If you modify the actions for signature 3050/0 Half-Open SYN Attack, you can enable SYN cookies.
Signature 3050
This signature fires when the number of embryonic connections to a specific port on a specific host has exceeded the syn-flood-max-embryonic value.
Default action for this signature is Produce Alert.
Modify Packet Inline initiates SYN Cookies. The sensor sends a SYN/ACK on behalf of the victim, inserting a cookie value into the packet. If the cookie is returned, then the connection is assumed valid and passed to the target host. Otherwise it is dropped.
Deny Connection will drop the packet, and Deny Packet Inline will drop the packet and all SYN packets to that port and host until the flood is over.
Lab
PC----IPS----ASA 5505----Server
- Set signature 3050 to fire on 5 embryonic connections
- The sensor is configured inline w/ an interface-pair
- Add the modify-packet-inline action to signature 3050
- Insert a fake ARP entry in the ASA for the PCs IP
- This was so that the Server's SYN/ACK is flooded out all ports in the 5505's inside VLAN
- When the PC receives the flooded packet, it does not match the PCs MAC and so the PC does not respond w/ an RST
- Send 7 packets to Server:<open port>, with incrementing source ports and received 1 SYN/ACK generated by the IPS
The IPS triggers 3050 when one additional packet is seen, after reaching the embryonic limit, but only initiates SYN cookies when two additional packets are seen.
ASA config:
arp inside 10.1.1.3 0013.21c9.98c3
PC:
IP: 10.1.1.3
MAC: 0013.21c9.98c2
Default gateway: 10.1.1.1
ASA:
IP: 10.1.1.1
MAC: 0019.0725.929B
Server:
IP: 172.18.124.76
TCP/80 open
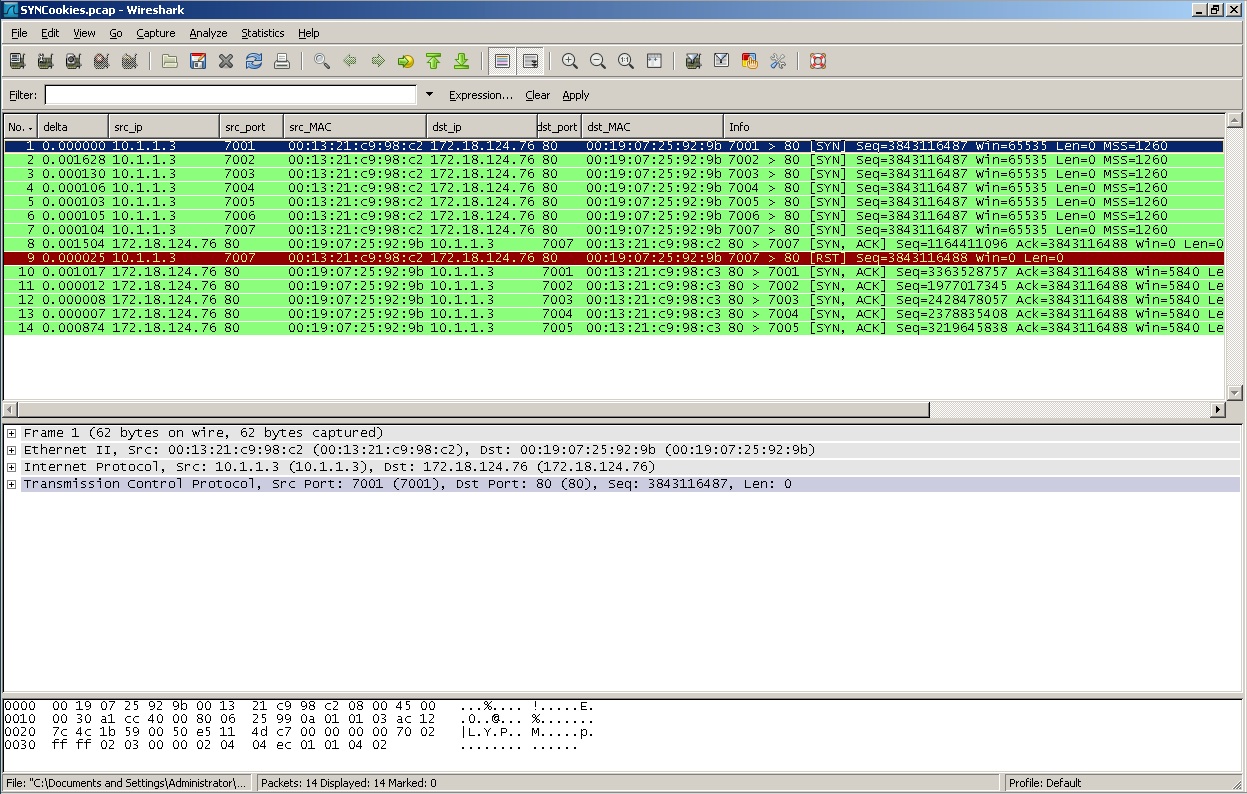
Packet Capture from the host: SYNCookies.pcap
Notes for the capture:
- The IPS silently drops the 6th packet and SYN/ACK's for the 7th
- The first SYN/ACK you see is destined to 0013.21c9.98c2 (the PCs real address). This was generated by the sensor.
- The RST you see is generated by the PC because the destination MAC of the first SYN/ACK matches the host's MAC.
- The 5 additional SYN/ACKs you see are from the Server and destined to the fake MAC configured on the ASA.