- Cisco Community
- Technology and Support
- Small Business Support Community
- Switches - Small Business
- Thank you Sir, that's very
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-08-2016 07:33 AM
Hi Forum,
I was wondering if anyone would be so kind as to give me some pointers on my home Cisco setup. To give you some background, I have a fairly large house and a lot of kit, both wired and wireless. I have Cat6 cable from the hallway (ISP entry point) to SG300 in my lab upstairs, as well as to the living room. The centre of my setup will focus on my homelab which runs ESXi6 (three hosts each with 5 NICS). I have attached my draft design, please excuse the quality - I have put this together in mspaint in 10 minutes :)
I have already purchased my networking equipment, comprising of:
1 x SG300-28
1 x SG300-10
1 x SG300-10 with POE
1 x Watchguard Firebox T10 (3 ports (0,1,2)
2 x Apple Airport Extreme 802.11ac
Various sizes of Cat6 patch cables
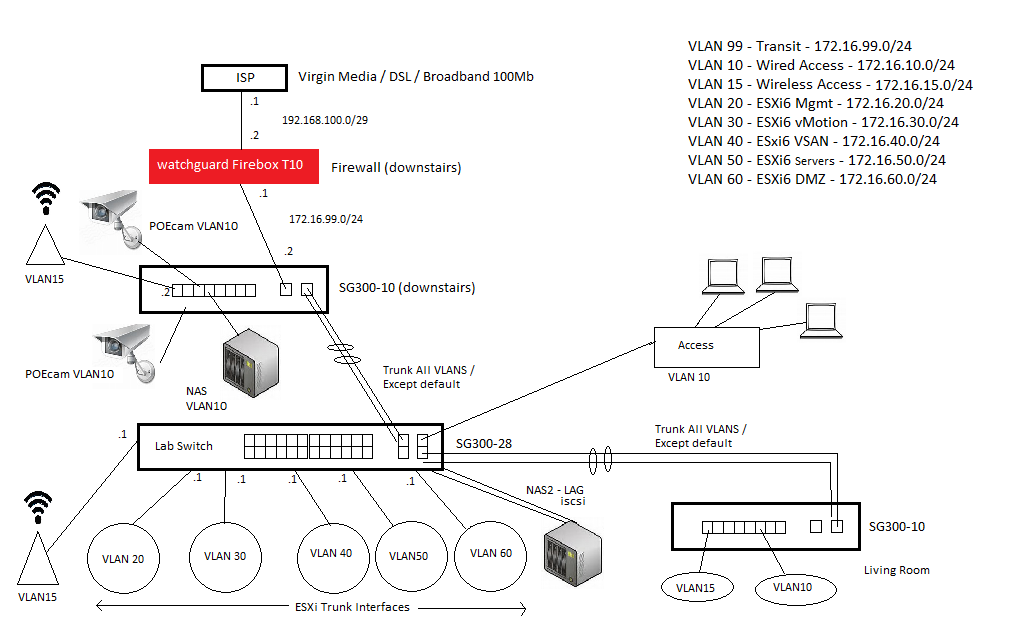
My requirements are that hosts on any VLAN can communicate with any host on another VLAN, examples
- I can remote desktop to any of my VM's running on ESXi from an iPad, laptop or workstation
- Outbound internet access from anywhere (unless I decide to lockdown the servers in ESXi to go via DMZ)
- Can look at security camera footage or live feeds from any location (internally or externally)
- obviously I may decide to lock down the DMZ etc.
- can manage the network (switches/ vCenter from anywhere internally)
- external management can be done by VPN connection using the Firebox.
OK, so my questions...... or any other advice you think is relevant.
1. I have already placed the SG300-28 into L3 mode, should I place both the SG300-10 units into L3 mode also? Or should I leave those in L2 mode, as long as all VLAN's can communicate (both ways) I am happy to leave the 10 port units in L2 mode, but I suspect If routes are needed they will need to be L3, correct?
2. what is the best way to link SG300-10P >>> SG300-28 >>>> SG300-10P. I have enough ports to be able to create an aggregation of 2 ports from each switch. I presume I need to trunk these and allow all VLANS across also, on both sides.
3. I presume there is no advantage to using the GBIC slots as my distances are relatively short (<50m) (as the SG300 range it's either you use the last 1Gb ports or the GBIC / not both )
4. I planned to put the security cameras (powered by POE) on the Wired VLAN (VLAN10). However, as these are constantly recording I was thinking of putting the security cameras on their own VLAN? My only concern is this NAS on VLAN10 is also used to server DLNA media to the house in the living room and bedroom (VLAN10).
Any other tips/ advice you can give on this setup would be greatly appreciated.
Many thanks.
Hef
Solved! Go to Solution.
- Labels:
-
Small Business Switches
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-09-2016 08:26 AM
Yes, that is correct as long as you create the same VLANs on all the switches and include them on the trunk links between switches.
devices in the same VLAN will be able to communicate. For inter-vlan routing they will need to route through a L3 device- either your core switch in L3 mode or your firewall. In either case you will need to assign ip addresses to the vlan interfaces and use those as the default gateways to allow routing between vlans. Then, if you choose to block communication between some vlans you would use ACL's on the switch or rules on the firewall.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-08-2016 03:54 PM
Nice MS Paint work :)
My first advice is run the global command 'macro auto disabled' on all the switches first. It will save you headaches later.
1. You normally only need your core switch in L3 (if even that). It is a choice, but for your small setup I don't see why you need to do routing on your edge switches. You could leave them all L2 and just route through your firewall too. Again, just a choice.
2. Yes, just a trunk port allowing VLANs you want (or all)
3. Agreed. You would normally need the for fiber if exceeding 100m
4. Yes I would put cameras on separate VLAN. Now you have an application where L3 routing on your core may be preferable to through your firewall because the switches should be able to route faster and you should not need to apply security policies between camera VLAN and the NAS.
Good luck and have fun with all that.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-08-2016 11:22 PM
Thank you Sir, that's very helpful indeed.
Just one one more question :)
If I leave the edge switches SG300's in L2 mode - I presume I will still be able to communicate with machines on all vlans, because the switch will either know about directly connected vlans or will have a static route to one. Ie, vlan 10 will be available on all switches and all machines in vlan 10 will be able to communicate .....
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-09-2016 08:26 AM
Yes, that is correct as long as you create the same VLANs on all the switches and include them on the trunk links between switches.
devices in the same VLAN will be able to communicate. For inter-vlan routing they will need to route through a L3 device- either your core switch in L3 mode or your firewall. In either case you will need to assign ip addresses to the vlan interfaces and use those as the default gateways to allow routing between vlans. Then, if you choose to block communication between some vlans you would use ACL's on the switch or rules on the firewall.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-09-2016 11:31 AM
Thank you so much for your advice. Tonight I start building :)
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community:
Switch products supported in this community
Cisco Business Product Family
- CBS110
- CBS220
- CBS250
- CBS350
Cisco Switching Product Family
- 110
- 200
- 220
- 250
- 300
- 350
- 350X
- 550X