- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
RV340 - L2TP
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-10-2017 02:27 AM
Hello,
anyone have experience with setting L2TP / IPSEC on RV340. According to the log after start it does not work at all.
- Labels:
-
Small Business Routers
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-07-2018 05:50 AM
I contacted Cisco support and they sent me the attached PDF which works for L2TP on RV340. A bit frustrating that the default IPSec Profile doesn't work. I'll suggest a firmware upgrade to set a default profile that works for L2TP or to add a L2TP profile alongside the default one. Hopefully they'll sort it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-07-2018 01:55 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-13-2018 11:35 AM - edited 06-13-2018 12:46 PM
Which version of anyconnect do you use ? (For those who sucessfully connected with)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-12-2018 07:35 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-13-2018 12:17 PM
Hi everybody,,
As anyone did the test from a windows 10 laptop.( the connection window in the pdf file is clearly from a older version of windows) ?
I configured my RV340W and the client side window' connections setting the exact same way (except for router ip and dns ) as in the document provided, upon connection test I still have this error message (see attached file).
My router is a RV340W but i don't think it should do a difference in configuration, unless it's firmware related ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-13-2018 12:19 PM - edited 06-13-2018 12:47 PM
And of course the user/password combination is ok, it's the same I'm using to log to the router webUI. :)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-13-2018 12:24 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-14-2018 05:23 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-15-2018 08:55 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-13-2018 12:27 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-14-2018 01:41 AM
Go to Control Panel (not settings) > Network and Internet > Network and Sharing Center > Change adapter settings > Right click the VPN connection and select properties.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-19-2019 09:05 AM
Ms. Calero and Mr. Raizada have both cited, and thankfully, provided the same-named PDF setup advice for RV340 as L2TP/IPSec server. To my amazement, they are not identical in content. The files are different, insofar as Ms. Calero's PDF is deleted for critical IPSec profile setup information on page 1 of the 4 page document. Thank you, Mr. Raizada, for providing this much needed, oh-so-hard to discover information; Windows clients are hard-coded for IPSec and nobody at Microsoft bothered to tell its customers how to set up a matching L2TP/IPSec server. Yes, this is infuriating.
I have re-posted Mr. Raizada's uploaded PDF with elaborate titling. Have mercy on your customers, Cisco and Microsoft! Pity the uninitiated, the struggling, the faithful drawn to Cisco's good name.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-22-2019 07:48 AM
Please reupload this fike it dont work now
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
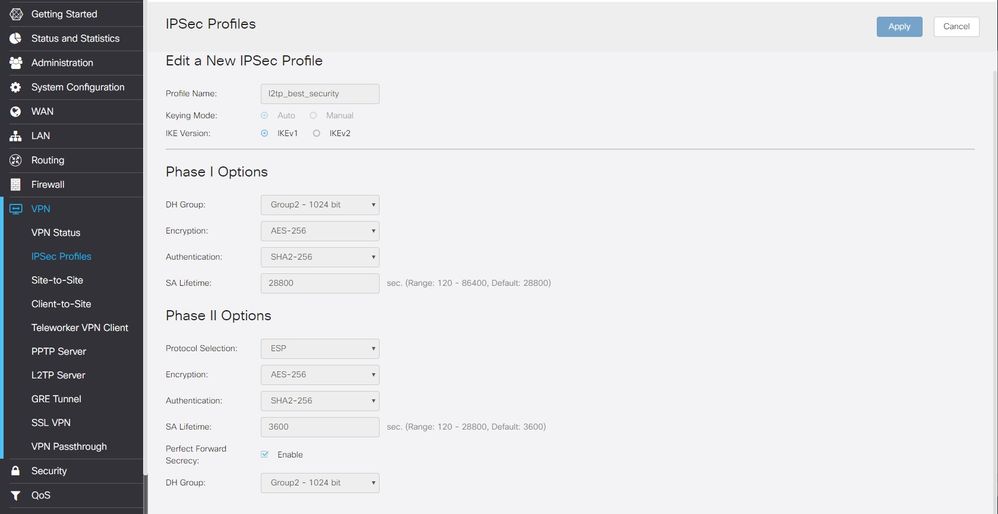
05-14-2019 04:15 AM - edited 06-24-2019 06:40 AM
It is possible to adapt this config to use AES encryption instead of 3DES. (in Windows 10 at least)
Here is a picture of my ipsec settings.
Then you need to run the following in Power Shell on the windows 10 machine.
Set-VpnConnectionIPsecConfiguration -ConnectionName "test" -AuthenticationTransformConstants SHA256128 -CipherTransformConstants AES256 -EncryptionMethod AES256 -IntegrityCheckMethod SHA256 -PfsGroup PFS2 -DHGroup Group2 -PassThru -Force
-ConnectionName is the name of the VPN connection I used test here.
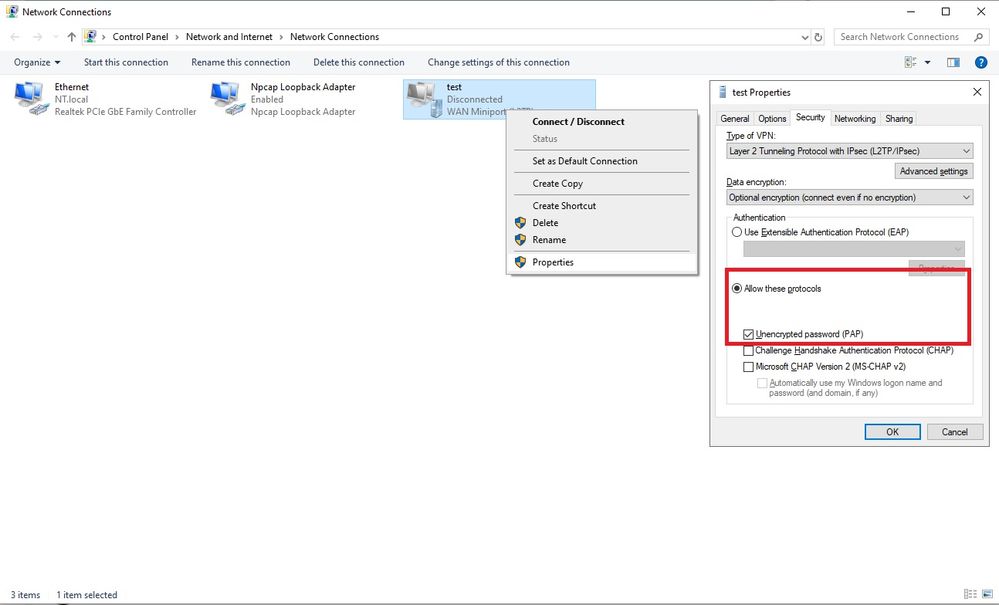
The rest is the same as in the pdf provided earlier in the thread. Ie need to use PAP.
Edit: Added a picture that shows the PAP authentication setting for the VPN connection.
With this the weakest point is the DH/PFS group.
Unfortunately Windows 10 doesn't support Group 5 so we are stuck with using group 2.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-14-2019 07:00 PM
Have you tried this? Is it working?
I have a similar setup which is working. Except it's SHA1 authentication for both phase 1 and phase 2. A Cisco Support Engineer helped me set it up.
I am trying to harden the settings some more. It shows ikev2, but when I select that it does not show up for the L2TP Server selection of the IPSec Profile.
I have managed to repeat the settings for AES256-SHA1 working with the L2TP Server though.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: