- Cisco Community
- Technology and Support
- Small Business Support Community
- Routers - Small Business
- Re: IPSec attack on RV042
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
IPSec attack on RV042
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-29-2017 11:37 PM - edited 03-21-2019 10:56 AM
I just bought 2 RV042 to setup as gateway-to-gateway VPN connection.
One of those got the unknown IP address on the log keeps connecting to the router via IPSec port 500 all the time. I tried to create the firewall rule to deny this IP address but it seems doesn't work.
Here's the log:
Sep 30 13:06:57 2017 Connection Accepted UDP 57.73.28.18:500->xx.xx.xx.xx:500 on MAC=00:2UDP
Sep 30 13:16:31 2017 VPN Log packet from 57.73.28.18:500: received Vendor ID payload [RFC 3947]
Sep 30 13:16:31 2017 VPN Log packet from 57.73.28.18:500: received Vendor ID payload [RFC 3947]
Sep 30 13:16:31 2017 VPN Log packet from 57.73.28.18:500: ignoring Vendor ID payload [439b59f8ba676c4c7737ae22eab8f582]
Sep 30 13:16:31 2017 VPN Log packet from 57.73.28.18:500: ignoring Vendor ID payload [439b59f8ba676c4c7737ae22eab8f582]
Sep 30 13:16:31 2017 VPN Log packet from 57.73.28.18:500: ignoring Vendor ID payload [draft-ietf-ipsec-nat-t-ike-03]
Sep 30 13:16:31 2017 VPN Log packet from 57.73.28.18:500: ignoring Vendor ID payload [draft-ietf-ipsec-nat-t-ike-03]
Sep 30 13:16:31 2017 VPN Log packet from 57.73.28.18:500: ignoring Vendor ID payload [draft-ietf-ipsec-nat-t-ike-02_n]
Sep 30 13:16:31 2017 VPN Log packet from 57.73.28.18:500: ignoring Vendor ID payload [draft-ietf-ipsec-nat-t-ike-02_n]
Sep 30 13:16:31 2017 VPN Log packet from 57.73.28.18:500: [Tunnel Negotiation Info] <<< Responder Received Main Mode 1st packet
Sep 30 13:16:31 2017 VPN Log packet from 57.73.28.18:500: [Tunnel Negotiation Info] <<< Responder Received Main Mode 1st packet
Sep 30 13:16:31 2017 VPN Log packet from 57.73.28.18:500: initial Main Mode message received on xx.xx.xx.xx:500 but no connection has been authorized with policy=PSK
- Labels:
-
Small Business Routers
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-30-2017 08:43 AM
Hello,
Not sure how did you create that but should work.
The problem per se is simple to understand. Someone saw your UDP 500 port openned and gave it a try.
Try to create in Service Management a specific UDP port 500 and add it on the rule with your IP as destination and the attacker IP as source.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-01-2017 09:03 PM
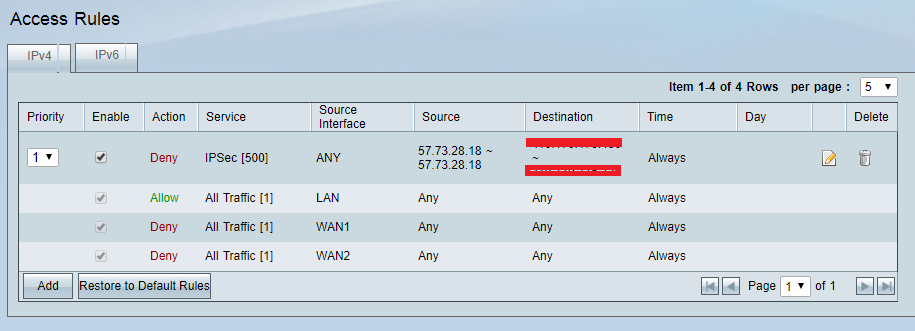
I tried to create the rule as you mentioned but it still no luck. That IP keeps attacking 500 port.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-02-2017 05:13 AM
Hi,
Make sure your firewall is enable:
Firewall > General
Take a look here for more detail
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-02-2017 08:09 AM - edited 10-02-2017 06:32 PM
Hi Flavio Miranda,
Thanks for your help.
I'm sure that the firewall is enabled but it still doesn't work.
I'm still using firmware version v4.2.2.08, is it a bug about the firewall rule on the firmware?
And I noticed the strange interface "MAC=00:2UDP"where the connection accepted that IP address.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-02-2017 07:11 PM
If you were using ASA would be easy by blocking at control plane level but RV042 I don't think is possible.
The problem is this, this kind of traffic is forwarded to control plane, not data plane, that's why normal acl does not work.
But you don't need to worry. As long as the other side does not have your PSK this VPN will never be established.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide