- Cisco Community
- Technology and Support
- Small Business Support Community
- Routers - Small Business
- RV120 Tunnel Crashing regularly
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
RV120 Tunnel Crashing regularly
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-16-2013 09:12 AM
I have a RV180 v1 set up in a remote site doing gateway to gateway IPSEC tunnels to two Watchguard XTM510s (in different locations). The RV180 is behind a DSL router with a dynamic IP, so the tunnels are created using aggressive mode. DPD and NAT-T are turned on, and the tunnels will build and pass traffic without any issue.
The problem I am having is that the tunnels crash regularly, see this graph: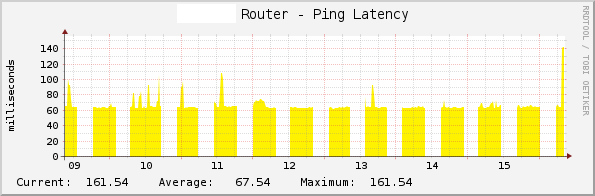
The pattern is tied to the key lifetime. When I look at the log on the RV180, it looks like the phase 1 SA and the phase 2 SA are expiring at different times, and when they expire they aren't getting recreated. A sample of the logs from the last gap of that graph is here:
Wed May 15 23:29:08 2013 (GMT -0800): [CO-Router] [IKE] INFO: Sending Informational Exchange: notify payload[10637]
Wed May 15 23:29:28 2013 (GMT -0800): [CO-Router] [IKE] INFO: Sending Informational Exchange: notify payload[10637]
Wed May 15 23:29:48 2013 (GMT -0800): [CO-Router] [IKE] INFO: Sending Informational Exchange: notify payload[10637]
Wed May 15 23:30:06 2013 (GMT -0800): [CO-Router] [IKE] INFO: Responding to new phase 2 negotiation: 192.168.1.4[0]<=>5.5.5.225[0]
Wed May 15 23:30:06 2013 (GMT -0800): [CO-Router] [IKE] INFO: Using IPsec SA configuration: 192.168.9.0/24<->192.168.0.0/26
Wed May 15 23:30:06 2013 (GMT -0800): [CO-Router] [IKE] INFO: Adjusting peer's encmode 61443(61443)->Tunnel(1)
Wed May 15 23:30:07 2013 (GMT -0800): [CO-Router] [IKE] INFO: IPsec-SA established[UDP encap 4500->4500]: ESP/Tunnel 5.5.5.225->192.168.1.4 with spi=126025766(0x7830026)
Wed May 15 23:30:07 2013 (GMT -0800): [CO-Router] [IKE] INFO: IPsec-SA established[UDP encap 4500->4500]: ESP/Tunnel 192.168.1.4->5.5.5.225 with spi=1807976333(0x6bc3878d)
Wed May 15 23:30:07 2013 (GMT -0800): [CO-Router] [IKE] INFO: Sending Informational Exchange: notify payload[10637]
Wed May 15 23:30:08 2013 (GMT -0800): [CO-Router] [IKE] INFO: Purged IPsec-SA with proto_id=ESP and spi=2480067544(0x93d2d3d8).
Wed May 15 23:30:08 2013 (GMT -0800): [CO-Router] [IKE] INFO: Purged IPsec-SA with proto_id=ESP and spi=139686414(0x853720e).
Wed May 15 23:30:17 2013 (GMT -0800): [CO-Router] [IKE] INFO: ISAKMP-SA expired 192.168.1.4[4500]-5.5.5.225[4500] spi:e2eb1d36ca501ef3:63c708129bc6fb9f
Wed May 15 23:30:17 2013 (GMT -0800): [CO-Router] [IKE] INFO: Sending Informational Exchange: delete payload[]
Wed May 15 23:30:18 2013 (GMT -0800): [CO-Router] [IKE] INFO: ISAKMP-SA deleted for 192.168.1.4[4500]-5.5.5.225[4500] with spi:e2eb1d36ca501ef3:63c708129bc6fb9f
Wed May 15 23:36:13 2013 (GMT -0800): [CO-Router] [IKE] INFO: [IPSEC_VPN] IPsec-SA expired: ESP/Tunnel 4.4.4.1->192.168.1.4 with spi=246339102(0xeaed61e)
Wed May 15 23:36:13 2013 (GMT -0800): [CO-Router] [IKE] INFO: Configuration found for 4.4.4.1.
Wed May 15 23:36:13 2013 (GMT -0800): [CO-Router] [IKE] INFO: Initiating new phase 2 negotiation: 192.168.1.4[0]<=>4.4.4.1[0]
Wed May 15 23:36:13 2013 (GMT -0800): [CO-Router] [IKE] INFO: Adjusting encryption mode to use UDP encapsulation
Wed May 15 23:36:13 2013 (GMT -0800): [CO-Router] [IKE] WARNING: Ignore RESPONDER-LIFETIME notification from 4.4.4.1[4500].
Wed May 15 23:36:13 2013 (GMT -0800): [CO-Router] [IKE] INFO: Adjusting peer's encmode 61443(61443)->Tunnel(1)
Wed May 15 23:36:13 2013 (GMT -0800): [CO-Router] [IKE] INFO: IPsec-SA established[UDP encap 4500->4500]: ESP/Tunnel 4.4.4.1->192.168.1.4 with spi=29839733(0x1c75175)
Wed May 15 23:36:13 2013 (GMT -0800): [CO-Router] [IKE] INFO: IPsec-SA established[UDP encap 4500->4500]: ESP/Tunnel 192.168.1.4->4.4.4.1 with spi=3303632320(0xc4e96dc0)
Wed May 15 23:36:13 2013 (GMT -0800): [CO-Router] [IKE] INFO: Purged IPsec-SA with proto_id=ESP and spi=246339102(0xeaed61e).
Wed May 15 23:36:14 2013 (GMT -0800): [CO-Router] [IKE] INFO: Sending Informational Exchange: notify payload[10637]
<SNIP several lines of the same between these>
Wed May 15 23:58:33 2013 (GMT -0800): [CO-Router] [IKE] INFO: Sending Informational Exchange: notify payload[10637]
Wed May 15 23:58:48 2013 (GMT -0800): [CO-Router] [IKE] INFO: ISAKMP-SA expired 192.168.1.4[4500]-4.4.4.1[4500] spi:447f971442f56e50:e746a025318ce9f8
Wed May 15 23:58:48 2013 (GMT -0800): [CO-Router] [IKE] INFO: Sending Informational Exchange: delete payload[]
Wed May 15 23:58:49 2013 (GMT -0800): [CO-Router] [IKE] INFO: ISAKMP-SA deleted for 192.168.1.4[4500]-4.4.4.1[4500] with spi:447f971442f56e50:e746a025318ce9f8
Thu May 16 04:18:19 2013 (GMT -0800): [CO-Router] [IKE] INFO: [IPSEC_VPN] IPsec-SA expired: ESP/Tunnel 192.168.1.4->5.5.5.225 with spi=1993017196(0x76cb076c)
Thu May 16 04:18:19 2013 (GMT -0800): [CO-Router] [IKE] INFO: Configuration found for 5.5.5.225.
Thu May 16 04:18:19 2013 (GMT -0800): [CO-Router] [IKE] INFO: Initiating new phase 1 negotiation: 192.168.1.4[500]<=>5.5.5.225[500]
Thu May 16 04:18:19 2013 (GMT -0800): [CO-Router] [IKE] INFO: Beginning Aggressive mode.
Thu May 16 04:18:19 2013 (GMT -0800): [CO-Router] [IKE] INFO: NAT-Traversal is Enabled
Thu May 16 04:18:19 2013 (GMT -0800): [CO-Router] [IKE] INFO: [isakmp_agg.c:257]: XXX: NUMNATTVENDORIDS: 3
Thu May 16 04:18:19 2013 (GMT -0800): [CO-Router] [IKE] INFO: [isakmp_agg.c:261]: XXX: setting vendorid: 4
Thu May 16 04:18:19 2013 (GMT -0800): [CO-Router] [IKE] INFO: [isakmp_agg.c:261]: XXX: setting vendorid: 8
Thu May 16 04:18:19 2013 (GMT -0800): [CO-Router] [IKE] INFO: [isakmp_agg.c:261]: XXX: setting vendorid: 9
Thu May 16 04:18:19 2013 (GMT -0800): [CO-Router] [IKE] INFO: [IPSEC_VPN] IPsec-SA expired: ESP/Tunnel 5.5.5.225->192.168.1.4 with spi=57594486(0x36ed276)
Thu May 16 04:18:20 2013 (GMT -0800): [CO-Router] [IKE] INFO: Received Vendor ID: DPD
Thu May 16 04:18:20 2013 (GMT -0800): [CO-Router] [IKE] INFO: Received Vendor ID: draft-ietf-ipsec-nat-t-ike-02
Thu May 16 04:18:20 2013 (GMT -0800): [CO-Router] [IKE] INFO: NAT-D payload does not match for 192.168.1.4[500]
Thu May 16 04:18:20 2013 (GMT -0800): [CO-Router] [IKE] INFO: NAT-D payload matches for 5.5.5.225[500]
Thu May 16 04:18:20 2013 (GMT -0800): [CO-Router] [IKE] INFO: For 5.5.5.225[500], Selected NAT-T version: draft-ietf-ipsec-nat-t-ike-02
Thu May 16 04:18:20 2013 (GMT -0800): [CO-Router] [IKE] INFO: NAT detected: ME
Thu May 16 04:18:20 2013 (GMT -0800): [CO-Router] [IKE] INFO: for debugging :: changing portsThu May 16 04:18:20 2013 (GMT -0800): [CO-Router] [IKE] INFO: port changed !!
Thu May 16 04:18:20 2013 (GMT -0800): [CO-Router] [IKE] INFO: ISAKMP-SA established for 192.168.1.4[4500]-5.5.5.225[4500] with spi:526e36cf7be01935:8934e8ae2fdb9fad
Thu May 16 04:18:20 2013 (GMT -0800): [CO-Router] [IKE] INFO: Sending Informational Exchange: notify payload[608]
Thu May 16 04:18:20 2013 (GMT -0800): [CO-Router] [IKE] INFO: Initiating new phase 2 negotiation: 192.168.1.4[0]<=>5.5.5.225[0]
Thu May 16 04:18:20 2013 (GMT -0800): [CO-Router] [IKE] INFO: Adjusting encryption mode to use UDP encapsulation
Thu May 16 04:18:20 2013 (GMT -0800): [CO-Router] [IKE] WARNING: Ignore RESPONDER-LIFETIME notification from 5.5.5.225[4500].
Thu May 16 04:18:20 2013 (GMT -0800): [CO-Router] [IKE] INFO: Adjusting peer's encmode 61443(61443)->Tunnel(1)
Thu May 16 04:18:20 2013 (GMT -0800): [CO-Router] [IKE] INFO: IPsec-SA established[UDP encap 4500->4500]: ESP/Tunnel 5.5.5.225->192.168.1.4 with spi=131754931(0x7da6bb3)
Thu May 16 04:18:20 2013 (GMT -0800): [CO-Router] [IKE] INFO: IPsec-SA established[UDP encap 4500->4500]: ESP/Tunnel 192.168.1.4->5.5.5.225 with spi=1507917835(0x59e1000b)
Thu May 16 04:18:23 2013 (GMT -0800): [CO-Router] [IKE] INFO: Responding to new phase 2 negotiation: 192.168.1.4[0]<=>5.5.5.225[0]
Thu May 16 04:18:23 2013 (GMT -0800): [CO-Router] [IKE] INFO: Using IPsec SA configuration: 192.168.9.0/24<->192.168.0.0/26
Thu May 16 04:18:23 2013 (GMT -0800): [CO-Router] [IKE] INFO: Adjusting peer's encmode 61443(61443)->Tunnel(1)
Thu May 16 04:18:23 2013 (GMT -0800): [CO-Router] [IKE] INFO: IPsec-SA established[UDP encap 4500->4500]: ESP/Tunnel 5.5.5.225->192.168.1.4 with spi=120862776(0x7343838)
Thu May 16 04:18:23 2013 (GMT -0800): [CO-Router] [IKE] INFO: IPsec-SA established[UDP encap 4500->4500]: ESP/Tunnel 192.168.1.4->5.5.5.225 with spi=2967981184(0xb0e7cc80)
Thu May 16 04:18:25 2013 (GMT -0800): [CO-Router] [IKE] INFO: Sending Informational Exchange: notify payload[10381]
Thu May 16 04:18:28 2013 (GMT -0800): [CO-Router] [IKE] INFO: Sending Informational Exchange: notify payload[10637]
Thu May 16 04:18:28 2013 (GMT -0800): [CO-Router] [IKE] INFO: Sending Informational Exchange: delete payload[]
Thu May 16 04:18:28 2013 (GMT -0800): [CO-Router] [IKE] INFO: an undead schedule has been deleted: 'pk_recvupdate'.
Thu May 16 04:46:50 2013 (GMT -0800): [CO-Router] [IKE] INFO: [IPSEC_VPN] IPsec-SA expired: ESP/Tunnel 192.168.1.4->4.4.4.1 with spi=2429062956(0x90c88f2c)
Thu May 16 04:46:50 2013 (GMT -0800): [CO-Router] [IKE] INFO: Configuration found for 4.4.4.1.
Thu May 16 04:46:50 2013 (GMT -0800): [CO-Router] [IKE] INFO: Initiating new phase 1 negotiation: 192.168.1.4[500]<=>4.4.4.1[500]
Thu May 16 04:46:50 2013 (GMT -0800): [CO-Router] [IKE] INFO: Beginning Aggressive mode.
Thu May 16 04:46:50 2013 (GMT -0800): [CO-Router] [IKE] INFO: NAT-Traversal is Enabled
Thu May 16 04:46:50 2013 (GMT -0800): [CO-Router] [IKE] INFO: [isakmp_agg.c:257]: XXX: NUMNATTVENDORIDS: 3
Thu May 16 04:46:50 2013 (GMT -0800): [CO-Router] [IKE] INFO: [isakmp_agg.c:261]: XXX: setting vendorid: 4
Thu May 16 04:46:50 2013 (GMT -0800): [CO-Router] [IKE] INFO: [isakmp_agg.c:261]: XXX: setting vendorid: 8
Thu May 16 04:46:50 2013 (GMT -0800): [CO-Router] [IKE] INFO: [isakmp_agg.c:261]: XXX: setting vendorid: 9
Thu May 16 04:46:50 2013 (GMT -0800): [CO-Router] [IKE] INFO: [IPSEC_VPN] IPsec-SA expired: ESP/Tunnel 4.4.4.1->192.168.1.4 with spi=267273663(0xfee45bf)
Thu May 16 04:46:51 2013 (GMT -0800): [CO-Router] [IKE] INFO: Received Vendor ID: DPD
Thu May 16 04:46:51 2013 (GMT -0800): [CO-Router] [IKE] INFO: Received Vendor ID: draft-ietf-ipsec-nat-t-ike-02
Thu May 16 04:46:51 2013 (GMT -0800): [CO-Router] [IKE] INFO: NAT-D payload does not match for 192.168.1.4[500]
Thu May 16 04:46:51 2013 (GMT -0800): [CO-Router] [IKE] INFO: NAT-D payload matches for 4.4.4.1[500]
Thu May 16 04:46:51 2013 (GMT -0800): [CO-Router] [IKE] INFO: For 4.4.4.1[500], Selected NAT-T version: draft-ietf-ipsec-nat-t-ike-02
Thu May 16 04:46:51 2013 (GMT -0800): [CO-Router] [IKE] INFO: NAT detected: ME
Thu May 16 04:46:51 2013 (GMT -0800): [CO-Router] [IKE] INFO: for debugging :: changing portsThu May 16 04:46:51 2013 (GMT -0800): [CO-Router] [IKE] INFO: port changed !!
Thu May 16 04:46:51 2013 (GMT -0800): [CO-Router] [IKE] INFO: ISAKMP-SA established for 192.168.1.4[4500]-4.4.4.1[4500] with spi:5ac8293133c36006:156da7568412e10f
Thu May 16 04:46:51 2013 (GMT -0800): [CO-Router] [IKE] INFO: Sending Informational Exchange: notify payload[608]
Thu May 16 04:46:51 2013 (GMT -0800): [CO-Router] [IKE] INFO: Initiating new phase 2 negotiation: 192.168.1.4[0]<=>4.4.4.1[0]
Thu May 16 04:46:51 2013 (GMT -0800): [CO-Router] [IKE] INFO: Adjusting encryption mode to use UDP encapsulation
Thu May 16 04:46:51 2013 (GMT -0800): [CO-Router] [IKE] WARNING: Ignore RESPONDER-LIFETIME notification from 4.4.4.1[4500].
Thu May 16 04:46:51 2013 (GMT -0800): [CO-Router] [IKE] INFO: Adjusting peer's encmode 61443(61443)->Tunnel(1)
Thu May 16 04:46:51 2013 (GMT -0800): [CO-Router] [IKE] INFO: IPsec-SA established[UDP encap 4500->4500]: ESP/Tunnel 4.4.4.1->192.168.1.4 with spi=78533723(0x4ae545b)
Thu May 16 04:46:51 2013 (GMT -0800): [CO-Router] [IKE] INFO: IPsec-SA established[UDP encap 4500->4500]: ESP/Tunnel 192.168.1.4->4.4.4.1 with spi=3286012270(0xc3dc916e)
Thu May 16 04:46:56 2013 (GMT -0800): [CO-Router] [IKE] INFO: Sending Informational Exchange: notify payload[10637]
Thu May 16 05:03:50 2013 (GMT -0800): [CO-Router] [IKE] INFO: an undead schedule has been deleted: 'pk_recvupdate'.
Thu May 16 05:03:50 2013 (GMT -0800): [CO-Router] [IKE] INFO: Purged IPsec-SA with proto_id=ESP and spi=3303632320(0xc4e96dc0).
Thu May 16 05:04:47 2013 (GMT -0800): [CO-Router] [IKE] INFO: Responding to new phase 2 negotiation: 192.168.1.4[0]<=>4.4.4.1[0]
Thu May 16 05:04:47 2013 (GMT -0800): [CO-Router] [IKE] INFO: Using IPsec SA configuration: 192.168.9.0/24<->192.168.0.64/26
Thu May 16 05:04:47 2013 (GMT -0800): [CO-Router] [IKE] INFO: Adjusting peer's encmode 61443(61443)->Tunnel(1)
Thu May 16 05:04:47 2013 (GMT -0800): [CO-Router] [IKE] INFO: IPsec-SA established[UDP encap 4500->4500]: ESP/Tunnel 4.4.4.1->192.168.1.4 with spi=142477(0x22c8d)
Thu May 16 05:04:47 2013 (GMT -0800): [CO-Router] [IKE] INFO: IPsec-SA established[UDP encap 4500->4500]: ESP/Tunnel 192.168.1.4->4.4.4.1 with spi=2721682347(0xa23993ab)
Thu May 16 05:04:47 2013 (GMT -0800): [CO-Router] [IKE] INFO: Sending Informational Exchange: notify payload[10637]
Thu May 16 05:04:50 2013 (GMT -0800): [CO-Router] [IKE] INFO: Sending Informational Exchange: notify payload[10637]
Thu May 16 05:05:11 2013 (GMT -0800): [CO-Router] [IKE] INFO: Sending Informational Exchange: notify payload[10637]
Does anyone see anything in there that might explain my issue?
- Labels:
-
Small Business Routers
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-20-2013 02:12 PM
Dear Ben,
Thank you for contacting Cisco Support Community. Please try this out:
VPN > IPsec > Advanced VPN Setup
Under your existing VPN Policy;
1. Disable Perfect Forward Secrecy (PFS Key Group unchecked)
2. Under exchange mode; change to "Main" instead of "Aggressive"
I'll be looking forward to your reply.
Kind regards,
Jeffrey Rodriguez S.
Cisco Customer Support Engineer.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-21-2013 08:19 AM
Hey Jeffrey,
PFS is already disabled.
The RV180 is NAT'd behind another router with a dynamic IP, for that situation don't I need aggressive mode?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-23-2013 01:47 PM
Hey Jeffrey,
Do you have any other information for me on this?
Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-27-2013 03:56 PM
Hello Ben,
I am sorry for the delay on my answer. You do need Aggressive Mode setting based on your clarification. I suggest you to backup your configuration, reset to factory conditions, upgrade the firmware to the latest v1.0.2.6 and then restore the configuration. Please refer to the admin guide, starting on page 151 for instructions in how to do all that:
http://www.cisco.com/en/US/docs/routers/csbr/rv180w/administration/guide/rv180w_admin.pdf
Firmware update at:
http://software.cisco.com/download/release.html?mdfid=284005904&softwareid=282465789&release=1.0.1.9
Just in case the problem persists, I then suggest you to contact the Small Business Contact Center for further assistance:
https://www.cisco.com/en/US/support/tsd_cisco_small_business_support_center_contacts.html
Please let me know if there is any further assistance I may help you with.
Kind regards,
Jeffrey Rodriguez S. .:|:.:|:.
Cisco Customer Support Engineer
*Please rate the Post so other will know when an answer has been found.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide