- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- Configuring DMVPN with ZBF (Hub and Spoke Topology)
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
03-26-2011 07:37 PM - edited 03-08-2019 06:40 PM
Objective:
To configure ZBF on both a DMVPN hub and a DMVPN spoke router.
Problem Description:
DMVPN(hub and spoke deployment) is a hub-and-spoke deployment model in which the primary enterprise resources are located in a large central site, with a number of smaller sites or branch offices connected directly to the central site over a VPN.
Zone Based Firewall is an advanced configuration model for the Cisco IOS Firewall feature set. It offers intuitive policies for multiple-interface routers, increased granularity of firewall policy application, and a default deny-all policy that prohibits traffic between firewall security zones until an explicit policy is applied to allow desirable traffic.
Often in case of small remote sites the DMVPN router serves not only as the GRE and Crypto aggregation router but also as the network edge device. In such cases, users often prefer to add an extra layer of security by enabling Zone Based Firewall feature set on the router. Network location of the crypto headend in relation to the headend firewall(s) impacts both the accessibility and performance of both systems. The network manager must ensure that all firewalls are properly configured to allow the tunnel traffic bi-directionally. The crypto headend must be accessible to the branch router because all crypto sessions are initiated by the branch router.
Prerequisites:
Please note, only single tiered headened architecture is discussed in this document. In case of double tiered architecture, ZBF needs to be configured to allow GRE traffic on one router and IPSEC traffic on the other.
Scenario:
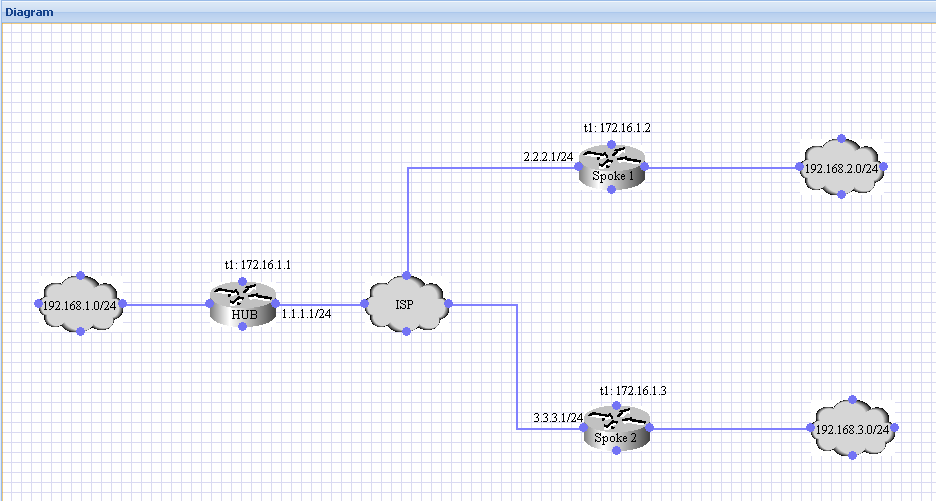
Solution:
One of the biggest differences between CBAC and ZBF is in the manner in which the firewall policies are applied. In CBAC the inspection policies are defined per interface, however to improve granularity and flexibility in the firewall configuration, ZBF was modelled based on zones. Each interface is made part of a zone, and the inspection policies are applied between two zones. Usually the private networks are part of the in-zone, and the poblic networks are part of the out-zone. All traffic destined to any ip address on the router itself is part of the "self" zone. By default traffic from any zone to the self zone is permitted, however if there is a specifc out-self zone then special care needs to be taken to permit those kinds of traffic that will be destined to the router itself. Depending on the crypto and DMVPN headend or branch placements, the following protocols and ports are required to be allowed:
•![]() UDP Port 500—ISAKMP as source and destination
UDP Port 500—ISAKMP as source and destination
•![]() UDP Port 4500—NAT-T as a destination
UDP Port 4500—NAT-T as a destination
•![]() IP Protocol 50—ESP
IP Protocol 50—ESP
•![]() IP Protocol 51—AH (if AH is implemented)
IP Protocol 51—AH (if AH is implemented)
•![]() IP Protocol 47—GRE
IP Protocol 47—GRE
•![]() Routing protocol
Routing protocol
Please note, only single tiered headened architecture is discussed in this document. In case of double tiered architecture, ZBF needs to be configured to allow GRE traffic on one router and IPSEC traffic on the other.
Please keep in mind that the above considerations need to be made in additition to the configuration reqiured to allow normal traffic as desired.
There are various ways that routers can be configured. I have identified 4 such use cases base on what zone each interface is mapped to:
•![]() Use of 2 zones
Use of 2 zones
interface | zone |
|---|---|
| inside | internal |
| outside | external |
tunnel | external* |
*it is not recommended to configure the tunnel interface in the same zone as the inside interface, because in this case, the DMVPN traffic does not require any kind of zone pair configuration at all to allow the traffic to pass through, thus making the FW completely redundant as far as the DMVPN traffic is concerned.
•![]() Use of 3 zones
Use of 3 zones
| interface | zone |
|---|---|
| inside | internal |
| outside | external |
| tunnel | dmvpn |
For both the above use cases you can refer to the document Using VPN with Zone-Based-Firewall for the configuration guide.
•![]() Use of self zone
Use of self zone
In this particular use case the interfaces can be configured using either 3 or 2 zone as described above, however an additional self zone is also applied in the zone pair configuration to provide added protection against traffic sent to the router.
Configuration:
The following configuration example is for the case where:
1. the hub is configured with 2 zones along with a self zone
2. the spoke is configured with 3 zones along with a self zone
Configuration on Hub:
crypto isakmp policy 1
encr 3des
hash md5
authentication pre-share
group 2
crypto isakmp key cisco123 address 0.0.0.0 0.0.0.0
!
crypto ipsec transform-set dmvpn-trans esp-3des esp-md5-hmac
mode transport
!
crypto ipsec profile dmvpn-pro
set transform-set dmvpn-trans
!
class-map type inspect match-any self-out-class
match protocol icmp
class-map type inspect match-any self-out-dmvpn-class
match access-group name test
match protocol isakmp
class-map type inspect match-any int-ext-class
match protocol telnet
match protocol ssh
match protocol icmp
!
policy-map type inspect int-ext-policy
class type inspect int-ext-class
inspect
class class-default
drop
policy-map type inspect self-out-policy
class type inspect self-out-dmvpn-class
pass
class type inspect self-out-class
inspect
class class-default
drop
!
zone security internal
zone security external
zone-pair security int-ext source internal destination external
service-policy type inspect int-ext-policy
zone-pair security ext-int source external destination internal
service-policy type inspect int-ext-policy
zone-pair security self-ext source self destination external
service-policy type inspect self-out-policy
zone-pair security ext-self source external destination self
service-policy type inspect self-out-policy
!
interface Tunnel1
ip address 172.16.1.1 255.255.255.0
no ip redirects
ip mtu 1400
ip nhrp authentication cisco123
ip nhrp map multicast dynamic
ip nhrp network-id 1
ip nhrp holdtime 600
zone-member security external
no ip split-horizon eigrp 1
tunnel source Ethernet0/1
tunnel mode gre multipoint
tunnel key 10000
tunnel protection ipsec profile dmvpn-pro
!
interface Ethernet0/0
ip address 192.168.1.1 255.255.255.0
zone-member security internal
!
interface Ethernet0/1
ip address 1.1.1.1 255.255.255.0
zone-member security external
!
router eigrp 1
network 192.168.1.0 0.0.0.255
network 172.16.1.0 0.0.0.255
auto-summary
!
ip forward-protocol nd
ip route 0.0.0.0 0.0.0.0 1.1.1.2
!
ip access-list extended test
permit gre any any
permit esp any any
permit eigrp any any
Configuration on Spoke:
crypto isakmp policy 1
encr 3des
hash md5
authentication pre-share
group 2
crypto isakmp key cisco123 address 0.0.0.0 0.0.0.0
!
crypto ipsec transform-set dmvpn-trans esp-3des esp-md5-hmac
mode transport
!
crypto ipsec profile dmvpn-pro
set transform-set dmvpn-trans
!
class-map type inspect match-any int-ext-clas
match protocol telnet
match protocol ssh
match protocol icmp
class-map type inspect match-any self-ext-class
match protocol icmp
class-map type inspect match-any self-ext-dmvpn-class
match protocol isakmp
match access-group name test-dmvpn
class-map type inspect match-any dmvpn-ext-class
match protocol icmp
!
policy-map type inspect dmvpn-ext-policy
class type inspect dmvpn-ext-class
inspect
class class-default
drop
policy-map type inspect int-ext-policy
class type inspect int-ext-clas
inspect
class class-default
drop
policy-map type inspect self-ext-policy
class type inspect self-ext-class
inspect
class type inspect self-ext-dmvpn-class
pass
class class-default
drop
!
zone security internal
zone security external
zone security dmvpn
zone-pair security int-dmvpn source internal destination dmvpn
service-policy type inspect int-ext-policy
zone-pair security dmvpn-int source dmvpn destination internal
service-policy type inspect int-ext-policy
zone-pair security int-ext source internal destination external
service-policy type inspect int-ext-policy
zone-pair security ext-int source external destination internal
service-policy type inspect int-ext-policy
zone-pair security self-ext source self destination external
service-policy type inspect self-ext-policy
zone-pair security ext-self source external destination self
service-policy type inspect self-ext-policy
!
interface Tunnel1
ip address 172.16.1.2 255.255.255.0
ip mtu 1400
ip nhrp authentication cisco123
ip nhrp map multicast 1.1.1.1
ip nhrp map 172.16.1.1 1.1.1.1
ip nhrp network-id 1
ip nhrp holdtime 600
ip nhrp nhs 172.16.1.1
zone-member security dmvpn
no ip split-horizon eigrp 1
tunnel source Ethernet0/1
tunnel destination 1.1.1.1
tunnel key 10000
tunnel protection ipsec profile dmvpn-pro
!
interface Ethernet0/0
ip address 192.168.2.1 255.255.255.0
zone-member security internal
!
interface Ethernet0/1
ip address 2.2.2.1 255.255.255.0
zone-member security external!
ip access-list extended test-dmvpn
permit esp any any
permit gre any any
permit eigrp any any
Known Caveats:
- CSCtn65512 - ZBF drops DMVPN traffic post IPSec decryption when using shared TP
- CSCta00183 - ZBF: Adding ins for esp from out to self zone may break DMVPN and EIGRP
Suggested Reading:
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
thank you for the posting
that is what i was looking for
i addition, my requirements also need NAT and
a means to ensure all SPOKE traffic only goes to the HUB
I am required to have the HUB acts as the inet gateway
even though most of my spokes will connect over the inet, their traffic needs to be "tunneled" to the HUB
some SPOKE sites are on the corporate network, they will be treated the same.
This ensures that we can moinitor and control inet traffic without having to replicate the strong filtering and monitoring at all SPOKE sites
any tips or advice? for the later two addional requirements?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi,
pretty nice guide. I have got few questions though. We are using separate ACLs for self-out and out-self zone pairs. in out_to_self ACL we have allowed gre any any but not in self_to_out ACL and the tunnel works fine. Also we did not permit eigrp any any (in both ACLs) and the neighbours come up with no problem. Could you provide some insight into this? I
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Martin, I would need to take a look at the configuraiton that you have could you post it here?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Walter, to control the traffic from the spokes so that they only go to the hub before they go anywhere else, you just need to control the routing. For example if you are using EIGRP then removing then enabling next-hop-self instead of disabling it should fix this issue for you. As far as NAT is concerned, just treat the tunnel interface like any other interface for natting, it should work.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi,
The physical interface is in outside, while the Tunnel interfaces are in zone "DMVPN". There is no eigrp protocol in either of the ACLs and GRE is allowed only in OUT->Self. I have changed the ACLs so they are mirrored. The EIGRP neighbour is up over 5 days now on both Hub and Spoke, the traffic flows fine, I can telnet and ping the destinations I need.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
amazing Atri !!! thank you !!!
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thanks -- out of the 4 examples I found on the internet, this was the only one that actually worked. Seems the Pass is a requirement for ISAKMP, thus needing to create the zone-pair in opposite direction as well.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: