- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- Cisco ISE with Microsoft Cloud PKI
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
09-25-2024 06:03 PM - edited 09-25-2024 06:21 PM
- Introduction
- What is Microsoft Cloud PKI?
- Cloud PKI and Cisco ISE
- High Level Flow Example
- Solution Validation Setup
- Entra ID Groups
- License Assignment
- Confirm Group License Assignment in Intune
- Create the Cloud PKI Instance
- Download the Root and Issuing CA Certificates
- Create Certificate Profiles
- Create Trusted Certificate Profile - Cloud PKI Root
- Create Trusted Certificate Profile - Cloud PKI Issuing
- Create Trusted Certificate Profile - ADCS
- Create SCEP Profile – User Certificate
- Create SCEP Profile – Device
- Create a Wi-Fi Profile
- ISE Configuration
- Import the Cloud PKI Trust Chain to ISE
- Configure the CRL Distribution Point
- ISE Policy Configuration
- Certificate Authentication Profile
- Authentication Policy
- Authorization Policy
- ISE Live Logs
- Client Certificate Attributes
- Device (Computer) Certificate examples
- Client Supplicant Attributes
Introduction
What is Microsoft Cloud PKI?
Cloud PKI and Cisco ISE
- The client must have the certificate trust chain (Root and all Intermediate certificates) that signed the ISE EAP certificate in their User and/or Computer trust store (depending on the use case)
- ISE must have the certificate trust chain (Root and all Intermediate certificates) that signed the User/Device EAP certificate in its Trusted Certificates store
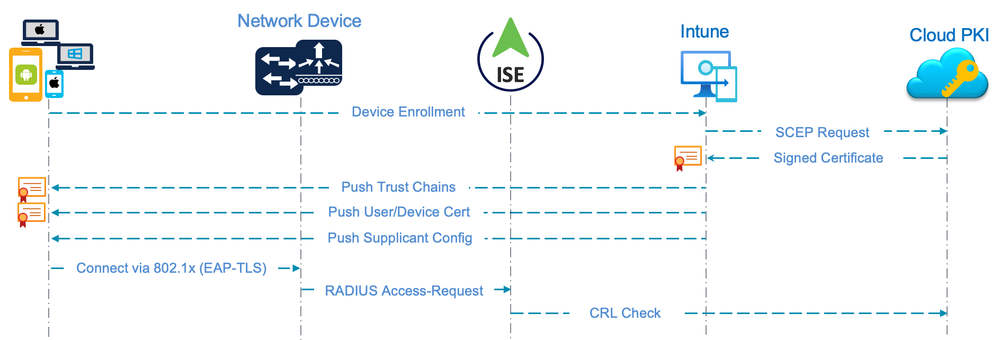
High Level Flow Example
- Installing trust chains for both the client (user/device certificates from Cloud PKI) and the ISE EAP (signed by a separate CA) certificates to the relevant user/device trust store locations.
- Enrolling the user/device certificates signed by Cloud PKI and installing them in the relevant user/device trust store locations.
- Configuring the endpoint supplicant (Wired, Wireless) as needed for 802.1x, including the necessary Trusted CA and certificate matching settings.
It is important to note that 802.1x connectivity relies on the proper certificates and supplicant configuration, so those steps must be done prior to connecting to an 802.1x secured network. As both Intune and Cloud PKI are cloud-based solutions, these processes can take place from any internet connection.
Solution Validation Setup
The following sections provide details on the lab setup that was used as an example to validate the solution. The setup was based on the following scenario.
- Entra Joined (not Hybrid Joined) Windows VM enrolled with Intune
- Windows 11 Pro Version 23H2
- Cisco ISE 3.3 patch 3
- Wireless 802.1x using EAP-TLS with User or Computer Authentication
While this example uses EAP-TLS, other certificate-based authentication methods could also be used in conjunction with Cloud PKI. See the following article for currently supported use cases involving Cisco ISE, Entra ID, and Intune.
Cisco ISE with Microsoft Active Directory, Entra ID, and Intune
Entra ID Groups
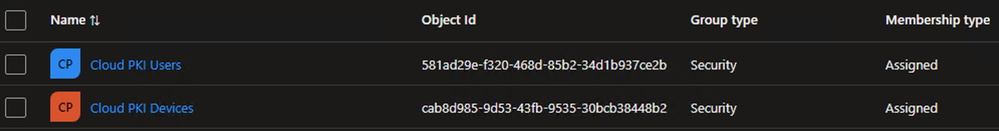
I started by creating two new Security Groups in Entra ID that were used to limit the scope of the solution validation to specific Users and Devices. My test User account and Device were added to the respective Group.
Example
License Assignment
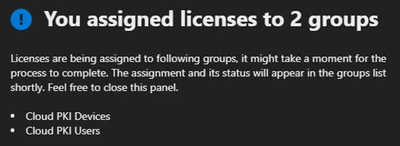
The Cloud PKI license was assigned to the above Groups by logging into Microsoft 365 (https://admin.microsoft.com) and following these steps.
- Navigate to Billing > Licenses
- Select the Microsoft Cloud PKI subscription
- Select the Groups tab and click Assign Licenses
- Select the Groups created in the prior step
The resulting license assignments are shown.
Example
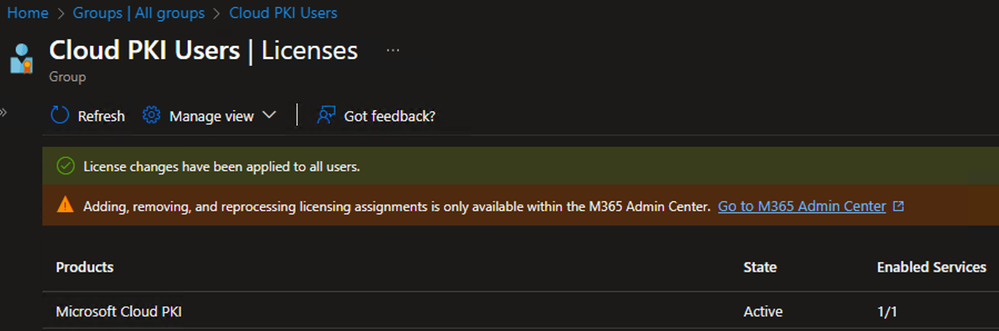
Confirm Group License Assignment in Intune
To confirm that Intune shows the license assignments, follow these steps:
- Open the Intune admin center (https://intune.microsoft.com)
- Navigate to Groups > All Groups and select the groups defined in the prior steps (e.g. Cloud PKI Users)
- Navigate to Manage > Licenses
Create the Cloud PKI Instance
Use the following steps to create the Cloud PKI instance.
- In the Intune admin center, navigate to Tenant administration > Cloud PKI
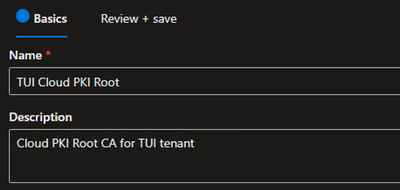
- On the Basics tab, provide the Name and (optional) Description and click Next
-
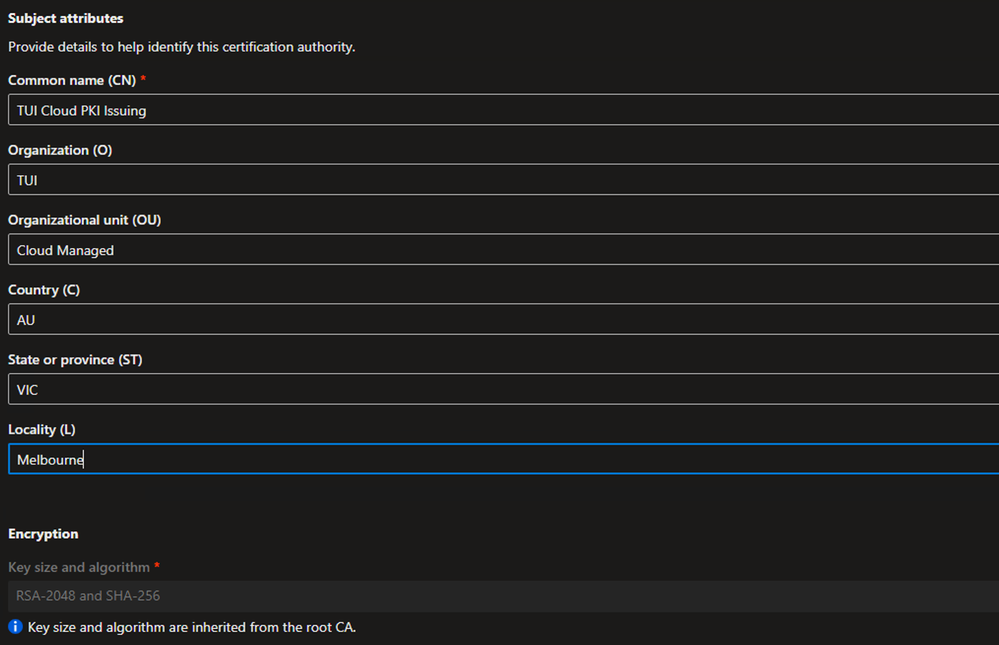
On the Configuration Settings, define the settings appropriate for your environment and click Next
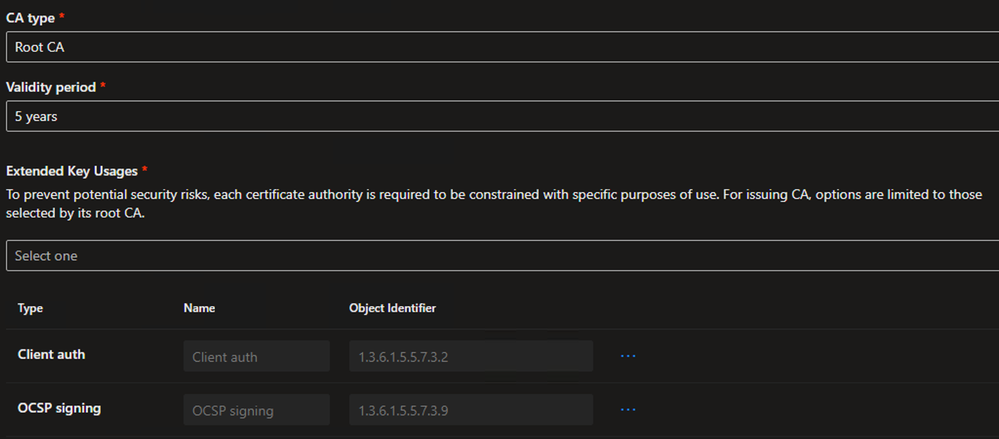
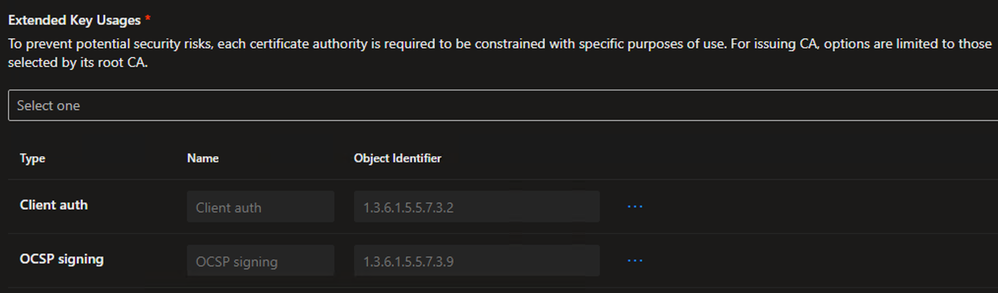
- As this CA will mainly be used for testing 802.1x, only the Client auth and OCSP signing EKUs were added
Example
- As this CA will mainly be used for testing 802.1x, only the Client auth and OCSP signing EKUs were added
- On the Scope tags tab, define any necessary tags for your environment (optional)
- On the Review + create tab, verify the settings are correct and click Create
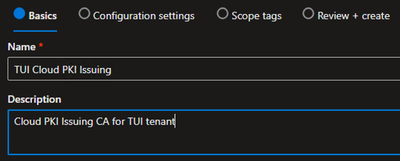
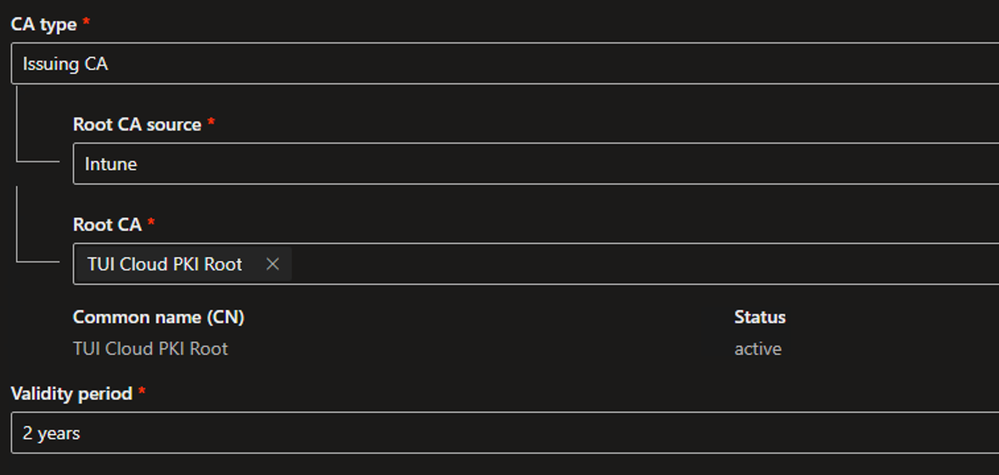
- Repeat the above steps for the Issuing CA
Examples
The resulting CAs will be shown.
Example

Download the Root and Issuing CA Certificates
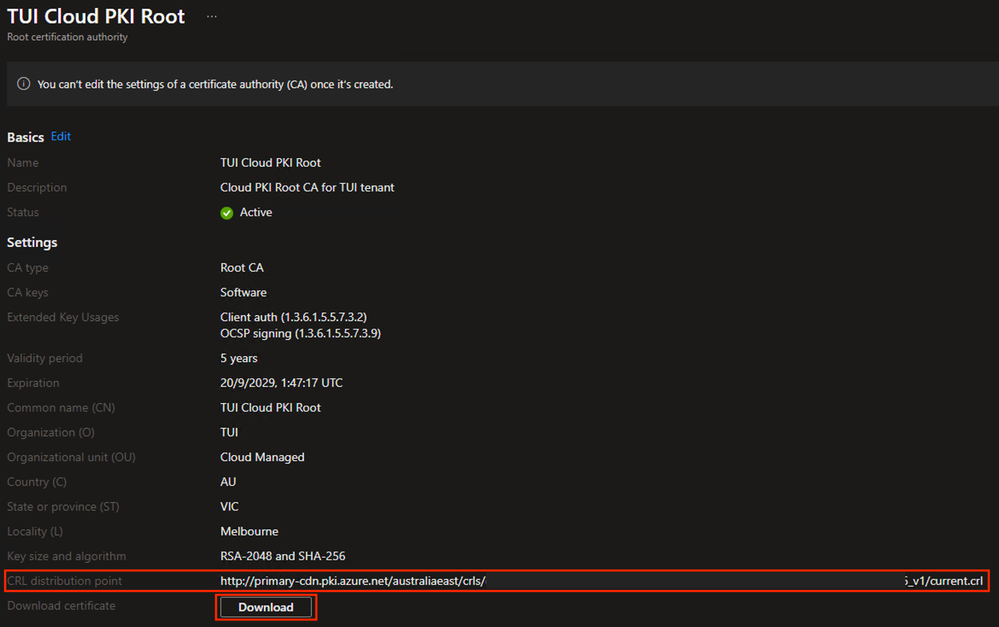
In the Tenant administration > Cloud PKI blade, select the Root CA that was created.
- Copy the URL for the CRL distribution point and save it locally
- Next to the Download certificate field, click the Download button
- Save the certificate to a secure location
Example
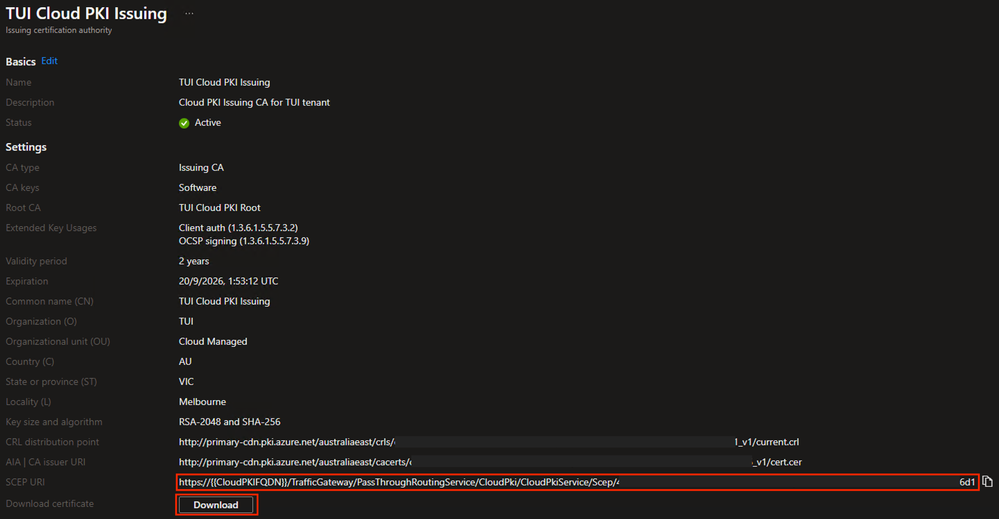
- Repeat the above steps to copy the SCEP URI and save it locally
- Download the Issuing CA certificate and save it to a secure location
Example
Create Certificate Profiles
The following Certificate Profiles will be configured for this example lab:
- Trusted certificate - Cloud PKI Root
- Trusted certificate - Cloud PKI Issuing
- Trusted certificate - ADCS (CA that signed the ISE EAP certificate)
- SCEP Profile - User
- SCEP Profile - Device
In the Intune admin center, navigate to Devices > Manage Devices > Configuration
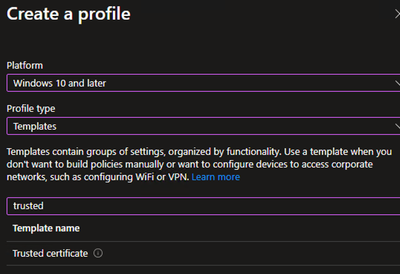
Create Trusted Certificate Profile - Cloud PKI Root
- Click Create > New Policy
- Platform = Windows 10 and later
- Profile type = Templates
- Template name = Trusted certificate
- Click Create
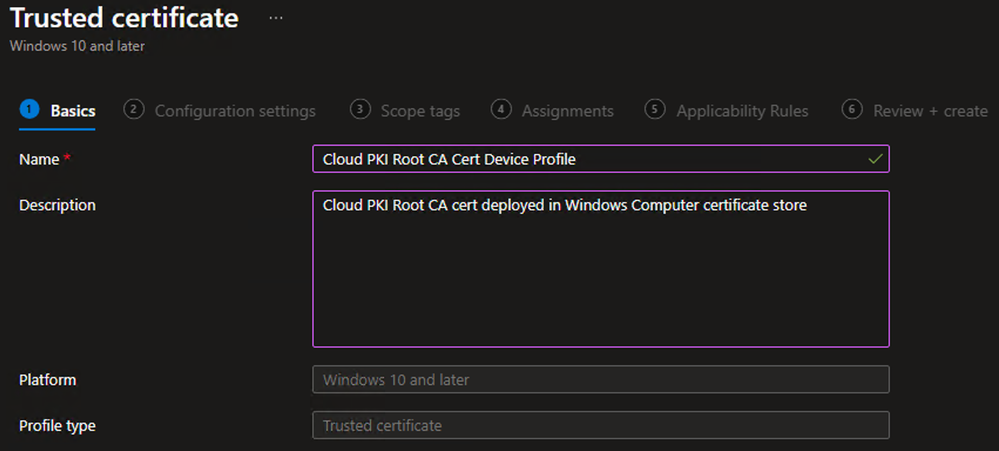
Example - On the Basics tab, define the Name and (optional) Description and click Next
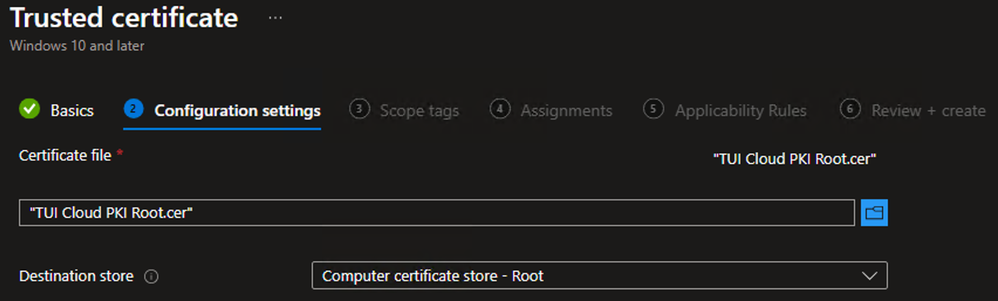
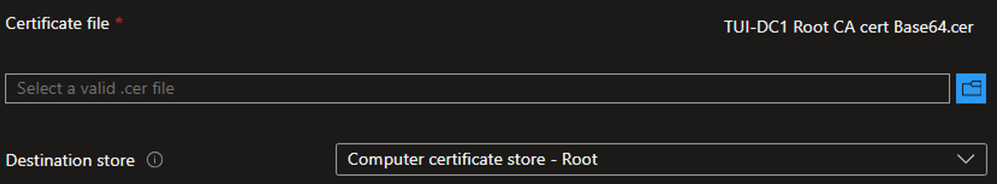
Example - On the Configuration settings tab, browse the Root CA certificate downloaded in the earlier step.
- For the Destination store, select Computer certificate store – Root
- Click Next
Example - On the Scope tags tab, select any tags necessary for your environment (optional)
- Click Next
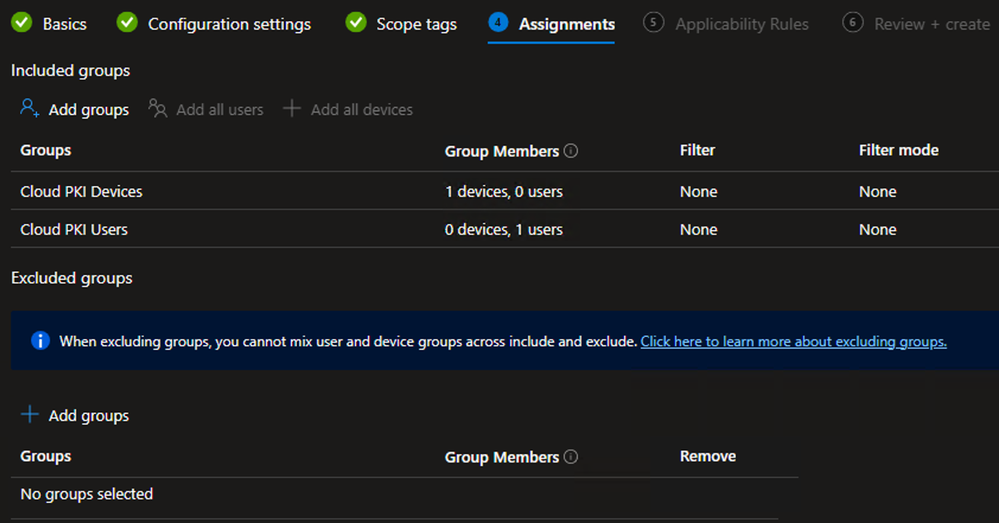
- On the Assignments tab, Select Add Groups
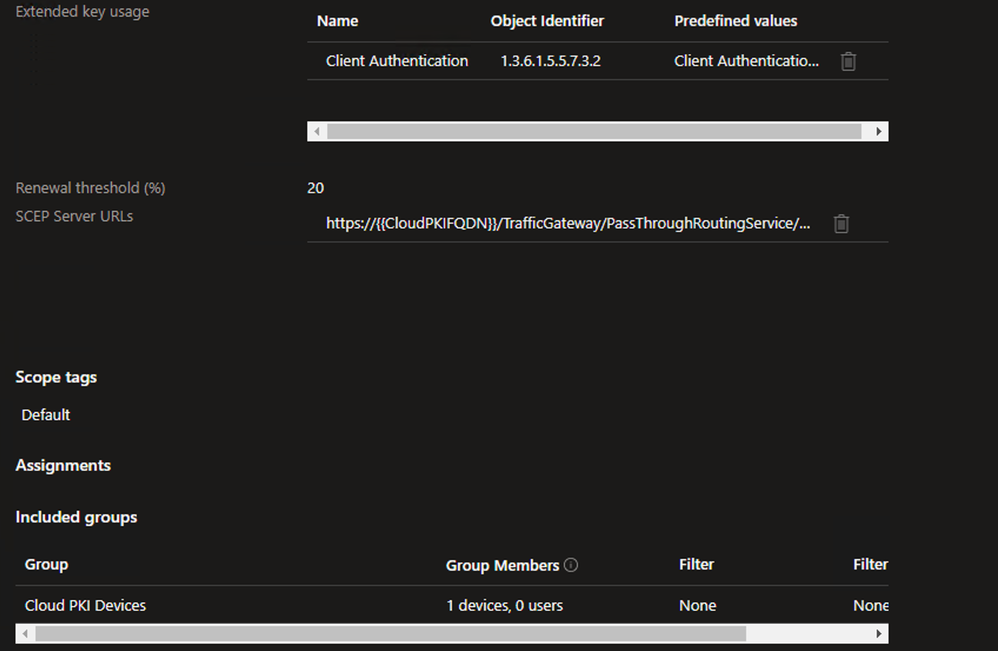
- Under the Included Groups section, select the Cloud PKI Devices group, Cloud PKI Users group, and/or any other Device groups to which the Root CA certificate should be deployed
** NOTE: The same User group that will be used to deploy the SCEP certificate must be included in this Trusted certificate profile.
When creating the SCEP certificate profile in later steps, this Root profile is specified. If the User group is not included here, the SCEP Profile will remain in a Pending state. - (Optional) Under the Excluded Groups section, select any Groups that should be explicitly excluded
- Click Next
Example - On the Applicability Rules tab, add any rule definitions required for your environment (optional)
- Click Next
- On the Review + create tab, verify the settings are correct and click Create
Example
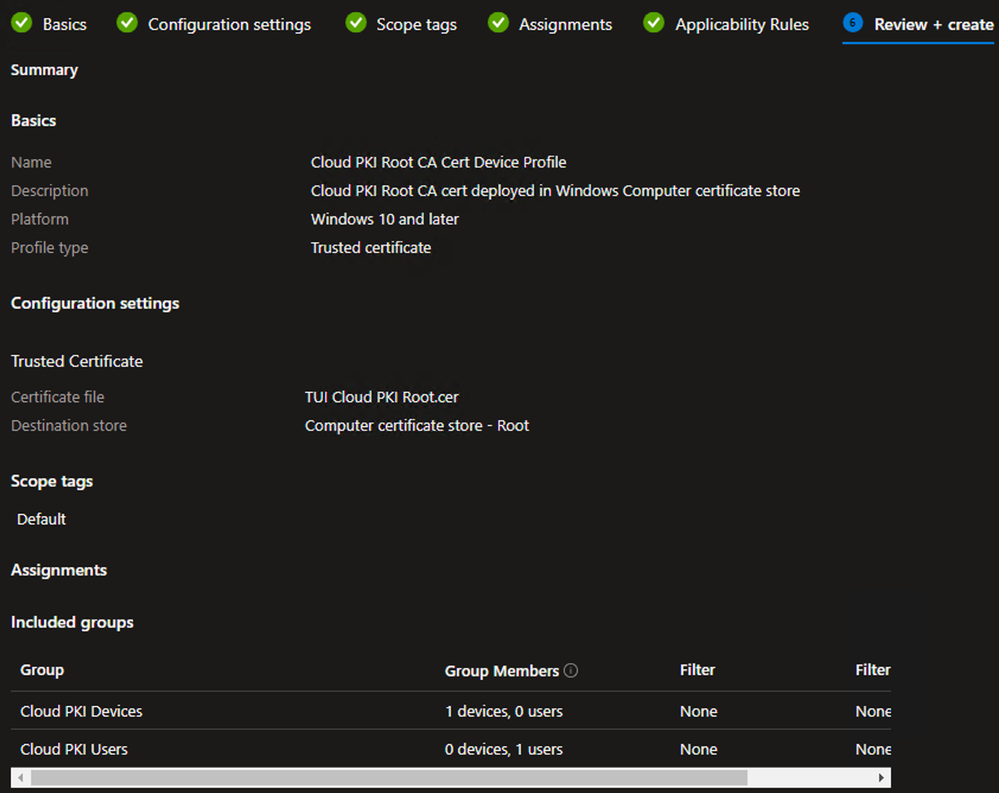
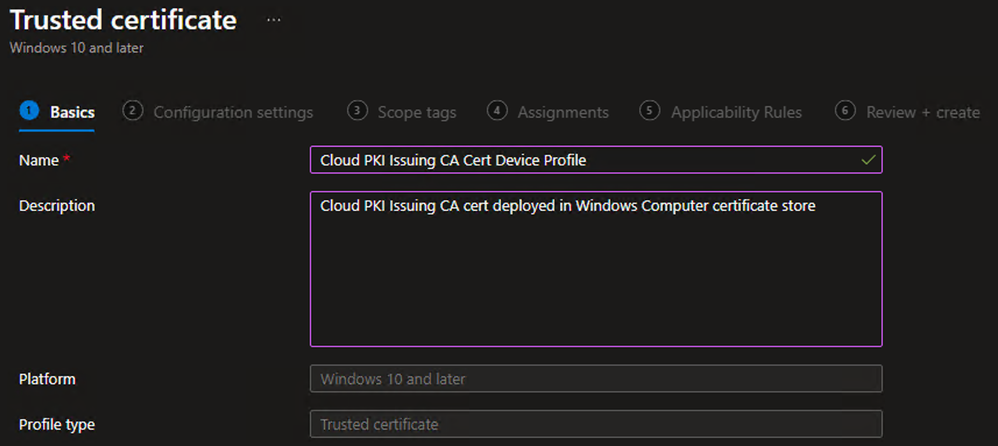
Create Trusted Certificate Profile - Cloud PKI Issuing
- Repeat steps 1 through 5 above to create a new Trusted certificate template
- On the Basics tab, define the Name and (optional) Description and click Next
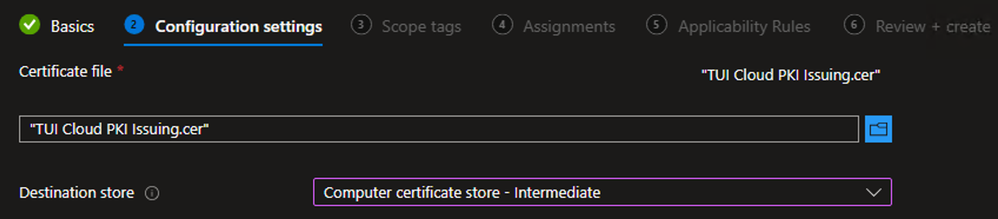
Example - On the Configuration settings tab, browse the Issuing CA certificate downloaded in the earlier step.
- For the Destination store, select Computer certificate store – Intermediate
- Click Next
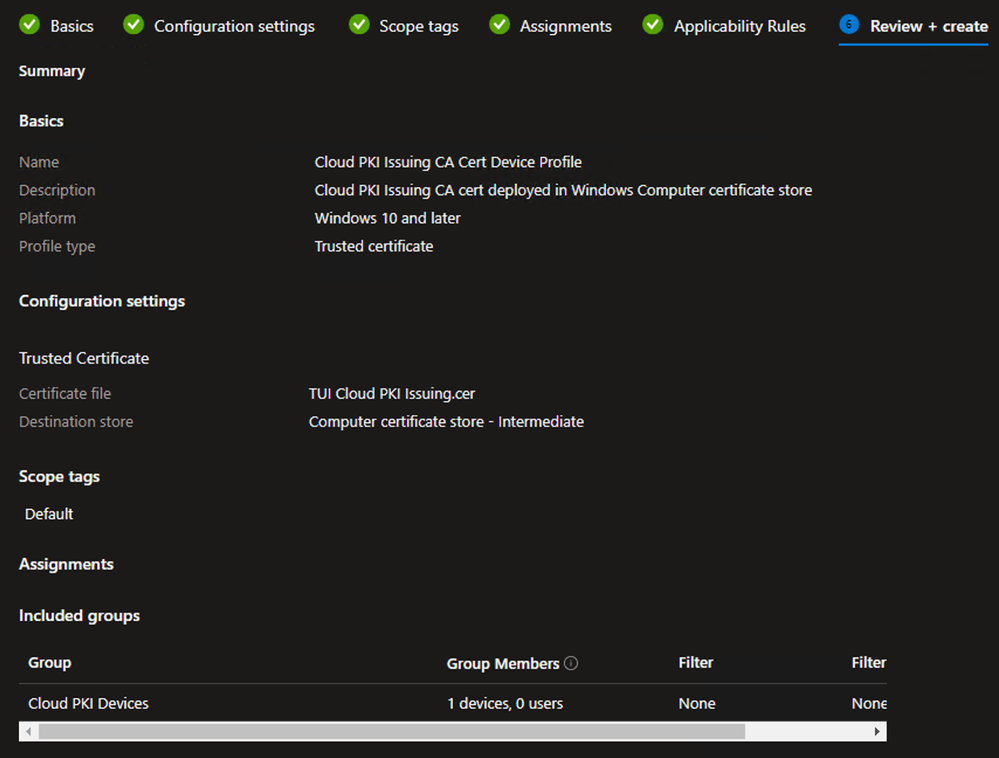
Example - Repeat the steps above to define any necessary Scope tags, Device Group Assignments, and Applicability Rules
- On the Review + create tab, verify the settings are correct and click Create
Example
Create Trusted Certificate Profile - ADCS
- Repeat the steps above to create a Trusted Certificate Profile for Root and Intermediate certificate(s) that signed the ISE EAP certificate
Examples
Create SCEP Profile – User Certificate
- Click Create > New Policy
- Platform = Windows 10 and later
- Profile type = Templates
- Template name = SCEP certificate
- Click Create
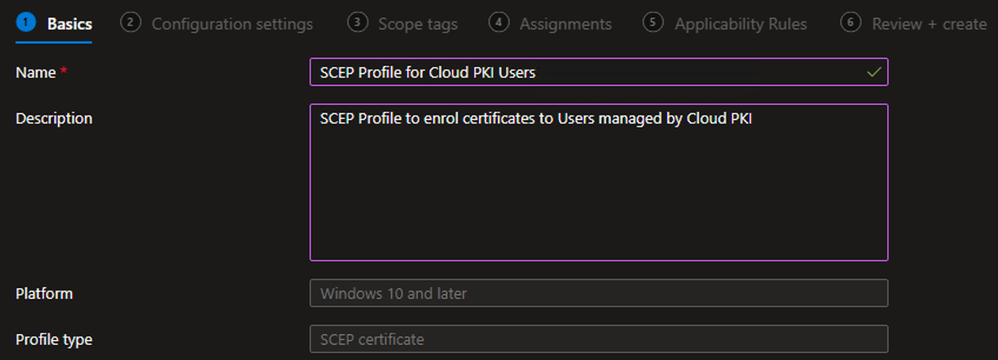
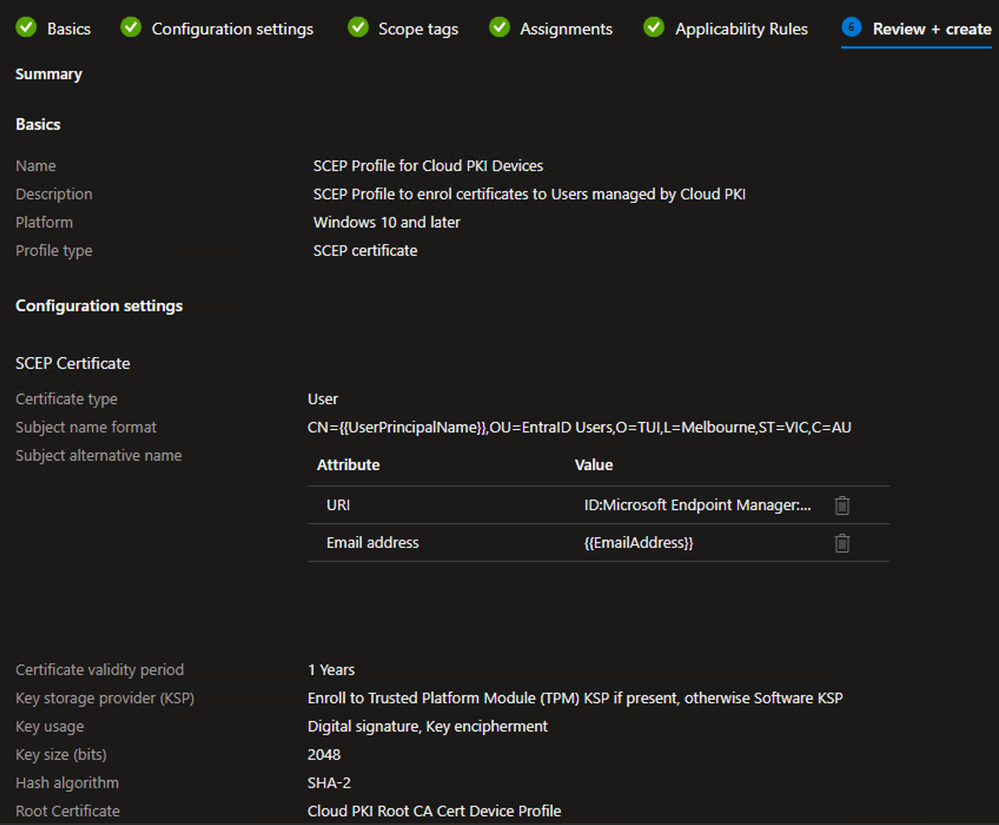
Example - On the Basics tab, define the Name and (optional) Description and click Next
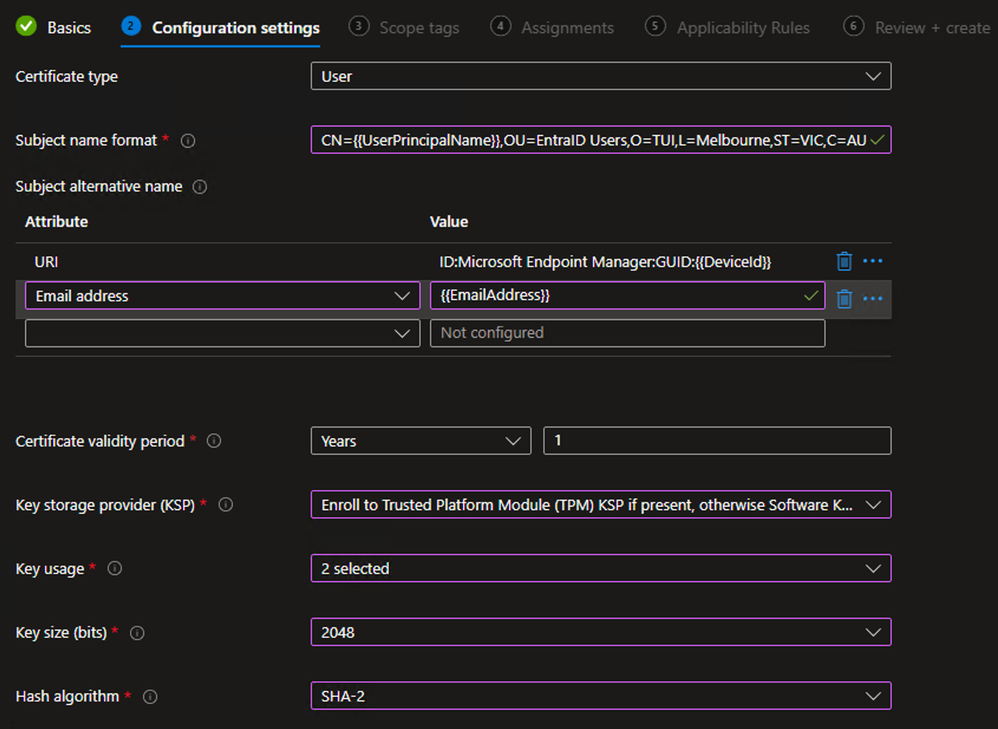
Example - On the Configuration settings tab, select the User Certificate type
- Input the Subject name format as per your requirements. For this example, I have defined the following:
- CN = User Principal Name for the enrolled User (this value must be in the CN or SAN for ISE Authorization against Entra ID using REST ID)
- OU = EntraID Users (defined for use as a matching condition in ISE policies)
- O = TUI
- L = Melbourne
- ST = VIC
- C = AU
- Input the Subject alternative name as per your requirements. For this example I have defined the following:
- URI = ID:Microsoft Endpoint Manager:GUID:{{DeviceId}} (this value is used for ISE integration with Intune MDM for device Registration/Compliance checks)
- Email address = Email address of the enrolled user
- Define the Certificate validity period as per your requirements
- Define the Key Storage Provider (KSP) to be used
- For the Key usage, select both Digital signature and Key encipherment
- Select the desired Key size and Hash algorithm
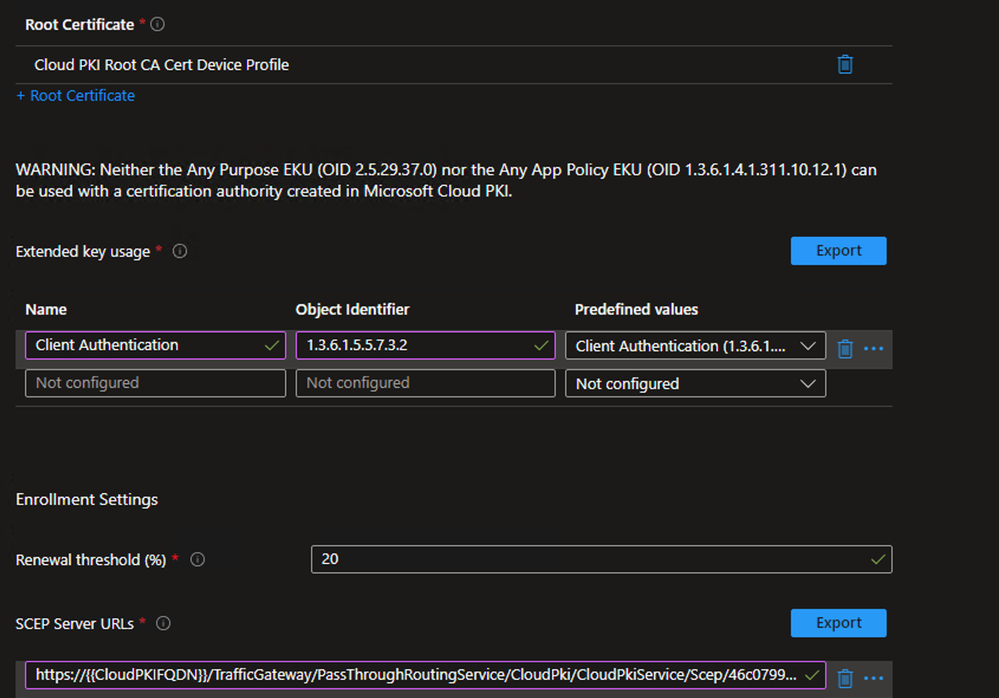
- Click the + Root certificate link and select the Trusted certificate profile created earlier for the Root CA certificate
- For the Extended key usage, use the drop-down for the Predefined values and select the Client authentication as well as any other desired EKUs
- Define the desired Renewal threshold (%)
- In the SCEP Server URLs field, paste in the SCEP URI string that was copied during the Cloud PKI Issuing CA configuration
- Click Next
Example - On the Scope tags tab, select any tags necessary for your environment (optional)
- Click Next
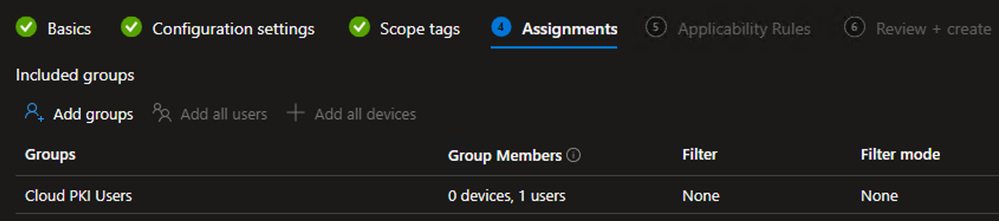
- On the Assignments tab, Select Add Groups
- Under the Included Groups section, select the Cloud PKI Users group and/or any other User groups to which the identity certificate should be deployed
- (Optional) Under the Excluded Groups section, select any Groups that should be explicitly excluded
- Click Next
Example - On the Applicability Rules tab, add any rule definitions required for your environment (optional)
- Click Next
- On the Review + create tab, verify the settings are correct and click Create
Example
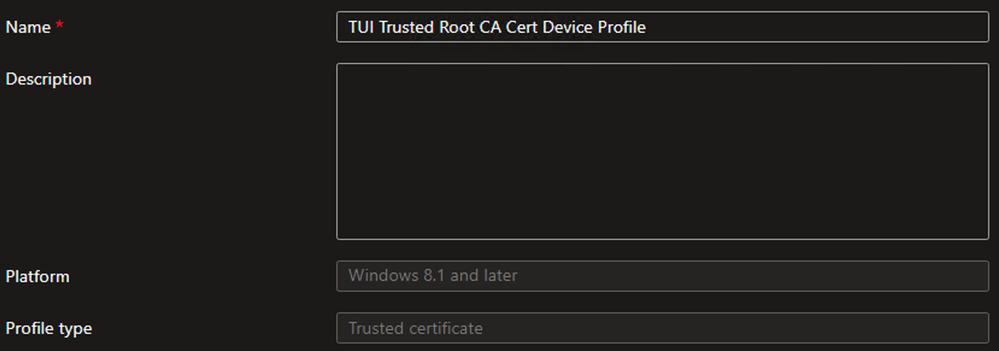
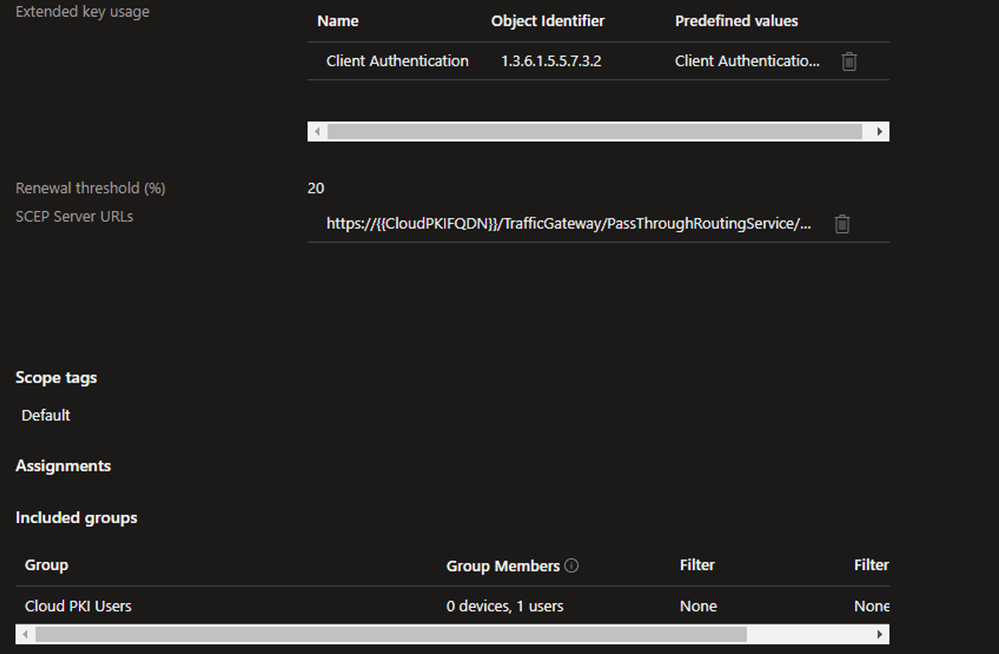
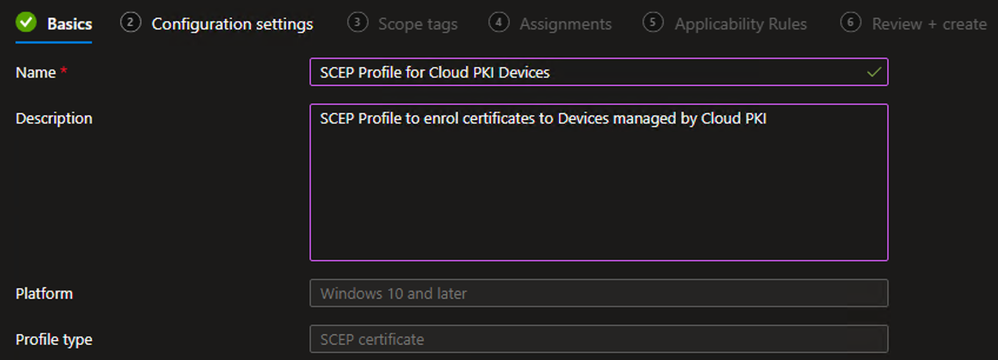
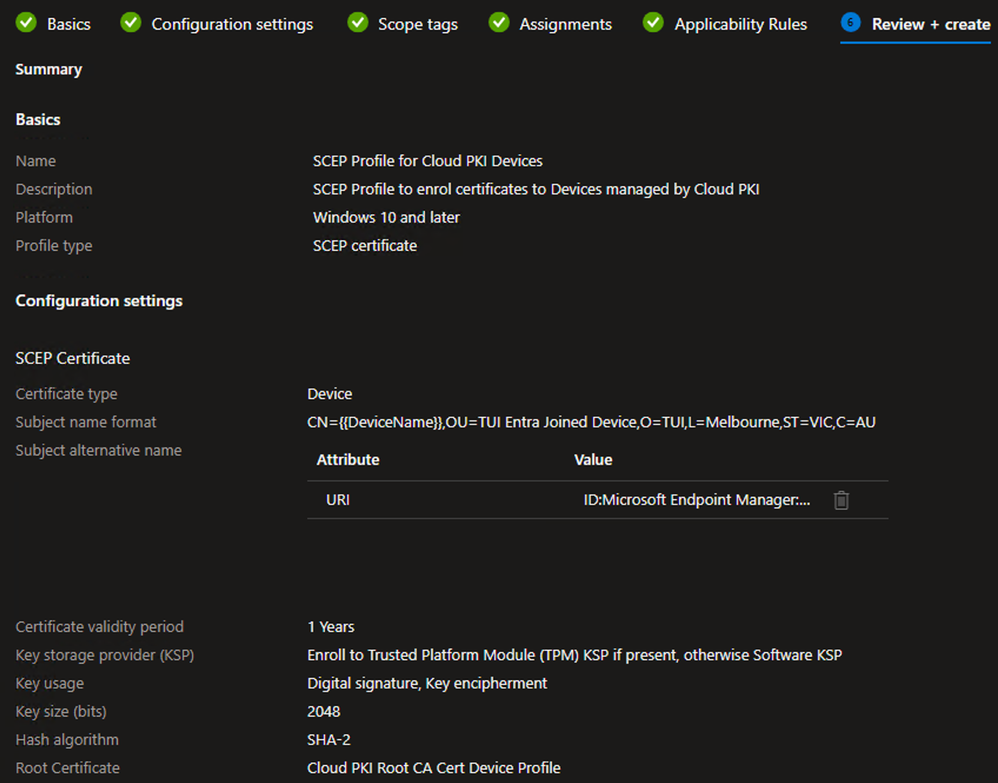
Create SCEP Profile – Device
- Repeat step 1 through 5 above to create a new SCEP certificate template
- On the Basics tab, define the Name and (optional) Description and click Next
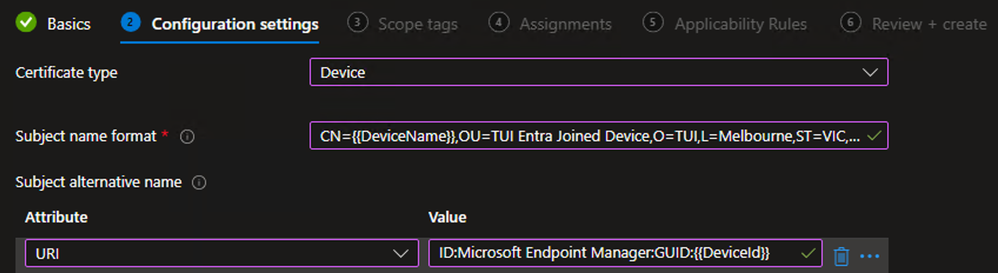
Example - On the Configuration settings tab, select the Device Certificate type
- Input the Subject name format as per your requirements. For this example, I have defined the following:
- CN = Device Name for the enrolled Device
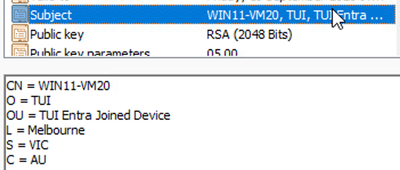
- OU = Entra Joined Device (defined for use as a matching condition in ISE policies)
- O = TUI
- L = Melbourne
- ST = VIC
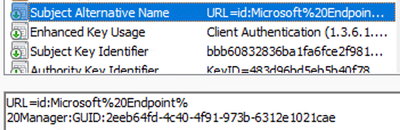
- Input the Subject alternative name as per your requirements. For this example, I have defined the following:
- URI = ID:Microsoft Endpoint Manager:GUID:{{DeviceId}} (this value is used for ISE integration with Intune MDM for device Registration/Compliance checks)
Example
- URI = ID:Microsoft Endpoint Manager:GUID:{{DeviceId}} (this value is used for ISE integration with Intune MDM for device Registration/Compliance checks)
- Repeat the steps above to configure the remaining settings as per your requirements
- Click Next
- Repeat the steps above to define the necessary Scope tags, Device Group Assignments, and Applicability Rules for your environment
- On the Review + create tab, verify the settings are correct and click Create
Example
Create a Wi-Fi Profile
- In the Intune admin center, navigate to Devices > Manage Devices > Configuration
- Click Create > New Policy
- Platform = Windows 10 and later
- Profile type = Templates
- Template name = Wi-Fi
- Click Create
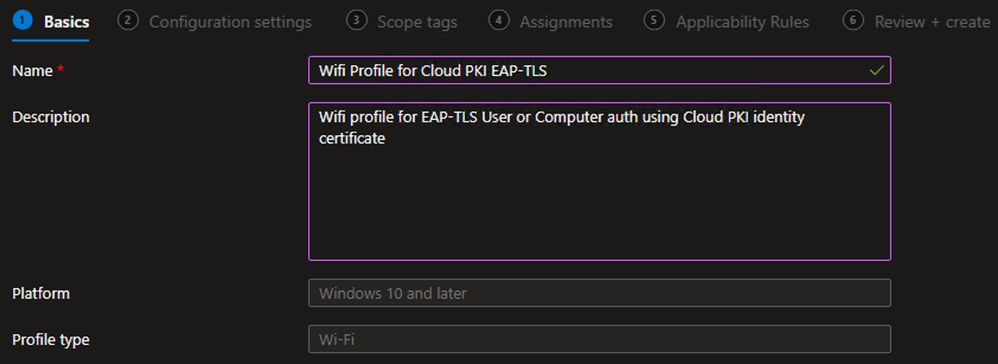
Example - On the Basics tab, define the Name and (optional) Description and click Next
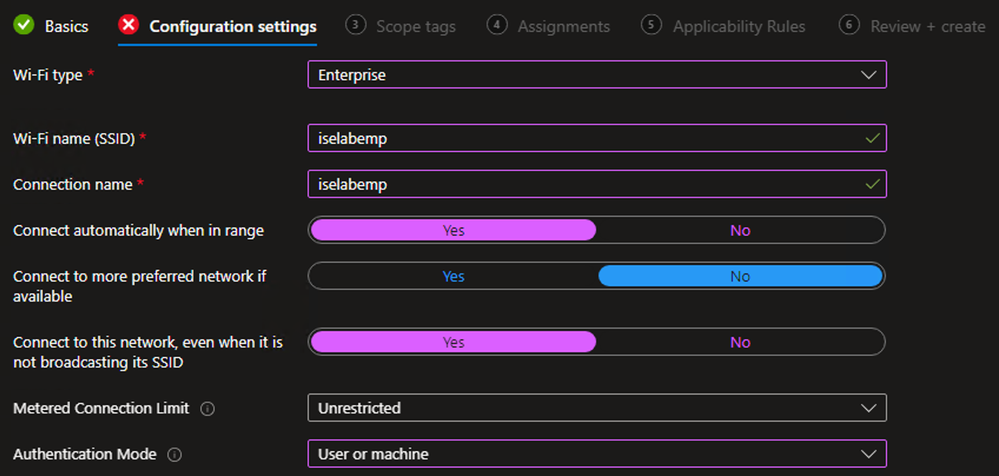
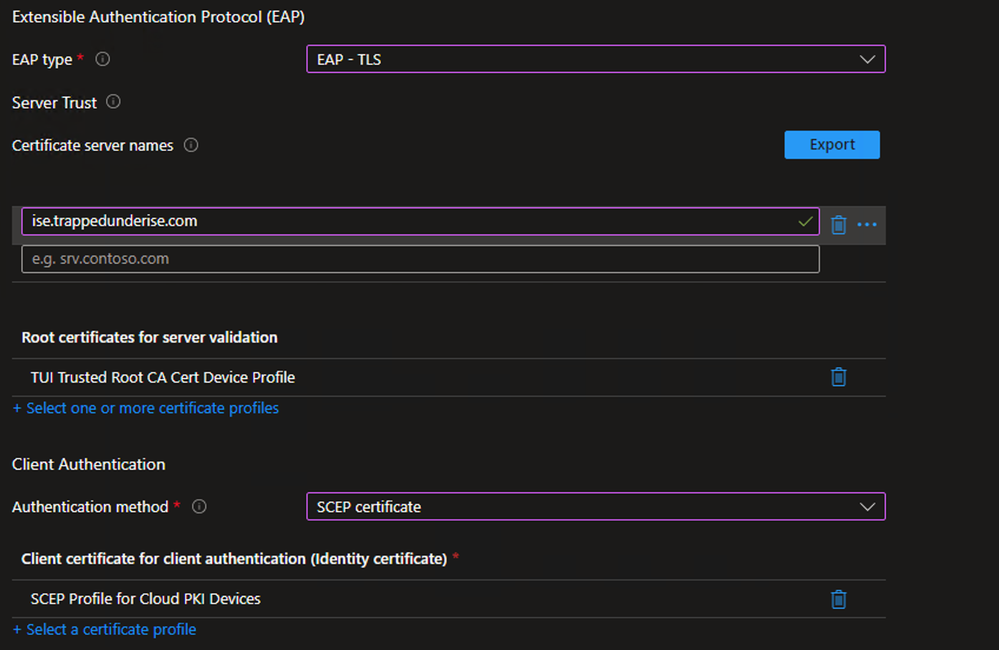
Example - Configure the Wifi Profile settings as per your environment and click Next
Example
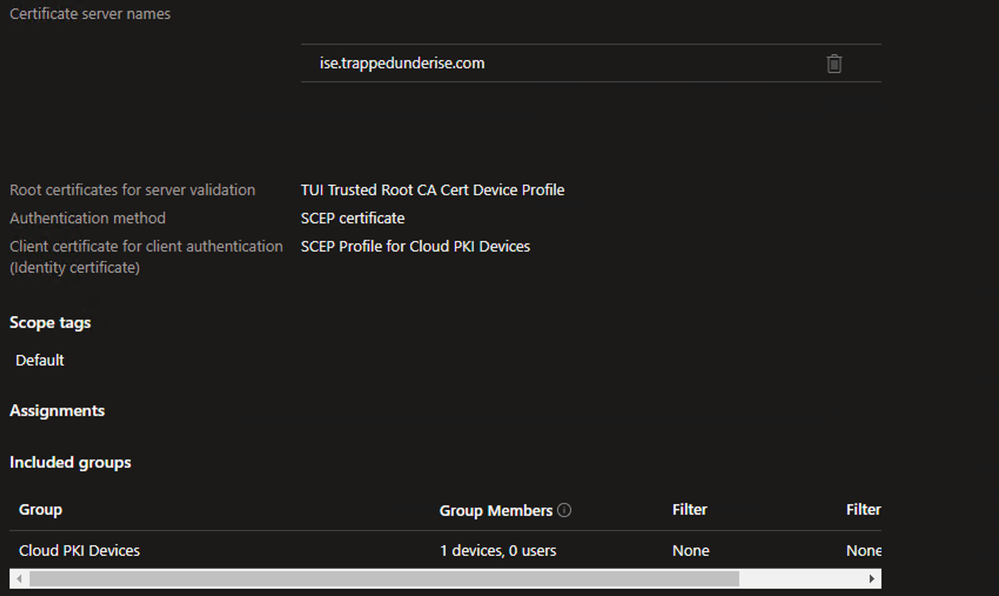
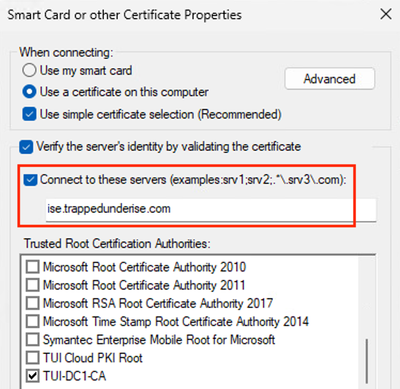
** PLEASE NOTE **
The Certificate server names description is a bit misleading. The values specified here must be the CN value(s) for the EAP certificate presented by ISE.
The Profile selected under the Root certificates for server validation section must be the Root CA that signed the EAP certificate on the ISE PSN. This certificate would be signed by a different CA than the Microsoft Cloud PKI. - On the Scope tags tab, select any tags necessary for your environment (optional)
- Click Next
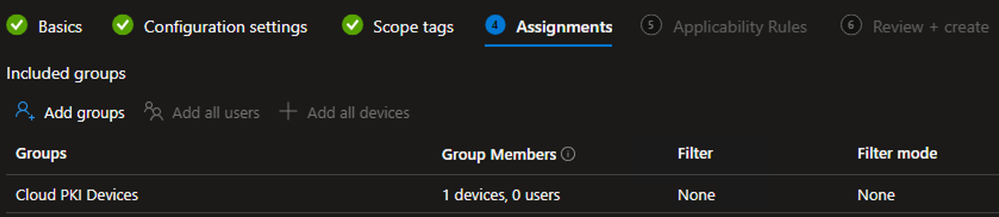
- On the Assignments tab, Select Add Groups
- Under the Included Groups section, select the Cloud PKI Devices group and/or any other Device groups to which the Wifi profile should be deployed
- (Optional) Under the Excluded Groups section, select any Groups that should be explicitly excluded
- Click Next
Example
- On the Applicability Rules tab, add any rule definitions required for your environment (optional)
- Click Next
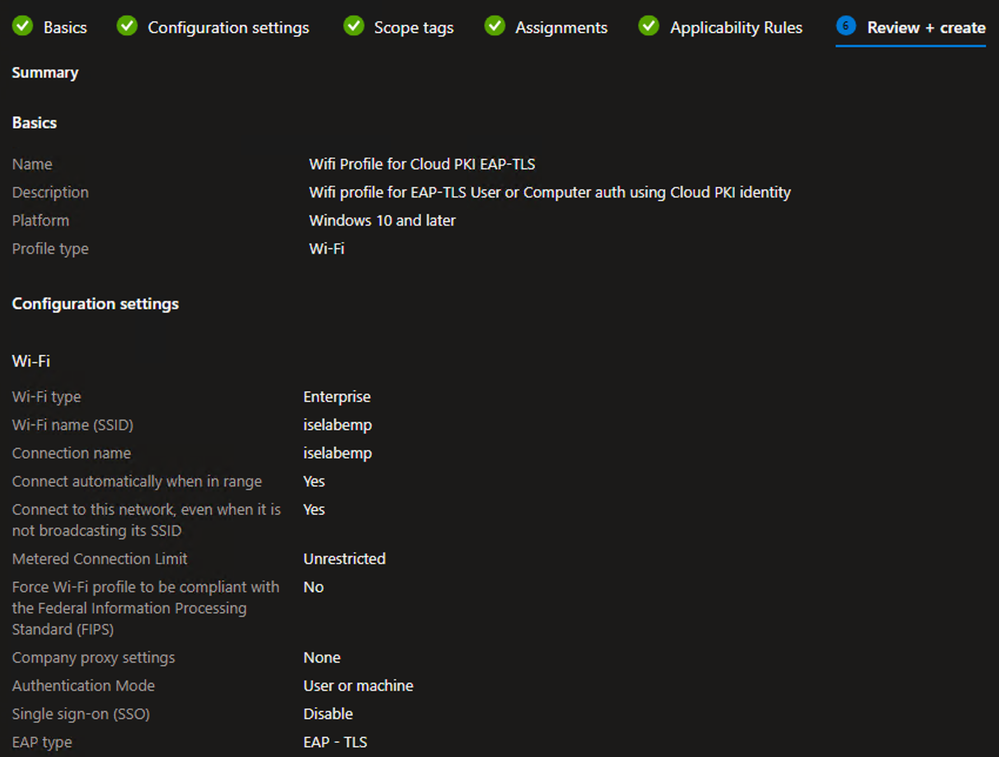
- On the Review + create tab, verify the settings are correct and click Create
Example
ISE Configuration
Now that the configuration is done on the Intune side, the remaining configuration must be completed in ISE.
Import the Cloud PKI Trust Chain to ISE
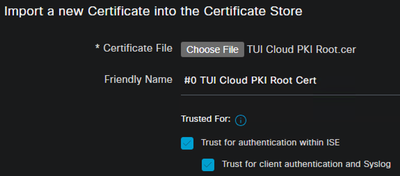
- On the Primary PAN, navigate to Administration > System > Certificate Management > Trusted Certificates
- Click Import
- Click the Choose File button and navigate to the Cloud PKI Root CA certificate downloaded in the early steps
- Define the Friendly Name
- Select the checkbox for the following options:
- Trust for authentication within ISE
- Trust for client authentication and Syslog
- Click Submit
Example - Repeat the steps above for the Cloud PKI Issuing CA certificate downloaded in the early steps
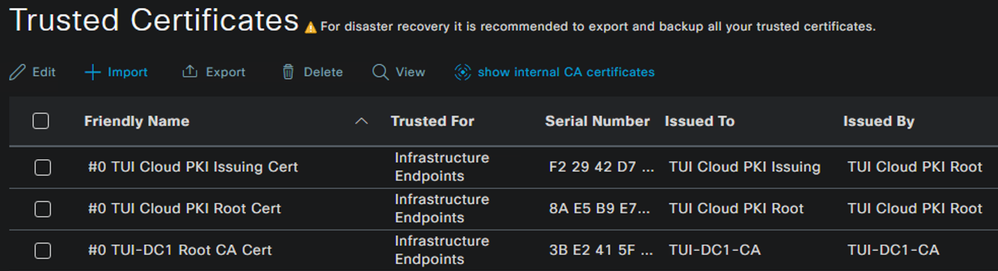
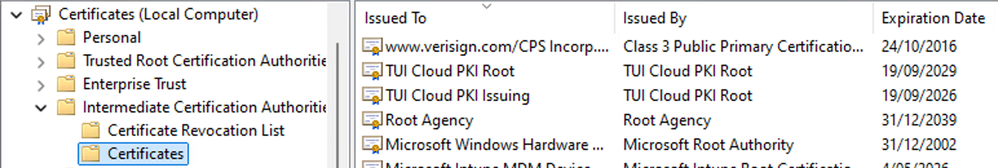
You should now see the certificates for all required trust chains in the Trusted Certificates page.
Example
In this example, the TUI-DC1-CA is the Root CA that signed the ISE EAP Certificate

Configure the CRL Distribution Point
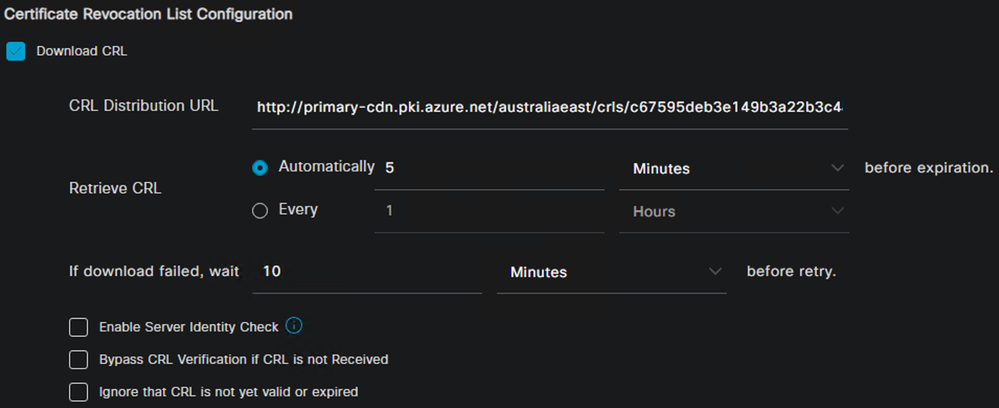
- On the Trusted Certificates page, select the Issuing certificate and click Edit
- Scroll down to the Certificate Status Validation section
- In the Certificate Revocation List Configuration section, select the Download CRL checkbox
- In the CRL Distribution URL field, paste the CRL distribution point URL saved in the early steps
- Configure any additional settings as per your requirements and click Save
Example
ISE Policy Configuration
The use case for validating the Cloud PKI solution is similar to the one defined in the following document:
Configure ISE 3.2 EAP-TLS with Microsoft Azure Active Directory
The relevant ISE policy elements configured for this use case include the following:
- Certificate Authentication Profile
- Authentication Policy
- Authorization Policies
Certificate Authentication Profile
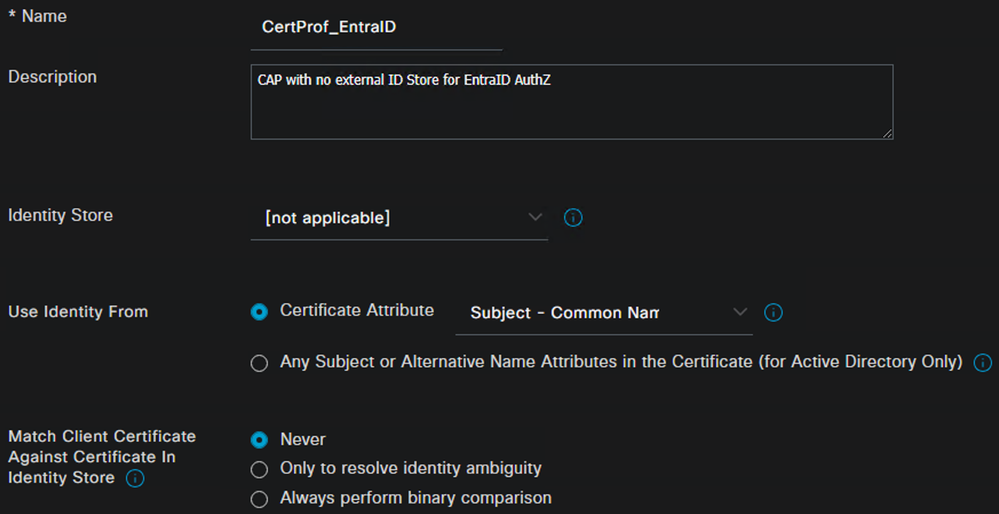
A Certificate Authentication Profile (CAP) is created to define the certificate attribute that ISE will use for identity. In this example, the Subject – Common Name will be used for identity.
As no Authentication can be performed against Entra ID, the Identity Store is set to [not applicable]
Example
Authentication Policy
An Authentication Policy is defined with the following conditions:
- Certificate issuer matching the CN of the Cloud PKI Issuing CA
- Certificate subject OU matching either the ‘TUI Entra Joined Device’ or ‘EntraID Users’ values defined in the Intune SCEP certificate profiles for the Device and User, respectively
- Authentication using the CAP defined above
Example
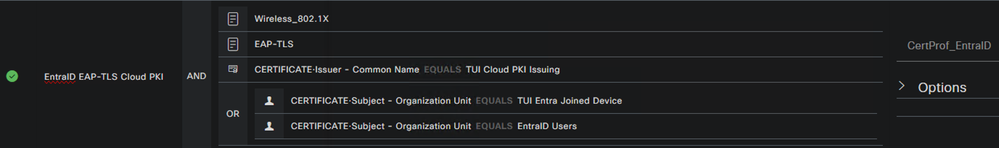
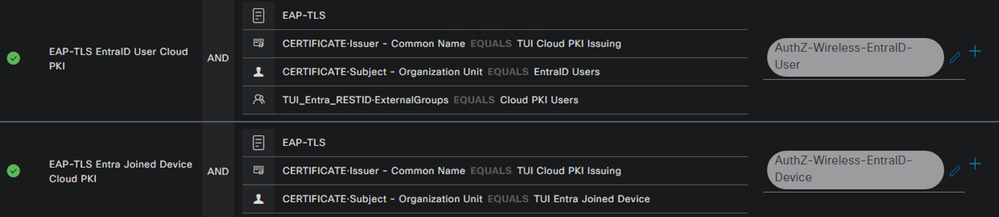
Authorization Policy
Two Authorization Policies are configured for this example use case; one for the User session, and one for the Device session.
The Authorization Policy is defined for the User session with the following conditions:
- Certificate issuer matching the CN of the Cloud PKI Issuing CA
- Certificate subject OU matching the ‘EntraID Users’ value defined in the Intune SCEP certificate profile for the User
- A REST ID lookup against the Microsoft Graph API for User membership in the Cloud PKI Users Entra ID Group
The Authorization Policy is defined for the Device session with the following conditions:
- Certificate issuer matching the CN of the Cloud PKI Issuing CA
- Certificate subject OU matching the ‘TUI Entra Joined Device’ value defined in the Intune SCEP certificate profiles for the Device
Example
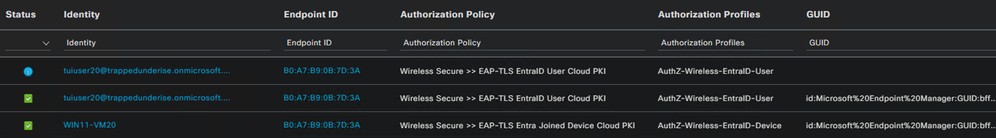
ISE Live Logs
The following screenshot shows the ISE Live Logs for the Device and User sessions from the Intune-enrolled test Windows VM.
Example
The detailed logs show the certificate Subject and Issuer attributes that were configured for the Certificate Profiles in Intune.
Example
Client Certificate Attributes
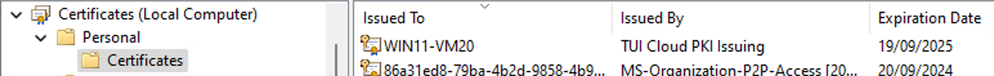
On the Windows client, use the MMC Certificate snap-ins to view the details of the certificate chain as well as the Device (Computer) and User certificates. Viewing the Computer certificate store requires local administrator permissions.
Device (Computer) Certificate examples
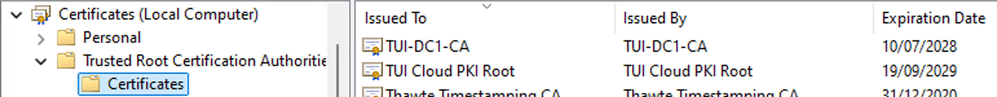
Example - Computer Root CA Certificates
Example - Computer Intermediate CA Certificates
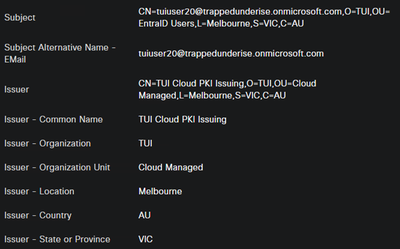
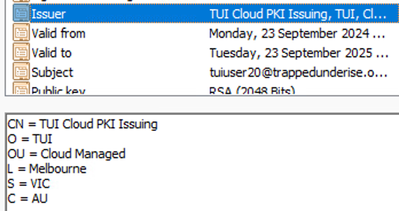
Example - Computer Identity Certificate
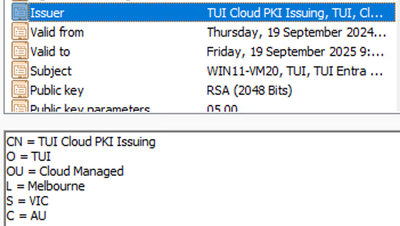
Example - Computer Identity Certificate Issuer
Example - Computer Identity Certificate Subject
Example - Computer Identity Certificate Subject
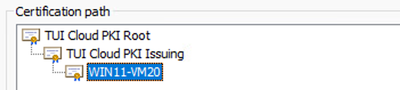
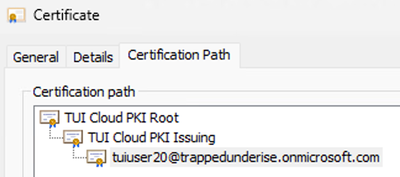
Example - Computer Identity Certificate Path
Example - User Identity Certificate
Example - User Identity Certificate Issuer
Example - User Identity Certificate Path
Client Supplicant Attributes
The following screenshots show the example Windows supplicant configuration applied by the Wifi Profile settings defined in Intune. To view these supplicant settings, you may need local administrator privileges and you must be connected to the SSID.
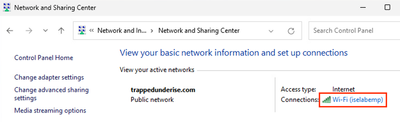
- Open the Control Panel and navigate to Network and Internet > Network Sharing Center
- Click on the Wifi connection
Example
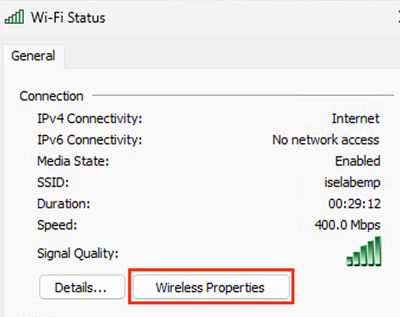
- Click on the Wifi Properties button
Example - Click on the Security tab
- Click the Settings button
Example - Properties
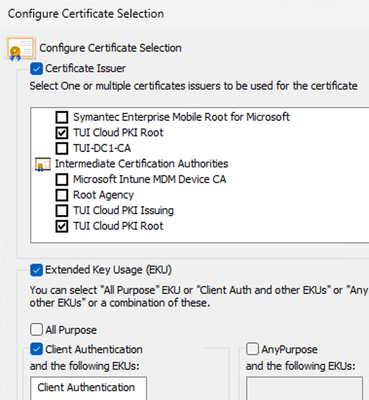
- Click the Advanced button to see the certificate selection settings
Example - Certificate Selection Settings
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: