- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- ISE 2.3 - TACACS+ - Command sets import and Export
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
on 09-14-2017 07:27 PM
In TACACS+ command authorization phase an IOS device will query the configured ISE (TACACS+) server to verify whether the device administrators are authorized to issue the commands. ISE can provide a list of commands granted to the users to fine tune which commands are available at various privilege levels.
ISE 2.3 allows you to import and export command sets using a csv file for all these command sets. ISE 2.3 provides a template where you can fill in the command sets.
First, we will discuss the formatting of command sets that needs to be imported.
Wildcards and Regex in Command Sets
An IOS command using CLI comprises the command and zero or more arguments. When Cisco ISE receives a command line (request), it handles the command and its arguments in different ways:
It matches the command in the request with the commands specified in the command set list using the wildcard matching paradigm.
Example: Sh?? or S*
It matches the arguments in the request with the arguments specified in the command set list using regular expressions (regex) matching paradigm.
Example: Show interface[1-4] port[1-9]:tty*
Command Line and Command Set List Match
To match a requested command line to a command set list containing wildcards and regex:
Cisco ISE will iterate over a command set list to detect matching commands obeying the following rules.
If there are wildcard matches in the commands following will apply
- Case insensitivity
- Any character in the command in the command set may be "?", which matches any individual character that must exist in the requested command
- Any character in the command in the command set may be "*", which matches zero or more characters in the requested command
Examples:
| Request | Command Set | Matches | Comments |
show | show | Y | — |
show | SHOW | Y | Case insensitive |
show | Sh?? | Y | Matches any character |
show | Sho?? | N | Second "?" intersects with the character that does not exist |
show | S* | Y | "*" matches any character |
show | S*w | Y | "*" matches characters "ho" |
show | S*p | N | Character "p" does not correspond |
For each matching command, Cisco ISE validates the arguments. (Note: Use standard UNIX regular expressions for arguments)
- The command set list will include a space-delimited set of arguments for each command.
Example: Show interface[1-4] port[1-9]:tty.*
This command has two arguments.
- Argument 1: interface[1-4]
- Argument 2: port[1-9]:tty.*
The command arguments in the request are taken in the position-significant order they appear in the packet. If all the arguments in the command definition match the arguments in the request, then this command/argument is said to be matched. Note that any extraneous arguments in the request are ignored.
Import Command Sets
ISE 2.3 introduced a way to import and export command sets from a csv file. For the sake of example and learning a csv file is attached at the end of the community page that you can download and copy to your local machine. Here are the following steps to import.
1. From the ISE UI, go to Work Centers > Device Administration > Policy Elements > TACACS Command Sets.
2. Click Import from the list of options on the right panel.
A window opens up asking you to “Import Command Sets”.
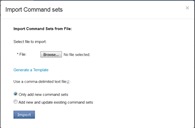
3. Click “Generate a template” option shown in screenshot above and save the Export_SommandSet csv file.
4. Here is the format of the template table and their description
name:String(64):Required | description:String(1024) | permit_unmatched:Boolean(true/false) | commands:Commands(Grant/command/arguments;Grant/command/arguments...) |
Name: Name of the command set (mandatory field)
Description: A brief description of the intended use of the command set
Permit_unmatched: Permit commands that are not listed (TRUE/FALSE)
Commands: Consists of Commands that includes GRANT, COMMAND and ARGUMENT as shown in example below separated by “/” character.
5. Please see the csv file of all the command sets attached at the bottom of the community page. Download and save it to your hard disk.
Here is the description of the command sets used.
helpDeskCmds Command set
Here is a list of commands that can be used to perform basic monitoring and troubleshooting functions in a IOS Network device.
Grant | Command | Argument |
PERMIT | *debug | |
PERMIT | traceroute | |
DENY | ping | ([0-9]{1,3}\.){3}255 |
PERMIT | ping | |
PERMIT | show |
We allow helpdesk analysts to perform debug, undebug, traceroute, and show. For ping, they are restricted from broadcast pings, assuming the network subnets with broadcast addresses ending with .255, as shown in the regular expression in the argument column.
iosSecCmds Command set
Here is a list of commands that can be used to perform basic administrative function that includes interface configuration.
Grant | Command | Argument |
PERMIT | config* | |
DENY_ALWAYS | interface | GigabitEthernet 1 |
DENY_ALWAYS | interface | GigabitEthernet [0-9]{1,3} 0 |
PERMIT | interface | |
PERMIT | shut | |
PERMIT | no | shut |
In this sample command set, security administrators may perform shut and no shut operations on any interfaces except the two types of interfaces specified in the DENY_ALWAYS entries, where the second type designates an interface pattern GigabitEthernet <0-999>/0.
pemitAllCmds Command set
Permits all commands for super admin.
7. From the ISE UI, go to Work Centers > Device Administration > Policy Elements > TACACS Command Sets. Click the Import button from the right panel that opens up a window “Import Command sets”.
8. Click Browse button to open the Windows explorer and go to the folder you saved the csv file, select the file by double clicking the file. Click Import button to complete the process.
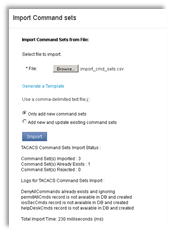
9. You will see the Import Status, Logs and the time taken as shown in the screenshot below.
10. While importing you have two options to add and update existing command sets. By default you the “Only add new command sets” is selected. If you want to update the command sets you have to choose the second option and upload the csv file.
11. You can also export the command set from ISE UI, go to Work Centers > Device Administration > Policy Elements > TACACS Command Sets.
12. The exported csv file will have a default deny command set, a command set available by default.
13. Once you created the command sets, you can add the command sets to the authorization policy. From ISE UI, go to Work Centers > Device Administration > Policy sets, expand it by clicking >, go to the authorization policy and select the command sets from the dropdown.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Can you share the csv file example attachment you mentioned?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Very useful thank you
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Please share the csv file if possible.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community:

