- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- Connectivity Issues when Firewall as default gateway
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
08-22-2010 01:20 PM - edited 03-08-2019 06:35 PM
Introduction
Firewalls, such as Cisco ASA and FWSM, use statefull inspection to protect traffic flows. One major requirement of successfully implementing statefull inspection is that both request (TCP SYN) and response (TCP SYN/ACK) must be seen by the firewall on the same corresponding ingress and egress interfaces. Otherwise, the firewall will treat it as TCP SYN attack or TCP SYN/ACK attack and drop the packet.
Core Issue
Topology
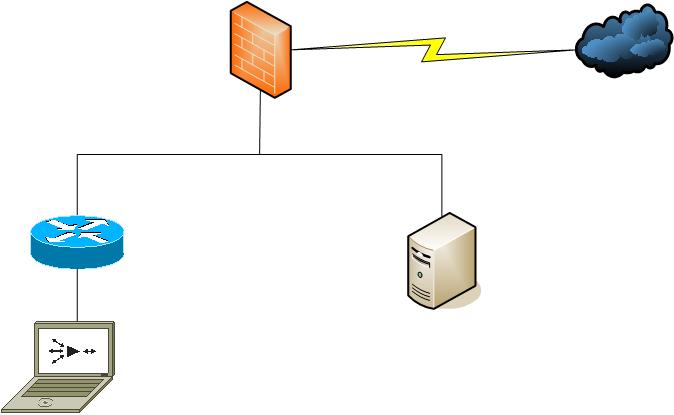
Resolution
1. To avoid the asymmetric traffic flow between servers and clients, the least disruptive change is to have the servers use the router/layer 3 as their default gateway. Ensure the router and layer 3 switch still uses the firewall as gateway for internet access. This is scaleable as you do not need to worry about how many vlans on the inside.
2. The other option is to use static routes on the servers such as traffic flow destined to inside nodes will use the inside router instead of the default gateway. This is not scaleable as you will need to add an entry for evey inside vlan subnets.
3. Add a DMZ interface on the firewall and move the servers behind it. This way, the servers are still protected from both the inside and internet access.
4. Enable tcp state-bypass on the Firewall specific to the traffic flow between the servers and clients. Note that this is only considered as a workaround and is not highly recommended. The reason is that TCP state-bypass disables the statefull inspection of the firewall. Either way, the traffic should not cross the firewall in the first place therefore the option may be acceptable depending on the company's security policy.
hostname(config)# access-list tcp_bypass extended permit tcp <servers-ip> <servers-subnet> <clients-ip> <clients-subnetmask>
hostname(config)# class-map tcp_bypass
hostname(config-cmap)# description "TCP traffic that bypasses stateful firewall"
hostname(config-cmap)# match access-list tcp_bypass
hostname(config-cmap)# policy-map tcp_bypass_policy
hostname(config-pmap)# class tcp_bypass
hostname(config-pmap-c)# set connection advanced-options tcp-state-bypass
hostname(config-pmap-c)# service-policy tcp_bypass_policy outside
Note: It is recommendated to more specific as much as possible when using tcp state-bypass. Check the release notes where
this feature is available.
Related Information
Checkout the configuration guide for more info on the TCP state bypass feature.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
just a word of caution, tcp state by pass is available on in 8.2 codes and later
also since asa randomizes the seq number it would be a good idea to turn it off for traffic destined to this server as the server would be responding to the randomised seq number and this can cause issues in some scenario'd depending on how the topology is
(config-pmap-c)# set connection random-sequence-number disable
also since tco state bypass is an option in the newer codes one might wonder how to get around this in older codes
use the static command
static (inside,inside) <ip> <ip> no-randomseq nailed
no-random disbales seq number randomization
nailed command achieves state bypass
these commands are now depracated from 8.2 and later with the introduction of state-by pass
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
TCP Sequence Number Randomization is automatically disabled on TCP bypassed flows.
The workaround that involves 'nailed' also requires 'failover timeout -1' and 'sysopt noproxyarp inside' commands; you may want to fix the syntax of 'static' line as well.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: