Introduction
This document describes how to configure a LAN-to-LAN (L2L) IPsec tunnel between two ASA (8.4.x). Each security appliance has a private protected network behind it.
A tunnel is formed using IPsec. IPsec is a combination of open standards that provide data confidentiality, data integrity, and data origin authentication between IPsec peers.
Prerequisites
Requirements
There are no specific requirements for this document.
Component Used
Cisco ASA 5510 Series Security Appliance with version 8.4.x and later
Network Diagram:
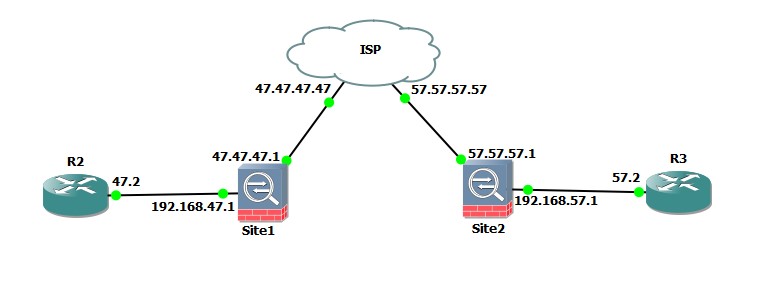
Site 1 Configuration
ASA Version 8.4(2)
!
hostname Site1
enable password welcome@12
names
!
interface GigabitEthernet0
nameif outside
security-level 0
ip address 47.47.47.1 255.255.255.0
!
object network obj_192.168.47.0
subnet 192.168.47.0 255.255.255.0
!
object network local_192.168.47.0
subnet 192.168.47.0 255.255.255.0
description "For NAT exempt"
!
object network remote_192.168.57.0
subnet 192.168.57.0 255.255.255.0
description "remote subnet for Site2"
!
access-list outside_in extended permit icmp any any
access-group outside_in in interface outside
!
access-list crypto-access extended permit ip 192.168.47.0 255.255.255.0 192.168.57.0 255.255.255.0
!
logging enable
logging buffered debugging
!
nat (inside,outside) source static local_192.168.47.0 local_192.168.47.0 destination static remote_192.168.57.0 remote_192.168.57.0 no-proxy-arp route-lookup
!
object network obj_192.168.47.0
nat (inside,outside) dynamic interface
!
route outside 0.0.0.0 0.0.0.0 47.47.47.47 1
!
crypto ipsec ikev1 transform-set ESP-3DES-SHA esp-3des esp-sha-hmac
!
crypto map outside_map 1 match address crypto-access
crypto map outside_map 1 set peer 57.57.57.1
crypto map outside_map 1 set ikev1 transform-set ESP-3DES-SHA
crypto map outside_map interface outside
!
crypto ikev1 enable outside
crypto ikev1 policy 10
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 86400
!
telnet timeout 5
ssh timeout 5
console timeout 0
!
management-access inside
!
ntp server 47.47.47.47
!
tunnel-group 57.57.57.1 type ipsec-l2l
tunnel-group 57.57.57.1 ipsec-attributes
ikev1 pre-shared-key cisco123
!
: end
Site 2 Configuration
ASA Version 8.4(2)
!
hostname Site2
enable password welcome@12
names
!
interface GigabitEthernet0
nameif outside
security-level 0
ip address 57.57.57.1 255.255.255.0
!
!
interface GigabitEthernet1
nameif inside
security-level 100
ip address 192.168.57.1 255.255.255.0
!
object network obj_192.168.57.0
subnet 192.168.57.0 255.255.255.0
!
object network local_192.168.57.0
subnet 192.168.57.0 255.255.255.0
!
object network remote_192.168.47.0
subnet 192.168.47.0 255.255.255.0
!
access-list outside_in extended permit icmp any any
access-group outside_in in interface outside
!
access-list crypto_access extended permit ip 192.168.57.0 255.255.255.0 192.168.47.0 255.255.255.0
!
logging enable
logging buffered debugging
!
!
nat (inside,outside) source static local_192.168.57.0 local_192.168.57.0 destination static remote_192.168.47.0 remote_192.168.47.0 no-proxy-arp route-lookup
!
object network obj_192.168.57.0
nat (inside,outside) dynamic interface
!
route outside 0.0.0.0 0.0.0.0 57.57.57.57 1
!
crypto ipsec ikev1 transform-set ESP-3DES-SHA esp-3des esp-sha-hmac
!
crypto map outside_map 1 match address crypto_access
crypto map outside_map 1 set peer 47.47.47.1
crypto map outside_map 1 set ikev1 transform-set ESP-3DES-SHA
crypto map outside_map interface outside
!
crypto ikev1 enable outside
crypto ikev1 policy 10
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 86400
!
tunnel-group 47.47.47.1 type ipsec-l2l
tunnel-group 47.47.47.1 ipsec-attributes
ikev1 pre-shared-key cisco123
!
: end
Debugs Are attached.