- Cisco Community
- Technology and Support
- Small Business Support Community
- Routers - Small Business
- Re: RV340 behind NAT/Firewall router
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-13-2021 04:55 AM
Hi
We bought two RV340(W) to create a site-to-site VPN, eventually. But for now, we have basic configuration problems.
Both RV340 will be behind routers with active NAT/firewalls/DHCP. VPN-Router 1 will be in local network 1 with local IP addresses 10.150.150.1/24, with static IP addres 10.150.150.2 and default gateway 10.150.150.1. VPN-router 2 will be in local network 2 with local IP addresses 10.150.155.1/24, with static IP address 10.150.155.2 and default gateway 10.150.155.1.
On both VPN-routers I disabled the Firewall and NAT, allowed DHCP-redirection and remote web GUI access. The VPN-router will be directly attached to the main internet router (with NAT/firewall), and all other network clients will be connected to the LAN ports of the VPN-router.
I was able to access the web GUI from "outside" (the WAN port of the VPN router), but not from "inside" (LAN ports), also no traffic was forwarded from the LAN ports to the "outside" local network. Then I tried to configure VLAN 1 on 10.150.150.1/24, but from that point on the VPN-Router was not accessible anymore and I had to reset it to defaults.
Can somebody please tell me what the correct configuration for this use case is?
The internet routers in question are FritzBoxes, they can't be set to bridge mode, among others because they also provide IP telephony (VoIP <-> DECT).
Best regards
Roman
Solved! Go to Solution.
- Labels:
-
Small Business Routers
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-21-2021 09:52 AM
Oh Ok...could you update the firmware on both RV34Xs to v1.0.03.22 which is the latest i guess...or anything later?
I can vouch my Job on the S2S tunnel config that i sent you...i have used and deployed this similar configurations in similar scenarios "hundreds of time" in my career till now (of 24+ years)....so iam not at all doubting or worried about the s2s tunnel config that i sent you
ofcourse by bet/vouch is based on my assumption and bet that:
a) the ipsec tunnel negotiation protocol packets - IKE-udp-500, IKE-udp-4500, IP-Proto-50-ESP are being processed/forwarded thru by the ISP-Routers till both RV340s...
b) And in case you configure the "Remote-Endoint: FQDN - routerX.dyndns.org on both the RV340s or either of them..iam assuming and betting that both RV340s are able to successfully do a dns-resolve of the fqdn and resolve it to the "public-ipaddress" allotted by the respective ISP routers (which you have already confirmed that it happens becos you are accessing the GUI of the remote RV340 using the dyndns fqdn
so yes, you go ahead and update the firmware and also do a permanent-save and reboot
- Note: You dont need any firewall rules to pass/allow/forward/permit any of the IPsec/IKE/ESP traffic (including any nat-bypass rules after the tunnel is UP). On RV34X platforms, these required rules are all installed/applied implicitly in the background automatically when required with the respective configurations enabled/applied on RV34X....so dont add any manual explicit rules..they will create problems instead
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-13-2021 06:52 AM
Hi,
If your RV router behind NAT router, you need to forward TCP/UDP for port 500 and 4500 from internet router to RV router's WAN IP (ex. 10.150.150.2 in your site 1). both RVs need to get above ports redirected from respective internet routers. then use internet router's public IP to establish VPNs.
rate if this solved your concern
Regards,
KB
Good luck
KB
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-13-2021 07:13 AM
Hi Kasun
Thank you for your answer. I understand that, but this is not the issue. The problem is that the network traffic from the LAN-Ports of the RW340 is not routed to the WAN, at least the PC connected to the LAN port does not receive a DHCP answer, although I switched on DHCP relay.
And once I switch off Firewall/NAT etc. of the RW340, the network traffic is routed, but then the VPN-Router does not respond anymore on its IP address.
Regards
Roman
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-13-2021 05:14 PM
Hi
Host(192.168.1.x)-----(192.168.1.1)vlan1[RV340]wan1(10.150.150.2)-----(x.150.1)lan[Router]wan----internet---{isp}
1. with reference to above setup (which is your deployment):
a). The use of dhcp-relay (enabled on RV340 in this case) is to allow the use of "dhcp-server" on Router (and NOT the dhcp-server on vlan1 interface of RV340)....SO with the use of dhcp-relay the dhcp-server on router will ASSIGN IPADDRESSES IN 192.168.1.0/24 subnet to the Hosts in the lan-side of RV340 (and also assign the default-gateway address of 192.168.1.1)
b). So is the dhcp-server on "isp-Router" configured with a pool/scope of 192.168.1.x/24 or not?
c) It would be better and efficient to enable and use the dhcp-server on RV340 to assign ipaddresses to hosts in the 192.168.1.x subnet (with the default-gw address assigned as 192.168.1.1)
2. As already mentioned in previous post, in your deployment with both RV340s behind the NAT-routers, you MUST configure DNAT/1:1-STATIC-NAT on atleast one of the ISP-routers for the vpn tunnel establishment...else it cannot be done
- ideally if you want to initiate tunnel establishment from either site1 and/or site2, then the DNAT/1:1-static-nat should be configured on both isp-routers
- if dnat/static-nat on isp-router is applied on only 1 site, then the ipsec tunnel has to always initiated from the other site-rv340
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-14-2021 03:18 AM
Hi
Thanks for your answer. Your drawing is correct, except that the address range given out by the ISP-Router is 10.150.150.x (20 and up), not 192.168.1.x. Once I figured out how to configure the RV340, I will enable port forwarding on the ISP router.
So, my idea would be that the RV340 would forward all traffic from its LAN ports to the WAN port, where the ISP-Router is connected, and vice versa. Only accesses to the other subnet (10.150.155.x) should be routed through the VPN. How should I configure the RV340 in this case?
- Should it be switched to bridge mode? I tried that, but then couldn't connect to its web interface anymore. How can one connect to the web interface in bridge mode?
- I also tried to switch it to DHCP mode, and enable DHCP relay, firewall and NAT disabled. In this case, a PC connected to the LAN interface did not receive a DHCP answer, and couldn't see anything on the network. Is there anything I can do to diagnose the problem?
A third option would be to connect the RV340 as "exposed host", and then it would act as Firewall, NAT-Host and DHCP server. I will try that once I have some time.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-14-2021 06:42 AM
Hi
This is my very humble suggestion. You should look at it in terms of logical flow of the traffic between the 2 sites that are connected via a ipsec vpn-tunnel. You should do it one step at a time instead of trying multiple methods
1. So let us first finalize about your VPN topology, what are the networks (behind site1-rv340 and site2-rv340) are you trying to protect?
Hosts(subnetX)----vlanX[RV340GW1]wan1----lan[Router1]wan--internet--wan[Router2]lan-----wan1[RV340GW2]vlanY---(subnetY)Hosts
- If you want Hosts behind the RV340GW1 to get their IPaddresses from Router1 in the subnet 10.150.150.x AND your wan1 ipaddress of RV340GW1 is also in the same subnet 10.150.150.2, what is the VPN tunnel going to protect? What is the vpn-policy?
- so please finalize what will be your vpn policy...which network/subnet will the vpn tunnel on RV340 will protect?
2. If you want the Hosts to have ipaddresses in 10.150.150.x range from the dhcp-server on router1, then a bridge can be configured on RV340GW1....but then again these hosts with ipaddresses 10.150.150.x cannot be protected by the vpn tunnel to site-2 (and the same is the case in site2)
3. On the RV340GW1, When you bridge say for example the vlan1-interface and wan1, you will also be configuring the wan1 ipaddress as 10.150.150.2/24 AND the hosts will now get their ipaddresses from the dhcp-server on router1 in the iprange 10.150.150.x...
- so that would mean that from the hosts (with ipaddr 10.150.150.x) if you want to access the GUI of RV340GW1, then connect using the ipaddress 10.150.150.2...(and you may need to enable Remote-Management access on the RV340GW1 firewall before you bridge it)
....and so on and so forth of all the complications with your present network deployment requirement
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-14-2021 06:50 AM
And then there is this scenario in your network...both RV340s are behind the NAT-Routers...so please ensure that there is DNAT/1:1-static-nat/port-forward rules on each of the routers (or atleast 1 of the routers) for Ike/isakmp udp-500 and udp-4500, ESP (iproto-50)
- The DNAT/static-nat/port-forward on the Router1/Router2 are necessary....so get that done first before configuring vpn-tunnel
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-15-2021 01:05 AM
Thank you for your suggestions. I appreciate your support!
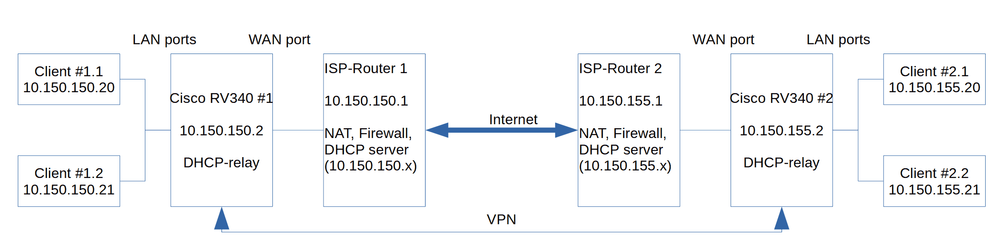
I drew a small sketch to show what I want to achieve:
I hope that makes it more clear. As you described, both ISP routers will enable port forwarding of the UDP ports 500 and 4500 and ESP protocol to the RV340's.
The goal is that all clients of both local networks see all clients of their own and the respective other networks. This means that the RV340's should forward all traffic that does not affect them (internet traffic or 10.150.15x.1 to WAN, the rest to the LAN), but RV340 #1 should route the traffic to 10.150.155.x through the VPN, while RV340 #2 should route traffic to 10.150.150.x trough the VPN.
What is the simplest configuration of the RV340's to achieve this?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-15-2021 05:14 AM
Hi
Thank you so much for the clear picture you have posted. It certainly helps in coming out with possible solutions
Its very interesting and challenging...i love it!!!. Please kindly give me a day atleast, i will try to simulate this in my network which has multiple RV34Xs and i could easily simulate the ISP-connectivity as yours...i have a certain idea in my head for the above setup, but i need to confirm with actual results. Only then i will post the sample configs that you will need to apply on both RV34X routers
will get back to you with some answer or the other ASAP
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-15-2021 10:08 AM - edited 09-15-2021 10:14 AM
Hi
1. If you consider only left-side of your setup
Hosts---x.x.x.1[RV340]10.150.150.2-----150.1[Router1]
Firstly enabling dhcp-relay on RV340 will NOT result in the Router1 assigning ip-addresses to hosts in the same subnet 10.150.150.x.
The dhcp-server on Router1 has to be configured with a dhcp-ipaddr-scope in "x.x.x.0" subnet and it will assign addresses to hosts (behind RV340) in the range of x.x.x.0 subnet only. This is the functionality of dhcp-relay and it cannot work otherwise
Note: And dhcp-relay is usually used when you dont have a dhcp-server in the lan-segment of RV340 (or a dhcp-server on rv340)...OR you use a dhcp-relay to forward dhcp-client requests to a centralized dhcp-server - but this server will have a dhcp-scope for x.x.x.0 only
2. Now I tried the same network deployment and checked with bridging the wan1/vlanx on RV340, and i could get the hosts behind rv340 to be assigned ipaddresses in 10.150.150.x range from the dhcp-server running on Router1
- and once you have a 10.150.150.x ipaddress assigned to one of the Hosts, you can access the GUI of RV340 by accessing its ipaddress 10.150.150.2....becos both are in the same subnet
3. BUT as for vpn tunnel, obviously i could not configure a S2S tunnel on RV340 with wan-ipaddr of 10.150.150.2 and the local-subnet/network also as 10.150.150.x/24...this is not possible
So, i though of configuring a GRE-wIPsec Tunnel between RV340GW1 and RV340GW2 (which also had a similar bridged configuration).
Unfortunately due to the bridging applied, this GRE-wIPsec tunnel did not work. The outbound traffic between 10.150.150.x to 10.150.155.x was NOT getting routed via the established GRE-wIPsec tunnel....it was instead getting routed as plain traffic on the wan1/bridged interface...
4. So in summary, i believe your planned/expected network deployment will not work as far as VPN tunneling is concerned.
5. So there is one other scenario you could configure instead. Configure your network deployment (also as in attached document for s2s tunnel config)
a) The local-network behind RV340GW1/site1 can be 192.168.1.x/24 and
- enable dhcp-server on the RV340 vlan1 to assign ipaddress of 192.168.1.x to hosts
- you can also apply static-dhcp-mapping to ensure that each of the hosts is always assigned the same ipaddress in 192.168.1.x
b) The local-network behind RV340GW2/site2 can be 192.168.2.x/24 and
- enable dhcp-server on the RV340 vlan1 to assign ipaddress of 192.168.2.x to hosts
- you can also apply static-dhcp-mapping to ensure that each of the hosts is always assigned the same ipaddress in 192.168.2.x
c) Since your original idea was to get the same hosts behind RV340GW1 assigned with the ipddress-range 10.150.150.20 to 200 from Router1 dhcp-server, instead you could configure and apply a Static-NAT rule on RV340GW1 as below.
- It will do the needful of your original expectation. The internet traffic from say 192.168.1.20 will be Static-NATed to ipaddress 10.150.150.20 ...and so on. It will be NOT be NATed to 10.150.150.2 ipaddress of wan1 interface of RV340
On RV340GW1
----------
Static-NAT Rule-1:
Enable
Private IP Range Begin: 192.168.1.20
Public IP Range Begin: 10.150.150.20
Range Length: 50
Service: All Traffic
Interfaces: WAN1
Static-NAT Rule-2:
Enable
Private IP Range Begin: 192.168.1.72
Public IP Range Begin: 10.150.150.72
Range Length: 50
Service: All Traffic
Interfaces: WAN1
d) Since your original idea was to get the same hosts behind RV340GW2 assigned with the ipddress-range 10.150.155.20 to 200 from Router2 dhcp-server, instead you could configure and apply a Static-NAT rule on RV340GW2 as below.
- It will do the needful of your original expectation. The internet traffic from say 192.168.2.20 will be Static-NATed to ipaddress 10.150.155.20 ...and so on. It will be NOT be NATed to 10.150.155.2 ipaddress of wan1 interface of RV340
On RV340GW2
----------
Static-NAT Rule-1:
Enable
Private IP Range Begin: 192.168.2.20
Public IP Range Begin: 10.150.155.20
Range Length: 50
Service: All Traffic
Interfaces: WAN1
Static-NAT Rule-2:
Enable
Private IP Range Begin: 192.168.2.72
Public IP Range Begin: 10.150.155.72
Range Length: 50
Service: All Traffic
Interfaces: WAN1
6. Next, with the above configs in place, you can configure your site-to-site VPN tunnel between the 2 RV340s behind the routers as in attached document "S2S-tunnel-configs-On-BothRV340-GWs."
Ofcourse here hosts with ipaddresses 192.168.1.x will have to communicate with destination ipaddresses of 192.168.2.x and vice-versa...this you cannot avoid and I believe that this is the best you could do in your network deployment with RV340s
thanks & best regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-15-2021 11:43 PM
Wow, thank you very much for the detailed instructions, and the time you took to develop them! I will try it out as soon as I can, which will unfortunately not be before beginning of next week.
It's a pity that dhcp-relay does not work in our case. But I understand the restrictions better now and will try to find a solution along the lines of your solution.
Thanks again! I will let you know how it goes.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-21-2021 12:46 AM
Thanks to your help I was able to set up the basic networking with the two new VPN routers. Due to some restrictions I didn't tell you about, I changed some IP address ranges, but the basic setup is exactly as you suggested. Here is what it looks like now:
Both RV340s are now defined by the ISP-routers as "exposed host", so I don't have to use port/protocol forwarding. I also adjusted the definitions of the VPN-tunnel accordingly. Since we don't have public static IP addresses, I am using FQDN as remote endpoint (and using a DynDNS-service provided by the ISP-routers). So far, so good. However, the VPN tunnel remains "DOWN", so there must be an error somewhere. In the RV340 #1 I see an icon in the "Action" column for connecting the tunnel, but it remains down after clicking it. In the RV340 #2 I don't see that icon. I checked the configuration for both sides of the tunnel several times, they are exactly according to your specifications (with the mentioned changes). I enabled the logs, but apart from messages like "VPN-cfg: Bringing UP tunnel s2s_FluximSiteToSite ..." I don't see anything useful.
How can we find out what is going wrong?
Also, in your description you mentioned a Static NAT. I don't understand why it is necessary. I didn't implement it, and except for the VPN everything works flawlessly. Can you please explain the reason for the Static NAT?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-21-2021 04:00 AM
Hi
If i had thought it possible to use dyndns -based fqdn registrations, i would have definitely suggested the same. But in your topology-deployment, the dyndns will NOT solve your vpn tunneling issue.
- Iam assuming that you must have enabled "dyndns" client on each of the RV340s? on the RV340 wan interfaces?
- well what is happening here is that yes the dyndns-client on say for example RV340GW1 will work correctly - BUT it will be registering the WAN-ipaddress of RV340GW1 as 10.150.157.2....and the same is the case for RV340GW2, the dyndns-client will correctly work - BUT will register 10.150.155.2 as the wan-ipaddr of RV340GW2
- which is of no use with reference to making the vpn-tunnel config work in your given deployment, becos both 10.150.157.2/10.150.155.2 are "private-ipaddresses" and are NOT ROUTABLE ON INTERNET.
So to understand "Static-NAT or DNAT to be applied on ISP-Router2/ISP-Router1" you should try the below steps to answer some of the queries yourselves
1. Firstly, go to firewall-page of both RV340s and uncheck/disable "Block Wan Request", and apply and save.
- do not add or enable or disable anything else in firewall section. DO NOT ADD ANY PORT-FORWARD RULES, OR SOME ACL-RULES ETC ETC...
- PLEASE NOTE, FOR NOW THERE IS NOTHING TO BE ADDED IN FIREWALL SECTION ON BOTH RV340s -
a) till ISP-Router1 has applied/configured a static-nat/dnat rule to map a "PUBLIC-INTERNET-IPADDRESS" to the wan-ipaddress 10.150.157.2 of RV340GW1
b) and till ISP-Router2 has applied/configured a static-nat/dnat rule to map a "PUBLIC-INTERNET-IPADDRESS" to the wan-ipaddress 10.150.155.2 of RV340GW2
2. Next say you are on RV340GW1 and you want to ping to RV340GW2 wan-ipaddress (from the diagnostic page of RV340GW1)
- so the question you should ask is - I(meaning RV340GW1) am all the way across the Internet connected behind a ISP-Router1, so what will be the ipaddress of RV340GW2 to which i will send Pings????
Note: you should remember that RV340GW2 is also all the way across internet and connected behind another ISP-Rputer2 (meaning hidden behind ISP-Router2)
- You should remember that the ipaddress of RV340GW2-wan interface 10.150.155.2 is a private-ipaddress, and the ISP-Router1 will NOT FORWARD ANY PACKETS WITH DESTINATION-IPADDR IN or PRIVATE-ADDRESS SPACE
The RFC-1918 standard has defined the below subnets/ip-ranges as private-address space that anybody can use within the organization internal network and these ip-ranges/subnets ARE NOT ROUTABLE BY ANY & ALL INTERNET ROUTERS (read ISPs)
----------------
10.0.0.0/8
172.16.0.0/12
192.168.0.0/16
------------
3. So for you to reach/ping to wan-ipaddress of RV340GW2, the ISP-Router2 should apply/configure a static-nat/dnat rule to "map/bind" a single static "public-ipaddress" to the internal wan-ipaddress 10.150.155.2 of RV340GW2
- say for example the ISP-Router2 has alloted/mapped a public-ipaddress such as 200.200.200.201 to 10.150.155.2
- and once this static-nat/map/binding is done, THEN from RV340GW1 you will be sending pings TO 200.200.200.201, from which you will recieve a ping-reply, becos the ping when sent from RV340GW1 via the ISP-Router1 will get NATed to the public-ipaddress of ISP-Router1
4. Now the same is to be done in the reverse case of traffic sent from RV340GW2 to RV340GW1...in this case
the ISP-Router1 should apply/configure a static-nat/dnat rule to "map/bind" a single static "public-ipaddress" to the internal wan-ipaddress 10.150.157.2 of RV340GW1
- say for example the ISP-Router1 has alloted/mapped a public-ipaddress such as 100.100.100.201 to 10.150.157.2
5. So when you come down to configuring the vpn tunnel,
- on RV340GW1 S2S tunnel config, if you use a FQDN to identify the remote RV340GW2, it must be resolved to the "public-ipaddress" of RV340GW2-wan and NOT 10.150.155.2...and vice-versa on RV340GW2
- else if you should decide to use static-ipaddress, On RV340GW1 s2s tunnel config, you should be configuring the "Public-IPaddress" of RV340GW2-wan, instead of 10.150.155.2...and vice-versa on RV340GW2...
I hope you will now get why the static-nat/dnat mapping is required to be applied "on the isp-routers and NOT on RV340s"
Or, if my understanding is correct, i dont think any ISP-routers will allow any static-nat/dnat rules to be applied on their routers. Instead you should pay and apply to get alloted "Static-Public-Internet-IPaddresses" from both the ISPs to be assigned/configured on the WAN-interfaces of the RV340s...
- and only when you have the public-ipaddresses mapped in place, the VPN tunnel will come up successfully...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-21-2021 05:50 AM
Hi
Thanks for your reply. However, I think you might have misread my post. The DynDNS service is running on the ISP routers 1 and 2, and they know the actual public IP addresses. I am not running a DynDNS service on the RV340s. Since I am able to connect to the Web interfaces of both the ISP routers 1 and 2 and RV340s via the dynamic DNS addresses, I am certain this part is working fine. And, as I said, both RV340s are "exposed hosts" with respect to the ISP routers, so they receive all network traffic from the internet (except the port for the configuration of the ISP routers, which are > 15000). So I don't think a static NAT is necessary.
I followed your suggestion and disabled "Block WAN request" in both RV340s, but the status of the VPN tunnel remains "DOWN". I also followed your other suggestion and went to the Diagnostic page of both RV340s and tried to ping the respective other RV340 with the dynamic DNS address, and both were able to see the other.
Just to give it a try, I replaced the FQDN with the "Static IP" and entered the current public IP address on both ends, but the VPN tunnel still doesn't come up.
Is there another way to track down the problem of the VPN tunnel?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-21-2021 07:06 AM
Hi
>>>The DynDNS service is running on the ISP routers 1 and 2, and they know the actual public IP addresses.
Ok. Now this is more clear info
>>Since I am able to connect to the Web interfaces of both the ISP routers 1 and 2 and RV340s via the dynamic DNS addresses, I am >>>certain this part is working fine.
Correct. It sure is working fine if you are able to reach the RV340-GUI via the dyndns-addresses.
>>>I followed your suggestion and disabled "Block WAN request" in both RV340s, but the status of the VPN tunnel remains "DOWN".
No this was only to check reachability of RV340GWx-wan from the other RV340. This is not connected to vpn-tunnel status
>>>Just to give it a try, I replaced the FQDN with the "Static IP" and entered the current public IP address on both ends, but the VPN >>>tunnel still doesn't come up.
Ok. Now either when you use fqdn and/or static-ipaddress in the S2S-tunnel config "remote-endpoint", can you try with the attached updated config-docs here...now?
Please note: Use the given values in Local/Remote Identifier (type and value) exactly as given in attached doc...dont change it to something else. These are IDs used during the IKE-negotiation between the 2 RV340 peers
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: