- Cisco Community
- Technology and Support
- Services
- Smart Services
- Smart Net Total Care
- SNTC Support
- Re: HTTPs Transport Mode has failed peer not authenticated -
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
HTTPs Transport Mode has failed peer not authenticated -
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-12-2020 12:12 PM
Hi Cisco
I was trying to get my SNTC portal up and running,to start, i put one IP in my CSPC and got the IP in my managed devices (discovery went fine) then i ran the collection and that job also went well. after clicking on upload, I got the following message:
HTTPs Transport Mode has failed peer not authenticated -
CSPC version 2.8.1.4
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-12-2020 01:43 PM
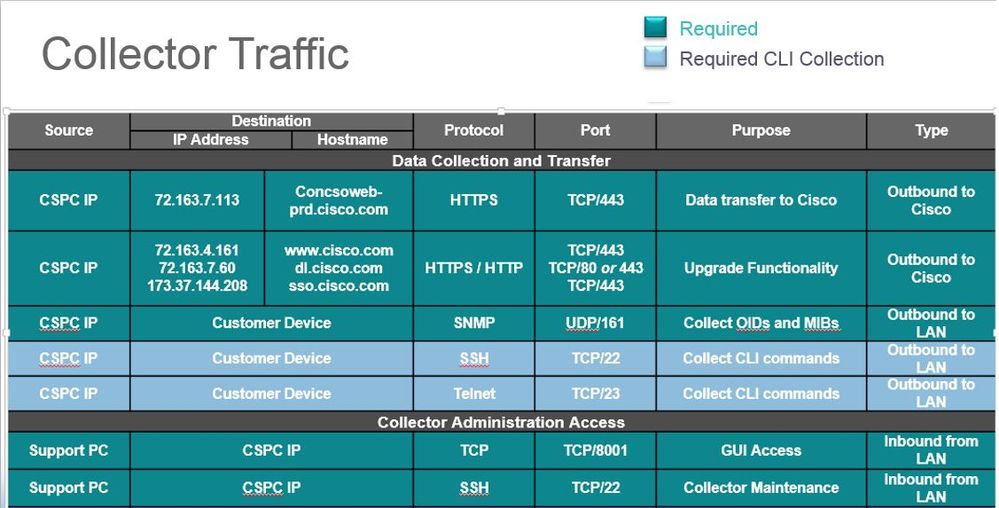
The following Ports must be open for a default SNTC deployment
Does your collector is configured or needs to be configured with a Proxy?
In deploying the image you would have created the cli admin password? (java based shell authentication is not the same as the GUI)
If so have you also created/activated the users collectorlogin and root ? (real linux shell)
If not do the following for the cli admin shell
admin# pwdreset root 90
And
admin# pwdreset collectorlogin 90
it will activate those accounts and generate their passwords ( keep them where you can refer to them in the future)
after that
Via SSH Login to collector as user collectorlogin and then use command below to connect as root (cannot connect directly)
# su root
Send me the output of the following commands in Private message
# tail -100 /opt/ConcsoTgw/tail-end-gateway-decoupled/bin/CONN_TEG_LOGS/tail-end-gateway.log
# openssl s_client -showcerts -connect concsoweb-prd.cisco.com:443
# tail -100 /opt/ConcsoTgw/tail-end-gateway-decoupled/bin/nohup.out
# wget https://72.163.7.113/HeadEndWebAppServlet/ --no-check-certificate
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-13-2020 09:40 AM - edited 03-13-2020 09:41 AM
Thank you for the logs and I have reviewed and here are the root cause for that message at the moment (HTTPs Transport Mode has failed peer not authenticated )
in reviewing the output of the command :
# openssl s_client -showcerts -connect concsoweb-prd.cisco.com:443
We can see that you company security is using what is a called a transparent proxy.. Cisco CSPC has a certificate that must be authenticated on backend. However your security is intercepting that certificate and injecting its own.
They need to whitelist the Collector IP so that they do not intercept the Cisco certificate. A normal collector output of that command would be like the following :
# openssl s_client -showcerts -connect concsoweb-prd.cisco.com:443
CONNECTED(00000003)
depth=2 C = BM, O = QuoVadis Limited, CN = QuoVadis Root CA 2
verify error:num=19:self signed certificate in certificate chain
---
Certificate chain
0 s:/C=US/ST=CA/L=San Jose/O=Cisco Systems, Inc./CN=concsoweb-prd.cisco.com
i:/C=US/O=HydrantID (Avalanche Cloud Corporation)/CN=HydrantID SSL ICA G2
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-17-2020 07:33 AM
It is not the IP or the dns of that IP that is causing the problem, ALL if there was any other would need to be allowed by your company. Any other IP or DNS name for those servers if there were others would need to either be whitelisted sufficiently to directly go to its destination if you company intercept certificates or use a proxy that do allows it,
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide