- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- Configuring Eduroam on Cisco ISE 1.4
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
10-09-2015 12:57 AM - edited 02-21-2020 10:01 PM
This document details the steps for using ISE to authenticate Eduroam users. Janet is the name of the UK provider of Eduroam, please replace this with your own reference.
Three rules cover the authentication scenarios which will be encountered:
Rule 1 : User is not a member of the institution
Rule 2 : User is a member of the home institution but is located at another institution. Authentication will be sourced from the Janet NRPS.
Rule 3 : User is a member of the home institution and the request will be sourced locally.
Regarding authorization, we are simply aiming for PermitAccess, but will break the AuthZ rules down to give granularity to the reporting.
Prerequisites
On all WLCs configured to offer the SSID 'eduroam' to AP Groups, make sure that WLAN ID is the same on all WLCs and that all ISE PSN are being used for authentication.
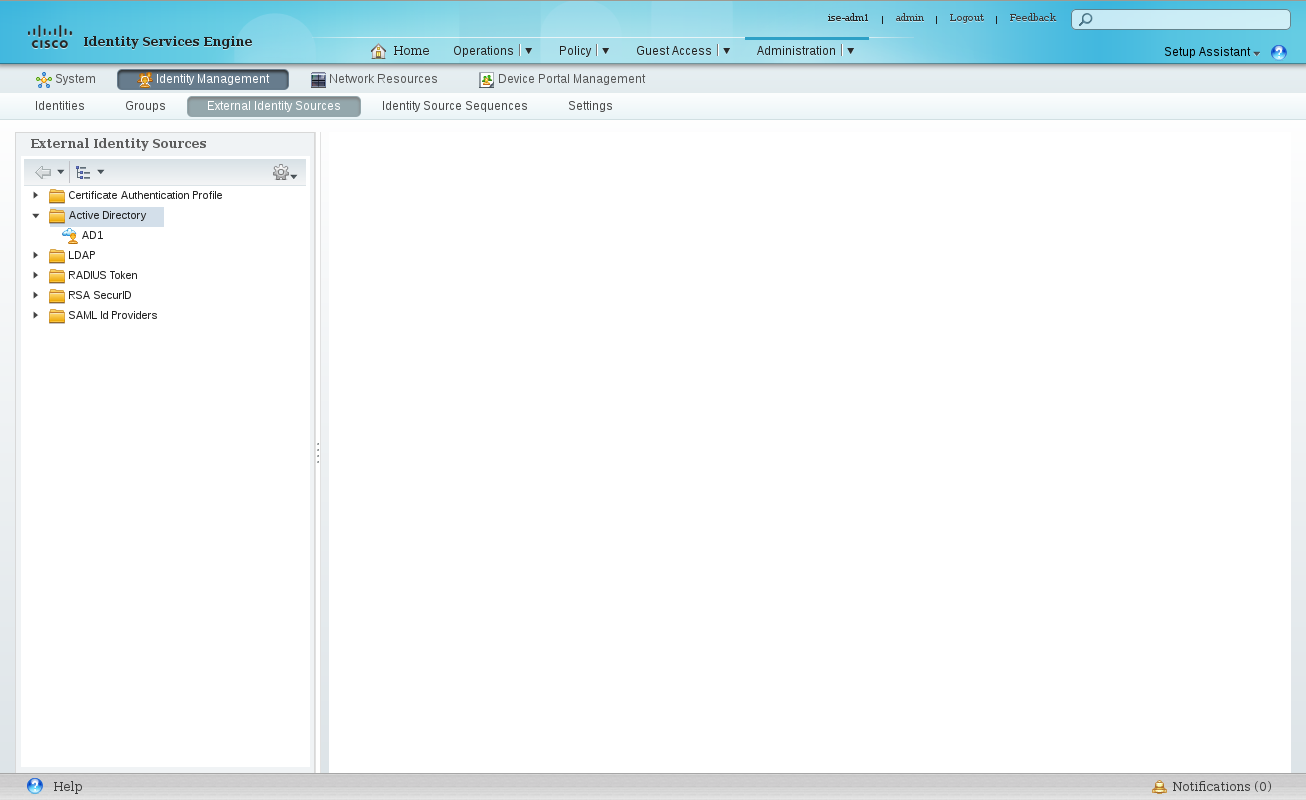
Administration → Identity Management → External Identity Sources → Active Directory
Create a service account in AD and use it to create a connection to your AD Domain
Administration → Network Resources → External RADIUS sources
Configure each of NRPS servers which will be used for authenticating users from external realms.

Administration → Network Resources → Network Device Groups
Create a new group 'NRPS'.
Create a new group 'Wireless'
Administration → Network Resources → Network Device List
Ensure your WLCs are part of the group Wireless, and the NRPS servers are part of the NRPS group.

Administration → Network Resources → Network Device List → RADIUS Server Sequences
Create an object which lists the access order of the external RADIUS servers.

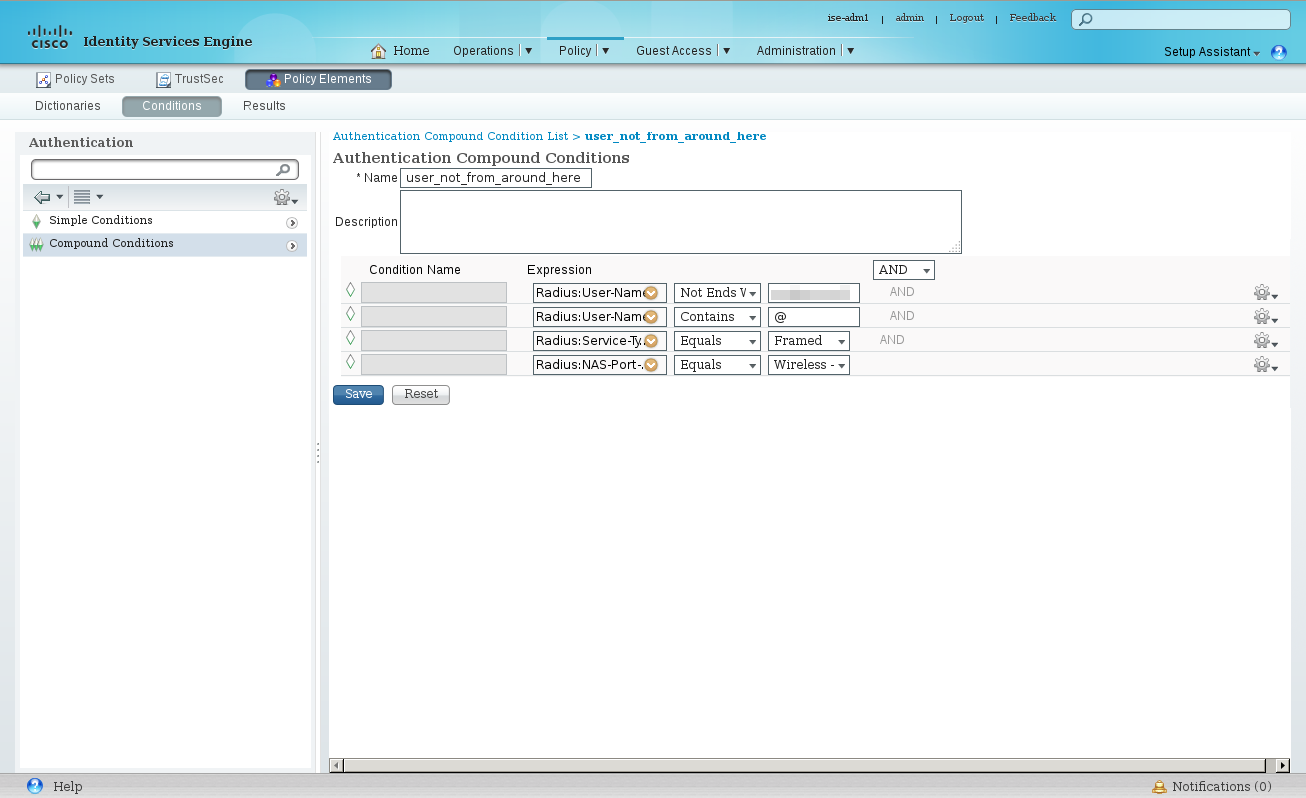
Policy → Policy Elements → Conditions → Authentication → Compound Conditions
Create a new condition, eg: 'user_not_from_around_here', this will be used to identify RADIUS requests that need to be handed off the the NRPS servers. In the event of receiving just a username we want to be able to handle that. We will make the assumption that such a user belongs to our own AD. As such we need to ensure that a 'foreign' username does not contain our realm but does contain an '@' symbol which we will infer means an alternative domain is provided.
Configure the following elements:
Radius: User-Name NOT ENDS WITH @<your_domain> AND Radius: User-Name CONTAINS @ AND Radius: Service-Type EQUALS Framed AND Radius: NAS-Port-Type EQUALS Wireless – IEEE 802.11
Create another condition 'eduroam-NRPS' similar to the above, but without the User-Name element. Since this condition will be used to identify eduroam traffic that must be sent to Janet we will include a check for the WLAN-ID:
Radius: Service-Type EQUALS Framed AND Radius: NAS-Port-Type EQUALS Wireless – IEEE 802.11 AND Airespace: Airespace-Wlan EQUALS 25

Policy → Policy Elements → Conditions → Authorization → Compound Conditions
Identify Authorization requests coming from the eduroam SSID and check the user names against AD. Name it 'eduroam-local':
Radius: Service-Type EQUALS Framed AND Radius: NAS-Port-Type EQUALS Wireless – IEEE 802.11 AND Airespace: Airespace-Wlan EQUALS 25 AD1:ExternalGroups EQUALS <your_domain>/Users/Domain Users

Policy
Policy
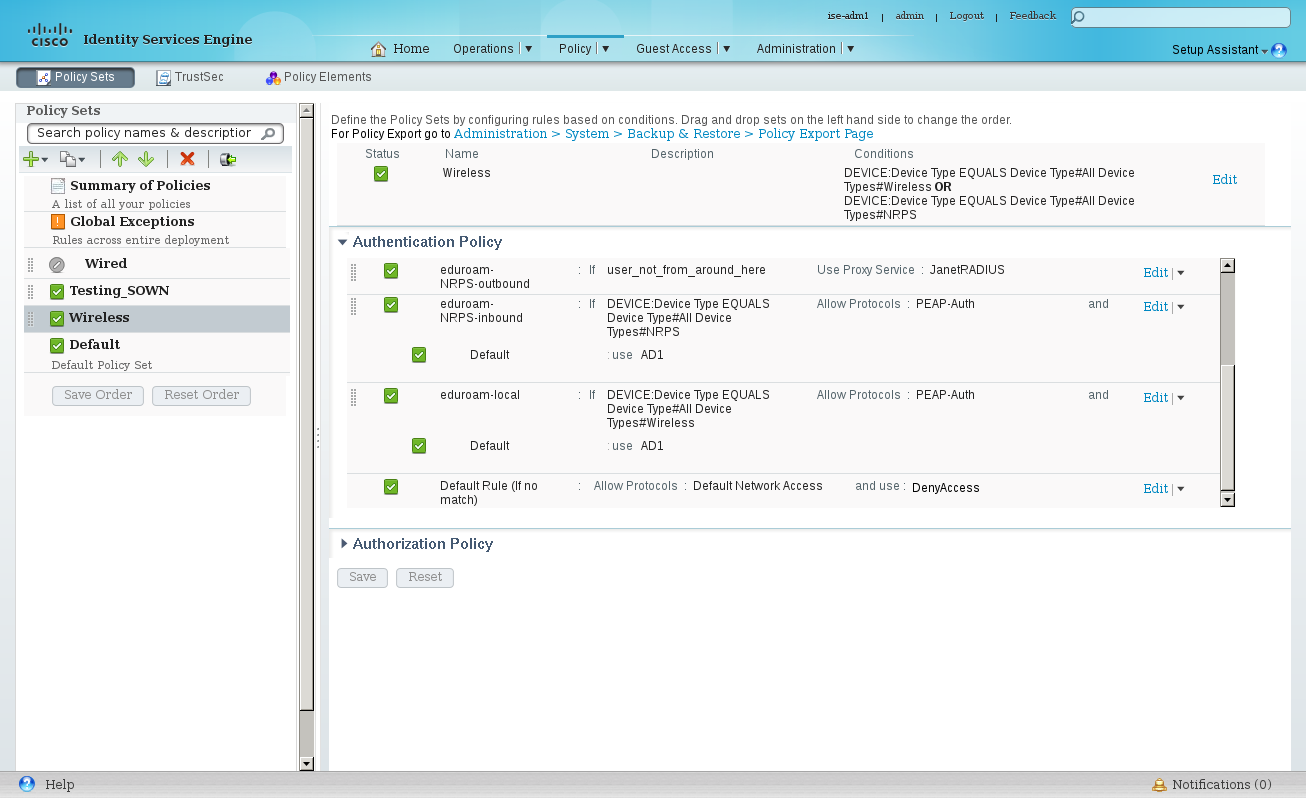
Turn on 'Policy Sets'. Create a new Policy Set 'Wireless'
Policy → Policy Sets → 'Wireless'
Set the Policy Set filer as:
DEVICE:Device Type EQUALS Device Type#All Device Types#Wireless OR DEVICE:Device Type EQUALS Device Type#All Device Types#NRPS
Policy → Policy Sets → 'Wireless' → Authentication Policy
Create three rules to handle the different authentication directions: inbound, local and outbound.
Name | If | Allow Protocols | Default |
eduroam-NRPS-outbound | user_not_from_around_here | Use Proxy Service: JanetRADIUS | |
eduroam-NRPS-inbound | DEVICE:Device Type EQUALS Device Type#All Device Types#NRPS | PEAP-Auth | AD1 |
eduroam-local | DEVICE:Device Type EQUALS Device Type#All Device Types#Wireless | PEAP-Auth | AD1 |
Policy → Policy Sets → 'Wireless' → Authorization Policy
Rule Name | Conditions | Permissions |
eduroam-nrps-inbound | eduroam-NRPS | PermitAccess |
eduroam-local | eduroam-local | PermitAccess |

[eof]
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi
Each agency has their own wlc and aaa servers.
Currently each angency should broadcast each other's WLAN by mobility anchors, so we are broadcasting our own plus about 7 more for each agency.
this should be replicated between us all.
so currently our own wlc are broadcasting 10 SSIDs at all time.
I'd like to propose that a large Eduroam style WLAN be broadcast, so all the public agencies connect and break out and only connect to their systems.
cheers
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
so if i got you correctly, you want to remove all 7 SSID's and substitute them with one SSID like eduroam? and all clients connect to that SSID whenever a userX from Agency X is at Agency Y.
if they do not share the same identity store, then the eduroam style would work but based on my understanding on how eduroam works you might face some challenges, like what i have seen in eduroam, the userX when he is in another location "location Y" he should use @AgencyX.com for username so that the RADIUS recognize that as a condition and that server would forward that to the external server. or you can add each and every AAA server as an external RADIUS server and in the conditions, and based on the client user name@HisAgnecy.com the request will be forwarded.
for the last part, in normal eduroam, the guest client will use the same VLAN that you currently have in your infrastructure, and cannot reach his original resources ONLY. "it provides normal internet access nothing more", i think you are using mobility anchor to force the client to go back to its original VLAN which i think is the only way to let the clients go back to their own VLAN. as the traffic goes encapsulated through EoIP.
i hope it makes sense.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
One thing came across my mind to keep the VLAN for each client...is load balancing between anchors, so create SSID's with WLAN ID higher than 16 "so that you can set the same name for multiple SSID's" and try to use this feature http://www.cisco.com/c/en/us/td/docs/wireless/controller/8-1/configuration-guide/b_cg81/b_cg81_chapter_010011100.html#concept_C25B66EA24BB4D439AE4B712F41CE35B
- « Previous
-
- 1
- 2
- Next »
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: