- Cisco Community
- Technology and Support
- Small Business Support Community
- Switches - Small Business
- Re: RADIUS supplied VLANs for SG250 switches
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-01-2020 02:14 PM
Hello
I recently purchased some SG250 switches (08's and 18's) and am trying to get 802.1x vlans served from a radius server
It appears that although these switches' manuals state that they can be configured to do so, I cannot see it in my configs.
Specifically, in the Sx250 Series Smart Switches Admin Guide, (2.2.5.x) under Port Host Modes on pages 309 - 310, it states:
"A user can specify that untagged traffic from the authorized host will be remapped to a
VLAN that is assigned by a RADIUS server during the authentication process. Tagged
traffic is dropped unless it belongs to the RADIUS-assigned VLAN or the
unauthenticated VLANs. Radius VLAN assignment on a port is set in the Port
Authentication page."
When I go to the Port Authentication page in my mgt console, I see no such option. In fact, this same admin guide's Port Authentication section on page 314 - 316 doesn't appear to document this option either.
Perhaps I've misunderstood this?
Thanks.
Solved! Go to Solution.
- Labels:
-
Small Business Switches
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-07-2020 05:51 AM
Just a followup for anyone interested / web search on this topic. I acquired replacement sg350 devices and radius-assigned vlans to access ports works, as does mac-auth.
I will be returning my sg250's. They perform radius auth, but vlan assignment to access ports uses the local device config.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-01-2020 02:24 PM
Not sure what is the firmware you using 1.0.0.18)
i do not have the device, but as per the SG220 model has featured as per the document :
https://www.cisco.com/assets/sol/sb/SG220_Emulators/SG220_Emulator_v1-0-0-18_20140626/home.html
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-01-2020 02:36 PM
Hi BB
my fw is 2.5.5.47 - the latest.
I'm looking at the emulator in your link and a Port Authentication page for a given port and cannot find an the option (same as my sg250).
thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-01-2020 02:44 PM
not sure 2.5.X is latest firmware, try downgrade to and test.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-01-2020 03:02 PM
I downgraded to the previous fw that came with the device : 2.5.0.83
It doesn't appear to have this option either.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-01-2020 03:13 PM - edited 09-01-2020 03:28 PM
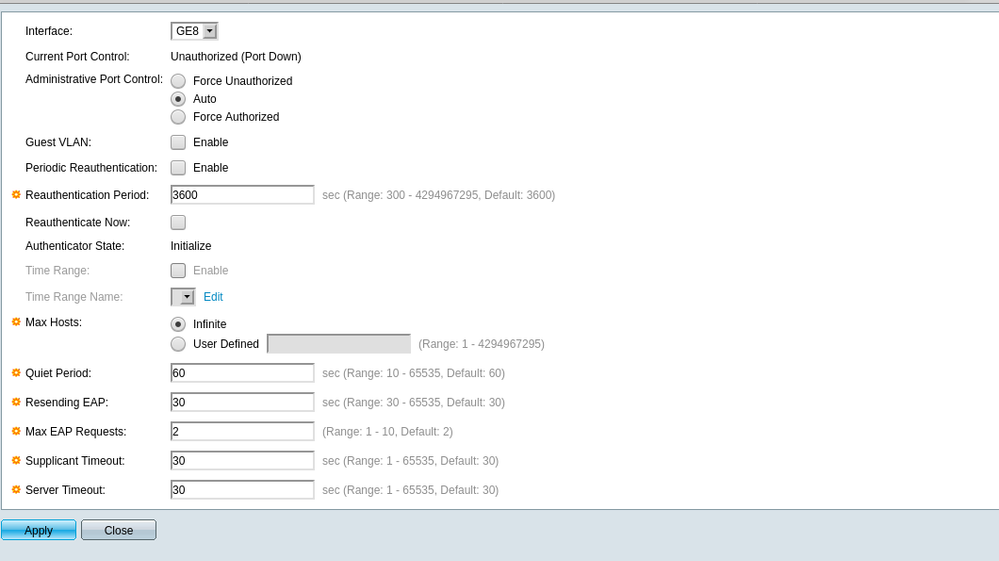
Port Authentication configuration is in Security > 802.1X Authentication (near the bottom, not RADIUS) > Port Authentication.
It's there in the linked emulator and covered on p. 363 of the most recent admin guide.
EDIT: Misread. I now see you're in the Port Authentication page but can't figure out how to configure the authorized VLAN? Is that the specific issue?
The untagged VLAN becomes the authorized VLAN once it authenticates to your RADIUS server. Whatever tagged VLANs might be configured on a given port (which port is also configured for authorization via 802.1X) will have all their traffic dropped until the port can authenticate via its untagged VLAN. I.e., if your Port VLAN Membership is configured correctly and you confirm a RADIUS authentication occurs, then the port should then be authorized and begin passing tagged traffic as well.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-01-2020 03:23 PM
Hi Cyberconsultants
i must be blind. I cannot see this in the emulator either. I am going to Security -> 802.1x Authenticate -> Port Authnetication, then selecting a Port and hitting Edit.
Show me where the RADIUS VLAN mapping setting is.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-01-2020 03:40 PM - edited 09-01-2020 03:40 PM
What do you mean by RADIUS VLAN mapping?
The 802.1X Port Authentication configuration will be carried out according to your VLAN Management > Port VLAN Memberships.
What VLAN is your RADIUS server on? Do you need hosts on other VLANs to authenticate to that RADIUS server? What specifically are you trying to do?
You've highlighted some text from a miscited version of a former admin guide. You were fine on the most recent firmware.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-01-2020 03:59 PM
As in my original message that started this thread - the admin manual states that
"A user can specify that untagged traffic from the authorized host will be remapped to a
VLAN that is assigned by a RADIUS server during the authentication process. Tagged
traffic is dropped unless it belongs to the RADIUS-assigned VLAN or the
unauthenticated VLANs. Radius VLAN assignment on a port is set in the Port
Authentication page."
I took this to mean that the RADIUS attributes, Tunnel-Type, Tunnel-Medium-Type and Tunnel-Private-Group-Id could be sent from the RADIUS server to the switch and would configure the port for the appropriate vlan. Perhaps I misunderstood what that paragraph from the manual means. To me it says very plainly "VLAN that is assigned by a radius server". The RAIDUS VLAN assignment on a port is set in the Port Authentication page".
This is the latest version of the admin guide I could find. If these devices aren't capable of assigning vlans from a radius reply, they should say so.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-01-2020 04:12 PM
Are you able to see exactly what's happening with/to the RADIUS attribute traffic?
You assume the switch is 'ignoring' that traffic because your config isn't working?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-01-2020 03:38 PM
Those are vlan memberships configured on the switch device. RADIUS does the auth but the switch ignores Tunnel-Type = VLAN,
Tunnel-Medium-Type = IEEE-802, Tunnel-Private-Group-Id = "11".
So I cannot map VLAN membership on the port via RADIUS like the manual states on pg 314-316?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-01-2020 03:50 PM - edited 09-01-2020 03:51 PM
Could you post one of your switch's configs?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-01-2020 04:15 PM - edited 09-01-2020 04:17 PM
Try modifying your Tunnel-Private-Group-Id attribute to "[tag], [string]"... as in "Tunnel-Private-Group-Id = [11, RemappedVLAN]" for example.
That string, up to 253 characters, is apparently used by IOS.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-01-2020 05:16 PM
This does not work either (Tunnel-Private-Group-Id = [11, RemappedVLAN]). I verified we are sending all the attributes to via wireshark.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-01-2020 05:34 PM - edited 09-01-2020 05:38 PM
I agree that language reads like at least the remapping should work. If a supplicant is able to authenticate to your RADIUS server, then the language reads like that supplicant's port's untagged VLAN should then be remapped by RADIUS assignment to VLAN 11 like you're trying (and verifying via capture).
Post up a switch config so I can follow along better.
Wouldn't be surprised if this SG line doesn't support RADIUS assignment beyond that initial remap either. Total speculation and not what you're asking at this point, but throwing that out there. It may also be that it supports 802.1X authentication but can 'remap' only to a tagged VLAN that's already configured and to which a port is already configured as a member on the switch.
Another softball—have you given all the relevant sections in the device's 'Help' manual a thorough read? I sometimes find interesting things in there I might've missed or that weren't covered in the admin guide. Personally not familiar with the Sx2xx lineup beyond what we've variously installed for clients.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community:
Switch products supported in this community
Cisco Business Product Family
- CBS110
- CBS220
- CBS250
- CBS350
Cisco Switching Product Family
- 110
- 200
- 220
- 250
- 300
- 350
- 350X
- 550X