- Cisco Community
- Technology and Support
- Service Providers
- Service Providers Knowledge Base
- Pre-Defined NAT White Paper
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
05-17-2019 02:25 AM - edited 05-17-2019 08:26 PM
Technical Guide to Pre-Defined NAT.
Abstract
In traditional NAT, due to the government regulations logging the CGN translations is mandatory and this is a huge cost incurrence. In Pre-defined NAT, the translations are known upfront, hence there is no need to maintain CGN logs. Pre-Defined NAT (or Deterministic NAT) is an IPv4 translation mechanism where Private IPv4 address is mapped to range of ports associated with corresponding Public IPv4 address. This is achieved with an algorithm without having to search massive CGN logs. The address and port translations are done as per the algorithm. In traditional NAT, the process of mapping a Private IPv4 to Public IPv4 or Private port to Public port is random. CGN sequential algorithm is based on RFC 7422 support for CGNAT44 deployment with A9K-VSM-500.
Goals
This White Paper aims to provide the reader with technical overview of Pre-Defined NAT. Details of port mapping algorithm will be described. This document will enable solid understanding of Pre-Deterministic NAT and its ability to position it effectively with Service Providers in regard to its benefits, relative to other options.
Solution Overview
Traditional NAT44 aims at preserving IPv4 address space by performing IPv4 to IPv4 translations, i.e. Private to Public IPv4 (and port). It allows to buy time before migrating to IPv6.NAT44 will rewrite the address and port. This translation will be maintained in local database and will be logged optionally. Ports are randomly picked from available ports associated with chosen outside IPv4 address. Each port is allocated once regardless of L4 protocol (UDP, TCP) is being used in the flow. CGN creates a translation binding between -

The Predefined NAT makes the translation “Predictable” or “Predefined”. CGN Pre-Defined NAT algorithm is based on RFC 7422 support for CGNAT44 deployment with A9K-VSM-500. The translations are predictable as they are done using a proprietary algorithm. The translation does NOT vary with time. In Pre-Defined NAT you can trace a subscriber’s Private IPv4 address from a Public IPv4 address and the associated port.
VSM is capable of hosting multiple VM's from where we can run the CGNAT application. The Service Enablement CLIs are needed to create, delete, access, and operate on VM. Traffic diversion may be done based on a static route or ACL-based forwarding (ABF).
- How does the Algorithm work?
- User configures the private IPv4 address to be served as well as the public pool.
- The Algorithm computes available port limit to per subscriber based on the pool and parameters such as dynamic start range.
- Equal number of ports are allocated for each subscriber. The algorithm assumes traffic will be evenly distributed across the subscribers. Hence load balancing will be handled by VSM.
- How can we trace a subscriber with Predefined NAT?
- A command is provided to show all translations.
- Just capture the output of this command right after configuring NAT.
- CLI for showing the current mappings:
- show cgn nat44 <nat instance name> mapping {inside-address | outside-address} inside-vrf <vrf name> <start address> [<end address>]
Example:
RP/0/RSP0/CPU0:router#show cgn nat44 nat1 mapping inside-address inside-vrf red start-addr 10.0.0.0 end-addr 10.0.0.255
Mapping details for address pool inside a Vrf
-----------------------------------------------------------------------------------------------
NAT44 instance : nat1
VRF : red
-----------------------------------------------------------------------------------------------
Inside Ip Outside IP Type Port Range Ports Used
Address Address
-----------------------------------------------------------------------------------------------
10.0.0.0 200.0.0.0 Predefined 2048-4095 41
10.0.0.1 200.0.0.0 Predefined 4096-6143 41
10.0.0.2 200.0.0.0 Predefined 6144-8191 41
10.0.0.3 200.0.0.0 Predefined 8192-10239 41
10.0.0.4 200.0.0.0 Predefined 10240-12287 41
10.0.0.5 200.0.0.0 Predefined 12288-14335 41
10.0.0.6 200.0.0.0 Predefined 14336-16383 41
10.0.0.7 200.0.0.0 Predefined 16384-18431 41
10.0.0.8 200.0.0.0 Predefined 18432-20479 41
10.0.0.9 200.0.0.0 Predefined 20480-22527 41
10.0.0.10 200.0.0.0 Predefined 22528-24575 41
10.0.0.11 200.0.0.0 Predefined 24576-26623 41
10.0.0.12 200.0.0.0 Predefined 26624-28671 41
10.0.0.13 200.0.0.0 Predefined 28672-30719 41
10.0.0.14 200.0.0.0 Predefined 30720-32767 41
Pre-Det NAT comes in different flavors, we will discuss below two
- Round Robin allocation &
- Sequential allocation of ports.
In Pre-det NAT Round-robin allocation of ports, the subscribers receive the same port number across pool of external IPv4 addresses. Suppose there are 10 addresses in the pool, and a subscriber is assigned 100 ports, the subscriber would receive range of ports such as ports 2000-2099 across all 10 external IPv4 addresses.
In Pre-det NAT Sequential allocation of ports, the next available address in the NAT pool is selected only when all the ports available from an address are exhausted. Example: first block goes to address1, second block goes to address 2 and so on. Sequential NAT was introduced on Cisco ASR9000. In Sequential NAT configuration, you can configure Private and Public pool as a range of IPv4 address.
You can perform the following:
Configure Dynamic port start range, Port block allocation size, Inside IPv4 pool, Outside IPv4 pool.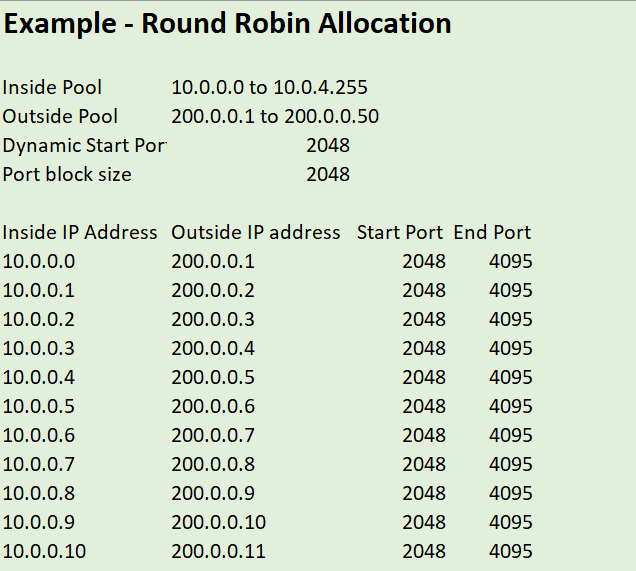
Pre-defined NAT configuration:
Configuring Sequential Predefined NAT
- configure terminal
- service cgn instance-name
- service-location preferred-active 0/x/CPU0 (‘x’ location of VSM card)
- service-type nat44 nat1
- dynamic-port-range start 2048
- inside-vrf vrf-name
- nat-mode
- predefined seq-private-pool start-address end-address
- map outside-vrf vrf-name seq-address-pool start-address end-address
- portlimit 2048
- commit
Sequential Predefined NAT Configuration: Example
service cgn cgn123
service-location preferred-active 0/3/CPU0
service-type nat44 nat1
dynamic-port-range start 2048
inside-vrf red
nat-mode
predefined seq-private-pool 10.0.0.0 10.0.0.255
!
map outside-vrf blue outsideServiceApp ServiceApp2 seq-address-pool 200.0.0.0 200.0.0.255
portlimit 2048
!
Verification
RP/0/RSP0/CPU0:router#show run service cgn cgn123
service cgn cgn123
service-location preferred-active 0/3/CPU0
service-type nat44 nat1
dynamic-port-range start 2048
inside-vrf red
nat-mode
predefined seq-private-pool 10.0.0.0 10.0.0.255
!
map outside-vrf blue seq-address-pool 200.0.0.0 200.0.0.255
portlimit 2048
!
!
RP/0/RSP0/CPU0:router#show cgn nat44 nat1 statistics
Statistics summary of NAT44 instance: 'nat1'
Number of active translations: 10496
Number of sessions: 0
Translations create rate: 0
Translations delete rate: 0
Inside to outside forward rate: 4078
Outside to inside forward rate: 4396
Inside to outside drops port limit exceeded: 0
Inside to outside drops system limit reached: 0
Inside to outside drops resource depletion: 0
No translation entry drops: 0
PPTP active tunnels: 0
PPTP active channels: 0
PPTP ctrl message drops: 0
Number of subscribers: 255
Drops due to session db limit exceeded: 0
Drops due to source ip not configured: 0
Pool address totally free: 0
Pool address used: 256
Pool address usage:
-------------------------------------------------
External Address Ports Used
-------------------------------------------------
200.0.0.0 41
200.0.0.0 41
200.0.0.1 41
200.0.0.2 41
200.0.0.3 41
200.0.0.3 41
200.0.0.4 41
200.0.0.5 41
Difference between Round Robin and Sequential allocation of ports:
|
Round Robin allocation |
Sequential allocation |
|
8 private pools for Serviceapp pair |
1 private pool for Serviceapp pair |
|
1 public address pool for Serviceapp pair |
1 public address pool for Serviceapp pair |
|
Dynamic-port-range start CLI supported |
Dynamic-port-range start CLI supported |
|
Per-vrf port limit supported |
Per-vrf port limit supported, it should be multiple of 2 |
|
Max. of 1M IP addresses (in private pool) supported |
Max. of 0.96M IP addresses (in private pool) supported |
|
Global port-limit not supported |
Global port-limit not supported |
|
Inside and outside pools can be specified only by IPv4 prefix |
Inside and outside pools can be specified by a start address and end address, instead of an IPv4 prefix |
|
By default, the private pool is round robin |
Key-word 'seq-private-pool' is used to define Private pool |
Customer Deployment considerations:
- Ensure you allocate port limit based on your SLA. Otherwise the service will be degraded with port limit exceeded warning.
- Try to keep the port limit uniform across subscribers.
- Any configuration change that results in changes in mapping deletes the existing translations. Therefore, ensure that you record such configuration changes. You might need this information to trace the port usage by a subscriber.
- Ensure that you configure NetFlow or syslog only if it is very much required.
- If you turn the predefined mode on or off for an inside VRF during the active translations, all the translations on that VRF are deleted.
- The global port limit parameter is not available for the Pre-defined mode. Even though you will be allowed to configure the global port limit, the inside VRF, which has predefined mode enabled, ignores that port limit and uses the port limit configured by the algorithm.
- The Bulk Port Allocation configuration is not available in the pre-defined mode. If you try to configure Bulk Port Allocation on an inside VRF that has the predefined mode enabled, the configuration is rejected during verification.
- The port-preservation option is not available in the predefined mode.
The following are some of the key benefits of implementing Pre-Det NAT:
- Logging is no longer necessary – Translation logging is required in today’s stateful implementations. Removing the need for logging results in reduced CAPEX and OPEX for Service Provider as they do not need to invest in infrastructure to collect and analyze translation logs which are often required to comply law enforcement requirements.
- No need to dimension a collector system nor store data for months/years – Removes the complexity and cost associated with sizing the logging solution over a period of time.
Summary
Pre-Defined NAT is an IPv4 translation mechanism to predict the translations even before actual translation. The outside IPv4 will exhaust all available ports based on the port limit configured before it picks up next IPv4 for another subscriber in case of sequential whereas port allocation is block wise per address in case of random allocation. In both cases you can scale subscribers up to 1 million and without requiring a use of logging solution.
References
Deterministic Address Mapping to Reduce Logging in Carrier-Grade NAT Deployments
https://tools.ietf.org/html/rfc7422
Config Guide
Glossary
- CGN – Carrier Grade NAT
- VSM – Virtualized Service Module
- CGNAT – Carrier Grade Network Address Translation
- SEQ-NAT – Sequential NAT
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community:

