- Cisco Community
- Technology and Support
- Services
- Smart Services
- Smart Net Total Care
- SNTC Support
- CSPC encryption question
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-24-2021 12:04 PM
I have a customer whose security team is being alerted that 2.8.1.8 is running 1024 bit encryption instead of their recommended 2048. Is there a way to change this in CSPC? Or is 2.9.X using higher level?
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-31-2021 01:16 PM
Hi,
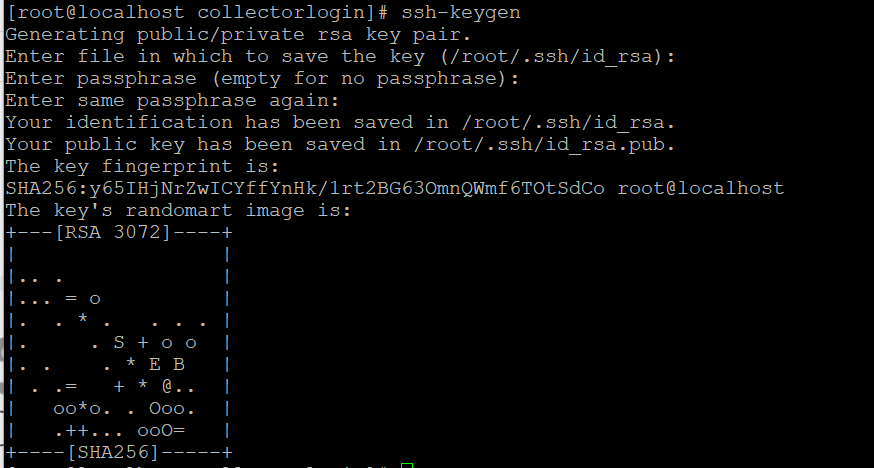
As informed in the Private message, I was testing in my Lab environment on this. This is not a vulnerability in CSPC but it is the vulnerability in OS level. Since CSPC 2.8 version run on CentOS 6, you are getting this alert.
However, it is resolved in CentOS 8. Hence you can upgrade the CSPC to the latest build 2.9.1.1. For your reference below is the screenshot where I have tested the same in my lab and it is using RSA 3072 key which is higher bit ssh key.
Thanks and Regards,
Madhusha R
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-25-2021 06:46 AM
Hi
We are looking into your post and we will get back to you with an update at the earliest.
Thanks and Regards,
Madhusha R
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-25-2021 08:11 AM
Hi,
Could you please share the screenshot of the alert that your team is getting over the Private Message?
Also, kindly elaborate your concern for further clarification.
Thanks and Regards,
Madhusha R
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-31-2021 01:16 PM
Hi,
As informed in the Private message, I was testing in my Lab environment on this. This is not a vulnerability in CSPC but it is the vulnerability in OS level. Since CSPC 2.8 version run on CentOS 6, you are getting this alert.
However, it is resolved in CentOS 8. Hence you can upgrade the CSPC to the latest build 2.9.1.1. For your reference below is the screenshot where I have tested the same in my lab and it is using RSA 3072 key which is higher bit ssh key.
Thanks and Regards,
Madhusha R
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide