- Cisco Community
- Technology and Support
- Small Business Support Community
- Routers - Small Business
- VPN on RV042G not working and crashing
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
VPN on RV042G not working and crashing
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-31-2013 03:46 AM
I have tried every possible combination and solution for creating a Client to Gateway Group VPN to my RV042G even with quickvpn and shrew vpn .
There is no in between firewall between the 2 connection points . My latest config for the RV042G is
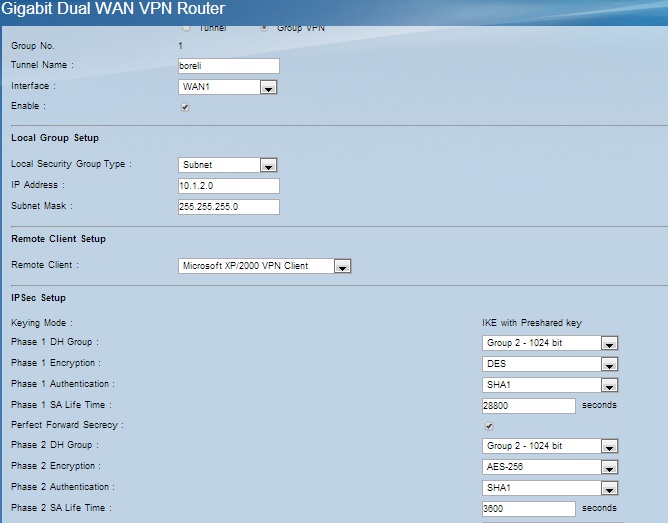
The config for the phase1 and phase2 for the Shrew client is exactly the same , and the preshared key and tunnel name properly configured . Even Tried it with FQDN .
The log file of the cisco is :
| packet from 79.131.159.79:500: ignoring Vendor ID payload [XAUTH] | ||
| Oct 31 11:49:17 2013 | VPN Log | packet from 79.131.159.79:500: ignoring Vendor ID payload [XAUTH] |
| Oct 31 11:49:17 2013 | VPN Log | packet from 79.131.159.79:500: received Vendor ID payload [draft-ietf-ipsec-nat-t-ike-00] |
| Oct 31 11:49:17 2013 | VPN Log | packet from 79.131.159.79:500: received Vendor ID payload [draft-ietf-ipsec-nat-t-ike-00] |
| Oct 31 11:49:17 2013 | VPN Log | packet from 79.131.159.79:500: ignoring Vendor ID payload [16f6ca16e4a4066d83821a0f0aeaa862] |
| Oct 31 11:49:17 2013 | VPN Log | packet from 79.131.159.79:500: ignoring Vendor ID payload [16f6ca16e4a4066d83821a0f0aeaa862] |
| Oct 31 11:49:17 2013 | VPN Log | packet from 79.131.159.79:500: received Vendor ID payload [draft-ietf-ipsec-nat-t-ike-02_n] |
| Oct 31 11:49:17 2013 | VPN Log | packet from 79.131.159.79:500: received Vendor ID payload [draft-ietf-ipsec-nat-t-ike-02_n] |
| Oct 31 11:49:17 2013 | VPN Log | packet from 79.131.159.79:500: received Vendor ID payload [draft-ietf-ipsec-nat-t-ike-03] |
| Oct 31 11:49:17 2013 | VPN Log | packet from 79.131.159.79:500: received Vendor ID payload [draft-ietf-ipsec-nat-t-ike-03] |
| Oct 31 11:49:17 2013 | VPN Log | packet from 79.131.159.79:500: received Vendor ID payload [RFC 3947] |
| Oct 31 11:49:17 2013 | VPN Log | packet from 79.131.159.79:500: received Vendor ID payload [RFC 3947] |
| Oct 31 11:49:17 2013 | VPN Log | packet from 79.131.159.79:500: received Vendor ID payload [Dead Peer Detection] |
| Oct 31 11:49:17 2013 | VPN Log | packet from 79.131.159.79:500: received Vendor ID payload [Dead Peer Detection] |
| Oct 31 11:49:17 2013 | VPN Log | packet from 79.131.159.79:500: ignoring Vendor ID payload [3b9031dce4fcf88b489a923963dd0c49] |
| Oct 31 11:49:17 2013 | VPN Log | packet from 79.131.159.79:500: ignoring Vendor ID payload [3b9031dce4fcf88b489a923963dd0c49] |
| Oct 31 11:49:17 2013 | VPN Log | packet from 79.131.159.79:500: ignoring Vendor ID payload [f14b94b7bff1fef02773b8c49feded26] |
| Oct 31 11:49:17 2013 | VPN Log | packet from 79.131.159.79:500: ignoring Vendor ID payload [f14b94b7bff1fef02773b8c49feded26] |
| Oct 31 11:49:17 2013 | VPN Log | packet from 79.131.159.79:500: ignoring Vendor ID payload [166f932d55eb64d8e4df4fd37e2313f0d0fd8451] |
| Oct 31 11:49:17 2013 | VPN Log | packet from 79.131.159.79:500: ignoring Vendor ID payload [166f932d55eb64d8e4df4fd37e2313f0d0fd8451] |
| Oct 31 11:49:17 2013 | VPN Log | packet from 79.131.159.79:500: ignoring Vendor ID payload [8404adf9cda05760b2ca292e4bff537b] |
| Oct 31 11:49:17 2013 | VPN Log | packet from 79.131.159.79:500: ignoring Vendor ID payload [8404adf9cda05760b2ca292e4bff537b] |
| Oct 31 11:49:17 2013 | VPN Log | packet from 79.131.159.79:500: ignoring Vendor ID payload [Cisco-Unity] |
| Oct 31 11:49:17 2013 | VPN Log | packet from 79.131.159.79:500: ignoring Vendor ID payload [Cisco-Unity] |
| Oct 31 11:49:17 2013 | VPN Log | packet from 79.131.159.79:500: [Tunnel Negotiation Info] <<< Responder Received Aggressive Mode 1st packet |
| Oct 31 11:49:17 2013 | VPN Log | packet from 79.131.159.79:500: [Tunnel Negotiation Info] <<< Responder Received Aggressive Mode 1st packet |
The log of the IKE service on Shrew VPN is :
peer config add message
13/10/31 11:51:22 <A : proposal config message
13/10/31 11:51:22 <A : proposal config message
13/10/31 11:51:22 <A : client config message
13/10/31 11:51:22 <A : xauth username message
13/10/31 11:51:22 <A : xauth password message
13/10/31 11:51:22 <A : local id 'akis.local' message
13/10/31 11:51:22 <A : preshared key message
13/10/31 11:51:22 <A : remote resource message
13/10/31 11:51:22 <A : peer tunnel enable message
13/10/31 11:51:22 ii : local supports XAUTH
13/10/31 11:51:22 ii : local supports nat-t ( draft v00 )
13/10/31 11:51:22 ii : local supports nat-t ( draft v01 )
13/10/31 11:51:22 ii : local supports nat-t ( draft v02 )
13/10/31 11:51:22 ii : local supports nat-t ( draft v03 )
13/10/31 11:51:22 ii : local supports nat-t ( rfc )
13/10/31 11:51:22 ii : local supports DPDv1
13/10/31 11:51:22 ii : local is SHREW SOFT compatible
13/10/31 11:51:22 ii : local is NETSCREEN compatible
13/10/31 11:51:22 ii : local is SIDEWINDER compatible
13/10/31 11:51:22 ii : local is CISCO UNITY compatible
13/10/31 11:51:22 >= : cookies 4f157ff4e4e793b6:0000000000000000
13/10/31 11:51:22 >= : message 00000000
13/10/31 11:51:27 -> : resend 1 phase1 packet(s) [0/2] 192.168.1.153:500 -> XXXXXXX:500
13/10/31 11:51:32 -> : resend 1 phase1 packet(s) [1/2] 192.168.1.153:500 -> XXXXXXX:500
13/10/31 11:51:37 -> : resend 1 phase1 packet(s) [2/2] 192.168.1.153:500 -> XXXXXXX:500
13/10/31 11:51:42 ii : resend limit exceeded for phase1 exchange
After every attempt either the tunnel or the vpn daemon on the cisco collapses and cannot even connect to it .
This matter is driving me crazy , any help would be much appreciated .
Connect machine windows 7 64bit , icmp ports allowed through firewall and shrew vpn application allowed .
Thank you in advance .
- Labels:
-
Small Business Routers
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide