- Cisco Community
- Technology and Support
- DevNet Hub
- DevNet Services
- Services Discussions
- Which information is accurate Cisco Advisory or CVRF?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-06-2023 12:07 AM
Hi Cisco PSIRT Team,
About Us: We are a team working on Vulnerability Assessment of Cisco devices.
Problem Statement: We are relying on CVRF for vulnerable versions. But the problem is for CVE-2022-20650,
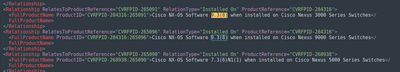
- From CVRF, Version 9.3(8) is given in vulnerable list for Cisco Nexus 9000 Series Switches (See image below)
- From Advisory, the same version is given as fixed release.(ref: cisco advisory)
There are even more CVEs having the same scenario.
Questions:
- Can we consider 9.3(8) as vulnerable for Nexus 9000 Series?
- Which should be considered for accurate information?
- What if we apply SMU patch, will it change the version in `show version` command output?
- Or, I'm I missing something?
Thank you.
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-10-2023 07:59 PM
Hello,
9.3(8) is vulnerable; hence why it has a SMU made available for that version. The CVRF/CSAF and Software Checker use the same data.
Software Checker has introduced support for SMU for IOS-XE; I need to check on that status for NX-OS. Support for the SMU details via API is also in development.
So to answer the questions:
1) Vulnerable. Software Checker and CSAF/CVRF indicate that.
2) The Software Checker; CSAF and CVRF are all indicating that 9.3(8) is vulnerable. The fact a SMU is made available for 9.3(8) also indicates that it is vulnerable. If you apply: nxos.CSCvz80191-n9k_ALL-1.0.0-9.3.8.lib32_n9000.rpm to 9.3(8) then it is fixed. But that is 9.3(8)+nxos.CSCvz80191-n9k_ALL-1.0.0-9.3.8.lib32_n9000.rpm
3) You should see it under Active Package(s): in the show version. Also show install active
4) The main thing here is that in the advisory the SMU listing is an indication of SMUs that exist for those affected versions. We are moving to having the SMU data fully integrated into Software Checker and the OpenVuln API. Till that time it remains a text option in the advisory.
HTH.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-10-2023 07:59 PM
Hello,
9.3(8) is vulnerable; hence why it has a SMU made available for that version. The CVRF/CSAF and Software Checker use the same data.
Software Checker has introduced support for SMU for IOS-XE; I need to check on that status for NX-OS. Support for the SMU details via API is also in development.
So to answer the questions:
1) Vulnerable. Software Checker and CSAF/CVRF indicate that.
2) The Software Checker; CSAF and CVRF are all indicating that 9.3(8) is vulnerable. The fact a SMU is made available for 9.3(8) also indicates that it is vulnerable. If you apply: nxos.CSCvz80191-n9k_ALL-1.0.0-9.3.8.lib32_n9000.rpm to 9.3(8) then it is fixed. But that is 9.3(8)+nxos.CSCvz80191-n9k_ALL-1.0.0-9.3.8.lib32_n9000.rpm
3) You should see it under Active Package(s): in the show version. Also show install active
4) The main thing here is that in the advisory the SMU listing is an indication of SMUs that exist for those affected versions. We are moving to having the SMU data fully integrated into Software Checker and the OpenVuln API. Till that time it remains a text option in the advisory.
HTH.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-10-2023 10:22 PM
Hello PR Oxman,
Thank you very much for clearing the doubts.
I Just remained one more questions,
Can I apply SMU Patch for below 9.3(8) versions, without upgrading to 9.3(8)?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-10-2023 10:43 PM
Hello,
No. A SMU is built for a specific platform/version of software. So a SMU for 9.3(8); needs 9.3(8) running on the switch.
For more information on NEXUS9000 and SMUs please consult: https://www.cisco.com/c/en/us/td/docs/switches/datacenter/nexus9000/sw/6-x/system_management/configuration/guide/b_Cisco_Nexus_9000_Series_NX-OS_System_Management_Configuration_Guide/sm_smu.html
For the particular advisory you referenced; there is a SMU for 7.0(3)I7(10) and 9.3(8).
| 7.0(3)I7(10) | Nexus 3000 and 9000 Series Switches | nxos.CSCvz80191-n9k_ALL-1.0.0-7.0.3.I7.10.lib32_n9000.rpm |
| 9.3(8) | Nexus 3000 and 9000 Series Switches |
nxos.CSCvz80191-n9k_ALL-1.0.0-9.3.8.lib32_n9000.rpm |
HTH
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide