- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- How Does NAT-T work with IPSec?
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
05-23-2011 01:20 AM - edited 08-24-2017 12:00 AM
Introduction:
This document describes details on how NAT-T works.
Background:
ESP encrypts all critical information, encapsulating the entire inner TCP/UDP datagram within an ESP header. ESP is an IP protocol in the same sense that TCP and UDP are IP protocols (OSI Network Layer 3), but it does not have any port information like TCP/UDP (OSI Transport Layer 4). This is a difference from ISAKMP which uses UDP port 500 as its transport layer.
PAT (Port Address Translation) is used to provide many hosts access to the internet through the same publically routable ip address. PAT works by building a database that binds each local host's ip address to the publically routable ip address using a specific port number. In this manner, any packet sourced from an inside host will have its IP header modified by the PAT devcie such that the source address and port number are changed from the RFC 1918 address/port to the publically routable ip address and a new unique port. Referencing this binding database, any return traffic can be untranslated in the same manner.
Q1: Why can't an ESP packet pass through a PAT device?
It is precisely because ESP is a protocol without ports that prevents it from passing through PAT devices. Because there is no port to change in the ESP packet, the binding database can't assign a unique port to the packet at the time it changes its RFC 1918 address to the publically routable address. If the packet can't be assigned a unique port then the database binding won't complete and there is no way to tell which inside host sourced this packet. As a result there is no way for the return traffic to be untranslated successfully.
Q2: How does NAT-T work with ISAKMP/IPsec?
NAT Traversal performs two tasks:
- Detects if both ends support NAT-T
- Detects NAT devices along the transmission path (NAT-Discovery)
Step one occurs in ISAKMP Main Mode messages one and two. If both devices support NAT-T, then NAT-Discovery is performed in ISKAMP Main Mode messages (packets) three and four. THe NAT-D payload sent is a hash of the original IP address and port. Devices exchange two NAT-D packets, one with source IP and port, and another with destination IP and port. The receiving device recalculates the hash and compares it with the hash it received; if they don't match a NAT device exists.
If a NAT device has been determined to exist, NAT-T will change the ISAKMP transport with ISAKMP Main Mode messages five and six, at which point all ISAKMP packets change from UDP port 500 to UDP port 4500. NAT-T encapsulates the Quick Mode (IPsec Phase 2) exchange inside UDP 4500 as well. After Quick Mode completes data that gets encrypted on the IPsec Security Association is encapsulated inside UDP port 4500 as well, thus providing a port to be used in the PAT device for translation.
To visualize how this works and how the IP packet is encapsulated:
- Clear text packet will be encrypted/encapsulated inside an ESP packet
- ESP packet will be encapsulated inside a UDP/4500 packet.
NAT-T encapsulates ESP packets inside UDP and assigns both the Source and Destination ports as 4500. After this encapsulation there is enough information for the PAT database binding to build successfully. Now ESP packets can be translated through a PAT device.
When a packet with source and destination port of 4500 is sent through a PAT device (from inside to outside), the PAT device will change the source port from 4500 to a random high port, while keeping the destination port of 4500. When a different NAT-T session passes through the PAT device, it will change the source port from 4500 to a different random high port, and so on. This way each local host has a unique database entry in the PAT devices mapping its RFC1918 ip address/port4500 to the public ip address/high-port.
Q3: What is the difference between NAT-T and IPSec-over-UDP ?
Although both these protocols work similiar, there are two main differences.
- When NAT-T is enabled, it encapsulates the ESP packet with UDP only when it encounters a NAT device. Otherwise, no UDP encapsulation is done. But, IPSec Over UDP, always encapsulates the packet with UDP.
- NAT-T always use the standard port, UDP-4500. It is not configurable. IPSec over UDP normally uses UDP-10000 but this could be any other port based on the configuration on the VPN server.
Example:
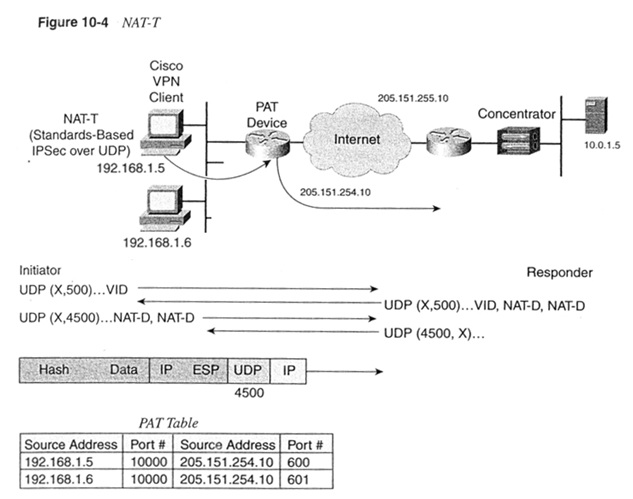
In above diagram, how does the device with PAT make unique identifiers in the PAT Table for both users if NAT-T sets the source and destination UDP ports 4500 ?
If client A sends a packet, the packet will have the form:
src: 192.168.1.5:4500 dst: 205.151.255.10:4500 - > src: 205.151.254.10:600 dst: 205.151.255.10:4500
If client B sends a packet, the packet will have the form:
src: 192.168.1.6:4500 dst: 205.151.255.10:4500 - > src: 205.151.254.10:601 dst: 205.151.255.10:4500
the response from the server will have the form to each Client:
src: 10.0.1.5:80 dst: 205.151.254.10:600 - > src: 205.151.255.10:4500 dst: 205.151.254.10:600
src: 10.0.1.5:80 dst: 205.151.254.10:601 - > src: 205.151.255.10:4500 dst:
205.151.254.10:601
References-----
Here is the RFC for the IPSec aware NAT (NAT-Traversal) for your reference:
http://datatracker.ietf.org/doc/rfc3947/
(It includes the full explaination of the negotiation for your reference)
Document was create from the following discussion thread----
https://supportforums.cisco.com/thread/2049410?tstart=0
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thank you for this article.
With this information, I was able to solve the connection to another customers asa/pix devices. This has been a problem for me since 5 years. Life gets easier because of your help!
Paul
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi Athukral,
The is an excellent article on NAT-T.
In the above example, we understand that the client 192.168.1.5 is trying to establish a connectivity to the server 10.0.1.5 over port 80 i.e. as per the interesting traffic defined.
I would really appreciate if the below points could be cleared:
i)
Datagram flow with IP and port modifications when 192.168.1.5: 10000 tries to establish connection to 10.0.1.5:80
ii)
NAT-T functionality in case we have overlapping subnets wherein we have to NAT the traffic at one end before sending it to the other.
@Experts: Please help.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello,
very nice article athukral. I have got better understanding of NAT-T, anyway I would like to ask you, when VPN peer2 got a hash of source IP adress and the port of VPN peer1 which don't match, at this point will VPN peer2 start to use public IP address of VPN peer1 for another communication with him or the process is little bit different? (let's say that DNAT is used to reach VPN peer1).
Thank you in advance,
Martin
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thank alotzzzzzzz
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Very detailed, yet briefed and useful. Great explanation.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Brief, clear and very great explanation!!!
Thanks!!
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thank you. You have explained this much better than the Cisco CCNA Security OCG. They should take the money they gave to the writers of that book and redirect some of that to you!
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Nice article Athul. Before coming across your article I did not know there was is something called "IPsec-over-UDP" which is different from NAT-T.
Could you please let me know if there is any RFC or more detailed documentation on "IPsec-over-UDP"which has details on -
1) The need for "IPsec-over-UDP"
2) Its advantages
3) How it works
Thanks,
-Ravi
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Network Address Translation-Traversal (NAT-T) is a method for getting around IP address translation issues encountered when data protected by IPsec passes through a NAT device for address translation. Any changes to the IP addressing, which is the function of NAT, causes IKE to discard packets. After detecting one or more NAT devices along the datapath during Phase 1 exchanges, NAT-T adds a layer of User Datagram Protocol (UDP) encapsulation to IPsec packets so they are not discarded after address translation. NAT-T encapsulates both IKE and ESP traffic within UDP with port 4500 used as both the source and destination port. Because NAT devices age out stale UDP translations, keepalive messages are required between the peers.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Great Explanation! Thanks!
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Awesome and simple explanation. Thank you.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thanks a lot
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
very nice document,
Cleared my doubts related to NAT-T.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
NAT-D will calculate the hashes on both VPN peer .Hash will be calculated based on Vendor ID , Source Port , Destination port , Source ip and destination IP . once receive on both VPN peer they will check individually with this value along with their own individual . if matches then we can assume there is no NAT device present in between VPN peer . if this is true , then how it will detect the PAT device ? will it works in same way ?
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community:



