- Cisco Community
- Technology and Support
- Networking
- Software-Defined Access (SD-Access)
- How to distribute manually mapped port SGT by SXP?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-25-2020 01:50 AM
Hello all!
I can not find an answer on my question. Please help
The issue:
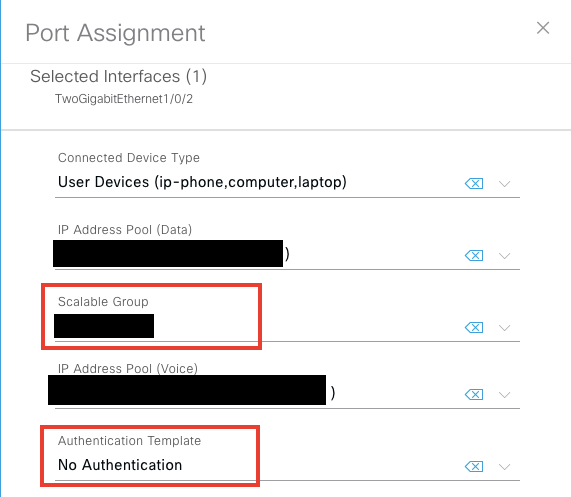
We need to have a number of ports with manual sgt mapping. We may configure it by DNAC as on a picture below.
All IP connected to this port are mapped to an appropriate sgt and all works fine but only with inline tagging. But I need to distribute ip to sgt mapping from this port by SXP.
And there is a problem. As I realise, the access switch with this port should be a source for this mapping but I can not establish SXP connection from this access switch to ISE for VRF (VN) where the this port (IP address pool) is situated. I have only GRT on uplinks and SXP connection for appropriate VRF (VN) can not be established. I also can not use vrf-aware sxp as so the access switch have an SVI in a vlan by sd-access design.
Is there any idea how to solve this issue?
Thank you in advance
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-02-2020 06:21 AM
I made software workaround for our case
The on-box python script runs periodically, check configuration and device-tracking database. Based on this information it add or remove static sgt-map in default vfr. From the default vrf these mappings are transferred to ISE by SXP and then distribute by SXP on other devices.
from cli import cli, configure
# get list of interface with manually configured sgt and their sgt
int_sgt_man = {}
for line in cli("show cts interface summ | i MANUAL").strip().split('\n'):
intf = line.split()[0]
sgt = cli("sh cts interface "+intf+" | i Peer SGT:").split(':')[1].strip()
int_sgt_man[intf] = sgt
# get list of statically configured sgt-map in default vrf except trustsec devices
cli_sgt_map = {}
for line in cli("sh run | i sgt-map").strip().split('\n'):
s_line = line.split()
if len(s_line)==6: # sgt map for default VRF
if s_line[5] != '2': # if not TrustSec device
cli_sgt_map[s_line[3]] = s_line[5]
# get list of IP tracked on interfaces from int_sgt_man list
track_ip = {}
for line in cli("sh device-tracking database | i REACHABLE").strip().split('\n'):
s_line = line.split()
if s_line[3] in int_sgt_man.keys() and ':' not in s_line[1]:
track_ip[s_line[1]] = int_sgt_man[s_line[3]]
ip_4_remove = set(cli_sgt_map.keys()) - set(track_ip.keys())
ip_4_add = set(track_ip.keys()) - set(cli_sgt_map.keys())
for ip in ip_4_remove:
configure('no cts role-based sgt-map %s sgt %s'%(ip,cli_sgt_map[ip]))
for ip in ip_4_add:
configure('cts role-based sgt-map %s sgt %s'%(ip,track_ip[ip]))This script is running periodically by applet
event manager applet sgtm authorization bypass event timer watchdog time 180 maxrun 10 action 1.0 cli command "en" action 2.0 cli command "guestshell run python /flash/guest-share/sgt-mapper.py"
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-02-2020 06:21 AM
I made software workaround for our case
The on-box python script runs periodically, check configuration and device-tracking database. Based on this information it add or remove static sgt-map in default vfr. From the default vrf these mappings are transferred to ISE by SXP and then distribute by SXP on other devices.
from cli import cli, configure
# get list of interface with manually configured sgt and their sgt
int_sgt_man = {}
for line in cli("show cts interface summ | i MANUAL").strip().split('\n'):
intf = line.split()[0]
sgt = cli("sh cts interface "+intf+" | i Peer SGT:").split(':')[1].strip()
int_sgt_man[intf] = sgt
# get list of statically configured sgt-map in default vrf except trustsec devices
cli_sgt_map = {}
for line in cli("sh run | i sgt-map").strip().split('\n'):
s_line = line.split()
if len(s_line)==6: # sgt map for default VRF
if s_line[5] != '2': # if not TrustSec device
cli_sgt_map[s_line[3]] = s_line[5]
# get list of IP tracked on interfaces from int_sgt_man list
track_ip = {}
for line in cli("sh device-tracking database | i REACHABLE").strip().split('\n'):
s_line = line.split()
if s_line[3] in int_sgt_man.keys() and ':' not in s_line[1]:
track_ip[s_line[1]] = int_sgt_man[s_line[3]]
ip_4_remove = set(cli_sgt_map.keys()) - set(track_ip.keys())
ip_4_add = set(track_ip.keys()) - set(cli_sgt_map.keys())
for ip in ip_4_remove:
configure('no cts role-based sgt-map %s sgt %s'%(ip,cli_sgt_map[ip]))
for ip in ip_4_add:
configure('cts role-based sgt-map %s sgt %s'%(ip,track_ip[ip]))This script is running periodically by applet
event manager applet sgtm authorization bypass event timer watchdog time 180 maxrun 10 action 1.0 cli command "en" action 2.0 cli command "guestshell run python /flash/guest-share/sgt-mapper.py"
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: