- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- FlexVPN: Anyconnect to IOS headend over IPsec with IKEv2 and certificates
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
04-20-2012 07:02 AM - edited 08-29-2017 02:39 AM
- Introduction
- Ingredients
- Headend
- Client
- Certificate authority
- Let's start cooking
- Headend configuration.
- Client
- Certificate authority
- Verification
- Known caveats & issues
- Troubleshooting
- Debugging
- Show commands
- DART package
- Further Reading & Documentation
Introduction
Several weeks ago I've given an overview of flex. It's is time to show what it can do.
As a starting point I picked a scenario one of my friends was interested in.
We want to have Anyconnect client connect to IOS box using IKEv2 with certificates as authentication for both sides - client and server.
No user authentication required - thus no need to perform EAP.
Please note that configuration below is not to be considered optimal.
It's meant to be a minimalistic configuration example.
Ingredients
Here are components I used.
Headend
As a headend I picked IOS 1941 router running 15.2(3)T release.
However if it's available you should use a newer release (please check "known caveats" section later on)
Client
Windows XP with Anyconnect 3.0.5 release, with DART package installed.
Certificate authority
As my certificate authority I picked up IOS device running 15.2(3)T release.
It is crucial that it's one of the newer releases, because we need it to support EKU (Extended Key Usage).
Let's start cooking
Let's see what needs to be configured.
Headend configuration.
Headend configuration is comprised ot two parts: the PKI part and actual flex/IKEv2.
PKI configuration
You will notice I use CN of bsns-1941-4.cisco.com - this needs to match a proper DNS entry and need to be included in Anyconnect profile.
crypto pki trustpoint CISCO2
enrollment url http://10.48.66.14:80
serial-number
ip-address 10.48.66.15
subject-name cn=bsns-1941-4.cisco.com,ou=TAC,o=cisco
revocation-check none
crypto pki certificate map CMAP 10
subject-name co cisco
Crypto/IPsec configuration
Please note that your PRF/integrity setting in proposal NEEDS to match what your certificate supports - typically it's SHA-1.
ip local pool AC 192.168.10.10 192.168.10.20
crypto ikev2 authorization policy AC
pool AC
crypto ikev2 proposal PRO
encryption 3des aes-cbc-128
integrity sha1
group 5 2
crypto ikev2 policy POL
match fvrf any
proposal PRO
crypto ikev2 profile PRO
match certificate CMAP
identity local dn
authentication remote rsa-sig
authentication local rsa-sig
pki trustpoint CISCO2
aaa authorization group cert list default AC
virtual-template 1
no crypto ikev2 http-url cert
crypto ipsec transform-set TRA esp-3des esp-sha-hmac
crypto ipsec profile PRO
set transform-set TRA
set ikev2-profile PRO
interface Virtual-Template1 type tunnel
ip unnumbered GigabitEthernet0/0
tunnel mode ipsec ipv4
tunnel protection ipsec profile PRO
Client
On client side two items need to be taken care of.
Importing the certificate from CA. I imported a pkcs12 that I generated on another router. The proper place to import is, in most cases, the personal store.
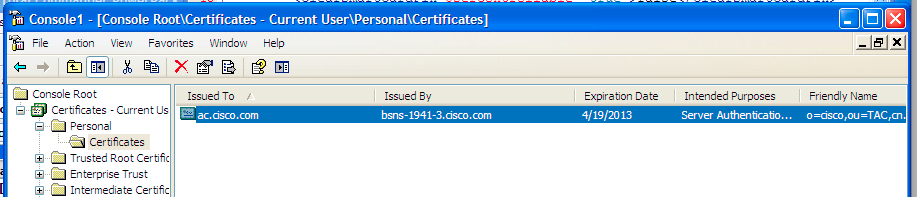
The Anyconnect profile was quite lengthy and very basic - it's attached to this document for reference (Profile_flex_ac_example.xml)
The relevent part is to define: host we will be connecting to, type of protocol and authentication to be used when connect to that host.
What I used:
<ServerList>
<HostEntry>
<HostName>bsns-1941-4.cisco.com</HostName>
<HostAddress>bsns-1941-4.cisco.com</HostAddress>
<PrimaryProtocol>IPsec
<StandardAuthenticationOnly>true
<AuthMethodDuringIKENegotiation>IKE-RSA</AuthMethodDuringIKENegotiation>
</StandardAuthenticationOnly>
</PrimaryProtocol>
</HostEntry>
</ServerList>
Certificate authority
You know that there are quite a bit of other documentation on how to configure IOS as CA. I will keep it short and show the relevant parts.
IOS CA configuration
You need to remember that CA server needs to put correct EKU on client AND server certificates.
In my case server-auth and client-auth EKU were set for all certificates.
bsns-1941-3#sh run | s crypto pki
crypto pki server CISCO
database level complete
database archive pem password 7 00071A1507545A545C
issuer-name cn=bsns-1941-3.cisco.com,ou=TAC,o=cisco
grant auto rollover ca-cert
grant auto
auto-rollover
eku server-auth client-auth
How to verify if correct EKU was set on certificate.
(Note that bsns-1941-3 is my CA server while bsns-1941-4 is my IPsec headend). Parts of output omitted for brevity.
BSNS-1941-4#sh cry pki cert ver
Certificate
(...omitted...)
Public Key Algorithm: rsaEncryption
RSA Public Key: (1024 bit)
Signature Algorithm: SHA1 with RSA Encryption
Fingerprint MD5: C3D52BE9 1EE97559 C7323995 3C51DC53
Fingerprint SHA1: 76BC7CD4 F298F8D9 A95338DC E5AF7602 9B57BE31
X509v3 extensions:
X509v3 Key Usage: A0000000
Digital Signature
Key Encipherment
X509v3 Subject Key ID: 83647B09 D3300A97 577C3E2C AAE7F47C F2D88ADF
X509v3 Authority Key ID: B3CC331D 7159C3CD 27487322 88AC02ED FAF2AE2E
Authority Info Access:
Extended Key Usage:
Client Auth
Server Auth
Associated Trustpoints: CISCO2
Storage: nvram:bsns-1941-3c#5.cer
Key Label: BSNS-1941-4.cisco.com
Key storage device: private config
CA Certificate
(...omitted...)
Verification
(Some information omitted for brevity)
BSNS-1941-4#sh crypto ikev2 sa
IPv4 Crypto IKEv2 SA
Tunnel-id Local Remote fvrf/ivrf Status
2 10.48.66.15/4500 10.55.193.212/65311 none/none READY
Encr: AES-CBC, keysize: 128, Hash: SHA96, DH Grp:5, Auth sign: RSA, Auth verify: RSA
Life/Active Time: 86400/180 sec
IPv6 Crypto IKEv2 SA
BSNS-1941-4#sh crypto ipsec sa
interface: Virtual-Access1
Crypto map tag: Virtual-Access1-head-0, local addr 10.48.66.15
protected vrf: (none)
local ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0)
remote ident (addr/mask/prot/port): (172.16.1.2/255.255.255.255/0/0)
current_peer 10.55.193.212 port 65311
PERMIT, flags={origin_is_acl,}
#pkts encaps: 2, #pkts encrypt: 2, #pkts digest: 2
#pkts decaps: 26, #pkts decrypt: 26, #pkts verify: 26
local crypto endpt.: 10.48.66.15, remote crypto endpt.: 10.55.193.212
path mtu 1500, ip mtu 1500, ip mtu idb GigabitEthernet0/0
current outbound spi: 0x5C171095(1545015445)
PFS (Y/N): N, DH group: none
inbound esp sas:
spi: 0x8283D0F0(2189676784)
transform: esp-3des esp-sha-hmac ,
in use settings ={Tunnel UDP-Encaps, }
conn id: 2003, flow_id: Onboard VPN:3, sibling_flags 80000040, crypto map: Virtual-Access1-head-0
sa timing: remaining key lifetime (k/sec): (4215478/3412)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
outbound esp sas:
spi: 0x5C171095(1545015445)
transform: esp-3des esp-sha-hmac ,
in use settings ={Tunnel UDP-Encaps, }
conn id: 2004, flow_id: Onboard VPN:4, sibling_flags 80000040, crypto map: Virtual-Access1-head-0
sa timing: remaining key lifetime (k/sec): (4215482/3412)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
Known caveats & issues
- Please remember to have following line configured on your IOS headend: no crypto ikev2 http-url cert.
The error produced by IOS and Anyconnect when this is not configured is quite misleading.
- In certain scenarios IOS might not be able to pick correct trustpoint to authenticate. We are aware of the issue, it should be fixed as of 15.2(3)T1 release. A tentative date for 15.2(3)T1 is 29th of June 2012.
- If Anyconnect is reporting message similar to this:
The client certificate's cryptographic service provider(CSP) does not support the sha512 algorithm
You need to make sure that the integrity/PRF setting in your IKEv2 proposals match what your certificates can handle. If you're using IOS CA like me I suggest using sha-1 and your PRF/Integrity setting.
Troubleshooting
Here's a few useful tips on how to troubleshoot, or if you're desparate, what to provide to TAC to smooth things out.
Debugging
Useful IKEv2 debugs (I'm assuming 15.2.2T or newer IOS version)
debug crypto ikev2
debug crypto ikev2 internal
debug crypto ikev2 packet
Useful PKI debugs
debug crypto pki m
debug crypto pki t
debug crypto pki v
Show commands
One that will be helpful the most is:
show crypto pki cert verb
DART package
If you would like TAC to look into this - provide a DART package. Please remember to CLEAR the event viewer logs before generating it.
This will help greatly.
Also note the time at which you've tried and failed connecting.
Further Reading & Documentation
You always should start with configuration guide. This particular
FlexVPN at a glance:
https://supportforums.cisco.com/community/netpro/security/vpn/blog/2012/03/19/flexvpn-at-a-glance
Standby for more articles on supportforums relating to flexVPN.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
I was looking for this, thanks
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: