- Cisco Community
- Technology and Support
- Networking
- Software-Defined Access (SD-Access)
- ISE VLAN ID/Name setup to match with DNAC Generated VLAN name
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-01-2020 11:22 AM
I am working on a DNAC 1.3.3.7 now. I am confused about the ISE policy element setup for VLAN.
From very early EFT guide, there is a statement for ISE VLAN ID/Name setup to match with DNAC IP Pool to Virtual Network:
Note: DNA Center will generate well formatted VLAN Names when deploying an IP Pool to a Virtual Network. This format is [<Virtual_Network_Name>_<IP_Pool_Subnet>] Where the subnet octet are separated by underscore characters, instead of decimals.
Therefore, I used to select section select VLAN and
set the ID/Name : Campus_172_16_101_0
From EFT 1.3.1.0 guide, I found the statement:
Note: DNA Center will generate well formatted VLAN Names when deploying an IP Pool to a Virtual Network. This format is [<IP_Pool_Subnet>-<Virtual_Network_Name>] where the subnet octet are separated by underscore characters, instead of decimals.
First the order of the ID/Name is reversed as compare to the early EFT guide. Moreover, from the 1.3.1.0 guide, it instructs me to
section select Security Group Tag and select the ID/Name: Campus
Therefore, I might have three available setup for VLAN ID/Name in ISE:
1) Campus_172_16_101_0
2) 172_16_101_0_Campus
3) Campus
Please advise which setup should I use for 1.3.3.7?
Solved! Go to Solution.
- Labels:
-
SD-Access
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-01-2020 12:28 PM - edited 09-01-2020 12:58 PM
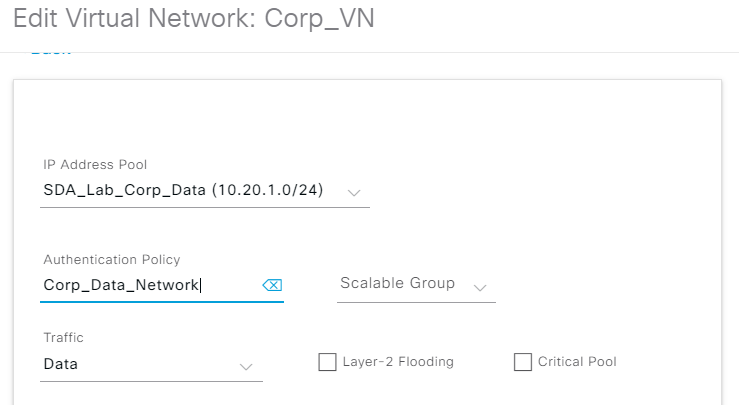
With DNAC version 1.3.3.7, the default VLAN/Authentication Policy name will use format [<IP_Pool_Subnet>-<Virtual_Network_Name>] which is the same behaviour as version 1.3.1.X. Note that you can customise the Authentication Policy name if it makes sense for your environment. For example, I changed the name for the below IP Address Pool from the default of 10_20_1_0-Corp_VN to Corp_Data_Network as this makes it clearer to understand the purpose of the IP Pool when inspecting the fabric edge VLAN database and ISE policies. There are also other reasons to change the default Authorisation Policy name as described in the following
You then set the Authentication Policy default or customised name as the VLAN ID/NAME within your ISE authorisation profile.
As you also stated, there is an alternative way to set the endpoint VLAN/IP pool from ISE and that is to use the 'Security Group' option under the authorisation profile instead of VLAN. This option pulls the VN/IP pool information directly from DNAC using the API instead of having to enter the VLAN name manually. This option also allows you to set the SGT under the authorisation profile instead of under the authorisation policy within the policy set. Please see the following for more info
https://community.cisco.com/t5/networking-documents/how-to-sda-host-onboarding-with-ise/ta-p/4012430
Setting the endpoint VLAN/IP Pool using either the VLAN or Security Group option are both acceptable for DNAC version 1.3.3.7 as noted in the above document. I have used both methods in production.
Hope this helps.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-01-2020 12:59 PM
Totally agree with @willwetherman on using either way. IMO it is a preference which one you choose. I typically use the 'Setting the VLAN/IP Pool using the VLAN' as I think it is easier for other admins to understand what range/VN will be used by that particular authz profile. Adding additional information for understanding purposes:
ISE will push the string that is configured in the matching policy authz profile that contains the unique string identifier extracted from DNAC and configured in each respective authz profile. The string gets pushed in the radius packet as a radius attribute that the switch will use as the identifier. The attribute I am referencing looks like this in detailed ISE logs: Tunnel-Private-Group-ID (tag=1) 192_168_0_0-VN1. This attribute allows the switch to map either the name or vlan id to the proper vlan. Once this happens your Anycast gateway comes up/up upon successful auth/mapping. Keep in mind that DNAC will automatically name the vlans which is why that string must match in ISE authz profiles in order for the process to work. Issue a '#show vlan' on an edge node and you will see what I am talking about. HTH!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-01-2020 12:28 PM - edited 09-01-2020 12:58 PM
With DNAC version 1.3.3.7, the default VLAN/Authentication Policy name will use format [<IP_Pool_Subnet>-<Virtual_Network_Name>] which is the same behaviour as version 1.3.1.X. Note that you can customise the Authentication Policy name if it makes sense for your environment. For example, I changed the name for the below IP Address Pool from the default of 10_20_1_0-Corp_VN to Corp_Data_Network as this makes it clearer to understand the purpose of the IP Pool when inspecting the fabric edge VLAN database and ISE policies. There are also other reasons to change the default Authorisation Policy name as described in the following
You then set the Authentication Policy default or customised name as the VLAN ID/NAME within your ISE authorisation profile.
As you also stated, there is an alternative way to set the endpoint VLAN/IP pool from ISE and that is to use the 'Security Group' option under the authorisation profile instead of VLAN. This option pulls the VN/IP pool information directly from DNAC using the API instead of having to enter the VLAN name manually. This option also allows you to set the SGT under the authorisation profile instead of under the authorisation policy within the policy set. Please see the following for more info
https://community.cisco.com/t5/networking-documents/how-to-sda-host-onboarding-with-ise/ta-p/4012430
Setting the endpoint VLAN/IP Pool using either the VLAN or Security Group option are both acceptable for DNAC version 1.3.3.7 as noted in the above document. I have used both methods in production.
Hope this helps.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-01-2020 12:59 PM
Totally agree with @willwetherman on using either way. IMO it is a preference which one you choose. I typically use the 'Setting the VLAN/IP Pool using the VLAN' as I think it is easier for other admins to understand what range/VN will be used by that particular authz profile. Adding additional information for understanding purposes:
ISE will push the string that is configured in the matching policy authz profile that contains the unique string identifier extracted from DNAC and configured in each respective authz profile. The string gets pushed in the radius packet as a radius attribute that the switch will use as the identifier. The attribute I am referencing looks like this in detailed ISE logs: Tunnel-Private-Group-ID (tag=1) 192_168_0_0-VN1. This attribute allows the switch to map either the name or vlan id to the proper vlan. Once this happens your Anycast gateway comes up/up upon successful auth/mapping. Keep in mind that DNAC will automatically name the vlans which is why that string must match in ISE authz profiles in order for the process to work. Issue a '#show vlan' on an edge node and you will see what I am talking about. HTH!
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: