), you will use them in an RNA Detection Policy. To edit/create a Detection Policy from the webUI, navigate to Policy & Response > RNA > Detection Policy. If you do not have an existing Detection Policy, or you want to create a new one, click on the Create Policy button, located at the top right of the page.
Detection Policy Settings
There are multiple settings in the Detection Policy (shown below):

Update Interval
The interval at which RNA updates information (such as when a host was last seen, when a service was used, or the number of hits for a service). The default setting is 3600 seconds (1 hour). Note that setting a lower interval for update timeouts provides more accurate information in the host display, but generates more network events.
Flow Data Mode
Indicates how flow data (including NetFlow data) is collected. You can:
- Select Enabled to configure your 3D Sensors to transmit individual flows to the Defense Center.
- Select Summary (the default) to configure your 3D Sensors to transmit flow summaries, which are sets of flow data aggregated over five‑minute intervals.
- Select Disabled to disable the collection of flow data.
Note that disabling or limiting flow data collection can reduce the traffic between your 3D Sensors and your Defense Center as well as reduce the space required to store flow data on the Defense Center, but it can also prevent or limit you from taking advantage of any feature that relies on flow data, such as the Flow Summary dashboard, traffic profiles, compliance rules based on flows or traffic profile changes, and flow trackers in compliance rules.
Save Unknown OS Data
Select this check box if you want to save data related to unidentified operating systems. This data is saved in packet capture (pcap) format on the appliance should you need to send this information to Sourcefire Support.
Save Unknown Service Data
Select this check box if you want to save events related to unidentified services. This data is saved in packet capture (pcap) format on the appliance should you need to send this information to Sourcefire Support.
Caution: Enabling the previous two options can cause slower performance and higher disk usage on the sensor(s) or the Defense Center. If you are applying your RNA policy to numerous sensors and/or or a broad range of networks, these options should probably not be enabled.
Capture Banners
Select this check box if you want RNA to store header information from network traffic that advertises service vendors and versions (“banners”). This information can provide additional context to the information gathered by RNA. You can access service banners collected for hosts by accessing service details.
Client Application Detection
Select this check box if you want RNA to generate events related to client application detection. Note that flows exported by NetFlow‑enabled devices do not contain any information on client applications involved in the monitored session.
Capture HTTP URLs
Select this check box if you want RNA to capture HTTP URLs and include them in flow events, where applicable. Note that flows exported by NetFlow‑enabled devices do not contain any URL information.
Generate Hosts from NetFlow Data
Select this check box if you want RNA to add hosts to the network map based on flow data exported by NetFlow‑enabled devices. You cannot select this check box if you have not applied a NetFlow feature license to your Defense Center. Note that there is no operating system information available for hosts added to the network map based on NetFlow data, unless you use the host input feature to manually set the hosts’ operating system identity.
Generate Services from NetFlow Data
Select this check box if you want RNA to add services to the network map based on flow data exported by NetFlow‑enabled devices. You cannot select this check box if you have not applied a NetFlow feature license to your Defense Center. Note that the Sourcefire 3D System is unable to identify the names, version, and vendors of services running on hosts detected by your NetFlow‑enabled devices, unless you use the host input feature to manually set those values.
Combine Flows for Out‑of‑Network Responders
Select this check box if:
- You kept the flow data mode as Summary (that is, your 3D Sensors will transmit aggregated flows instead of individual flows to the Defense Center)
- You want to combine flow summaries involving external hosts on the sensors, before they transmit the data to the Defense Center
Enabling this option treats flow summary data from IP addresses that are not in your list of monitored networks as coming from a single host. Event views, graphs, and reports use external to indicate the hosts outside your monitored network, instead of an individual IP address.
Networks to Monitor
The next option in the Detection Policy is specifying networks to monitor. To add a network to monitor, click on the Add Network button. A new section will be created where you can specify the IP Address, Netmask, Data Collection, and Reporting Detection Engine. If you know which networks the sensing interfaces on your 3D Sensors are physically connected to, configure the RNA detection policy so that the reporting detection engine for a subnet is the detection engine that uses the interface set monitoring that subnet. The reporting detection engine for a particular network segment is responsible for reporting most of the information about the hosts on that network, for example, the operating systems and services running on the hosts. An example showing the various options is shown below:

- For the first network, the RNA detection engine will collect host and flow data from the 10.8 subnet.
- For the second network, the RNA detection engine will collect only host data from the 10.7 subnet.
- For the third network, the RNA detection engine will exclude data from the host with IP address: 10.7.45.32.
Note: Be sure to select a Reporting Detection Engine. It is better to specify a detection engine rather than using Auto-detect if you know what network segment the detection engine is monitoring. Using Auto-detect will only grab a limited amount of information like MACs and hops.
Caution: If you delete a detection engine or recreate a detection engine that is used in your policy, make sure you go back into the policy and specify the new detection engine, as deleting a detection engine will cause the Reporting Detection Engine field to be blank, which can cause issues.
Ports to Exclude
The next option in the Detection Policy is specifying ports to exclude. To add a port to exclude, click on the "Add Port" button. A new section will be created and you can specify the Port(s), Protocol, Source/Destination, IP Address, and Netmask.

This configuration will exclude port 80 from IP address 10.8.12.12.
Caution: The port exclusion feature only effects data collected by 3D Sensors with RNA. You cannot configure NetFlow‑enabled devices to exclude ports from monitoring.
Note: Do not use the port exclusion to exclude all ports for a specific host/network segment. Instead, you should exclude the host/network segment itself using the Exclude Data Collection option in the Networks to Monitor section.
Once you have your policy configured, click the Save Policy button if you are creating a new policy, or the Update Policy button if you are editing an existing policy. Once you save the policy, click Apply and select the sensor(s) that this policy should be applied to (the sensor that have the detection engines being used in the policy).
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Very helpful post Nazmul.
Had a query.
We have ordered 2 x 8130 and 1 x DC-1500, want to know what will be the default RNA/RUA license capacity ?
Akhtar
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Akhtar,
This document discusses about software version 4.10.x. Since you have just ordered new products, are you going to use RNA/RUA (on legacy Version 4.10), or the FireSIGHT (on Version 5.2 or 5.3)?
The FireSIGHT license on your Defense Center determines how many individual hosts and users you can monitor with the Defense Center and its managed devices, as well as how many users you can use to perform user control. A FireSIGHT license on the DC1500 supports up to 50,000 hosts and users. Because FireSIGHT licensed limits are matched to the hardware capabilities of Defense Centers, we do not recommend exceeding them.
Thank you.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: