- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- Deploying Cisco WSA 11.7 with Cisco Identity Services Engine (ISE) 2.4 Using Cisco Platform Exchange...
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
01-24-2019 04:34 PM - edited 02-21-2020 10:02 PM
Author: John Eppich
Table of Contents
- About this Document
- Technical Details
- Configuring ISE-PIC
- Create a Common Join Point
- WSA pxGrid Configuration
- Using an External CA Server
- Import CA-Signed Cert
- Upload WSA certificate
- Enable ISE External RESTful Services
- Testing Communications with ISE pxGrid Node
- Verifying Connectivity
- Using ISE Internal CA
- Configuring WSA Policies
- Creating Security Group Tag (SGT) Policies
- Defining Identification Profile
- Creating Web Access Policy
- Testing
- Creating AD User-Based Policies
- Defining Identification Profile
- Creating Web Access Policy
- Testing
- References
About this Document
This document is for Cisco Engineers, partners and customers deploying Cisco Web Security Appliance (WSA) 11.7 with Cisco Identity Services Engine (ISE) ver. 2.4 using Cisco Platform Exchange Grid (pxGrid) 2.0.
Cisco pxGrid 2.0 does not use “java” or “C”-based SDK; instead pxGrid 2.0 uses WebSocket and REST API over STOMP Messaging Protocol.
WSA 11.7 includes ISE-PIC support and uses a combination of the ISE External RESTful Services (ERS) APIs and pxGrid 2.0 this functionality.
This document assumes that you have a full version of ISE installed and along with plus licenses for pxGrid so you have the ability to assign to Active Directory (AD) User groups to the WSA web access policies and Cisco Security Group Tags (SGT).
This document includes:
- Configuring ISE-PIC for WMI operation
- Configuring the WSA for pxGrid and ISE ERS Operation to illustrate assigning AD user groups to web access policies and assigning Cisco TrustSec Security Group Tags (SGT) to web access policies as well.
- Using external Certificate Authority (CA) and ISE internal CA for certificate operation
- Create web access policies for SGT of Employees to monitor all traffic
- Create web access policies to Deny Gambling sites for the IT Group based on the AD user groups obtained by the provider, Active Directory.
.
Technical Details
Cisco WSA 11.7 and above uses Cisco Platform Exchange Grid (pxGrid 2.0) for integration with Cisco Identity Services Engine (ISE) 2.4 and above. Cisco pxGrid 2.0 uses Websocket and REST APIs over the STOMP Messaging protocol. For more information on pxGrid 2.0 please see www.cisco.com/go/pxgridpartner
The WSA will subscribe to the /topic/com.cisco.ise.session topic, the /topic/com.cisco.ise.session.group and the /topic/com.cisco.ise.config.trustsec.security.group
The session topic provides a wealth of information about the authenticated session:
timestamp": "2017-06-29T13:22:46.788-07:00", "state": "STARTED", "userName": "user1", "callingStationId": "33:33:33:33:33:33", "auditSessionId": "101", "ipAddresses": ["1.2.3.4"], "macAddress": "33:33:33:33:33:33", "nasIpAddress": "172.21.170.242", "adNormalizedUser": "user1", "providers": ["None"], "endpointCheckResult": "none", "identitySourcePortStart": 0, "identitySourcePortEnd": 0, "identitySourcePortFirst": 0, "networkDeviceProfileName": "Cisco", "mdmMacAddress": "33:33:33:33:33:33", "mdmOsVersion": "9.3.5", "mdmRegistered": true, "mdmCompliant": true, "mdmDiskEncrypted": false, "mdmJailBroken": false, "mdmPinLocked": true, "mdmModel": "iPad mini", "mdmManufacturer": "Apple", "mdmImei": "dummy15", "mdmMeid": "dummy16", "mdmUdid": "dummy17", "mdmSerialNumber": "dummy18", "mdmDeviceManager": "sns"
The session group topic provides authenticated group identification, the provider attribute will contain the provider or authentication source details such as “Active Directory”,”External”, “Identity” for the authenticated groups. This also contains “interesting groups” related to ISE-PIC. The ISE Extended RESTful (ERS) APIs are used to the fetch the groups from the AD groups “interesting groups” and incorporate these groups in a WSA web access policy directly. You will be able to apply these groups directly:
The trustsec.security.group provides Security Group Details (SGT) such as id, name and description.
"id":"92adf9f0-8c01-11e6-996c-525400b48521","name":"Unknown","description":"Unknown Security Group","tag"
With pxGrid 2.0, the pxGrid client requests the ISE node publishing the services, i.e. com.cisco.ise.session, via a service lookup request. The ISE pxGrid node responds with the ISE node publishing this service, along with the WebSocket URL. The pxGrid client then requests an access secret with the published node and receives a response.
The pxGrid client then registers and connects to the published node, using certificates. The pxGrid node also subscribes to the topics. The status “ON” represents a successful WebSocket connection. If this were in the “OFF” position, there would be some type of network connectivity issues with the client.
Configuring ISE-PIC
ISE Passive Identity Connector (PIC) connector gathers user identities and IP addresses from external authentication servers such as Active Directory, known as providers, and then share that information with subscribers such as the WSA. ISE-PIC first receives the user identity information from the providers, usually based on the user login and password, and then performs the necessary checks and services in order to match the user identity with the relevant IP address, thereby delivering the authenticated IP address to the subscriber.
The flow for ISE-PIC is as follows:
-
Provider performs the authentication of the user or endpoint.
-
Provider sends authenticated user information to ISE-PIC.
-
ISE-PIC normalizes, performs lookups, merges, parses and maps user information to IP addresses and publishes mapped details to pxGrid.
-
pxGrid subscribers receive the mapped user details.
Create a Common Join Point
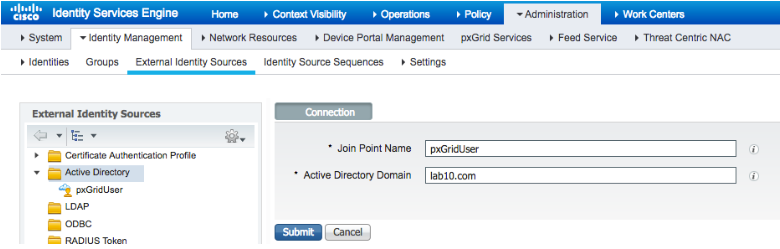
- Select Administration->Identity Management->External Identity Sources->Active Directory->Add the Joint Point Name, i.e.pxGridUser and the Active Directory Domain, i.e. lab10.com
- Select Submit
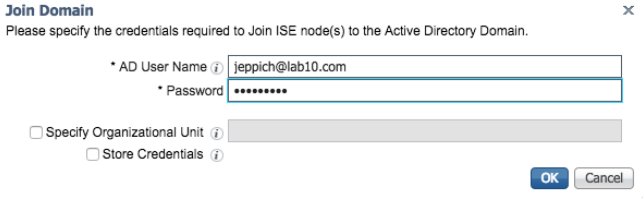
- Select Join, add the
- Select Ok
- You will be prompted to join the newly created join point to the domain, select Yes
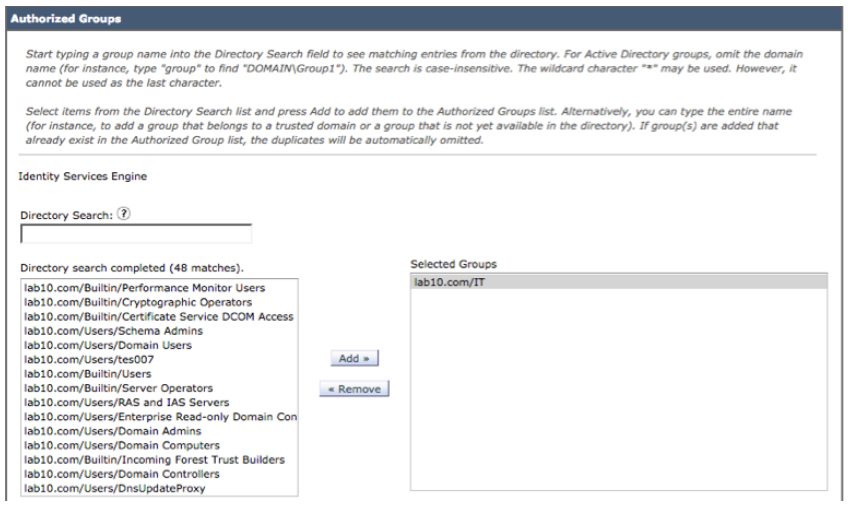
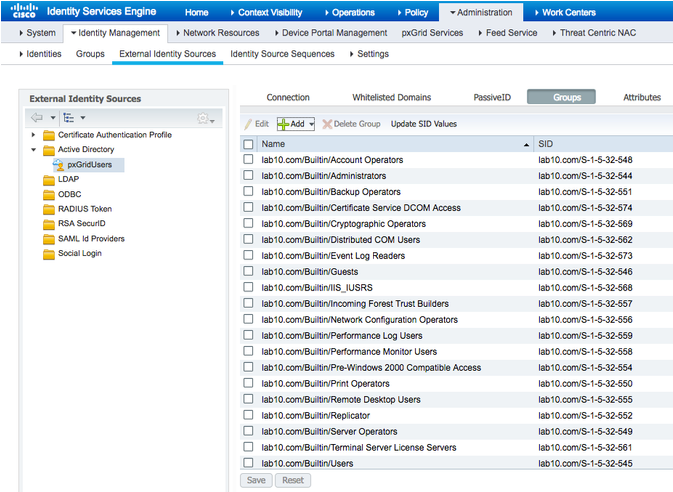
- Select Groups->Add->Select Directory Groups
- Select Retrieve Groups
You will see - Select OK
- Select Save
- Select Administration->Identity Management->External Identity Sources
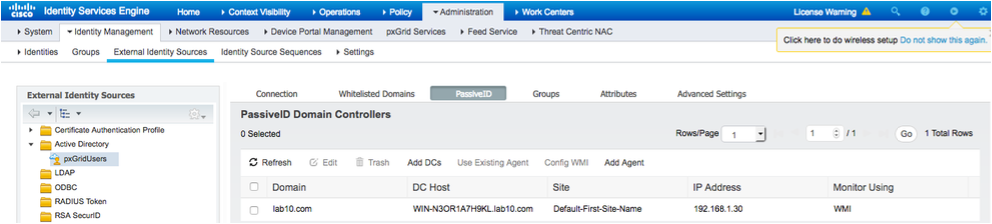
- Select PassiveID->Add DCs
- You should see the following
- Select the Domain Controller
- Select OK
You should see the following: - Select OK
You should see the following:
Note: in this example, WMI has already been configured. To configure WMI, select WMI, this may take a while to complete. You should see a successfully configured DC message. - Select Groups. You should see the groups already enabled for the initial AD setup:
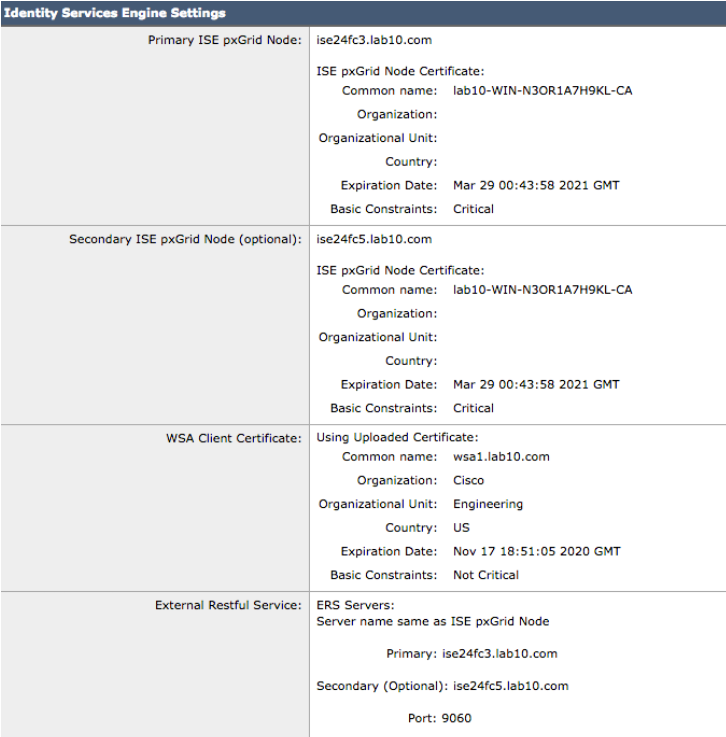
WSA pxGrid Configuration
In this section, an external Certificate Authority (CA) server was used for generating certificates for the WSA and the ISE pxGrid node. If you are not familiar with creating certificates using an external CA server, please see Deploying Certificates with pxGrid using an External CA with updates to ISE 2.0/2.1/2.2 . It is also assumed that you have created the ISE pxGrid node for external CA server operation, if you are not familiar with this, please see Deploying Certificates with pxGrid using an External CA with updates to ISE 2.0/2.1/2.2 . Additionally, if this is a productional ISE deployment, please see: Deploying pxGrid in a Productional ISE Deployment.
Using an External CA Server
Import CA-Signed Cert
-
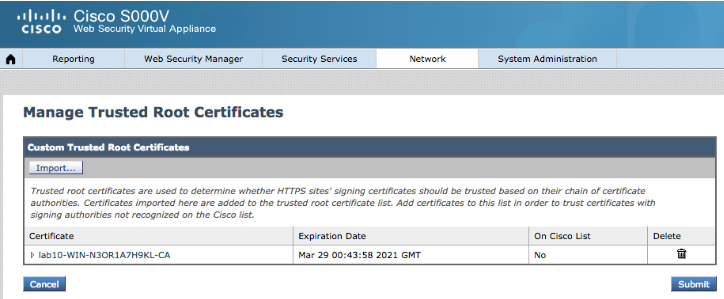
Select Network->Certificate Management->Managed Trusted Root Certificates
-
Select Import
-
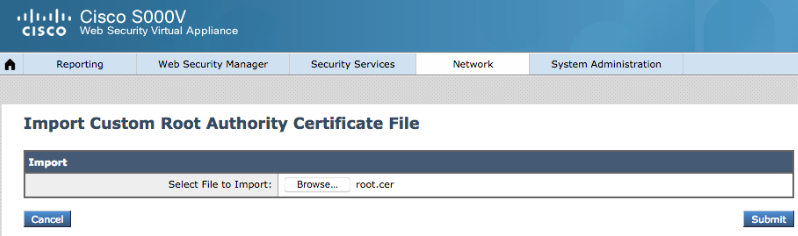
Upload root certificate
-
Select Submit
-
Select Network->Identification Services->Identity Services Engine->Enable ISE Service
-
Enter the host name or IP address of the primary pxGrid node. i.e. ise24fc3.lab10.com
-
Upload the external root CA
You should see the following:
-
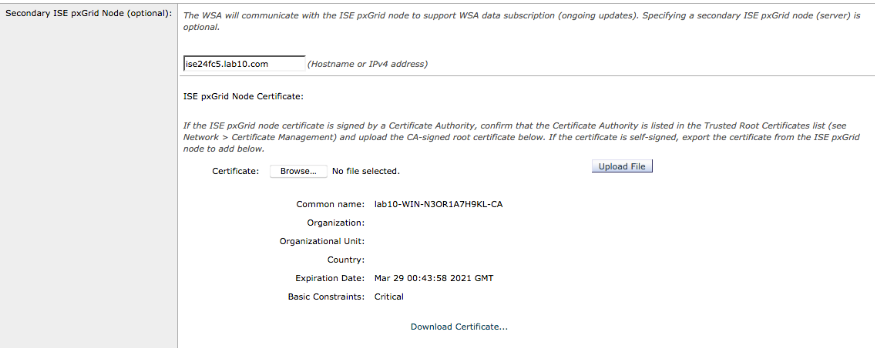
Enter Secondary ISE pxGrid node, i.e. ise24fc5.lab10.com
-
Upload CA root certificate
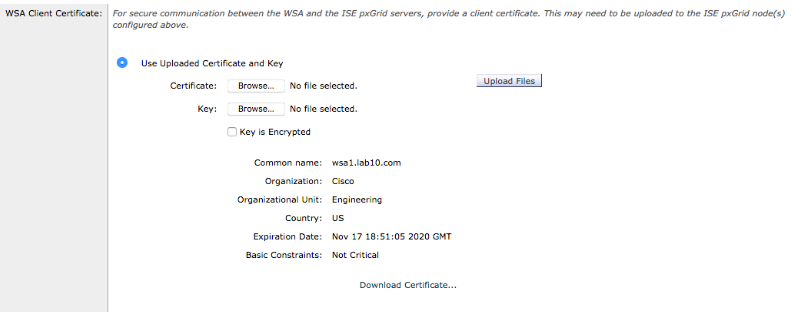
Upload WSA certificate
-
Upload the WSA certificate and WSA private key, enter encrypted password
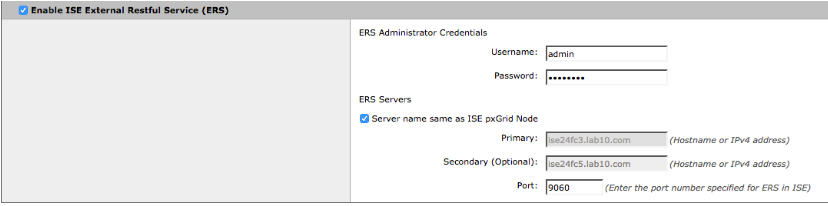
Enable ISE External RESTful Services
-
Enable ISE External RESTful Services
-
Enter the ERS Admin credentials for Username and Password
-
Select the ERS ISE Server
Testing Communications with ISE pxGrid Node
-
Under Test Communications with ISE Node, select Start Test and you should see :
Checking DNS resolution of ISE pxGrid Node hostname(s) ...
Success: Resolved 'ise24fc3.lab10.com' address: 192.168.1.251
Success: Resolved 'ise24fc5.lab10.com' address: 192.168.1.244
Validating WSA client certificate ...
Success: Certificate validation successful
Validating ISE pxGrid Node certificate(s) ...
Success: Certificate validation successful
Success: Certificate validation successful
Checking connection to ISE pxGrid Node(s) ...
Trying primary PxGrid server...
Completed TLS handshake with PxGrid successfully.
Trying download user-sessions...
Able to Download 20 user-sessions.
Trying download SGT...
Able to Download 21 SGTs.
Trying connecting to primary ERS service...
Trying download user-groups...
Able to Download 46 user-groups.
Trying connecting to secondary ERS service...
Trying download user-groups...
Able to Download 46 user-groups.
Success: Connection to ISE pxGrid Node was successful.
Trying secondary PxGrid server...
Completed TLS handshake with PxGrid successfully.
Trying download user-sessions...
Able to Download 2 user-sessions.
Trying download SGT...
Able to Download 21 SGTs.
Trying connecting to primary ERS service...
Trying download user-groups...
Able to Download 46 user-groups.
Trying connecting to secondary ERS service...
Trying download user-groups...
Able to Download 46 user-groups.
Success: Connection to ISE pxGrid Node was successful.
Test completed successfully.
Verifying Connectivity
-
To verify logs ssh admin@192.168.1.18
Type: tail ise_service_logs
You should see:Sun Nov 18 04:34:37 2018 Debug: Completed TLS handshake with PxGrid successfully.
Sun Nov 18 04:34:37 2018 Debug: PxGrid Response is : {"accountState":"ENABLED","version":"2.0.0.13"}
Sun Nov 18 04:34:37 2018 Debug: PxGrid Response is : {"services":[{"name":"com.cisco.ise.session","nodeName":"ise-mnt-ise24fc5","properties":{"sessionTopic":"/topic/com.cisco.ise.session","groupTopic":"/topic/com.cisco.ise.session.group","wsPubsubService":"com.cisco.ise.pubsub","restBaseURL":"https://ise24fc5.lab10.com:8910/pxgrid/mnt/sd","restBaseUrl":"https://ise24fc5.lab10.com:8910/pxgrid/mnt/sd"}},{"name":"com.cisco.ise.session","nodeName":"ise-mnt-ise24fc3","properties":{"sessionTopic":"/topic/com.cisco.ise.session","groupTopic":"/topic/com.cisco.ise.session.group","wsPubsubService":"com.cisco.ise.pubsub","restBaseURL":"https://ise24fc3.lab10.com:8910/pxgrid/mnt/sd","restBaseUrl":"https://ise24fc3.lab10.com:8910/pxgrid/mnt/sd"}}]}
Sun Nov 18 04:34:37 2018 Info: Name:( com.cisco.ise.session ) Node-Name:( ise-mnt-ise24fc5 ) Rest-Link:( https://ise24fc5.lab10.com:8910/pxgrid/mnt/sd )Topic:( /topic/com.cisco.ise.session ) service_name:(
Sun Nov 18 04:34:37 2018 Info: Name:( com.cisco.ise.session ) Node-Name:( ise-mnt-ise24fc3 ) Rest-Link:( https://ise24fc3.lab10.com:8910/pxgrid/mnt/sd )Topic:( /topic/com.cisco.ise.session ) service_name:(
Sun Nov 18 04:34:37 2018 Debug: PxGrid Response is : {"services":[{"name":"com.cisco.ise.config.trustsec","nodeName":"ise-admin-ise24fc3","properties":{"restBaseUrl":"https://ise24fc3.lab10.com:8910/pxgrid/ise/config/trustsec","securityGroupTopic":"/topic/com.cisco.ise.config.trustsec.security.group","wsPubsubService":"com.cisco.ise.pubsub"}}]}
Sun Nov 18 04:34:37 2018 Debug: Trying download user-sessions...
Sun Nov 18 04:34:37 2018 Debug: PxGrid Response is : {"sessions":[{"timestamp":"2018-11-14T19:30:21.861Z","state":"STARTED","userName":"00:01:5C:8E:52:46","callingStationId":"00:01:5C:8E:52:46","calledStationId":"50:3D:E5:C4:05:83","auditSessionId":"0A00000100000057011273DE","ipAddresses":[],"macAddress":"00:01:5C:8E:52:46","nasIpAddress":"192.168.1.3","nasPortId":"GigabitEthernet1/0/3","nasPortType":"Ethernet","adNormalizedUser":"00:01:5C:8E:52:46","providers":["None"],"endpointCheckResult":"none","identitySourcePortStart":0,"identitySourcePortEnd":0,"identitySourcePortFirst":0,"serviceType":"Framed","networkDeviceProfileName":"Cisco","radiusFlowType":"WiredMAB","ssid":"50-3D-E5-C4-05-83","mdmRegistered":false,"mdmCompliant":false,"mdmDiskEncrypted":false,"mdmJailBroken":false,"mdmPinLocked":false},{"timestamp":"2018-11-18T04:31:51.333Z","state":"STARTED","userName":"00:0C:29:01:5D:E8","callingStationId":"00:0C:29:01:5D:E8","calledStationId":"50:3D:E5:C4:05:8E","auditSessionId":"0A0000010000005902619242","ipAddresses":["192.168.1.13"],"macAddress":"00:0C:29:01:5D:E8","nasIpAddress":"192.168.1.3","nasPortId":"GigabitEthernet1/0/14","nasPortType":"Ethernet","endpointProfile":"Unknown","endpointOperatingSystem":"Windows 7 Professional","adNormalizedUser":"pxgrid5","providers":["WMI"],"endpointCheckResult":"none","identitySourcePortStart":0,"identitySourcePortEnd":0,"identitySourcePortFirst":0,"serviceType":"Framed","networkDeviceProfileName":"Cisco","radiusFlowType":"WiredMAB","ssid":"50-3D-E5-C4-05-8E","mdmRegistered":false,"mdmCompliant":false,"mdmDiskEncrypted":false,"mdmJailBroken":false,"mdmPinLocked":false},{"timestamp":"2018-11-18T04:33:24.301Z","state":"STARTED","userName":"00:0C:29:36:2E:14","callingStationId":"00:0C:29:36:2E:14","calledStationId":"50:3D:E5:C4:05:8D","auditSessionId":"0A00000100000051003EE10C","ipAddresses":["192.168.1.18"],"macAddress":"00:0C:29:36:2E:14","nasIpAddress":"192.168.1.3","nasPortId":"GigabitEthernet1/0/13","nasPortType":"Ethernet","endpointProfile":"Unknown","endpointOperatingSystem":"Linksys BEFW11S4 WAP (accuracy 89%)","adNormalizedUser":"00:0C:29:36:2E:14","providers":["None"],"endpointCheckResult":"none","identitySourcePortStart":0,"identitySourcePortEnd":0,"identitySourcePortFirst":0,"serviceType":"Framed","networkDeviceProfileName":"Cisco","radiusFlowType":"WiredMAB","ssid":"50-3D-E5-C4-05-8D","mdmRegistered":false,"mdmCompliant":false,"mdmDiskEncrypted":false,"mdmJailBroken":false,"mdmPinLocked":false},{"timestamp":"2018-11-18T04:20:12.979Z","state":"STARTED","userName":"00:0C:29:3C:4F:27","callingStationId":"00:0C:29:3C:4F:27","calledStationId":"50:3D:E5:C4:05:85","auditSessionId":"0A00000100000058019DFE75","ipAddresses":["192.168.1.244"],"macAddress":"00:0C:29:3C:4F:27","nasIpAddress":"192.168.1.3","nasPortId":"GigabitEthernet1/0/5","nasPortType":"Ethernet","endpointProfile":"ISE-Appliance","adNormalizedUser":"00:0C:29:3C:4F:27","providers":["None"],"endpointCheckResult":"none","identitySourcePortStart":0,"identitySourcePortEnd":0,"identitySourcePortFirst":0,"serviceType":"Framed","networkDeviceProfileName":"Cisco","radiusFlowType":"WiredMAB","ssid":"50-3D-E5-C4-05-85","mdmRegistered":false,"mdmCompliant":false,"mdmDiskEncrypted":false,"mdmJailBroken":false,"mdmPinLocked":false},{"timestamp":"2018-11-18T04:25:48.584Z","state":"STARTED","userName":"Administrator","callingStationId":"00:0C:29:7C:79:39","calledStationId":"50:3D:E5:C4:05:89","auditSessionId":"0A00000100000052004A0019","ipAddresses":["192.168.1.30"],"macAddress":"00:0C:29:7C:79:39","nasIpAddress":"192.168.1.3","nasPortId":"GigabitEthernet1/0/9","nasPortType":"Ethernet","endpointProfile":"Unknown","endpointOperatingSystem":"Windows Server 2008 R2 Enterprise","adNormalizedUser":"administrator","adUserDomainName":"lab10.com","adUserNetBiosName":"LAB10","adUserResolvedIdentities":"Administrator@lab10.com","adUserResolvedDns":"CN\u003dAdministrator,CN\u003dUsers,DC\u003dlab10,DC\u003dcom","providers":["WMI"],"endpointCheckResult":"none","identitySourcePortStart":0,"identitySourcePortEnd":0,"identitySourcePortFirst":0,"serviceType":"Framed","network
Sun Nov 18 04:34:37 2018 Debug: Able to Download 20 user-sessions.
Sun Nov 18 04:34:37 2018 Debug: Trying download SGT...
Sun Nov 18 04:34:37 2018 Debug: PxGrid Response is : {"securityGroups":[{"id":"92bb1950-8c01-11e6-996c-525400b48521","name":"ANY","description":"Any Security Group","tag":65535},{"id":"27f7f4b0-de0e-11e8-88f2-2e693f0641cd","name":"ASA","description":"","tag":19},{"id":"72c13a80-de0c-11e8-88f2-2e693f0641cd","name":"AccessSwitch","description":"","tag":18},{"id":"934557f0-8c01-11e6-996c-525400b48521","name":"Auditors","description":"Auditor Security Group","tag":9},{"id":"935d4cc0-8c01-11e6-996c-525400b48521","name":"BYOD","description":"BYOD Security Group","tag":15},{"id":"9370d4c0-8c01-11e6-996c-525400b48521","name":"Contractors","description":"Contractor Security Group","tag":5},{"id":"0dd4f730-4067-11e8-93b6-76ac7bb85424","name":"CustomIOTDevices","description":"","tag":17},{"id":"93837260-8c01-11e6-996c-525400b48521","name":"Developers","description":"Developer Security Group","tag":8},{"id":"9396d350-8c01-11e6-996c-525400b48521","name":"Development_Servers","description":"Development Servers Security Group","tag":12},{"id":"93ad6890-8c01-11e6-996c-525400b48521","name":"Employees","description":"Employee Security Group","tag":4},{"id":"93c66ed0-8c01-11e6-996c-525400b48521","name":"Guests","description":"Guest Security Group","tag":6},{"id":"70cf2080-3ff5-11e8-93b6-76ac7bb85424","name":"IOT_Devices","description":"","tag":16},{"id":"93e1bf00-8c01-11e6-996c-525400b48521","name":"Network_Services","description":"Network Services Security Group","tag":3},{"id":"93f91790-8c01-11e6-996c-525400b48521","name":"PCI_Servers","description":"PCI Servers Security Group","tag":14},{"id":"940facd0-8c01-11e6-996c-525400b48521","name":"Point_of_Sale_Systems","description":"Point of Sale Security Group","tag":10},{"id":"9423aa00-8c01-11e6-996c-525400b48521","name":"Production_Servers","description":"Production Servers Security Group","tag":11},{"id":"9437a730-8c01-11e6-996c-525400b48521","name":"Production_Users","description":"Production User Security Group","tag":7},{"id":"944b2f30-8c01-11e6-996c-525400b48521","name":"Quarantined_Systems","description":"Quarantine Security Group","tag":255},{"id":"94621290-8c01-11e6-996c-525400b48521","name":"Test_Servers","description":"Test Servers Security Group","tag":13},{"id":"947832a0-8c01-11e6-996c-525400b48521","name":"TrustSec_Devices","description":"TrustSec Devices Security Group","tag":2},{"id":"92adf9f0-8c01-11e6-996c-525400b48521","name":"Unknown","description":"Unknown Security Group","tag":0}]}
Sun Nov 18 04:34:37 2018 Debug: Able to Download 21 SGTs.
Sun Nov 18 04:34:37 2018 Debug: Trying connecting to primary ERS service...
Sun Nov 18 04:34:38 2018 Debug: Trying download user-groups...
Sun Nov 18 04:34:38 2018 Debug: Able to Download 46 user-groups.
Sun Nov 18 04:34:38 2018 Debug: Trying connecting to secondary ERS service...
Sun Nov 18 04:34:39 2018 Debug: Trying download user-groups...
Sun Nov 18 04:34:39 2018 Debug: Able to Download 46 user-groups.
Sun Nov 18 04:34:42 2018 Debug: Completed TLS handshake with PxGrid successfully.
Sun Nov 18 04:34:42 2018 Debug: PxGrid Response is : {"accountState":"ENABLED","version":"2.0.0.13"}
Sun Nov 18 04:34:42 2018 Debug: PxGrid Response is : {"services":[{"name":"com.cisco.ise.session","nodeName":"ise-mnt-ise24fc5","properties":{"sessionTopic":"/topic/com.cisco.ise.session","groupTopic":"/topic/com.cisco.ise.session.group","wsPubsubService":"com.cisco.ise.pubsub","restBaseURL":"https://ise24fc5.lab10.com:8910/pxgrid/mnt/sd","restBaseUrl":"https://ise24fc5.lab10.com:8910/pxgrid/mnt/sd"}},{"name":"com.cisco.ise.session","nodeName":"ise-mnt-ise24fc3","properties":{"sessionTopic":"/topic/com.cisco.ise.session","groupTopic":"/topic/com.cisco.ise.session.group","wsPubsubService":"com.cisco.ise.pubsub","restBaseURL":"https://ise24fc3.lab10.com:8910/pxgrid/mnt/sd","restBaseUrl":"https://ise24fc3.lab10.com:8910/pxgrid/mnt/sd"}}]}
Sun Nov 18 04:34:42 2018 Info: Name:( com.cisco.ise.session ) Node-Name:( ise-mnt-ise24fc5 ) Rest-Link:( https://ise24fc5.lab10.com:8910/pxgrid/mnt/sd )Topic:( /topic/com.cisco.ise.session ) service_name:(
Sun Nov 18 04:34:42 2018 Info: Name:( com.cisco.ise.session ) Node-Name:( ise-mnt-ise24fc3 ) Rest-Link:( https://ise24fc3.lab10.com:8910/pxgrid/mnt/sd )Topic:( /topic/com.cisco.ise.session ) service_name:
Sun Nov 18 04:34:42 2018 Debug: PxGrid Response is : {"services":[{"name":"com.cisco.ise.config.trustsec","nodeName":"ise-admin-ise24fc3","properties":{"restBaseUrl":"https://ise24fc3.lab10.com:8910/pxgrid/ise/config/trustsec","securityGroupTopic":"/topic/com.cisco.ise.config.trustsec.security.group","wsPubsubService":"com.cisco.ise.pubsub"}}]}
Sun Nov 18 04:34:42 2018 Debug: Trying download user-sessions...
Sun Nov 18 04:34:42 2018 Debug: PxGrid Response is : {"sessions":[{"timestamp":"2018-11-18T04:31:51.337Z","state":"STARTED","userName":"00:0C:29:01:5D:E8,pxgrid5","callingStationId":"192.168.1.13","calledStationId":"50:3D:E5:C4:05:8E","auditSessionId":"0A0000010000005902619242","ipAddresses":["192.168.1.13"],"macAddress":"192.168.1.13","nasIpAddress":"192.168.1.3","nasPortId":"GigabitEthernet1/0/14","nasPortType":"Ethernet","endpointProfile":"Unknown","adNormalizedUser":"pxgrid5","providers":["WMI"],"endpointCheckResult":"none","identitySourcePortStart":0,"identitySourcePortEnd":0,"identitySourcePortFirst":0,"serviceType":"Framed","networkDeviceProfileName":"Cisco","radiusFlowType":"WiredMAB","ssid":"50-3D-E5-C4-05-8E","mdmRegistered":false,"mdmCompliant":false,"mdmDiskEncrypted":false,"mdmJailBroken":false,"mdmPinLocked":false},{"timestamp":"2018-11-18T04:25:48.587Z","state":"STARTED","userName":"00-0C-29-7C-79-39,Administrator","callingStationId":"192.168.1.30","calledStationId":"50:3D:E5:C4:05:89","auditSessionId":"0A00000100000052004A0019","ipAddresses":["192.168.1.30"],"macAddress":"192.168.1.30","nasIpAddress":"192.168.1.3","nasPortId":"GigabitEthernet1/0/9","nasPortType":"Ethernet","adNormalizedUser":"administrator","adUserDomainName":"lab10.com","adUserNetBiosName":"LAB10","adUserResolvedIdentities":"Administrator@lab10.com","adUserResolvedDns":"CN\u003dAdministrator,CN\u003dUsers,DC\u003dlab10,DC\u003dcom","providers":["WMI"],"endpointCheckResult":"none","identitySourcePortStart":0,"identitySourcePortEnd":0,"identitySourcePortFirst":0,"serviceType":"Framed","mdmRegistered":false,"mdmCompliant":false,"mdmDiskEncrypted":false,"mdmJailBroken":false,"mdmPinLocked":false}]}
Sun Nov 18 04:34:42 2018 Debug: Able to Download 2 user-sessions.
Sun Nov 18 04:34:42 2018 Debug: Trying download SGT...
Sun Nov 18 04:34:42 2018 Debug: PxGrid Response is : {"securityGroups":[{"id":"92bb1950-8c01-11e6-996c-525400b48521","name":"ANY","description":"Any Security Group","tag":65535},{"id":"27f7f4b0-de0e-11e8-88f2-2e693f0641cd","name":"ASA","description":"","tag":19},{"id":"72c13a80-de0c-11e8-88f2-2e693f0641cd","name":"AccessSwitch","description":"","tag":18},{"id":"934557f0-8c01-11e6-996c-525400b48521","name":"Auditors","description":"Auditor Security Group","tag":9},{"id":"935d4cc0-8c01-11e6-996c-525400b48521","name":"BYOD","description":"BYOD Security Group","tag":15},{"id":"9370d4c0-8c01-11e6-996c-525400b48521","name":"Contractors","description":"Contractor Security Group","tag":5},{"id":"0dd4f730-4067-11e8-93b6-76ac7bb85424","name":"CustomIOTDevices","description":"","tag":17},{"id":"93837260-8c01-11e6-996c-525400b48521","name":"Developers","description":"Developer Security Group","tag":8},{"id":"9396d350-8c01-11e6-996c-525400b48521","name":"Development_Servers","description":"Development Servers Security Group","tag":12},{"id":"93ad6890-8c01-11e6-996c-525400b48521","name":"Employees","description":"Employee Security Group","tag":4},{"id":"93c66ed0-8c01-11e6-996c-525400b48521","name":"Guests","description":"Guest Security Group","tag":6},{"id":"70cf2080-3ff5-11e8-93b6-76ac7bb85424","name":"IOT_Devices","description":"","tag":16},{"id":"93e1bf00-8c01-11e6-996c-525400b48521","name":"Network_Services","description":"Network Services Security Group","tag":3},{"id":"93f91790-8c01-11e6-996c-525400b48521","name":"PCI_Servers","description":"PCI Servers Security Group","tag":14},{"id":"940facd0-8c01-11e6-996c-525400b48521","name":"Point_of_Sale_Systems","description":"Point of Sale Security Group","tag":10},{"id":"9423aa00-8c01-11e6-996c-525400b48521","name":"Production_Servers","description":"Production Servers Security Group","tag":11},{"id":"9437a730-8c01-11e6-996c-525400b48521","name":"Production_Users","description":"Production User Security Group","tag":7},{"id":"944b2f30-8c01-11e6-996c-525400b48521","name":"Quarantined_Systems","description":"Quarantine Security Group","tag":255},{"id":"94621290-8c01-11e6-996c-525400b48521","name":"Test_Servers","description":"Test Servers Security Group","tag":13},{"id":"947832a0-8c01-11e6-996c-525400b48521","name":"TrustSec_Devices","description":"TrustSec Devices Security Group","tag":2},{"id":"92adf9f0-8c01-11e6-996c-525400b48521","name":"Unknown","description":"Unknown Security Group","tag":0}]}
Sun Nov 18 04:34:42 2018 Debug: Able to Download 21 SGTs.
Sun Nov 18 04:34:42 2018 Debug: Trying connecting to primary ERS service...
Sun Nov 18 04:34:42 2018 Trace: Websocket, Received data: 0
Sun Nov 18 04:34:42 2018 Debug: Trying download user-groups...
Sun Nov 18 04:34:42 2018 Debug: Able to Download 46 user-groups.
Sun Nov 18 04:34:42 2018 Debug: Trying connecting to secondary ERS service...
Sun Nov 18 04:34:43 2018 Debug: Trying download user-groups...
Sun Nov 18 04:34:43 2018 Debug: Able to Download 46 user-groups.
Sun Nov 18 04:34:43 2018 Trace: Websocket, Received data: 0 -
Select Submit
-
Select Commit Changes twice
Using ISE Internal CA
Please to generate certificates for the WSA using the ISE internal CA, please see: Using ISE 2.2 Internal Certificate Authority (CA) to Deploy Certificates to Cisco Platform Exchange Grid (pxGrid) Clients.
The pxGrid certificate is signed by the default ISE internal CA by default.
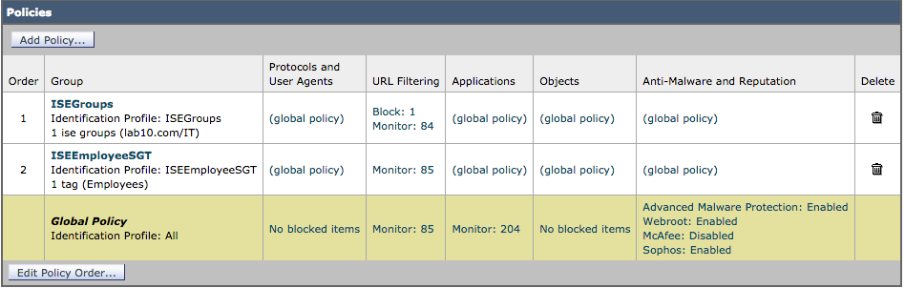
Configuring WSA Policies
In this section we create the identification profiles and web access policies for assigning Security Group Tag (SGT) and AD user groups these polices and also for assigning AD user groups.
Creating Security Group Tag (SGT) Policies
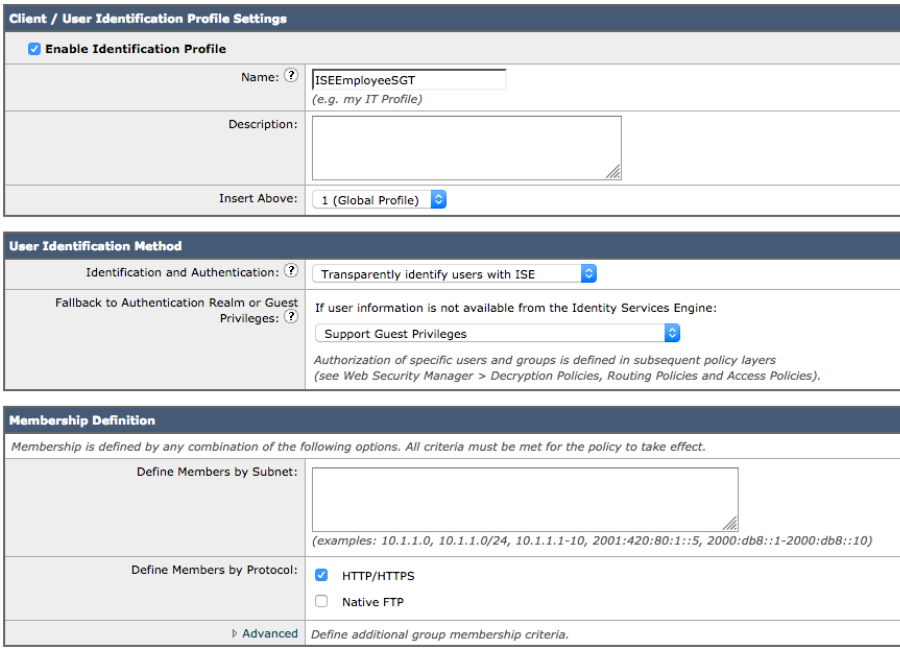
Defining Identification Profile
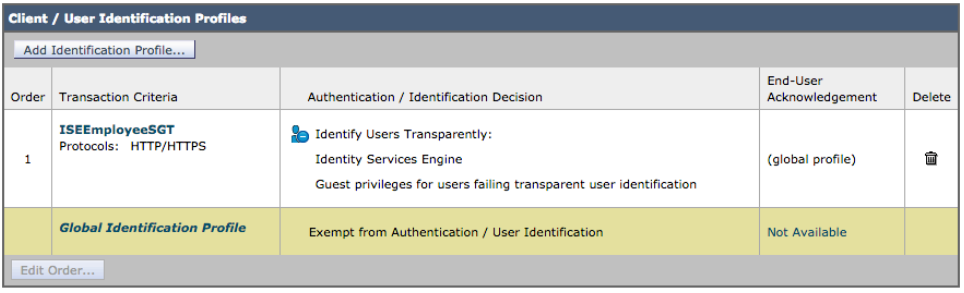
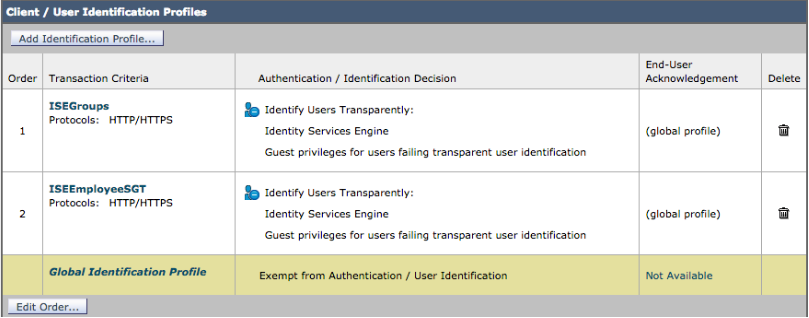
- Select Web Security Manager->Authentication->Identification Profiles->Add Identification Profile->Add the Name, i.e. ISEEmployeeSGT
- Under Identification and Authentication select Transparently Identify Users with ISE
- Select Submit
- Select Commit Changes twice
You should see:
Creating Web Access Policy
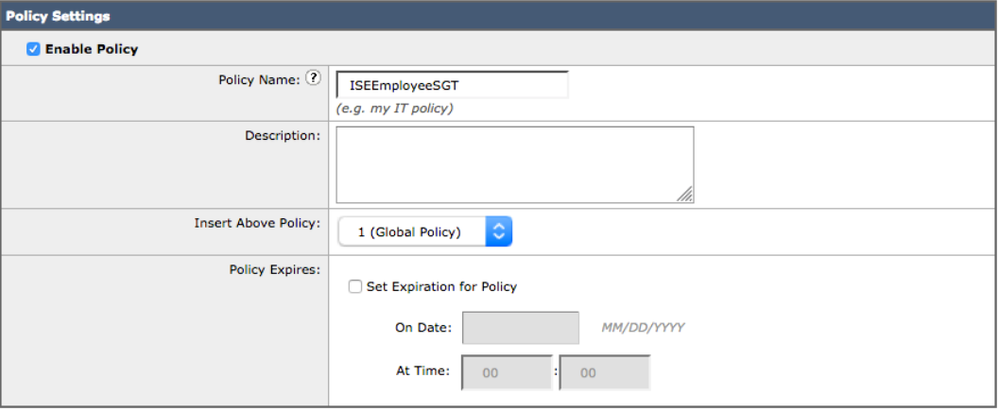
- Select Web Security Manager->Web Policies->Access Policies->Add Policy
- Enter Policy Name: ISEEmployeeSGT
- Under Policy Member Definition->Identification Profile and Users->Select One or More Identification Policies
- Under Identification Profile->select ISE from the drop-down
- Under Authorized Users and Groups->Selected Groups and Users->
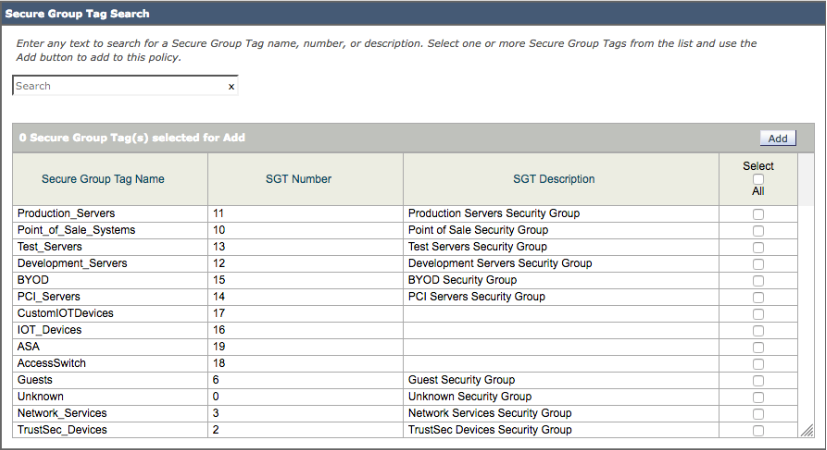
- Under ISE Security Group Tags->No Tags Entered
- Under Secure Group Tag Search, you should see:
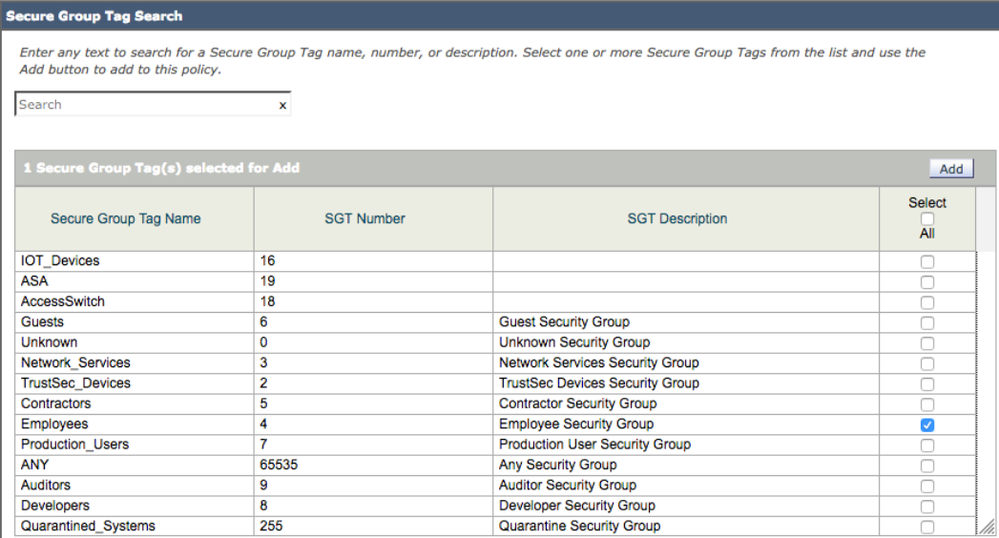
- Select SGT groups you want to add to a Web Access Policy
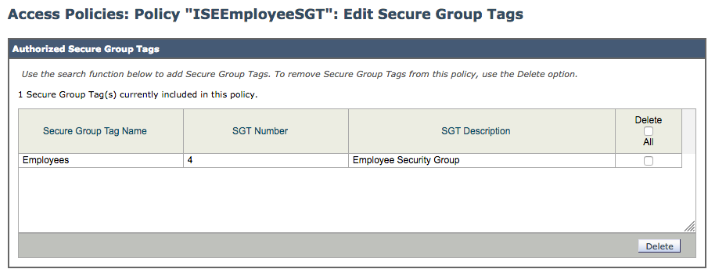
- In this use case, Employee was selected
- Select Add
- Under Authorized Secure Group Tags you should see
- Select Done
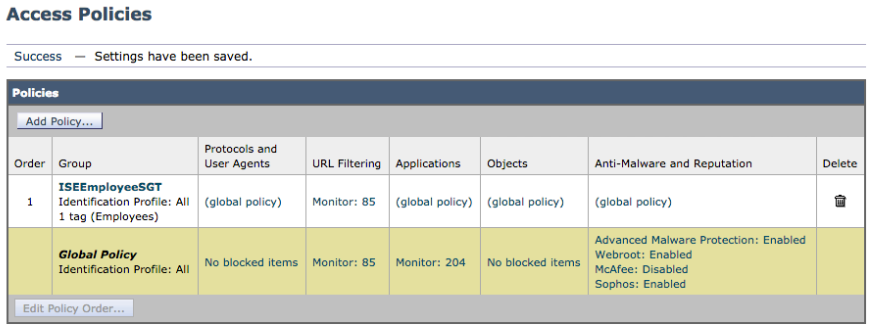
- Select Submit. You should see:
- Select Commit changes twice
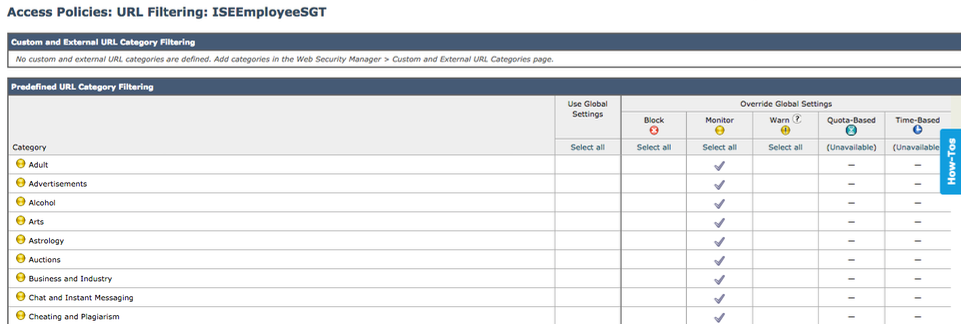
- Select Web Security Manager->ISEEmployeeSGT->URL Filtering
- Select Global Policy->Under Monitor, select all
- Select Submit and you should see:
- Select Commit Changes twice
Testing
-
User authenticates via 802.X access internet, user pxGrid2
-
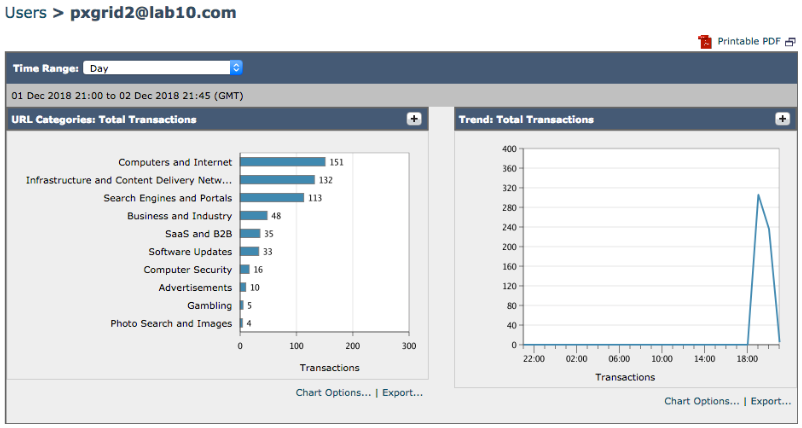
Verify the SGT IP Mapping
In the example below, pxGrid2@lab10.com has been assigned the Employee SGT which has a hex value of 4, as defined in ISE.
ssh admin@192.168.1.18
password: xxxxxx
wsa1.lab10.com:>isedata
Choose the operation you want to perform:
- STATISTICS - Show the ISE server status and ISE statistics.
- CACHE - Show the ISE cache or check an IP address.
- SGTS - Show the ISE Secure Group Tag (SGT) table.
- GROUPS - Show the ISE Groups table.
[]> CACHE
Choose the operation you want to perform:
- SHOW - Show the ISE ID cache.
- CHECKIP - Query the local ISE cache for an IP address
[]> SHOW
192.168.1.50 pxgrid2@lab10.com 4
192.168.1.150 00:0C:29:FE:3F:1F 0
10.0.0.7 74:E5:0B:4A:48:0C 0
192.168.1.251 00:0C:29:AD:40:27 0
10.0.0.1 44:32:C8:93:A0:E3 0
192.168.1.232 00:0C:29:FE:18:62 0
192.168.1.18 00:0C:29:36:2E:14 0
192.168.1.231 00:0C:29:8B:18:78 0
-
Verify the user has been assigned to the correct web access based on the SGT.
ssh admin@192.168.1.18
password: xxxxxx
wsa1.lab10.com>tail accesslogs
1543786057.280 269 192.168.1.27 TCP_CLIENT_REFRESH_MISS_SSL/200 39 CONNECT tunnel://unitedstates.smartscreen-prod.microsoft.com:443/ "pxgrid2@lab10.com" DIRECT/unitedstates.smartscreen-prod.microsoft.com - DECRYPT_ADMIN_DEFAULT_ACTION_7-DefaultGroup-ISEEmployeeSGT-NONE-NONE-NONE-DefaultGroup-NONE <IW_comp,ns,1,"-",-,-,-,-,"-",-,-,-,"-",-,-,"-","-",-,-,IW_comp,-,"-","Computers and Internet","-","Unknown","Unknown","-","-",1.16,0,-,"-","-",-,"-",-,-,"-","-",-,-,"-",-> - auth mechanism: SSO_ISE auth user: "pxgrid2@lab10.com"
1543786057.630 350 192.168.1.27 TCP_MISS_SSL/200 25366 GET https://unitedstates.smartscreen-prod.microsoft.com:443/windows/browser/edge/data/script/2 "pxgrid2@lab10.com" DIRECT/unitedstates.smartscreen-prod.microsoft.com text/plain DEFAULT_CASE_12-ISEEmployeeSGT-ISEEmployeeSGT-NONE-NONE-NONE-DefaultGroup-NONE <IW_comp,ns,1,"-",0,0,0,-,"-",-,-,-,"-",1,-,"-","-",-,-,IW_comp,-,"Unknown","Computers and Internet","-","Unknown","Unknown","-","-",579.79,0,-,"Unknown","-",0,"-",0,0,"AMP_NoFilename","f2156a842c5d93354459e4eedad575da34cc97f33d1d31bc5e2758a65e19c4d5",4,-,"-",-> - auth mechanism: SSO_ISE auth user: "pxgrid2@lab10.com"
Creating AD User-Based Policies
Defining Identification Profile
-
Select Web Security Manager->Authentication->Identification Profiles->Add Identification Profile->Add the Name, i.e. ISEGroups
-
Under Identification and Authentication select Transparently Identify Users with ISE
- Select Submit
-
Select Commit Changes twice
You should see the ISEGroups Identification Profile
Creating Web Access Policy
-
Select Web Security Manager->Web Policies->Access Policies->Add Policy
-
Enter Policy Name: ISEGroups
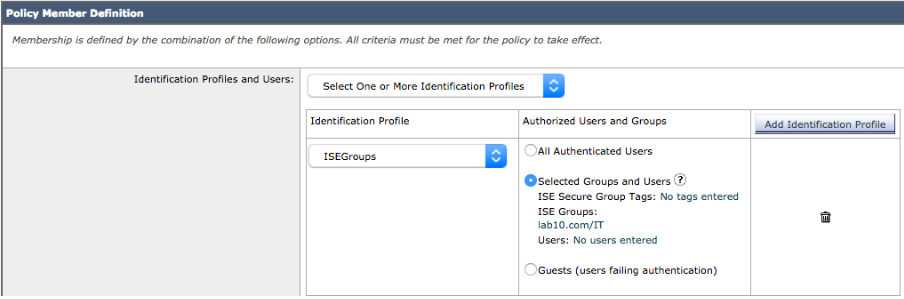
- Under Policy Member Definition->Identification Profile and Users->Select One or More Identification Policies
- Under Identification Profile->select ISE from the drop-down
- Under Authorized Users and Groups->Selected Groups and Users->
-
Under ISE Group Tags->No Groups Entered
-
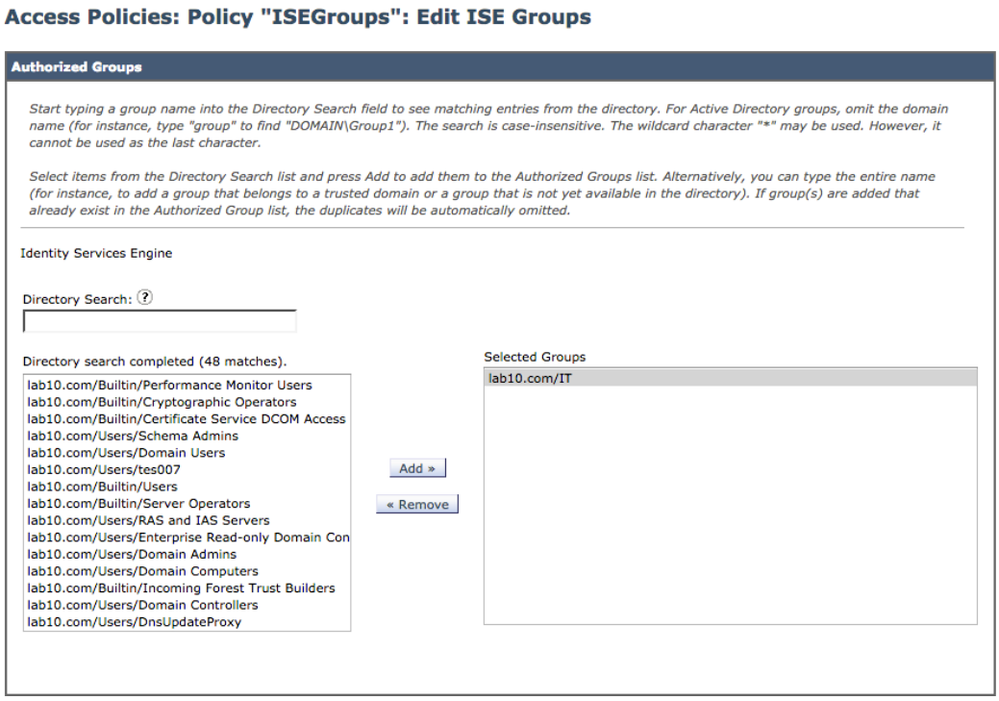
Under ISE Groups, select IT Groups
-
Select Done
You should see:
- Select Submit
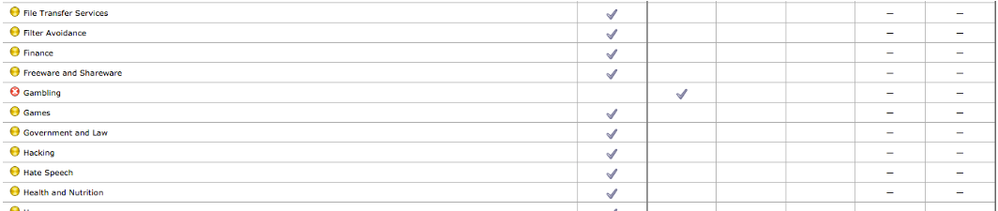
- Configure access policy to block gambling site
- Select Web Security Manager->ISEGroups->URL Filtering
- Select Global Policy->Under Block, select Gambling
-
Select Submit
You should see:
- Select Commit Changes twice
Testing
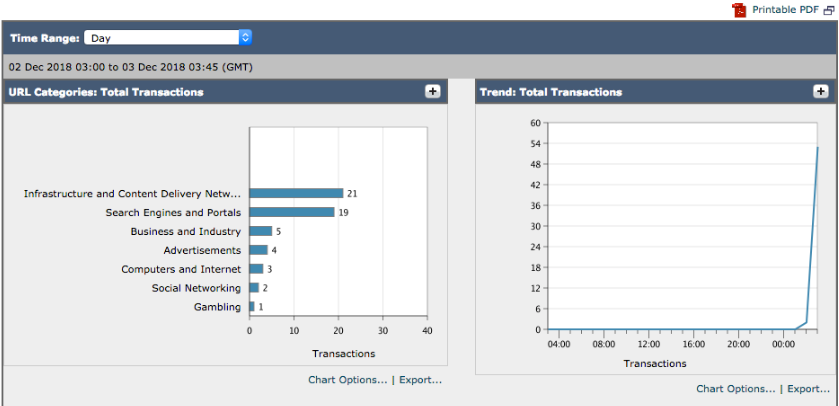
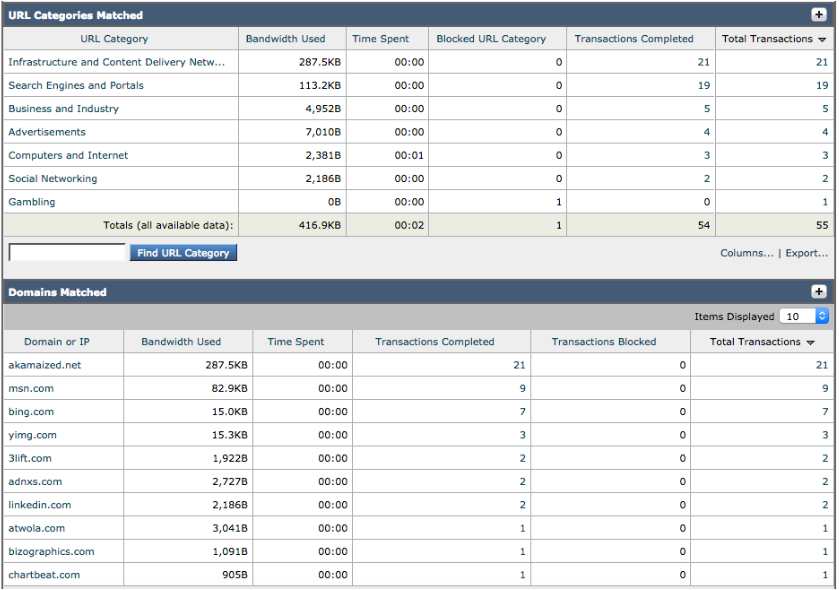
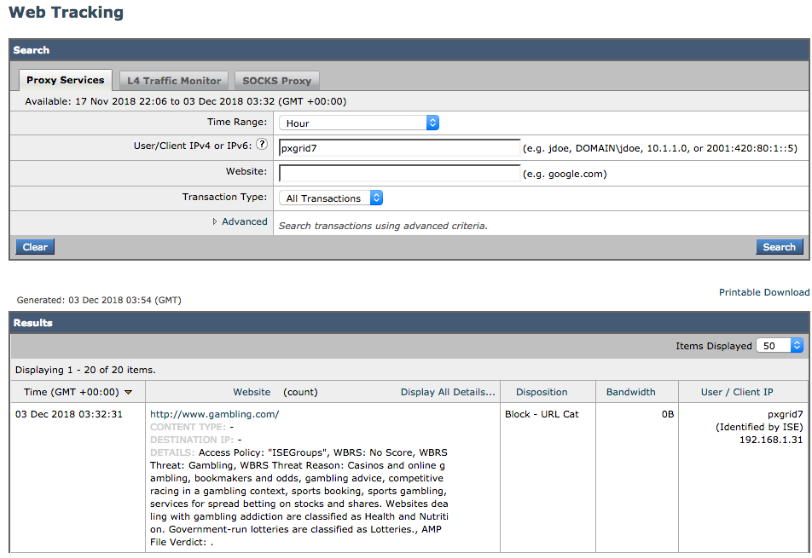
User pxGrid belonging to the AD IT group is denied access from going to Gambling sites.
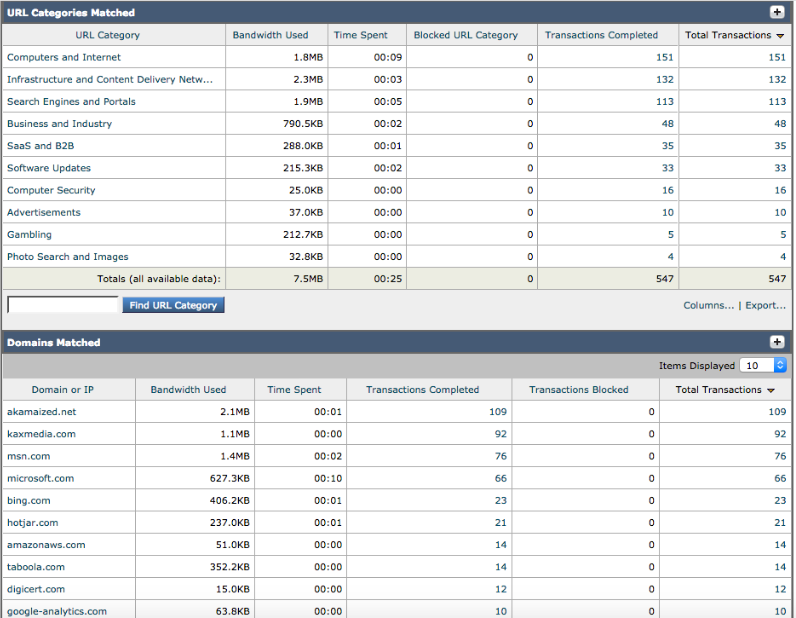
- Instead of the CLI, you can also verify the correct access policy for IT Groups, by accessing Reporting->Security Services->Web Tracking :
- Instead of the CLI, you can also verify the correct access policy for IT Groups, by accessing Reporting->Security Services->Web Tracking
Configure the custom fields with “auth mechanism: %m auth user: %A”
Submit and Commit the changes
ssh admin@192.168.1.18
password: xxxxxx
wsa1.lab10.com>tail accesslogs
1544133951.244 606 192.168.1.12 TCP_MISS_SSL/200 39 CONNECT tunnel://v10.events.data.microsoft.com:443/ "pxgrid2" DIRECT/v10.events.data.microsoft.com - DECRYPT_ADMIN_DEFAULT_ACTION_7-DefaultGroup-ISEGroups-NONE-NONE-NONE-DefaultGroup-NONE <IW_comp,ns,1,"-",-,-,-,-,"-",-,-,-,"-",-,-,"-","-",-,-,IW_comp,-,"-","Computers and Internet","-","Unknown","Unknown","-","-",0.51,0,-,"-","-",-,"-",-,-,"-","-",-,-,"-",-> - "auth mechanism: SSO_ISE auth group: "lab10.com/Builtin/Administrators,lab10.com/Builtin/Users,lab10.com/Users/Denied RODC Password Replication Group,lab10.com/Users/Enterprise Admins,lab10.com/Users/Domain Admins,lab10.com/Users/Domain Users" auth user: "pxgrid2"
References
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello all
Thanks for sharing.
I currently have problems related to the sequence policy in wsa, if the user successfully authenticates in cisco ISE and gets the employee SGT, but if the wsa access policy requires another SGT, the user will ignore it, how can I make the SGT in ISE automatically sync according to the needs of wsa?
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: