- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- Router Security: Snort IPS on Routers - Step-by-Step Configuration
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
04-19-2018 11:25 AM - edited 06-05-2022 05:00 PM
- Benefits
- Documentation
- Prerequisite
- Image Download Links
- Limitations
- Supported Platforms
- License Requirements
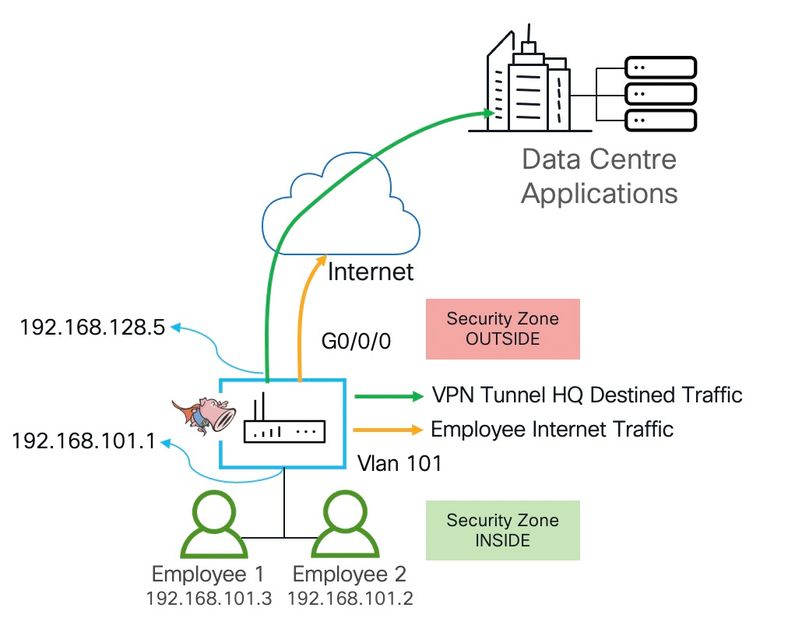
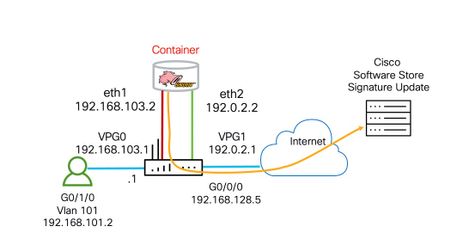
- Topology
- Step-By-Step Configuration
- Configure Virtual Service using IOx
- Configure Port Groups
- Activate the virtual service and configure guest IPs
- Configuring UTD (Service Plane)
- Configuring UTD (Data Plane)
- Whitelisting (optional)
- Verification:
- Check virtual service
- Check UTD (service plane)
- Engine Status
- Check UTD(data plane)
- How to test Snort IPS firing signature:
- Using 'curl' on a linux host
- Troubleshooting
Benefits
- Helps meet PCI compliance.
- Threat protection built into ISR and ISRv branch routers and CSR
- Complements ISR Integrated Security
- Lightweight IPS solution with low TCO (Total Cost of Ownership) and automated signature updates
- Supports VRF (16.6)
Documentation
This configuration example is meant to be interpreted with the aid of the official documentation from the configuration guide located here:
Prerequisite
If it is a physical ISR it must be running IOS-XE version 3.16.1 or above. If it is a CSR it must be running 16.3.1 or above and if it is an ISRv (ENCS) then it must be running 16.8.1 or above. Catalyst 8300 (starting 17.3.2 and above), 8200 (starting 17.4.1 and above), 8000V (starting 17.4.1 and above).
Image Download Links
Catalyst 8500L - https://software.cisco.com/download/home/286324574/type
Catalyst 8300 - https://software.cisco.com/download/home/286324476/type
Catalyst 8200 - https://software.cisco.com/download/home/286324472/type
Catalyst 8000V - https://software.cisco.com/download/home/286327102/type
ISR - https://software.cisco.com/download/home/284389362/type
CSR - https://software.cisco.com/download/home/284364978/type
ISRv - https://software.cisco.com/download/home/286308693/type
Limitations
- Only tcp, udp and icmp packets will be diverted to snort for inspection
- Only through the box traffic will be diverted to snort for inspection
Supported Platforms
ISR 4461, 4451, 4431, 4351, 4331, 4321, 4221X, 4221, CSR, ISRv and ISR 1K (X PIDs such as 1111X, 1121X, 1161X etc that support 8GB DRAM only, starting 17.2.1r release)
Catalyst 8500L, 8300, 8200, 8000V.
License Requirements
Security K9 license is required on the ISR1K, ISR 4K routers, CSRs and ISRv. In addition to that, signature subscription 1yr or 3yr is required.
DNA-Essentials license is required on the Catalyst 8000 Edge routers mentioned in the Supported Platforms section in order to be able to use IPS/Snort.
Please refer the data sheet here: http://www.cisco.com/c/en/us/products/collateral/security/router-security/datasheet-c78-736114.html
Topology
Step-By-Step Configuration
Configure Virtual Service using IOx
Copy the UTD Snort IPS engine software to the routers flash. The file name should be similar to this
secapp-utd.17.07.01a.1.0.3_SV2.9.16.1_XE17.7.x86_64.tar. Once done, install the virtual service using the IOx commands.
app-hosting install appid UTD package bootflash:secapp-utd.17.07.01a.1.0.3_SV2.9.16.1_XE17.7.x86_64.tar
Configure Port Groups
Configure two port groups. VPG0 for management traffic. This VPG (Virtual Port Group) will be used to source logs to the log collector as well as pulling signature updates from Cisco.com.
The second port group is for data. This VPG1 will be used to send and receive packets that are marked for inspection that arrive on the data plane for IPS inspection.
Make sure to provide proper NAT and routing for VPG0 to be able to reach the log server as well as cisco.com to grab the signature update files.
interface VirtualPortGroup0 description Management interface ip address 192.168.103.1 255.255.255.252 Interface VirtualPortGroup1 description Data interface ip address 192.0.2.1 255.255.255.252
Activate the virtual service and configure guest IPs
Next step is to configure matching guest IPs on the same subnet for the container side. Make sure to "start" the service.
app-hosting appid UTD
app-vnic gateway0 virtualportgroup 0 guest-interface 0
guest-ipaddress 192.168.103.2 netmask 255.255.255.252
app-vnic gateway1 virtualportgroup 1 guest-interface 1
guest-ipaddress 192.0.2.2 netmask 255.255.255.252
app-resource package-profile low (medium, high) ===> this option is not available on ISR1K Routers
start
Configuring UTD (Service Plane)
This following section is to configure whether you want snort in IPS or IDS mode, where do you want to send the snort events sent to, what policy and profile to configure for snort etc.
utd engine standard logging host 10.12.5.55 logging syslog threat-inspection threat protection (protection-ips, detection-ids) policy security (balanced, connectivity) signature update server cisco username user1 password ##### signature update occur-at daily 0 0 logging level warning whitelist (optional)
Configuring UTD (Data Plane)
This section is to configure the data plane settings. Whether we need snort enabled on all the interfaces or on selected interfaces. Whether we need "fail-close" meaning when snort engine goes down for what ever reason, no traffic will be allowed to leave.
utd all-interfaces engine standard fail close =====> fail open is default Or optionally enable snort under selected interfaces interface vlan 101 utd enable interface G0/0/0 utd enable
Whitelisting (optional)
If you see any false positives, there is an option to whitelist signatures.
utd threat-inspection whitelist signature id 21599 comment Index signature id 20148 comment ActiveX
Verification:
Check virtual service
Make sure the virtual service is installed and activated.
kusankar-1121X#show app-hosting list
App id State
---------------------------------------------------------
UTD RUNNING
kusankar-1121X#show app-hosting detail App id : UTD Owner : ioxm State : RUNNING Application Type : LXC Name : UTD-Snort-Feature Version : 1.0.3_SV2.9.16.1_XE17.7 Description : Unified Threat Defense Author : Path : /bootflash/secapp-utd.17.07.01a.1.0.3_SV2.9.16.1_XE17.7.aarch64.tar URL Path : Activated profile name : Resource reservation Memory : 1024 MB Disk : 711 MB CPU : CPU-percent : 33 % VCPU : 0 Platform resource profiles Profile Name CPU(unit) Memory(MB) Disk(MB) -------------------------------------------------------------- Attached devices Type Name Alias --------------------------------------------- Disk /tmp/xml/UtdLogMappings-IOX Disk /tmp/xml/UtdIpsAlert-IOX Disk /tmp/xml/UtdDaqWcapi-IOX Disk /tmp/xml/UtdUrlf-IOX Disk /tmp/xml/UtdTls-IOX Disk /tmp/xml/UtdDaq-IOX Disk /tmp/xml/UtdAmp-IOX Watchdog watchdog-504.0 Disk /opt/var/core Disk /tmp/HTX-IOX Disk /opt/var NIC ieobc_1 ieobc Disk _rootfs NIC dp_1_1 net3 NIC dp_1_0 net2 Serial/Trace serial3 Network interfaces --------------------------------------- eth0: MAC address : 54:e:0:b:c:2 IPv6 address : :: Network name : ---------------------------------------------------------------------- Process Status Uptime # of restarts ---------------------------------------------------------------------- climgr UP 0Y 0W 0D 1:24:50 2 logger UP 0Y 0W 0D 1:19:25 0 snort_1 UP 0Y 0W 0D 1:19:25 0 Network stats: eth0: RX packets:27151, TX packets:27060 eth1: RX packets:4774, TX packets:4564 DNS server: domain kusankar.cisco.com nameserver 208.67.222.222 nameserver 208.67.220.220 nameserver 4.2.2.2 nameserver 192.168.128.1 Coredump file(s): lost+found Interface: eth2 ip address: 192.0.2.2/30 Interface: eth1 ip address: 192.168.103.2/30 Address/Mask Next Hop Intf. ------------------------------------------------------------------------------- 0.0.0.0/0 192.0.2.1 eth2 0.0.0.0/0 192.168.103.1 eth1
Check UTD (service plane)
kusankar-1121X#show utd engine standard config
UTD Engine Standard Configuration:
VirtualPortGroup Id: 1
IPS/IDS : Enabled
Operation Mode : Intrusion Prevention
Policy : Security
Signature Update:
Server : cisco
User Name : ******
Password : [b_TJUZiEbigI_RNM]VIdNAVLgcAQVUEI
Occurs-at : daily ; Hour: 0; Minute: 0
Logging:
Server : IOS Syslog;
Level : debug
Statistics : Disabled
Hostname : kusankar-1121x
Whitelist : Disabled
Port Scan : Disabled
Web-Filter : Disabled
Engine Status
kusankar-1121X#show utd engine standard status
Engine version : 1.0.3_SV2.9.16.1_XE17.7
Profile : Default
System memory :
Usage : 31.70 %
Status : Green
Number of engines : 1
Engine Running Health Reason
=======================================================
Engine(#1): Yes Green None
=======================================================
Overall system status: Green
Signature update status:
=========================
Current signature package version: 29161.245.s
Last update status: Successful
Last successful update time: Sat Jun 4 19:07:10 2022 EST
Last failed update time: None
Last failed update reason: None
Next update scheduled at: Sunday Jun 05 00:00 2022 EST
Current status: Idle
Check UTD(data plane)
Make sure the counts increment for encap, decap, redirect, reinject and the health shows "Green".
kusankar-1121X#show platform hardware qfp active feature utd stats
Summary Statistics:
Policy
Active Connections 32
TCP Connections Created 5964
UDP Connections Created 4521
ICMP Connections Created 2110
Channel Summary
Active Connections 32
decaps 95328
encaps 95668
Expired Connections 12563
Packet stats - Policy
Pkts entered policy feature pkt 452887
byt 240683116
Pkts slow path pkt 12595
byt 862149
Packet stats - Channel Summary
Bypass pkt 26454
byt 7451485
Divert pkt 95668
byt 34022809
Reinject pkt 94970
byt 33986080
Would Drop Statistics (fail-open):
Policy
Stats were all zero
Channel Summary
Stats were all zero
General Statistics:
Non Diverted Pkts to/from divert interface 4547
Inspection skipped - UTD policy not applicable 332209
Policy already inspected 241268
Pkts Skipped - New pkt from RP 2021
Response Packet Seen 9521
Feature memory allocations 12595
Feature memory free 12563
Feature Object Delete 12563
Skipped - First-in-flow RST packets of a TCP flow 1789
Diversion Statistics Summary:
SN offloaded flow 6426
Flows Bypassed as SN Unhealthy 26454
Service Node Statistics:
SN health green 2
SN health red 1
SN Health: Channel: Threat Defense : Green
AppNAV registration 1
SN Health: Channel: Service : Down
Stats were all zero
TLS Decryption policy not enabled
How to test Snort IPS firing signature:
Using 'curl' on a linux host
Make sure you have subscription signature set enabled, in IPS mode with the security policy to do the following test.
"show utd engine standard config" should show you what policy is configured and whether IPS is enabled.
"show utd engine standard signature update status" will show you what signature package is currently on the router.
From a linux client or a mac laptop that sits behind the router, you can send
“curl -A "SAH Agent" http://url.com”
[or]
“curl -v -L -m 10 dfgvx.com”
for snort to trigger a signature and print a message as shown below.
Jun 5 04:05:21.435: %VMAN-5-VIRT_INST_NOTICE: R0/0: vman: VIRTUAL SERVICE UTD LOG:
2022/06/04-23:05:20.719516 EST [**] [Hostname: kusankar-1121x] [**] [Instance_ID: 1]
[**] Drop [**] [1:27984:2] APP-DETECT DNS request for Dynamic Internet Technology
domain dfgvx.com [**] [Classification: Misc activity] [Priority: 3] [VRF: 0]
{UDP} 192.168.102.4:64350 -> 4.2.2.2:53
Troubleshooting
https://supportforums.cisco.com/t5/security-documents/snort-ip-on-isr-isrv-and-csr-troubleshooting/ta-p/3369225
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Yes, 4221 does support Snort IPS though it has fixed 4 GB DRAM that is not upgradable. We did some internal magic to get this done. Check the NPI deck.
-Kureli
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@Kureli Sankar I am looking to run Snort on a CSR1000V. We would be terminating Phase 1 DMVPN tunnels on the CSR1000V which would be the hub router. Throughput requirement is pretty low so we would probably be OK with 100M or 250M throughput however does that mean I am locked in to a 1vCPU deployment where the CPU is split across the control plane, service plane, and data plane? Is it possible to use 2vCPU but still stick with 100M or 250M throughput licensing? Also, I assume we would need the 4GB memory upgrade since documentation indicates the CSR platform requires 8GB RAM when running snort.
Thanks...
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi @Kureli Sankar I saw that Snort IPS is now supported on ISR 4461 and ISR 1K (8 Gb dram versions).
Supported Platforms
ISR 4461, 4451, 4431, 4351, 4331, 4321, 4221X, 4221, CSR, ISRv and ISR 1K (X PIDs such as 1111X, 1121X, 1161X etc that support 8GB DRAM only, starting 17.2.1r release)
Does this work with traditional IOS XE router or it must be in in IOS XE SD WAN routers?
If it works with traditional IOS XE router, what would be the Snort subscriber SKU?
I cannot find L-SNT4461-S= or L-SNT11xx-S= SKU
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello i am trying to the same senarios and same config but packets never inspecting.
Policy already inspected 0
i tried with few versions but result same
Do you have an experience related this iissue.?
Thanks
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Any help on this,
The package won't install.
8 22:53:17.141: %VMAN-3-MACH_PARSE_FAILURE: F0: vman: Virtual Service[myips]::Parsing::XML parsing failure::Unable to parse VM machine definition::Extra element devices in interleave
Feb 8 22:53:17.449: VIRTUAL-SERVICE: Install pkg response for tid 30000012: rc=1, descr=VM [myips]: Install failed, unable to parse VM machine def
*Feb 8 22:53:17.449: %IOSXE_VMAN-3-MSGINITFAIL: Failed to initialize required Virt-manager resource: VM [myips]: Install failed, unable to parse VM machine def
%IOSXE_VMAN-3-MSGINITFAIL: Failed to initialize required Virt-manager resource: VM [myips]: Install failed, unable to parse VM machine def
kind regards,
khalid
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Resolved i was on an older IOS version.
- « Previous
-
- 1
- 2
- Next »
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: