- Cisco Community
- Technology and Support
- Networking
- Switching
- It works now! I can access
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-19-2017 08:57 AM - edited 03-08-2019 10:39 AM
Dear networking experts,
I have an ASA 5506-X and I use ASDM to manage the ASA. My end goal is to have a user connected to my Guest WIFI network access a host on my internal network. The job of the host is to authenticate the guest users and allow them to access the internet once the guest accepts our TOS.
Background Info:
I have multiple interfaces on the ASA, but the main focus is on 3 of them.
Interface 1/2 - Inside security level 100
Interface 1/2.30 - GuestWifi (vlan30) security level 40
Intterface 1/3 - COMCAST (outside network) security level 0
GuestWIFI vlan uses a different subnet than the inside interface and uses the ASA as a DHCP server to issue IP address to clients. Right now, everything works, the users are able to connect to the guest wifi and obtain an IP address and surf the web. However, I want the guest users to accept a TOS before accessing the internet. The TOS is a web application installed on a server that is connected to the inside network. By default, in the guest interface, there is an Implicit rule created that will allow traffic from any source to any destination with a less secure network, see the image below. With this rule in place internet connectivity works, but the host is not accessible via the Guest Wifi. When I create an ACL to allow traffic destined for port 8843, it overrides the Implicit rule, and therefore the internet connectivity stops working. How do I keep the internet connectivity as wells allow clients to access the host to authenticate and accept the TOS?
The NAT Rules are below:
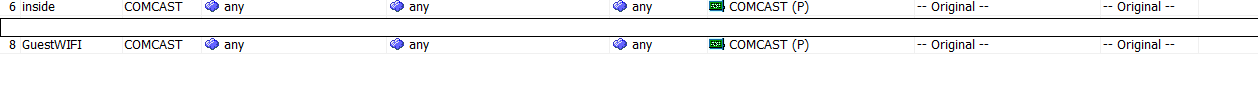
The ACL:

Solved! Go to Solution.
- Labels:
-
Other Switching
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-23-2017 11:19 AM
Can you post the CLI "sh runn" output. (exclude the senstive information like passwords, Public IP's, Credentials etc)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-23-2017 11:36 AM
Hi,
Here you go:
Result of the command: "sh runn"
: Saved
:
: Serial Number: XXXXXXXXXXX
: Hardware: ASA5506, 4096 MB RAM, CPU Atom C2000 series 1250 MHz, 1 CPU (4 cores)
:
ASA Version 9.4(2)
!
hostname ASA-5506-ASA
domain-name XXXXXXXXXXXXXXXXXXX
enable password XXXXXXXXXX
names
ip local pool VPN_Pool 1xx.xx.xx-1xx.xx.xx.xx mask 255.xxx.xxx.0
!
interface GigabitEthernet1/1
description To Verizon WAN
nameif outside
security-level 0
ip address XXX.XX.XXX.XX XXX.XXX.XXX.2XX
!
interface GigabitEthernet1/2
description Inside Network
nameif inside
security-level 100
ip address XXXXXXXXXXXXXXXXXXXXXXXXXX
!
interface GigabitEthernet1/2.30
description Guest_Wifi_Vlan
vlan 30
nameif GuestWIFI
security-level 40
ip address 192.168.18.1 255.255.255.0
!
interface GigabitEthernet1/3
description To Comcast WAN
nameif COMCAST
security-level 0
ip address XXXXXXXXXXXXXXXXXXXXXXXXXX
!
interface GigabitEthernet1/4
description DMZ Interface
nameif DMZ
security-level 50
ip address XXXXXXXXXXXXXXXXXXXXXXXXXX
!
interface GigabitEthernet1/5
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet1/6
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet1/7
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet1/8
shutdown
no nameif
no security-level
no ip address
!
interface Management1/1
management-only
no nameif
no security-level
no ip address
!
boot system disk0:/XXXXX.SPA
ftp mode passive
clock timezone EST -5
clock summer-time EDT recurring
dns domain-lookup inside
dns domain-lookup COMCAST
dns domain-lookup DMZ
dns server-group DefaultDNS
name-server XXXXXXXXXXXXXXXXXXX
domain-name XXXXXXXXXXXXXXXXXXX
same-security-traffic permit inter-interface
same-security-traffic permit intra-interface
object network obj_any
subnet XXXXXXXXXXXXXXXXXXX
object network NETWORK_OBJ_XXXXXXXXXXXXXXXXXXX
subnet XXXXXXXXXXXXXXXXXXX
object network CUCM-6970
host XXXXXXXXXXXXXXXXXXX
object network CUCM-69
host XXXXXXXXXXXXXXXXXXX
object network DMZ-Subnet
subnet XXXXXXXXXXXXXXXXXXX
object-group service ICMP_ALLOWED
service-object icmp echo
service-object icmp echo-reply
service-object icmp unreachable
service-object icmp time-exceeded
object-group network INSIDE_SUBNET
network-object XXXXXXXXXXXXXXXXXXX
object-group network TOS_HOST
network-object host XXXXXXXXXXXXXXXXXXX
object-group network GuestWiFi_SUBNET
network-object 192.168.18.0 255.255.255.0
access-list SplitTunnel standard permit XXXXXXXXXXXXXXXXXXX
access-list SplitTunnel standard permit XXXXXXXXXXXXXXXXXXX
access-list SplitTunnel standard permit XXXXXXXXXXXXXXXXXXX
access-list outside_access_in extended permit object-group DM_INLINE_SERVICE_1 any object-group DM_INLINE_NETWORK_1
access-list AnyConnect_Client_Local_Print extended deny ip any4 any4
access-list AnyConnect_Client_Local_Print extended permit tcp any4 any4 eq lpd
access-list AnyConnect_Client_Local_Print remark IPP: Internet Printing Protocol
access-list AnyConnect_Client_Local_Print extended permit tcp any4 any4 eq 631
access-list AnyConnect_Client_Local_Print remark Windows' printing port
access-list AnyConnect_Client_Local_Print extended permit tcp any4 any4 eq 9100
access-list AnyConnect_Client_Local_Print remark mDNS: multicast DNS protocol
access-list AnyConnect_Client_Local_Print extended permit udp any4 host XXXXXXXXXXXXXXXXXXX eq 5353
access-list AnyConnect_Client_Local_Print remark LLMNR: Link Local Multicast Name Resolution protocol
access-list AnyConnect_Client_Local_Print extended permit udp any4 host XXXXXXXXXXXXXXXXXXX eq 5355
access-list AnyConnect_Client_Local_Print remark TCP/NetBIOS protocol
access-list AnyConnect_Client_Local_Print extended permit tcp any4 any4 eq 137
access-list AnyConnect_Client_Local_Print extended permit udp any4 any4 eq netbios-ns
access-list GuestWIFI_access_in extended permit ip object-group GuestWiFi_SUBNET object-group TOS_HOST
access-list GuestWIFI_access_in extended deny ip object-group GuestWiFi_SUBNET object-group INSIDE_SUBNET
access-list GuestWIFI_access_in extended deny ip object-group GuestWiFi_SUBNET any
pager lines 24
logging enable
logging asdm informational
mtu outside 1500
mtu inside 1500
mtu GuestWIFI 1500
mtu COMCAST 1500
mtu DMZ 1500
icmp unreachable rate-limit 1 burst-size 1
asdm image disk0:/XXXXXXXXXXXXXXXXXXX.bin
no asdm history enable
arp timeout 14400
no arp permit-nonconnected
nat (inside,outside) source static any any destination static NETWORK_OBJ_XXXXXXXXXXXXXXXXXXX NETWORK_OBJ_XXXXXXXXXXXXXXXXXXX no-proxy-arp route-lookup
!
object network CUCM-6970
nat (inside,outside) static interface service tcp 6970 6970
object network CUCM-69
nat (inside,outside) static interface service udp tftp tftp
object network DMZ-Subnet
nat (DMZ,COMCAST) dynamic interface
nat (inside,COMCAST) after-auto source dynamic any interface
nat (inside,outside) after-auto source dynamic any interface
nat (GuestWIFI,COMCAST) after-auto source dynamic any interface
access-group outside_access_in in interface outside
access-group COMCAST_access_in in interface COMCAST
route COMCAST XXXXXXXXXXXXXXXXXXX
route outside XXXXXXXXXXXXXXXXXXX
route inside XXXXXXXXXXXXXXXXXXX XXXXXXXXXXXXXXXXXXX
ldap attribute-map LDAP_memberOf
map-name memberOf Group-Policy
map-value memberOf CN=XXXXXXXXXXXXXXXXXXX,OU=Groups,DC=XXX,DC=XXXX TEST
aaa-server RADIUS protocol radius
aaa-server RADIUS (inside) host XXXXXXXXXXXXXXXXXXX
key *****
radius-common-pw XXXXXXXXXXXXXXXXXXX
aaa-server LDAP_Domain protocol ldap
aaa-server LDAP_Domain (inside) host XXXXXXXXXXXXXXXXXXX
ldap-base-dn DC=XXX,DC=XXXX
ldap-scope subtree
ldap-naming-attribute sAMAccountName
ldap-login-password *****
ldap-login-dn CN=XXXXXXXXXXXXXXXX,OU=XXXXXXXXXXXXXXX,DC=XXX,DC=XXXXX
server-type microsoft
ldap-attribute-map LDAP_memberOf
user-identity default-domain LOCAL
aaa authentication enable console LOCAL
aaa authentication http console LOCAL
aaa authentication ssh console LOCAL
http server enable
http XXXXXXXXXXXXXXXXXXX inside
http XXXXXXXXXXXXXXXXXXX inside
http XXXXXXXXXXXXXXXXXXX outside
http XXXXXXXXXXXXXXXXXXX outside
snmp-server host inside XXXXXXXXXXXXXXXXXXX community *****
snmp-server host inside XXXXXXXXXXXXXXXXXXX community *****
snmp-server host inside XXXXXXXXXXXXXXXXXXX poll community ***** version 2c
no snmp-server location
no snmp-server contact
service sw-reset-button
dhcpd auto_config outside
!
dhcpd address 192.168.18.2-192.168.18.254 GuestWIFI
dhcpd dns 8.8.8.8 8.8.4.4 interface GuestWIFI
dhcpd option 3 ip 192.168.18.1 interface GuestWIFI
dhcpd option 6 ip 8.8.8.8 8.8.4.4 interface GuestWIFI
dhcpd enable GuestWIFI
!
threat-detection basic-threat
threat-detection statistics port
threat-detection statistics protocol
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
ntp server 192.5.41.40 source outside
: end
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-23-2017 11:43 AM
Hey,
Following config is missing.
access-group GuestWIFI_access_in in interface GuestWIFI
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-23-2017 11:46 AM
That's why I didn't see the ACLs in GUI. I run the command and I can see the ACLs in ASDM GUI now.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-23-2017 11:53 AM
It works now! I can access the TOS_Host.
Thank you so much for helping solve the issue.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-23-2017 11:56 AM
Glad to hear :-) You are welcome.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-14-2020 09:32 PM
can you tell me how can you access one interface to another?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-15-2020 04:05 AM
Hello,
is this on an ASA ? Do you have 'same-security-traffic permit inter-interface' confgured ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-15-2020 02:35 PM
Thanks for your reply and I really appreciate it . I found the solution.
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-14-2020 08:33 PM
Hello
did you solve the problem I have the same problem but can't find the solution
- « Previous
-
- 1
- 2
- Next »
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community:
