- Cisco Community
- Technology and Support
- Networking
- Software-Defined Access (SD-Access)
- SDA and embedded wlc cannot assign vlan id from ISE
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
SDA and embedded wlc cannot assign vlan id from ISE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-25-2021 01:08 AM
Hi,
Struggeling with getting fabric in a box in a branch office up and running. Everything looks good in ISE, getting the correct policy hit - but the embedded wlc says it cannot assign vlan-id to the client from the name its getting from ISE:
[auth-mgr-feat_wireless] [31006]: (info): [0000.0000.0000:unknown] retrieving vlanid from name failed
This comes from ISE:
2021/09/25 07:53:49.949463 {wncd_x_R0-0}{1}: [radius] [31006]: (info): RADIUS: Tunnel-Private-Group-Id[81] 21 "10_208_23_0-VRF1"
2021/09/25 07:53:49.949468 {wncd_x_R0-0}{1}: [radius] [31006]: (info): RADIUS: EAP-Key-Name [102] 67 *
2021/09/25 07:53:49.949484 {wncd_x_R0-0}{1}: [radius] [31006]: (info): RADIUS: Cisco AVpair [1] 32 "cts:security-group-tag=0022-00"
2021/09/25 07:53:49.949495 {wncd_x_R0-0}{1}: [radius] [31006]: (info): RADIUS: Cisco AVpair [1] 32 "cts:security-group-tag=0022-00"
2021/09/25 07:53:49.949505 {wncd_x_R0-0}{1}: [radius] [31006]: (info): RADIUS: Cisco AVpair [1] 30 "cts:sgt-name=VRF1-SG"
2021/09/25 07:53:49.949516 {wncd_x_R0-0}{1}: [radius] [31006]: (info): RADIUS: Cisco AVpair [1] 15 "cts:vn=VRF1"
2021/09/25 07:53:49.949525 {wncd_x_R0-0}{1}: [radius] [31006]: (info): RADIUS: MS-MPPE-Send-Key [16] 52 *
2021/09/25 07:53:49.949539 {wncd_x_R0-0}{1}: [radius] [31006]: (info): RADIUS: MS-MPPE-Recv-Key [17] 52 *
This "10_208_23_0-VRF1" exists as Vlan1033 on the switch, and the correct VNID is assigned from the control-plane under Fabric. Has anyone seen this before? The clients arent getting an IP without the correct vlan-id mapping from that name.
- Labels:
-
SD-Access
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-25-2021 10:40 AM
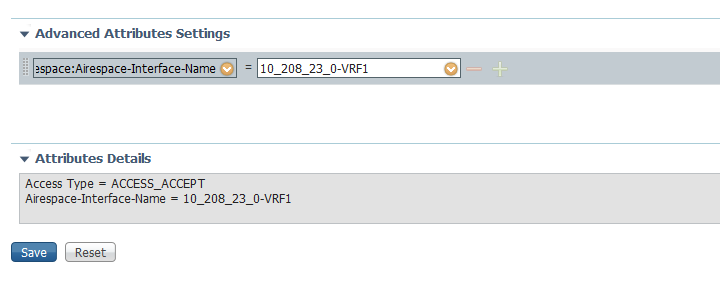
Try to use the AireSpace interface name attribute instead of the VLAN:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-27-2021 01:08 AM
Hi,
Didnt have time this weekend to test this, we had to roll this branch back. It was our pilot location - this problem didnt happen in the lab. Will keep you updated.
I suspect the error in the initial post is cosmetic - as the MAC-address of the clients showed up in the correct VLAN, but somehow they didnt get an IP. The topology was ISR 4331 - Fabric in a box (control, border, wlc and edge in a 9300), and then 5 other 9300s behind that FIAB acting as edges. As far as i can see, this is supported - but maybe i was wrong? Version 17.3.4.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-27-2021 07:49 AM
What are you using for your DHCP server ? Whatever you use must preserve Option 82 as that is what we use to determine the correct Fabric Edge to send the DHCP reply.
We do support connecting Fabric Edge Nodes to a Fabric-in-a-Box (FiaB ... B/CP/E/eWLC).
Cheers,
Scott Hodgdon
Senior Technical Marketing Engineer
Enterprise Networking and Cloud Group
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-03-2021 11:55 PM
Hi,
Does a VLAN with the following name exist on the FIAB? 10_208_23_0-VRF1
Could you do a show VLAN brief?
When configuring SDA it is important to use the built in AV-Pairs to get the full use of our SDA. This is how ours look:
Access Type = ACCESS_ACCEPT cisco-av-pair = cts:security-group-tag=0002-0 cisco-av-pair = cts:sgt-name=ClientSGT cisco-av-pair = cts:vn=CORPORATE Tunnel-Private-Group-ID = 1:CORPORATE Tunnel-Medium-Type = 1:13 Tunnel-Type = 1:6
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-20-2021 12:37 AM
Hallo,
I did some comparisons between our onprem fabric with external wlc-9800 that works, and our branch fabric with fabric-in-a-box on a 9300. There were some commands relating to CTS that seems to have made som problems:
cts role-based enforcement
cts role-based enforcement vlan-list x,y,z
When i removed these, the clients started getting IP-adresses in the correct pool. This doesnt make much sense to me, bug?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-20-2021 11:42 PM
Has those commands been added as part of the fabric provisioning, or have you typed them in manually?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-20-2021 11:49 PM
They were added as part of the provisioning, and so i cant quite understand why they were there in the branch, and not onprem.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-22-2021 01:09 AM
I cannot rememeber if I have ever seen those commands on a FIAB, let me just verify in the lab and see if this is normal behavior.
I have create FIAB with wireless many times with the default provisioning, with out any issues.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-24-2021 11:40 PM
Did you see the same commands @rasmus.elmholt ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-03-2021 03:19 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-04-2021 01:31 AM
Hm ok, but that config works with those lines in? could you share the ISE authentication result where you assign pools for this config?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-05-2021 03:04 AM
Access Type = ACCESS_ACCEPT cisco-av-pair = cts:security-group-tag=0002-0 cisco-av-pair = cts:sgt-name=ClientSGT cisco-av-pair = cts:vn=CORPORATE Tunnel-Private-Group-ID = 1:CORPORATE Tunnel-Medium-Type = 1:13 Tunnel-Type = 1:6
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide