- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
RV340 - L2TP
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-10-2017 02:27 AM
Hello,
anyone have experience with setting L2TP / IPSEC on RV340. According to the log after start it does not work at all.
- Labels:
-
Small Business Routers
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-15-2019 05:34 AM
It's live and running at this moment, so yes it's working.
This was the most secure/hardened configuration that I found that worked.
If you have gotten AES-256 to work I guess I will give that a try as well.
Unfortunately the rv340 doesn't seem to support ikev2 for l2tp tunnels since any profile with ikev2 doesn't show up as an option in the l2tp settings as you noted.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-15-2019 10:50 AM
I cannot get L2TP to work with the latest Firmware (1.0.03.15). Prior versions I had no issues following instructions in this thread. Has anyone gotten this to work with the most recent Firmware?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-15-2019 06:37 PM
What was your original settings for the L2TP Ipsec VPVN before you upgraded the firmware?
I had it set on a previous parameter, not the one shown by Mathias Garcia, but prior to that. The settings I had worked when I upgraded the firmware, but Mathias Garcia is more secure if you can do it the way he mentioned. Only thing is the additional step of adding the Power shell script which I have not tried yet.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-16-2019 07:15 AM
I would really appreciate your help.
Just wondering why the need to input all this information in PowerShell?
I have several clients, so I am guessing that I will need to enter these Powershell parameters for each computer which I want to connect from.
Do you know if this conflicts with different setups? For example, I have one computer which is setup for several connections. At the present moment I connect to several CISCO RV340s at different sites.
I am most interested in hardening my security to atleast use SHA256 and the Perfect Forward Secrecy which doesn't work at the present moment for me without the power shell script.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-17-2019 04:14 AM
The reason for the Power Shell commands is to make Windows use the same settings for IPsec as we have configured on the cisco device (RV340).
It seems that Windows 10 uses 3DES by default for l2tp tunnel, or at least it doesn't try AES-128 or AES-256 without it being specifically set via commando.
Since these commands entered via Power Shell are limited in scope for a particular vpn connection there should not be any possibility for conflicts.
If you need to get this to work for many computers you should be able to make this change via a GPO.
But I would suggest that you turn to windows/ms support for that, my windows skills are somewhat lacking these days.
As a sidenote I can confirm that aes-256 does work, I just tried it.
Not sure how I missed this when I was trying to come up with a working solution.
-CipherTransformConstants AES256 -EncryptionMethod AES256
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-29-2020 09:59 AM
Windows 10, in a default state without command line modifications, will use AES-128 for L2TP IPsec with no issues. I have converted a half dozen or more sites from Cisco RV130/320/340 routers to Ubiquiti Edgerouters and even MikroTik routers with functioning versions of this style of VPN with no stability issues.
Either brand are much easier to cfg and manage after (albeit with CLI on the Edgerouter, then Config Tree after vs all GUI on the MikroTik) vs this product--which was the final straw for me. I used the RV models for years prior to them, and was fed up dealing with performance issues / artificial restrictions / bugs on these product lines. As a bonus, the skills on either brand are permanently useful as both have relatively universal cfg interfaces vs Cisco's "interface lottery" with every new RV series router.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-29-2020 11:19 AM
Please clarify/correct. L2TP is a Layer Two VPN, according to the OSI Seven Layer Model. IPSec operates in Layer Three. Your first sentence therefore doesn't make it clear what you're trying to do.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-06-2020 11:40 AM
Unless you're responding to someone else, this whole thread is about L2TP over IPSec VPN configuration. The other brands I mentioned are easy to configure and work fine with pure GUI configuration of Win10 client connections (no CLI mods or overrides) using this style of VPN...and the tunnel uses AES-128 in the default state.
Whatever the issue is, it is an issue with the default VPN protocol & authentication support of the Cisco firmware. They seem to be intentionally making it needlessly difficult, with no legitimate effort to resolve it after years of firmware development. Feeling a sense of achievement after working around this router platform's "engineered frustration" is like having "handled" a manipulator or bully--sure you did it, but the better approach is to cut that thing out of your life before it continues to perform endless variations on that theme at your expense. Although in this case, it's likely at your client's expense as well.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-27-2019 11:54 AM
Was lucky to find this post. We just purchased a RV345 Router and couldn't get any of the Windows 10 VPN client services to work. We had a RV325 which we hand no problem doing PPTP for VPN. Not so with the RV345.
Followed your example and it worked like a champ for L2TP using of all things PAP authentication protocol.
Thanks for the post.
Keven
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-18-2019 06:18 PM
Hi all,
Have you managed to run the VPN RV340 with firmware 1.0.03.16.
I have a connection error that failed because of the security layer
Powershell Script :
Set-VpnConnectionIPsecConfiguration -ConnectionName "test" -AuthenticationTransformConstants SHA256128 -CipherTransformConstants AES256 -EncryptionMethod AES256 -IntegrityCheckMethod SHA256 -PfsGroup PFS2 -DHGroup Group2 -PassThru -Force
IPsec Profiles:
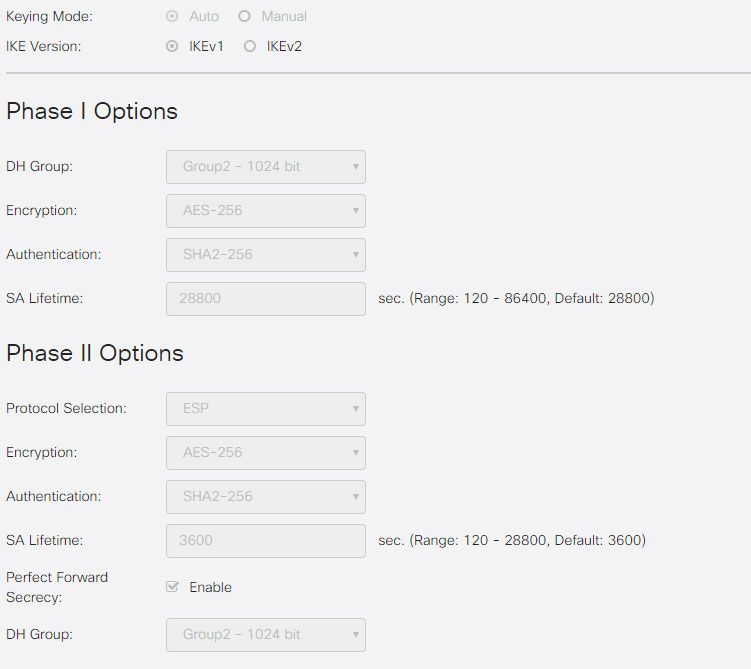
Thank a lot.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-20-2021 09:46 AM
This Post have bas been quite helpful, however, I encountered that the original manuals in this post don't seem to work for the RV345. It's like the 'default' IPSEC policy for VPN on Windows 10 does not work with the 3DES/SHA1/DH Group 2 settings* in the IPSEC profile of the router. I can't figure out what the default Windows 10 IPSEC policy for VPN is exactly, or rule out there is some bug somewhere, so instead I wrote a new manual for how to use an RV345 router with Windows 10 using L2TP, including the necessary Powershell commands. Perhaps its useful to somebody.
*If you configure the matching parameters in Powershell, it then works.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-03-2022 09:23 AM
Hi Matt,
I´m trying quite some time to get this up an running - have 5 sites with RV340 an need to migrate the last one ( where we have the older RV320, which is as well the PPTP server for the Windows clients) As I´m not able to set any kind of VPN for the Win10 machines I´m not able to get a rid of this old one..
Can you please share if there is need to create any ACL rule or any other related settings?
Thanks jakub
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-06-2022 12:47 PM
Hi ,
My name is Nikola Butlev and I'm L1 Cisco Engineer.
Have you already created IPSEC profile?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-30-2019 02:24 PM
Hello everyone. I recently purchased RV345 VPN Router I am trying to utilize L2TP Server on the appliance to connect with Windows Build in L2TP VPN Client. My issue is I cant connect more than one L2TP VPN Client connection from the same external network. Does L2TP protocol has some kind of limitation or its a RV345 issue
Best Regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-09-2019 05:14 PM
Also wondering how secure the Unencrypted PAP authentication is?
I dealt with a couple CISCO Support techs. The one who helped me setup an RV340 for L2TP over IPSEC for Windows said that the unencrypted PAP authentication was passed through a secure IPSEC. Another encouraged just using IPSEC like Shrew Soft because they did not want to trust the unencrypted PAP. However, when asked, that tech did defer to the first tech saying that they were much more knowledgeable and should know what they were talking about.
That's my main concern with the VPN with the RV340.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: