- Cisco Community
- Technology and Support
- Small Business Support Community
- Switches - Small Business
- SG300 routing to VLAN
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-09-2018 03:20 PM
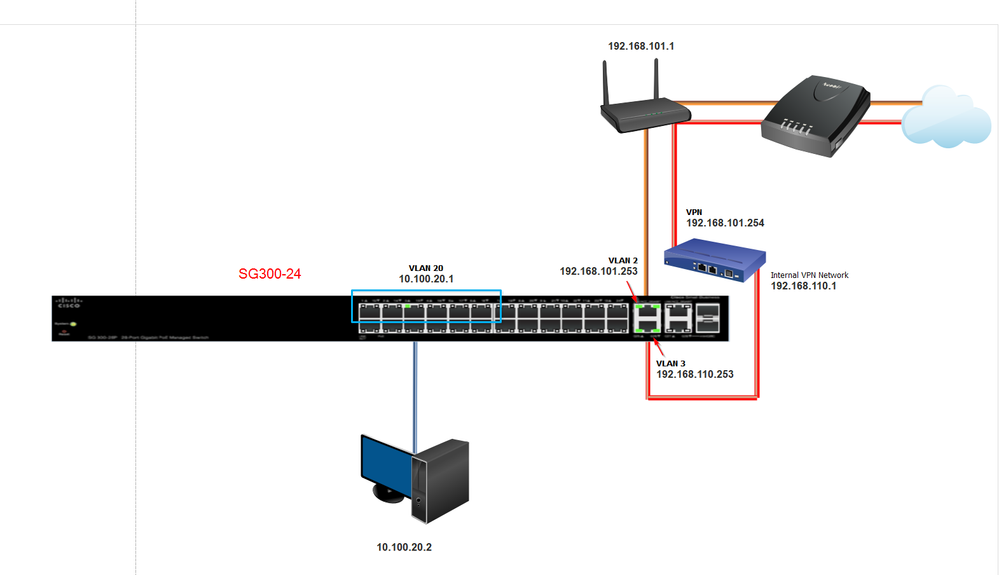
I need some assistance and guidance if all possible, I thank you in advance. First, this is my first switch setup and configuration. I have research and read what I thought would be enough and continue to search in the hopes I can complete this task.I have configures 3 VLANs
VLAN 2 – Internal Wireless (First connection to the internet from the cable company., Can’t really screw this up. This is a simple TP-Link wireless router with DD-WRT installed.
VLAN 3 – VPN (TP-Link TL-R600VPN router with an active VPN Connection)
VLAN20 – Internal VLAN (only one pc for testing)
From the console connection on the SG-300 I can ping all devices.
SW1#ping 192.168.101.253
Pinging 192.168.101.253 with 18 bytes of data:
18 bytes from 192.168.101.253: icmp_seq=1. time=0 ms
18 bytes from 192.168.101.253: icmp_seq=2. time=0 ms
18 bytes from 192.168.101.253: icmp_seq=3. time=0 ms
----192.168.101.253 PING Statistics----
4 packets transmitted, 4 packets received, 0% packet loss
round-trip (ms) min/avg/max = 0/0/0
SW1#ping 10.100.20.1
Pinging 10.100.20.1 with 18 bytes of data:
18 bytes from 10.100.20.1: icmp_seq=1. time=0 ms
18 bytes from 10.100.20.1: icmp_seq=2. time=0 ms
18 bytes from 10.100.20.1: icmp_seq=3. time=0 ms
18 bytes from 10.100.20.1: icmp_seq=4. time=0 ms
----10.100.20.1 PING Statistics----
4 packets transmitted, 4 packets received, 0% packet loss
round-trip (ms) min/avg/max = 0/0/0
SW1#ping 10.100.20.2
Pinging 10.100.20.2 with 18 bytes of data:
18 bytes from 10.100.20.2: icmp_seq=1. time=0 ms
18 bytes from 10.100.20.2: icmp_seq=2. time=0 ms
18 bytes from 10.100.20.2: icmp_seq=3. time=0 ms
18 bytes from 10.100.20.2: icmp_seq=4. time=0 ms
----10.100.20.2 PING Statistics----
4 packets transmitted, 4 packets received, 0% packet loss
round-trip (ms) min/avg/max = 0/0/0
SW1#ping 192.168.101.1
Pinging 192.168.101.1 with 18 bytes of data:
18 bytes from 192.168.101.1: icmp_seq=1. time=0 ms
18 bytes from 192.168.101.1: icmp_seq=2. time=0 ms
18 bytes from 192.168.101.1: icmp_seq=3. time=0 ms
18 bytes from 192.168.101.1: icmp_seq=4. time=0 ms
----192.168.101.1 PING Statistics----
4 packets transmitted, 4 packets received, 0% packet loss
round-trip (ms) min/avg/max = 0/0/0
And more importantly in can ping outside of the wireless router to the internet.
SW1#ping 1.1.1.1
Pinging 1.1.1.1 with 18 bytes of data:
18 bytes from 1.1.1.1: icmp_seq=1. time=0 ms
18 bytes from 1.1.1.1: icmp_seq=2. time=20 ms
18 bytes from 1.1.1.1: icmp_seq=3. time=0 ms
18 bytes from 1.1.1.1: icmp_seq=4. time=20 ms
----1.1.1.1 PING Statistics----
4 packets transmitted, 4 packets received, 0% packet loss
round-trip (ms) min/avg/max = 0/10/20
I have added the static route on the TP-Link Wireless router and can ping the work station on VLAN 20 (10.100.20.2)
BusyBox v1.28.0 (2018-02-12 05:35:08 CET) built-in shell (ash)
root@Router1:~# ping 192.168.101.253
PING 192.168.101.253 (192.168.101.253): 56 data bytes
64 bytes from 192.168.101.253: seq=0 ttl=64 time=7.825 ms
64 bytes from 192.168.101.253: seq=1 ttl=64 time=1.151 ms
64 bytes from 192.168.101.253: seq=2 ttl=64 time=1.111 ms
--- 192.168.101.253 ping statistics ---
5 packets transmitted, 5 packets received, 0% packet loss
round-trip min/avg/max = 1.111/2.483/7.825 ms
root@Router1:~# ping 10.100.20.1
PING 10.100.20.1 (10.100.20.1): 56 data bytes
64 bytes from 10.100.20.1: seq=0 ttl=64 time=1.358 ms
64 bytes from 10.100.20.1: seq=1 ttl=64 time=1.151 ms
64 bytes from 10.100.20.1: seq=2 ttl=64 time=1.116 ms
--- 10.100.20.1 ping statistics ---
8 packets transmitted, 8 packets received, 0% packet loss
round-trip min/avg/max = 1.116/1.171/1.358 ms
root@Router1:~# ping 10.100.20.2
PING 10.100.20.2 (10.100.20.2): 56 data bytes
64 bytes from 10.100.20.2: seq=0 ttl=127 time=0.947 ms
64 bytes from 10.100.20.2: seq=1 ttl=127 time=1.280 ms
64 bytes from 10.100.20.2: seq=2 ttl=127 time=0.900 ms
--- 10.100.20.2 ping statistics ---
6 packets transmitted, 6 packets received, 0% packet loss
round-trip min/avg/max = 0.699/0.933/1.280 ms
root@Router1:~#
Problem
The PC on the VLAN20 can ping up to the Wireless router (192.168.101.1) but not passed it. It cannot ping the internet.
Not sure what I have missed, any assistance is greatly appreciated. Once I have this figured out, I can proceed on the VPN side. I am attaching current running config and a diagram of how i have the items connect.
Running Configuration.
SW1#show running-config
config-file-header
SW1
v1.2.7.76 / R750_NIK_1_2_584_002
CLI v1.0
file SSD indicator encrypted
@
ssd-control-start
ssd config
ssd file passphrase control unrestricted
no ssd file integrity control
ssd-control-end cb0a3fdb1f3a1af4e4430033719968c0
!
vlan database
vlan 2-4,20
exit
voice vlan oui-table add 0001e3 Siemens_AG_phone________
voice vlan oui-table add 00036b Cisco_phone_____________
voice vlan oui-table add 00096e Avaya___________________
voice vlan oui-table add 000fe2 H3C_Aolynk______________
voice vlan oui-table add 0060b9 Philips_and_NEC_AG_phone
voice vlan oui-table add 00d01e Pingtel_phone___________
voice vlan oui-table add 00e075 Polycom/Veritel_phone___
voice vlan oui-table add 00e0bb 3Com_phone______________
ip dhcp information option
bonjour interface range vlan 1
hostname SW1
line console
exec-timeout 0
exit
!
interface vlan 1
ip address 10.100.10.254 255.255.255.0
no ip address dhcp
!
interface vlan 2
ip address 192.168.101.253 255.255.255.0
!
interface vlan 3
ip address 192.168.110.253 255.255.255.0
!
interface vlan 20
ip address 10.100.20.1 255.255.255.0
!
interface gigabitethernet1
switchport mode access
switchport access vlan 20
!
interface gigabitethernet2
switchport mode access
switchport access vlan 20
!
interface gigabitethernet3
switchport mode access
switchport access vlan 20
!
interface gigabitethernet4
switchport mode access
switchport access vlan 20
!
interface gigabitethernet5
switchport mode access
switchport access vlan 20
!
interface gigabitethernet25
switchport mode access
switchport access vlan 2
!
interface gigabitethernet26
switchport mode access
switchport access vlan 3
!
ip route 0.0.0.0 0.0.0.0 192.168.101.1
Solved! Go to Solution.
- Labels:
-
Small Business Switches
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-16-2018 10:02 AM
Update
The problem was that DD-WRT only routes the internet to its Internal NAT. I hope this helps some one in the future.
To allow routing to another subnet the firewall rule will need adjustment.
in my example, the following will route to one one subnet:
WAN_IF="$(route -n | awk '/^0.0.0.0/{wif=$NF} END {print wif}')"
iptables -t nat -I POSTROUTING -s 10.100.20.0/24 -o $WAN_IF -j MASQUERADE)
The Following will route to every 10.100.x.x.
WAN_IF="$(route -n | awk '/^0.0.0.0/{wif=$NF} END {print wif}')"
iptables -t nat -I POSTROUTING -s 10.100.0.0/16 -o $WAN_IF -j MASQUERADE
This will allow all routing -but considered bad practice.
WAN_IF="$(route -n | awk '/^0.0.0.0/{wif=$NF} END {print wif}')"
iptables -t nat -I POSTROUTING -o $WAN_IF -j MASQUERADE
If you go to Administration/Commands in DD-WRT and put the rule in a box and press "Save Firewall" it will be saved in nvram and survives a reboot (or if you already have rules in the Firewall box, press Edit).
Could not have done this with out the guys at DD-WRT https://forum.dd-wrt.com
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-12-2018 03:33 AM
Hi there,
Is the Wireless router performing NAT for VLAN20 ?
The issue you may be encountering is traffic from 10.100.20.0/24 is arriving at the ISP modem, but it does not know how to return the traffic and potentially its NAT rules do not permit any other subnets that 192.168.101.0/24 .
Assuming 192.168.101.0/24 is the default ‘inside’ subnet for the ISP modem, simply re-purpose VLAN2 on the wireless router and use it as a point to point link to the SG300. Configure this interface as NAT ‘inside’ interface and translate traffic as it passes through.
[SG300] < .2 --- VLAN2 (192.168.102.0/24) --- .1 > (NAT inside) [DD-WRT] (NAT outside) < .1 --- (192.168.101.0/24) --- .2> [ISP_MODEM]
The following routes will need to be configured:
DD-WRT:
ip route 10.100.20.0 255.255.255.0 192.168.102.2 ip route 10.100.110.0 255.255.255.0 192.168.102.2
SG300
ip route 0.0.0.0 0.0.0.0 192.168.102.1
cheers,
Seb.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-12-2018 06:28 PM
Seb, thank you for the assistance.
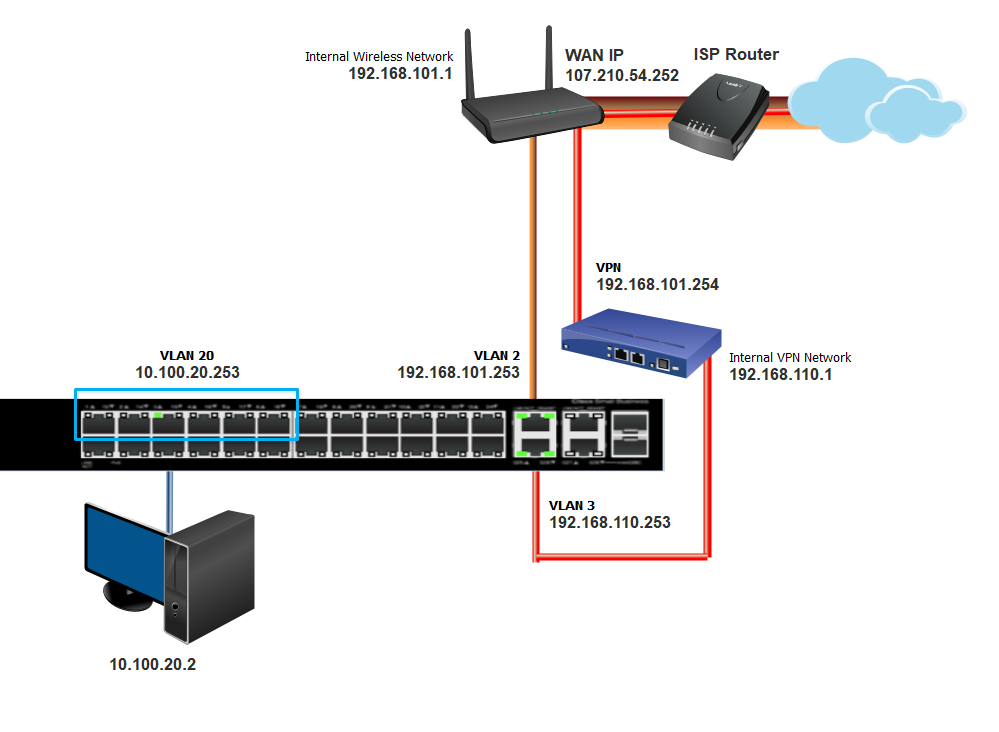
From the layout you have, it seems that the DDWRT and ISP_MODEM have the same network. the ISP_Modem device is inaccessible and all i can see the WAN IP issued to DDWRT (new diagram below) . The wireless router is only preforming NAT on 192.168.101.0 not VLAN20 .
As far as the wireless router is concerned it does not know that the IP address from 10.100.20.0 are coming from VLAN20
Should the logic you describe above continued to be taken into consideration even though the Router is NOT performing NAT for VLAN20?
Again, thank you for taking the time and the assistance.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-13-2018 02:24 AM
Ah OK, thanks for the update. The ISP router is functioning as a bridge (“modem” mode) which is how you are receiving the public WAN IP on the DD-WRT. It is safe to ignore my previous suggestion based on an incorrect assumption.
It seems that to get your VLAN20 devices to communicate with the internet all you need to it permit the subnets that are routed on the SG300 (10.100.20.0/24 and 192.168.110.0/24 if that is to be your VPN user pool and you require them to have internet access) in the NAT statement you have configured on the DD-WRT.
Cheers,
Seb.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-13-2018 07:14 PM
I already have a default route to the 10.100.20.0 network on the DDW-RT and from the DDW-RT i can ping the pc on VLAN20. not sure I follow how to proceed, would it be possible to clarify further?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-14-2018 12:59 AM
From your previous message:
"The wireless router is only preforming NAT on 192.168.101.0 not VLAN20 ."
I'm not sure what the DDW-RT NAT syntax looks like, but the VLAN subnet needs to be included in this. On a Cisco device this is typically achieved via an ACL listing permitted subnets which is listed in the NAT statement.
cheers,
Seb.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-15-2018 04:15 AM
Seb,
Thank you for the guidance, I will hunt down a solution for applying the VLAN Subnet to DDW-RT. I will re-post a solution once i have obtained it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-16-2018 10:02 AM
Update
The problem was that DD-WRT only routes the internet to its Internal NAT. I hope this helps some one in the future.
To allow routing to another subnet the firewall rule will need adjustment.
in my example, the following will route to one one subnet:
WAN_IF="$(route -n | awk '/^0.0.0.0/{wif=$NF} END {print wif}')"
iptables -t nat -I POSTROUTING -s 10.100.20.0/24 -o $WAN_IF -j MASQUERADE)
The Following will route to every 10.100.x.x.
WAN_IF="$(route -n | awk '/^0.0.0.0/{wif=$NF} END {print wif}')"
iptables -t nat -I POSTROUTING -s 10.100.0.0/16 -o $WAN_IF -j MASQUERADE
This will allow all routing -but considered bad practice.
WAN_IF="$(route -n | awk '/^0.0.0.0/{wif=$NF} END {print wif}')"
iptables -t nat -I POSTROUTING -o $WAN_IF -j MASQUERADE
If you go to Administration/Commands in DD-WRT and put the rule in a box and press "Save Firewall" it will be saved in nvram and survives a reboot (or if you already have rules in the Firewall box, press Edit).
Could not have done this with out the guys at DD-WRT https://forum.dd-wrt.com
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide