- Cisco Community
- Technology and Support
- Small Business Support Community
- Routers - Small Business
- Re: RV340 Router Security Risk or Intrusion?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
RV340 Router Security Risk or Intrusion?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-21-2020 08:35 PM
Hello,
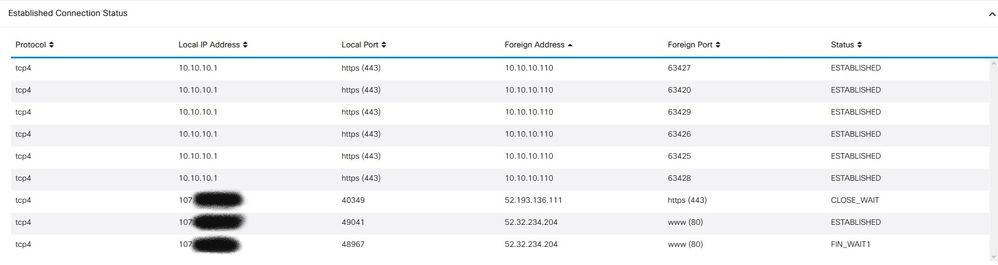
Can anyone explain why there are remote IP addresses with established connections to my ISP IP address on the WAN port?
The IPs in the pic below in the 52 range are in Japan and connected to the IP from my ISP on my RV340 router WAN port.
This is suspicious, and I'm not confident . How to resolve this?
The GUI screen shot below is in the path:
Admin UI - Status and Statistics - TCP/IP Services - Established Connection Status
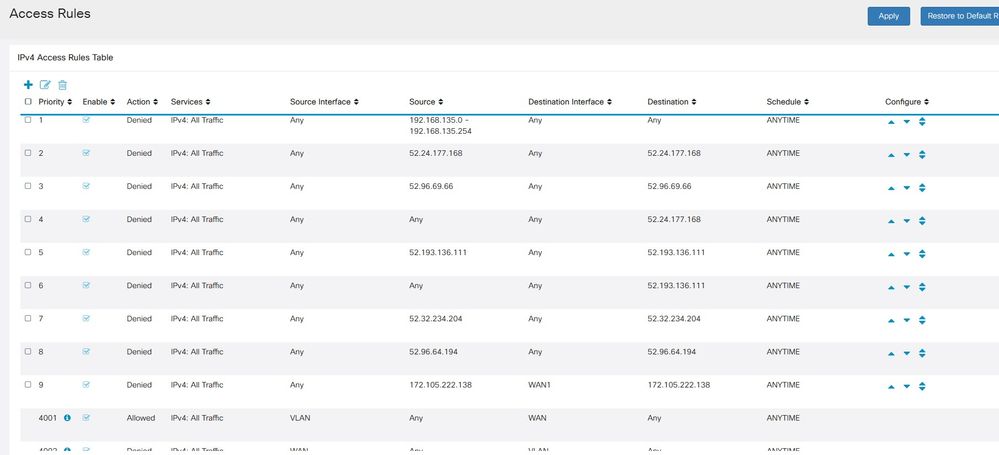
I have attempted to block these IPs with a rule to deny all access on any Source, Destination and any Interface in:
Admin UI - Firewall - Access Rules - IPv4 Access Rules Table
From my tests, that function in the router seems to have no effect on network traffic. It does not block access to that remote IP.
Any suggestions?
- Labels:
-
Device Admin
-
Threat Containment
-
Wired
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-22-2020 01:36 PM
what region you are ? are you from JP region ?
the IP belong to Amzon AWS Cloud, is 107 IP from your ISP ?
As i remember this brightcloud IP the one try to connect from your network for some secure update ( need to check)
your rule should be :
if above rules already allowed 1-5 then 6 rule is redundant, so post all 6 rules to understand better.
to make rule collectly to capture if you like to block 52.32.234.204
Denied--IPv4-Traffic------WAN/LAN-----Any----WAN--52.32.234.204- Any time
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-22-2020 03:21 PM - edited 05-22-2020 03:25 PM
Thank you very much for your reply.
I am in U.S. not Japan. Yes ISP provides 107.xxx.xxx.xxx
There should be no updates from brightcloud IPs in JP region. I have no indication there should be any open connection to JP region IP addresses.
I have tried to separate the rules in the table - see rule 5 and 6 below. That has no effect that i can tell.
Denying any source or destination interface for an IP or range seems like the solution.
Would this rule be most effective at blocking access?
Denied -- IPv4: All Traffic -- Any -- 52.32.234.204 -- Any -- 52.32.234.204 -- ANYTIME
With your suggested rule, would that only block outgoing traffic to the IP 52.32.234.204 ??
And mainly, why would there be any open connection from a random IP to my ISP WAN address?
All traffic routes through ISP address of course, however, then the -- Status and Statistics -- TCP/IP Services - Established Connection Status -- would show all connections through NAT to the LAN. That only shows seven connections at most.
The documentation from Cisco is very lacking about the expected behavior of many functions in the Admin UX.
Access Rules screenshot below:
Thanks again for any suggestion.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-22-2020 03:36 PM - edited 05-22-2020 03:38 PM
With your suggested rule, would that only block outgoing traffic to the IP 52.32.234.204 ??
BB - you can add as many rules, if you see any suspcious like this.
I also like to see any LAN Side device compromised and sending traffic also, another way to Look.
I have seen the documentaion - Webfilter uses the brightcloud.
for now it is going to contact port 80 and 443, we can not guess what is this related, as per the IP concern, it related to brighcloud. do you have any webfilter enabled.
I do see some firesight other firepower product use below URL :
database.brightcloud.com
service.brightcloud.com
below guide for reference :
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-22-2020 04:41 PM
Hi,
Thanks again.
I have no evidence of compromised LAN side devices.
I do not use webfilter function.
I have no access to firesight product.
There should be no connection to JP region IPs
There should be no connections on the ISP IP.
I do fault very poor documentation.
What is the expected behavior of the router for that function - Status and Statistics - TCP/IP Services - Established Connection Status - ??
What is the expected behavior for the access control rules?
Your suggestion may be valid, but how much experimentation must I do?
How do I validate that anyway?
Why the H is the router admin not documented?
All the documentation does is repeat what is already in the Admin UI.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-23-2020 12:17 AM
So Many Quesion i can not answer. Bur few i can.
1. The Device com with advanced security Features WebFilter - so it required conmstant database update from the clod to protect your network (latest name called Zero Trust - and many other names)- this means you have upto date DB from Cisco.
2. I have given firesight example, to understand why brightcloud involved to know - you do not need to spend much time on that.
3. Today trends are different, the more devices expose to internet have high risk, So your FW need to monitor and tune as per the requirement,
Hope this make sense ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-23-2020 04:43 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-24-2020 03:14 AM
I have provided the information based on the input you have given and provided in the post screenshot, this is pure your environment and controlled by your network admin (or you).
This is information based on the destination IP you were investigating the suspecting.52.32.234.204
This may be wrong on other side your point of view, i would suggest here to contact Cisco TAC and confirm by providing that IP address,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-24-2020 11:36 AM - edited 05-24-2020 11:39 AM
You still don't understand the issue. There are several foreign IP addresses connected directly to the WAN IP. Packet traces show absolutely no LAN side connection to those foreign IPs. Sorry, you have provided no meaningful or helpful information.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-24-2020 01:07 PM
"You still don't understand the issue" - As per the orginal post you were onlyconcerned about the IP you provided.
Now you have mentioned in the last post "There are several foreign IP addresses connected directly to the WAN IP"
This not make any sense for me, since you have not provide enough evidence that what IP address those are.
I am sure some this not right here for sure, you may have attacks on WAN IP, but no evidence.
I will Hold my fire to assits here, since i do not have visibility, wait for further input from you or some other can assits who can understand your issue better.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: