- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- Configure Anyconnect with SAML authentication on FTD managed via FDM
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
09-16-2021 08:22 AM - edited 01-31-2022 05:38 AM
Introduction
This document provides a configuration example of Security Assertion Markup Language (SAML) Authentication on FTD managed over FDM. The configuration allows Anyconnect users to establish a VPN session authenticating with a SAML Identity Service Provider.
Prerequisites
Requirements
FTD managed over FDM using minimum version 6.7.0
Cisco recommends that you have knowledge of these topics:
- Knowledge of Anyconnect configuration on FDM
- Knowledge of SAML and metatada.xml values
Components Used
The information in this document is based on these software and hardware versions:
- Firepower Threat Defense managed over FDM using version 7.0.
- ADFS from AD Server with SAML 2.0
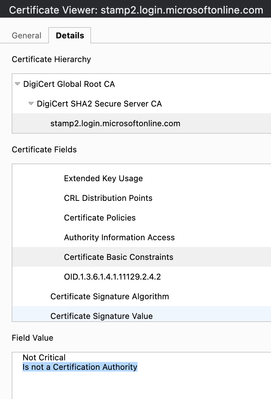
Note: I am using an ADFS IdP server where a custom IdP's certificate was created, this includes the "Basic Constraints CA flag set".
Also, if possible, use an NTP server to synchronize the time between the FTD and IdP. Otherwise, make sure the time is manually synchronized between them.
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, ensure that you understand the potential impact of any command.
Background Information
Due to CSCvu95526, the only SAML server fully supported is DUO, see below:
SAML Servers
Following are the supported SAML servers: Duo.
In this lab, I am using ADFS as SAML server; however, I created a custom IdP's signing certificate which does contain the CA flag under Basic Constraints. Which basically eliminates the limitation defined under bug: CSCvu95526.
You can check if the IdP's signing certificate contains this flag using the following SSL command:
openssl x509 -in vpnx.local/id.crt -noout -text
Configuration
This section describes how to configure Anyconnect with SAML authentication on FTD managed via FDM.
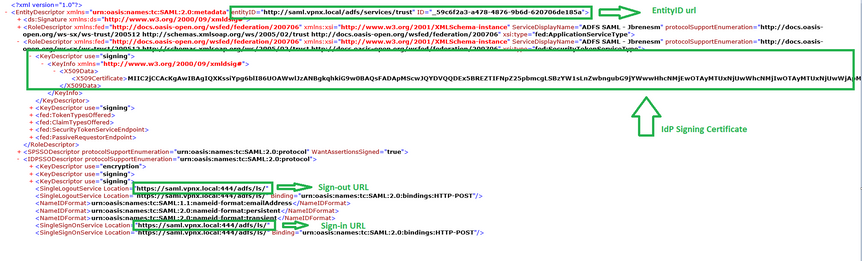
Get the SAML IdP parameters
The below image shows a SAML IdP metadata.xml file. From the output, you can get all values needed in order to configure the Anyconnect profile using SAML:
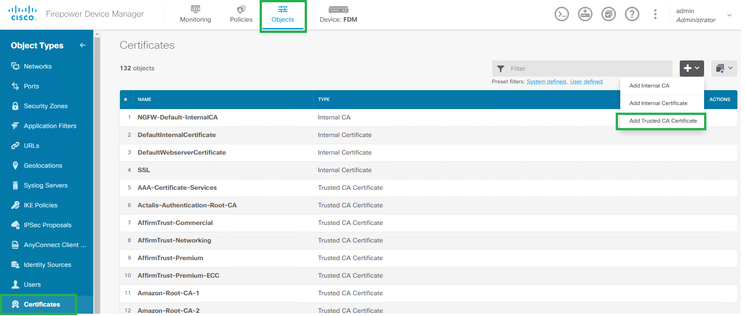
Step 1. Import the IdP's certificate. Under Objects -> Certificates -> Add Trusted CA Certificate.
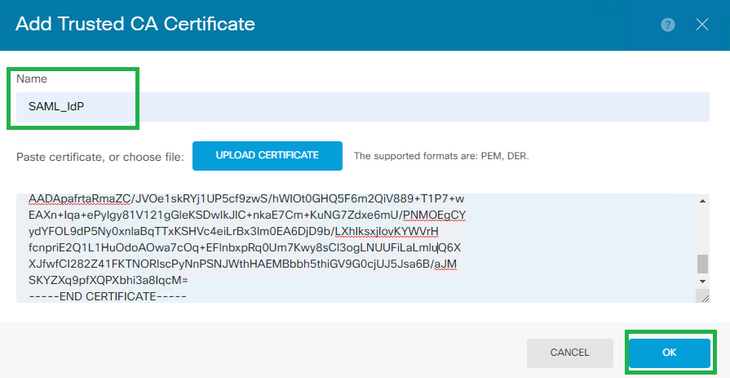
Step 2. The name you define will be used later on when calling the IdP's certificate.
Step 3. Create the SAML server. Under Objects -> Identity Sources -> SAML Server.
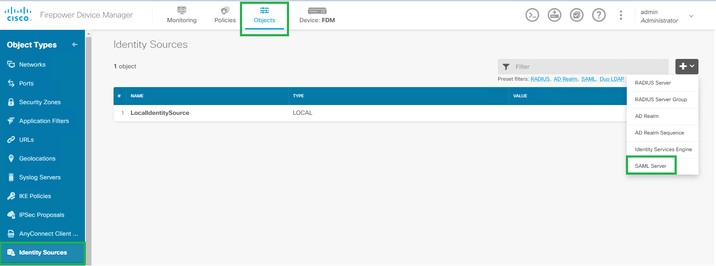
Step 4. Based on the metadata.xml file already provided by your IdP, configure the SAML values.
Name: SAML Server's name.
Identity Provider (IDP) Entity ID URL: entityID from metadata.xml
Sign in URL: SingleSignOnService from metadata.xml.
Sign out URL: SingleSignLogoutService from metadata.xml.
FTD Service Provider Certificate: FTD signing certificate.
Identity Provider Certificate: IdP signing certificate.

Step 5. Create a Connection profile that uses SAML as authentication method. Under Device -> Remote Access VPN.
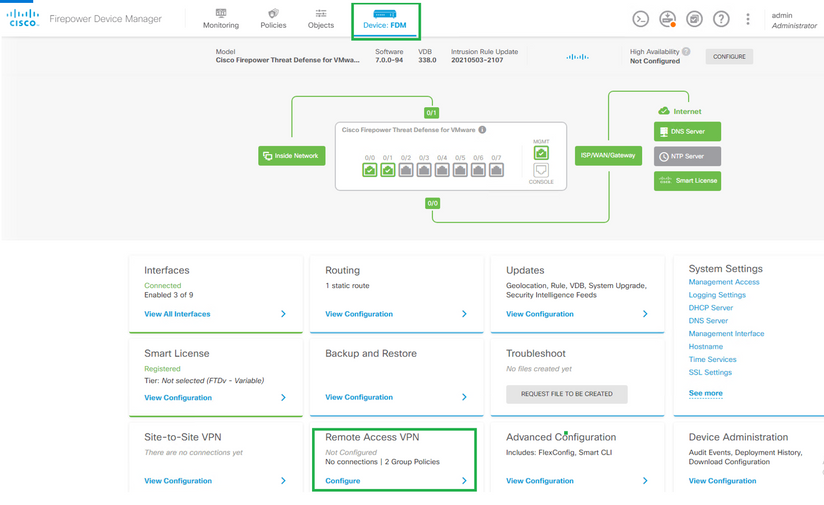
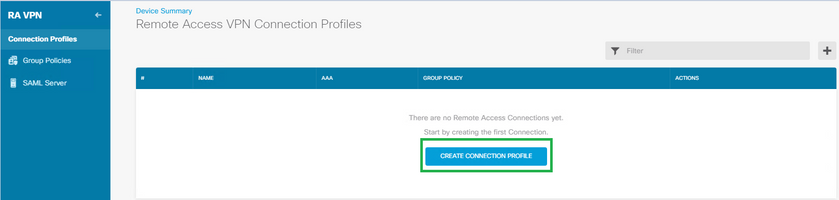
Step 6. Click on Create Connection Profile.
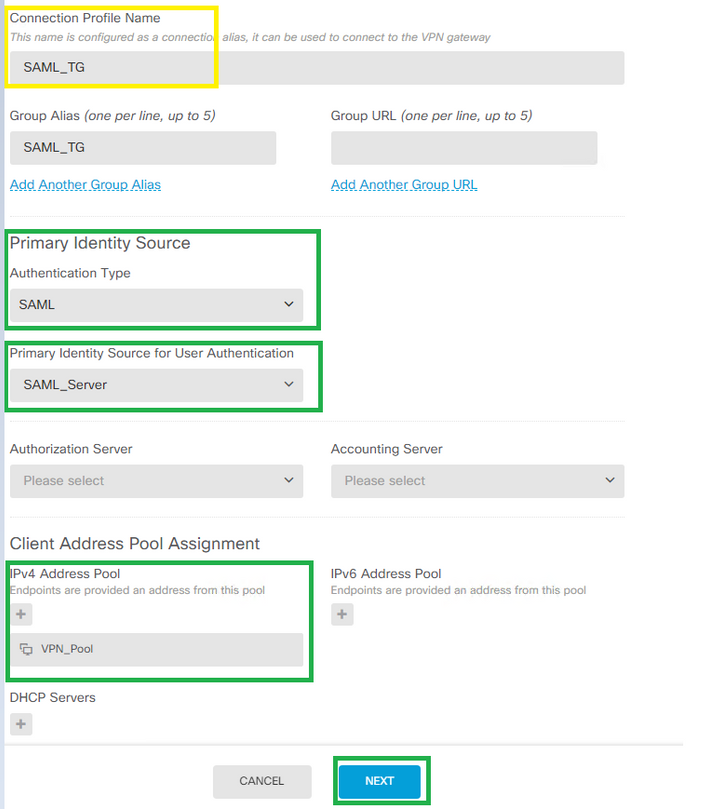
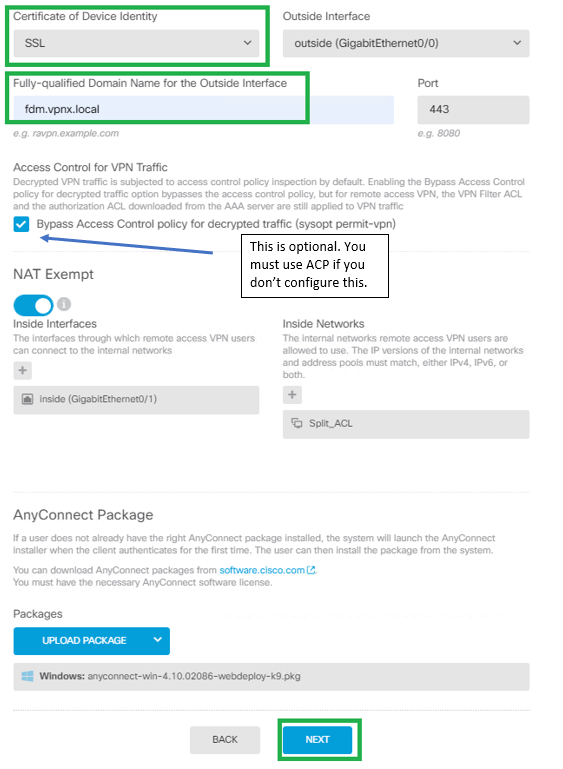
Step 7. Define the Connection Profile's name, the authentication method under Primary Identity Source and select the SAML Server we created under step #3. Also, the ip local pool or DHCP if you want to assign
IP's to the RA users via DHCP.
Step 8. Select the group-policy for this Connection profile. You can create a dedicated GP for this
connection profile or use the default instead.
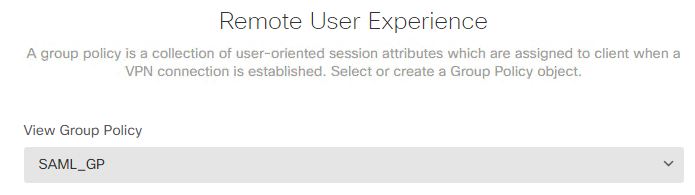
Step 9. Define what SSL Certificate to use for this RA, the FQDN for the RA's FTD, the Anyconnect .pkg
file we will use. Optionally you can set the NAT Exemption and the sysopt permit-vpn.
Very important: What you define under "Fully-qualified Domain Name for the Outside Interface" will be set as base URL for the SAML config. Make sure the proper FTD's RA FQDN is set there.
Step 10. Deploy the changes.
Step 11. Now, provide the FTD's metadata.xml file to the IdP so they add the FTD as a trusted device.
On the FTD CLI, run the command:"show saml metadata SAML_TG "where SAML_TG is the name of our
Connection Profile created on Step 7
As seen in the below bracket, this is the expected output from the command mentioned above:
> system support diagnostic-cli
Attaching to Diagnostic CLI ... Press 'Ctrl+a then d' to detach.
Type help or '?' for a list of available commands.
FDM> en
Password:
FDM# show saml metadata SAML_TG
<?xml version="1.0" encoding="UTF-8" standalone="yes"?>
<EntityDescriptor entityID="https://fdm.vpnx.local/saml/sp/metadata/SAML_TG" xmlns="urn:oasis:names:tc:SAML:2.0:metadata">
<SPSSODescriptor AuthnRequestsSigned="false" WantAssertionsSigned="true" protocolSupportEnumeration="urn:oasis:names:tc:SAML:2.0:protocol">
<KeyDescriptor use="signing">
<ds:KeyInfo xmlns:ds="http://www.w3.org/2000/09/xmldsig#">
<ds:X509Data>
<ds:X509Certificate>MIIDtDCCApygAwIBAgIUPTIJfezEbif278Yv/6WeD6cZ/18wDQYJKoZIhvcNAQEL
BQAwgY4xCzAJBgNVBAYTAkNSMQ0wCwYDVQQIDAROb25lMQ0wCwYDVQQHDAROb25l
MRgwFgYDVQQKDA9WUE4tWCBDQSBTZXJ2ZXIxDDAKBgNVBAsMA1ZQTjEWMBQGA1UE
AwwNY2EudnBueC5sb2NhbDEhMB8GCSqGSIb3DQEJARYSamJyZW5lc21AY2lzY28u
Y29tMB4XDTIxMDgyODE1NTc0M1oXDTIzMDQyMDE1NTc0M1owfDELMAkGA1UEBhMC
Q1IxDTALBgNVBAgMBE5vbmUxDTALBgNVBAcMBE5vbmUxETAPBgNVBAoMCFZQTlgg
QVNBMQwwCgYDVQQLDANWUE4xFTATBgNVBAMMDCoudnBueC5sb2NhbDEXMBUGCSqG
SIb3DQEJARYIamJyZW5lc20wggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIB
AQDixBmrt0q2tY/iPnAGhOYftAZq5+azrDVC/8zkNMG3pXsvTWpVGau2oOwGgwoq
bITOS24PLdXWH5bgPRRIufX4a+sJKCs4sbroCbmm+Xr/uWbjlaxlXgkMO4BhwTkU
u9iAchMp76+18IKpVp0Ny+R+jvfWnwbIifLvXEu73sUmJKkX3R3HSjxpAk9fkLOn
15o2IgnpzTI/jeDxUpQiYxlgKPRPnoKFp9gE7JCCLKiE2bEuJ9cI64KYtsXj6w3k
K2i1HX7BOnPVo2ayHDIPPtHk4ho0c8Cq+VNObVf1IMT6/6K12f7ES3zK+kVFHRBZ
GmddvasJ2wyPsdMib4hrnE7DAgMBAAGjGzAZMBcGA1UdEQQQMA6CDCoudnBueC5s
b2NhbDANBgkqhkiG9w0BAQsFAAOCAQEAe+OUCDV7NcC36g3ruU4RuNl5T9JzmvO9
S+CHUxyPBAqy9iusXGHOW5VWis+rjnR+z18DaSHeoSfXUOdShwaI6OQxs3pbyW/A
t+Vc/Doq4ok5ZWNQWj7UMOlWzA8X1rcCAHDNRJ7vee87sjyUljXgMDUt1pE2qKvV
dbsxwU2JJA+A62yegMPlxbaE5FBqsm20Thio2N5v3CV2JX6stABRH9nlyn84hAZr
IsJ/dUqkHacW0fogXiW2PienfOF58klE3NsnPIOaS+oKHTN6iA4kcTeZv08dOaC6
Wqix+84JVl9bvdCPrA+TNjCj+mfoLe2v1+xKU0KsCQw/LCHy2igYIg==
</ds:X509Certificate>
</ds:X509Data>
</ds:KeyInfo>
</KeyDescriptor>
<AssertionConsumerService index="0" isDefault="true" Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://fdm.vpnx.local/+CSCOE+/saml/sp/acs?tgname
<SingleLogoutService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect" Location="https://fdm.vpnx.local/+CSCOE+/saml/sp/logout"/><SingleLogoutService Binding=:HTTP-POST" Location="https://fdm.vpnx.local/+CSCOE+/saml/sp/logout"/></SPSSODescriptor>
</EntityDescriptor>
FDM#
Once the metadata.xml from the FTD is provided to the IdP and they add it as a trusted device, a test under the VPN connection can be done.
Verify
Verify if the VPN Anyconnect connection was established using SAML as an authentication method with the commands seen below:
FDM# show vpn-sessiondb detail anyconnect
Session Type: AnyConnect Detailed
Username : jbrenesm Index : 3
Assigned IP : 10.1.2.1 Public IP : 10.2.210.250
Protocol : AnyConnect-Parent SSL-Tunnel
License : AnyConnect Premium
Encryption : AnyConnect-Parent: (1)none SSL-Tunnel: (1)AES-GCM-256
Hashing : AnyConnect-Parent: (1)none SSL-Tunnel: (1)SHA384
Bytes Tx : 14474 Bytes Rx : 5538
Pkts Tx : 10 Pkts Rx : 34
Pkts Tx Drop : 0 Pkts Rx Drop : 0
Group Policy : SAML_GP Tunnel Group : SAML_TG
Login Time : 18:30:35 UTC Tue Sep 14 2021
Duration : 0h:00m:19s
Inactivity : 0h:00m:00s
VLAN Mapping : N/A VLAN : none
Audt Sess ID : 00000000000030006140ea4b
Security Grp : none Tunnel Zone : 0
AnyConnect-Parent Tunnels: 1
SSL-Tunnel Tunnels: 1
AnyConnect-Parent:
Tunnel ID : 3.1
Public IP : 10.2.210.250
Encryption : none Hashing : none
TCP Src Port : 58143 TCP Dst Port : 443
Auth Mode : SAML
Idle Time Out: 30 Minutes Idle TO Left : 29 Minutes
Client OS : win
Client OS Ver: 10.0.19042
Client Type : AnyConnect
Client Ver : Cisco AnyConnect VPN Agent for Windows 4.10.02086
Bytes Tx : 7237 Bytes Rx : 0
Pkts Tx : 5 Pkts Rx : 0
Pkts Tx Drop : 0 Pkts Rx Drop : 0
SSL-Tunnel:
Tunnel ID : 3.2
Assigned IP : 10.1.2.1 Public IP : 10.2.210.250
Encryption : AES-GCM-256 Hashing : SHA384
Ciphersuite : ECDHE-RSA-AES256-GCM-SHA384
Encapsulation: TLSv1.2 TCP Src Port : 58153
TCP Dst Port : 443 Auth Mode : SAML
Idle Time Out: 30 Minutes Idle TO Left : 29 Minutes
Client OS : Windows
Client Type : SSL VPN Client
Client Ver : Cisco AnyConnect VPN Agent for Windows 4.10.02086
Bytes Tx : 7237 Bytes Rx : 5538
Pkts Tx : 5 Pkts Rx : 34
Pkts Tx Drop : 0 Pkts Rx Drop : 0
FDM#
Troubleshoot
Some verification commands on the FTD CLI can be used to troubleshoot SAML and Remote Access VPN connection as seen in the bracket:
Verification commands on the FTD CLI:
firepower# show run webvpn
firepower# show run tunnel-group
firepower# show crypto ca certificate
firepower# debug webvpn saml 255
DART from the Anyconnect's user PC.
I hope it helps
- Josue Brenes (jbrenesm)
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Great writeup - thanks for sharing @Josue Brenes
One caveat I've encountered is that if "sysopt permit-vpn" is enabled for ANY remote access VPN connection profile or site-to-site VPN on the firewall it will affect all of them (since it is a global command in the running-config)
FYI your bugID that's linked should point to the public-facing site vs. the cdets internal one. i.e., use:
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@Josue Brenes great write up - can see how ADFS can be used in this method. But can FTD with FDM use Azure? https://community.cisco.com/t5/vpn/saml-authentication-configuration-on-ftd-managed-via-fmc/td-p/4316978 and https://www.cisco.com/c/en/us/td/docs/security/firepower/710/relnotes/firepower-release-notes-710/features.html
thanks in advance
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@Marvin Rhoads, yes thanks, already posted the correct bug link.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello @Rudi Heitbaum,
Yes I don't see why not. As long as the Azure's IdP certificate does contain the "CA flag" under Basic Constraints then it should be good.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Ciao @Josue Brenes ,
very good guide. However, trying to configure Azure IDP this error occurs:
ERROR: SAML IDP certificate failed
Check the IDP certificate, no CA Basic Constraints in the Azure certificate. Is it the bug ???
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Ciao,
after some googling and testing I found the right way: Create your own CA cert and import it in Azure SSO configuration.
The certificate must have: basicConstraints = CA:TRUE for FDM and need support the Azure Signature Alghoritm: SHA-1 or SHA-256:
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: