- Cisco Community
- Technology and Support
- Networking
- Switching
- Re: Anyconnect VPN no internet access (Tunnel All Networks)
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Anyconnect VPN no internet access (Tunnel All Networks)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-15-2019 11:08 PM
Hi,
I'm try to setup the Anyconnect client on the ASA-5510. I want to make all traffic go through the firewall. But I can't access to the internet if I chose Tunnel All Networks.
Can someone please tell me what did I set incorrectly on the ACL / NAT? Thanks.
: Saved
:
ASA Version 8.2(5)
!
hostname RFHKASA
names
name 192.168.10.10 RFHK
name 218.255.21.162 New-WAN
name 192.168.10.20 Wireless_Router
name 192.168.10.21 Wireless_Satellite
name 10.10.1.0 VPN
name 192.168.10.1 ASA_LAN
name 10.21.5.254 PBX_GW
!
interface Ethernet0/0
nameif Outside
security-level 0
ip address 118.143.97.218 255.255.255.252
!
interface Ethernet0/1
nameif Inside
security-level 100
ip address ASA_LAN 255.255.255.0
!
interface Ethernet0/2
nameif New_Outside
security-level 0
ip address New-WAN 255.255.255.252
!
interface Ethernet0/3
nameif PBX
security-level 100
ip address PBX_GW 255.255.255.0
!
interface Management0/0
nameif management
security-level 100
ip address 192.168.2.1 255.255.255.0
management-only
!
ftp mode passive
clock timezone HKST 8
dns domain-lookup Outside
dns domain-lookup Inside
dns domain-lookup New_Outside
dns domain-lookup PBX
dns domain-lookup management
dns server-group DefaultDNS
name-server 175.45.33.251
name-server 59.152.248.251
name-server 8.8.8.8
same-security-traffic permit inter-interface
object-group service DM_INLINE_SERVICE_1
service-object icmp
service-object tcp eq imap4
service-object tcp-udp eq www
service-object tcp eq https
object-group service DM_INLINE_SERVICE_2
service-object icmp
service-object tcp eq imap4
access-list outside extended deny ip any any
access-list outside extended permit tcp 192.168.10.0 255.255.255.0 any eq www
access-list outside extended permit tcp 192.168.10.0 255.255.255.0 any eq https
access-list Outside_access_in extended permit ip 192.168.10.0 255.255.255.0 any
access-list VPN standard permit host 0.0.0.0
access-list VPN_access_in extended permit ip any 192.168.10.0 255.255.255.0
access-list VPN_access_in extended permit ip 192.168.10.0 255.255.255.0 any
access-list VPN_access_in extended permit ip any VPN 255.255.255.0
access-list VPN_access_in extended permit icmp any any inactive
access-list Inside_access_in extended permit ip any any
access-list Inside_access_in extended permit ip any 192.168.10.0 255.255.255.0
access-list Inside_access_in extended permit ip any VPN 255.255.255.0
access-list Inside_access_in extended permit object-group DM_INLINE_SERVICE_2 any 10.21.5.0 255.255.255.0
access-list Inside_access_in extended permit ip 10.21.5.0 255.255.255.0 any
access-list PBX_access_in extended permit ip any any
access-list PBX_access_in extended permit object-group DM_INLINE_SERVICE_1 any any
access-list LOCAL_LAN standard permit 192.168.10.0 255.255.255.0
access-list New_Outside_nat0_outbound extended permit ip any VPN 255.255.255.0
access-list New_Outside_nat0_outbound extended permit ip VPN 255.255.255.0 any
access-list Inside_nat0_outbound extended permit ip any VPN 255.255.255.0
pager lines 24
logging enable
logging asdm informational
mtu Outside 1500
mtu Inside 1500
mtu New_Outside 1500
mtu PBX 1500
mtu management 1500
ip local pool ClientVPN 10.10.1.10-10.10.1.50 mask 255.255.255.0
ip local pool VPN2 192.168.20.10-192.168.20.50 mask 255.255.255.0
ip local pool VPN 10.10.1.51-10.10.1.100 mask 255.255.255.0
icmp unreachable rate-limit 1 burst-size 1
asdm image disk0:/asdm-645.bin
no asdm history enable
arp timeout 14400
global (New_Outside) 1 interface
nat (Inside) 0 access-list Inside_nat0_outbound
nat (Inside) 1 0.0.0.0 255.255.255.255
nat (Inside) 1 VPN 255.255.255.0
nat (Inside) 1 0.0.0.0 0.0.0.0
nat (New_Outside) 0 access-list New_Outside_nat0_outbound
access-group Outside_access_in in interface Outside
access-group Inside_access_in in interface Inside
access-group VPN_access_in in interface New_Outside
access-group PBX_access_in in interface PBX
route New_Outside 0.0.0.0 0.0.0.0 218.255.21.161 1
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
dynamic-access-policy-record DfltAccessPolicy
http server enable
http 192.168.1.0 255.255.255.0 management
http 192.168.1.0 255.255.255.0 Inside
http 192.168.10.0 255.255.255.0 Inside
http 192.168.1.0 255.255.255.0 PBX
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart
sysopt noproxyarp Inside
crypto ipsec transform-set ESP-DES-SHA esp-des esp-sha-hmac
crypto ipsec transform-set ESP-DES-MD5 esp-des esp-md5-hmac
crypto ipsec security-association lifetime seconds 28800
crypto ipsec security-association lifetime kilobytes 4608000
crypto map Outside_map interface Outside
crypto isakmp enable Outside
crypto isakmp policy 10
authentication pre-share
encryption des
hash sha
group 2
lifetime 86400
crypto isakmp policy 50
authentication pre-share
encryption des
hash md5
group 2
lifetime 86400
telnet 0.0.0.0 0.0.0.0 Inside
telnet 192.168.1.0 255.255.255.0 PBX
telnet timeout 5
ssh timeout 5
console timeout 0
management-access PBX
dhcpd dns 175.45.33.251 59.152.248.251
!
dhcpd address 192.168.10.50-192.168.10.149 Inside
dhcpd enable Inside
!
dhcpd address 192.168.2.2-192.168.2.254 management
!
threat-detection basic-threat
threat-detection statistics access-list
threat-detection statistics tcp-intercept rate-interval 30 burst-rate 400 average-rate 200
webvpn
enable New_Outside
anyconnect-essentials
svc image disk0:/anyconnect-win-3.1.08009-k9.pkg 1
svc image disk0:/anyconnect-win-2.4.1012-k9.pkg 2
svc image disk0:/anyconnect-linux-2.4.1012-k9.pkg 3 regex "Linux"
svc image disk0:/anyconnect-macosx-i386-3.1.05187-k9.pkg 4
svc profiles VPN_Profile disk0:/vpn_profile.xml
svc enable
tunnel-group-list enable
group-policy SSLVPN internal
group-policy SSLVPN attributes
banner value Welcome to Finsbury SSL VPN
wins-server none
dns-server value 175.45.33.251 59.152.248.251
vpn-tunnel-protocol svc webvpn
split-tunnel-policy tunnelspecified
split-tunnel-network-list value LOCAL_LAN
default-domain none
address-pools value ClientVPN
webvpn
url-list none
svc keep-installer installed
svc profiles value VPN_Profile
svc ask none default svc
group-policy DefaultRAGroup internal
group-policy DefaultRAGroup attributes
banner value Welocme to RLM Finsbury VPN Access
banner value This VPN Access Is For AUTHORIZED USERS Only
dns-server value 8.8.8.8
vpn-tunnel-protocol IPSec l2tp-ipsec
default-domain none
address-pools value ClientVPN
ipv6-address-pools none
tunnel-group DefaultRAGroup general-attributes
address-pool (New_Outside) ClientVPN
default-group-policy DefaultRAGroup
tunnel-group DefaultRAGroup ipsec-attributes
pre-shared-key *****
tunnel-group DefaultRAGroup ppp-attributes
no authentication chap
authentication ms-chap-v2
tunnel-group VPN type remote-access
tunnel-group VPN general-attributes
address-pool ClientVPN
default-group-policy SSLVPN
tunnel-group VPN webvpn-attributes
group-alias SSLVPN enable
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum client auto
message-length maximum 512
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
inspect ip-options
inspect icmp
!
service-policy global_policy global
prompt hostname context
no call-home reporting anonymous
Cryptochecksum:ce91ff0393e3aaac7a7fd3d9645682bc
: end
- Labels:
-
Other Switching
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-16-2019 02:32 AM
Hello,
try and change the NAT exemption access list you currently have from:
access-list Inside_nat0_outbound extended permit ip any VPN 255.255.255.0
to
access-list Inside_nat0_outbound extended permit ip 192.168.10.0 255.255.255.0 10.10.1.0 255.255.255.0
Also, although I am not sure if you need that in pre 8.3 versions, I think you also need to configure:
same-security-traffic permit intra-interface
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-16-2019 08:10 AM
Thanks Georg. I updated the NAT rules but still couldn't access to the internet via VPN.
For the same-security-traffic permit intra-interface, Is that the option below I should enable in ASDM?
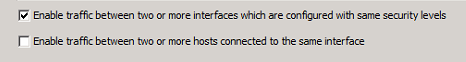
Thanks again.
Result of the command: "sh run"
: Saved
:
ASA Version 8.2(5)
!
hostname RFHKASA
names
name 192.168.10.10 RFHK
name 218.255.21.162 New-WAN
name 192.168.10.20 Wireless_Router
name 192.168.10.21 Wireless_Satellite
name 10.10.1.0 VPN
name 192.168.10.1 ASA_LAN
name 10.21.5.254 PBX_GW
!
interface Ethernet0/0
nameif Outside
security-level 0
ip address 118.143.97.218 255.255.255.252
!
interface Ethernet0/1
nameif Inside
security-level 100
ip address ASA_LAN 255.255.255.0
!
interface Ethernet0/2
nameif New_Outside
security-level 0
ip address New-WAN 255.255.255.252
!
interface Ethernet0/3
nameif PBX
security-level 100
ip address PBX_GW 255.255.255.0
!
interface Management0/0
nameif management
security-level 100
ip address 192.168.2.1 255.255.255.0
management-only
!
ftp mode passive
clock timezone HKST 8
dns domain-lookup Outside
dns domain-lookup Inside
dns domain-lookup New_Outside
dns domain-lookup PBX
dns domain-lookup management
dns server-group DefaultDNS
name-server 175.45.33.251
name-server 59.152.248.251
name-server 8.8.8.8
same-security-traffic permit inter-interface
object-group service DM_INLINE_SERVICE_1
service-object icmp
service-object tcp eq imap4
service-object tcp-udp eq www
service-object tcp eq https
object-group service DM_INLINE_SERVICE_2
service-object icmp
service-object tcp eq imap4
access-list outside extended deny ip any any
access-list outside extended permit tcp 192.168.10.0 255.255.255.0 any eq www
access-list outside extended permit tcp 192.168.10.0 255.255.255.0 any eq https
access-list Outside_access_in extended permit ip 192.168.10.0 255.255.255.0 any
access-list VPN standard permit host 0.0.0.0
access-list VPN_access_in extended permit ip any 192.168.10.0 255.255.255.0
access-list VPN_access_in extended permit ip 192.168.10.0 255.255.255.0 any
access-list VPN_access_in extended permit ip any VPN 255.255.255.0
access-list VPN_access_in extended permit icmp any any inactive
access-list Inside_access_in extended permit ip any any
access-list Inside_access_in extended permit ip any 192.168.10.0 255.255.255.0
access-list Inside_access_in extended permit ip any VPN 255.255.255.0
access-list Inside_access_in extended permit object-group DM_INLINE_SERVICE_2 any 10.21.5.0 255.255.255.0
access-list Inside_access_in extended permit ip 10.21.5.0 255.255.255.0 any
access-list PBX_access_in extended permit ip any any
access-list PBX_access_in extended permit object-group DM_INLINE_SERVICE_1 any any
access-list LOCAL_LAN standard permit 192.168.10.0 255.255.255.0
access-list New_Outside_nat0_outbound extended permit ip any VPN 255.255.255.0
access-list New_Outside_nat0_outbound extended permit ip VPN 255.255.255.0 any
access-list Inside_nat0_outbound extended permit ip 192.168.10.0 255.255.255.0 VPN 255.255.255.0
pager lines 24
logging enable
logging asdm informational
mtu Outside 1500
mtu Inside 1500
mtu New_Outside 1500
mtu PBX 1500
mtu management 1500
ip local pool ClientVPN 10.10.1.10-10.10.1.50 mask 255.255.255.0
ip local pool VPN2 192.168.20.10-192.168.20.50 mask 255.255.255.0
ip local pool VPN 10.10.1.51-10.10.1.100 mask 255.255.255.0
icmp unreachable rate-limit 1 burst-size 1
asdm image disk0:/asdm-645.bin
no asdm history enable
arp timeout 14400
global (New_Outside) 1 interface
nat (Inside) 0 access-list Inside_nat0_outbound
nat (Inside) 1 0.0.0.0 255.255.255.255
nat (Inside) 1 VPN 255.255.255.0
nat (Inside) 1 0.0.0.0 0.0.0.0
nat (New_Outside) 0 access-list New_Outside_nat0_outbound
static (Inside,PBX) 192.168.10.0 192.168.10.0 netmask 255.255.255.0
static (PBX,Inside) 10.21.5.0 10.21.5.0 netmask 255.255.255.0
access-group Outside_access_in in interface Outside
access-group Inside_access_in in interface Inside
access-group VPN_access_in in interface New_Outside
access-group PBX_access_in in interface PBX
route New_Outside 0.0.0.0 0.0.0.0 218.255.21.161 1
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
dynamic-access-policy-record DfltAccessPolicy
http server enable
http 192.168.1.0 255.255.255.0 management
http 192.168.1.0 255.255.255.0 Inside
http 192.168.10.0 255.255.255.0 Inside
http 192.168.1.0 255.255.255.0 PBX
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart
sysopt noproxyarp Inside
crypto ipsec transform-set ESP-DES-SHA esp-des esp-sha-hmac
crypto ipsec transform-set ESP-DES-MD5 esp-des esp-md5-hmac
crypto ipsec security-association lifetime seconds 28800
crypto ipsec security-association lifetime kilobytes 4608000
crypto map Outside_map interface Outside
crypto isakmp enable Outside
crypto isakmp policy 10
authentication pre-share
encryption des
hash sha
group 2
lifetime 86400
crypto isakmp policy 50
authentication pre-share
encryption des
hash md5
group 2
lifetime 86400
telnet 0.0.0.0 0.0.0.0 Inside
telnet 192.168.1.0 255.255.255.0 PBX
telnet timeout 5
ssh timeout 5
console timeout 0
management-access PBX
dhcpd dns 175.45.33.251 59.152.248.251
!
dhcpd address 192.168.10.50-192.168.10.149 Inside
dhcpd enable Inside
!
dhcpd address 192.168.2.2-192.168.2.254 management
!
threat-detection basic-threat
threat-detection statistics access-list
threat-detection statistics tcp-intercept rate-interval 30 burst-rate 400 average-rate 200
webvpn
enable New_Outside
anyconnect-essentials
svc image disk0:/anyconnect-win-3.1.08009-k9.pkg 1
svc image disk0:/anyconnect-win-2.4.1012-k9.pkg 2
svc image disk0:/anyconnect-linux-2.4.1012-k9.pkg 3 regex "Linux"
svc image disk0:/anyconnect-macosx-i386-3.1.05187-k9.pkg 4
svc profiles VPN_Profile disk0:/vpn_profile.xml
svc enable
tunnel-group-list enable
group-policy SSLVPN internal
group-policy SSLVPN attributes
banner value Welcome to Finsbury SSL VPN
wins-server none
dns-server value 175.45.33.251 59.152.248.251
vpn-tunnel-protocol svc webvpn
split-tunnel-policy tunnelspecified
split-tunnel-network-list value LOCAL_LAN
default-domain none
address-pools value ClientVPN
webvpn
url-list none
svc keep-installer installed
svc profiles value VPN_Profile
svc ask none default svc
group-policy DefaultRAGroup internal
group-policy DefaultRAGroup attributes
banner value Welocme to RLM Finsbury VPN Access
banner value This VPN Access Is For AUTHORIZED USERS Only
dns-server value 8.8.8.8
vpn-tunnel-protocol IPSec l2tp-ipsec
default-domain none
address-pools value ClientVPN
ipv6-address-pools none
tunnel-group DefaultRAGroup general-attributes
address-pool (New_Outside) ClientVPN
default-group-policy DefaultRAGroup
tunnel-group DefaultRAGroup ipsec-attributes
pre-shared-key *****
tunnel-group DefaultRAGroup ppp-attributes
no authentication chap
authentication ms-chap-v2
tunnel-group VPN type remote-access
tunnel-group VPN general-attributes
address-pool ClientVPN
default-group-policy SSLVPN
tunnel-group VPN webvpn-attributes
group-alias SSLVPN enable
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum client auto
message-length maximum 512
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
inspect ip-options
inspect icmp
!
service-policy global_policy global
prompt hostname context
no call-home reporting anonymous
Cryptochecksum:a5ccf722a3512d8790b271c0bf824be9
: end
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-16-2019 11:48 AM
Hello,
you need to enable BOTH of the options. Check both fields...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-16-2019 11:54 AM
Just did. But still internet connection is lost once the VPN is connected
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-16-2019 01:14 PM
Hello,
I think you are missing the line in bold under the webvpn::
RFHKASA(config)# webvpn
RFHKASA(config-webvpn)# enable New_Outside
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-16-2019 01:45 PM
I am not sure if the post has been updated. But I am seeing enable New_Outside in the config.
Is AnyConnect working to access internal resources? (can you establish an AnyConnect session from outside and login successfully?) If so then I believe it is enabled on the interface. Could you post a fresh copy of the running config?
HTH
Rick
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-16-2019 01:57 PM
Rick,
you are right, it is already in there...my bad.
I wonder if this could be simply a licensing issue. Make sure you have the AnyConnect Essentials license installed. The output of:
RFHKASA#sh ver | inc AnyConnect
should include the line:
AnyConnect Essentials : 25 perpetual
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-16-2019 10:14 PM
Hi Georg,
Result of the command: "sh ver | inc AnyConnect"
AnyConnect for Mobile : Disabled
AnyConnect for Cisco VPN Phone : Disabled
AnyConnect Essentials : Enabled
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-16-2019 10:13 PM
Hi Richard,
Yes. I can login to the VPN client and access internal. Thanks.
Result of the command: "sh run"
: Saved
:
ASA Version 8.2(5)
!
hostname RFHKASA
names
name 192.168.10.10 RFHK
name 218.255.21.162 New-WAN
name 192.168.10.20 Wireless_Router
name 192.168.10.21 Wireless_Satellite
name 10.10.1.0 VPN
name 192.168.10.1 ASA_LAN
name 10.21.5.254 PBX_GW
!
interface Ethernet0/0
nameif Outside
security-level 0
ip address 118.143.97.218 255.255.255.252
!
interface Ethernet0/1
nameif Inside
security-level 100
ip address ASA_LAN 255.255.255.0
!
interface Ethernet0/2
nameif New_Outside
security-level 0
ip address New-WAN 255.255.255.252
!
interface Ethernet0/3
nameif PBX
security-level 100
ip address PBX_GW 255.255.255.0
!
interface Management0/0
nameif management
security-level 100
ip address 192.168.2.1 255.255.255.0
management-only
!
ftp mode passive
clock timezone HKST 8
dns domain-lookup Outside
dns domain-lookup Inside
dns domain-lookup New_Outside
dns domain-lookup PBX
dns domain-lookup management
dns server-group DefaultDNS
name-server 175.45.33.251
name-server 59.152.248.251
name-server 8.8.8.8
same-security-traffic permit inter-interface
same-security-traffic permit intra-interface
object-group service DM_INLINE_SERVICE_1
service-object icmp
service-object tcp eq imap4
service-object tcp-udp eq www
service-object tcp eq https
object-group service DM_INLINE_SERVICE_2
service-object icmp
service-object tcp eq imap4
access-list outside extended deny ip any any
access-list outside extended permit tcp 192.168.10.0 255.255.255.0 any eq www
access-list outside extended permit tcp 192.168.10.0 255.255.255.0 any eq https
access-list Outside_access_in extended permit ip 192.168.10.0 255.255.255.0 any
access-list VPN standard permit host 0.0.0.0
access-list VPN_access_in extended permit ip any 192.168.10.0 255.255.255.0
access-list VPN_access_in extended permit ip 192.168.10.0 255.255.255.0 any
access-list VPN_access_in extended permit ip any VPN 255.255.255.0
access-list VPN_access_in extended permit icmp any any inactive
access-list Inside_access_in extended permit ip any any
access-list Inside_access_in extended permit ip any 192.168.10.0 255.255.255.0
access-list Inside_access_in extended permit ip any VPN 255.255.255.0
access-list Inside_access_in extended permit object-group DM_INLINE_SERVICE_2 any 10.21.5.0 255.255.255.0
access-list Inside_access_in extended permit ip 10.21.5.0 255.255.255.0 any
access-list PBX_access_in extended permit ip any any
access-list PBX_access_in extended permit object-group DM_INLINE_SERVICE_1 any any
access-list LOCAL_LAN standard permit 192.168.10.0 255.255.255.0
access-list New_Outside_nat0_outbound extended permit ip any VPN 255.255.255.0
access-list New_Outside_nat0_outbound extended permit ip VPN 255.255.255.0 any
access-list Inside_nat0_outbound extended permit ip 192.168.10.0 255.255.255.0 VPN 255.255.255.0
pager lines 24
logging enable
logging asdm informational
mtu Outside 1500
mtu Inside 1500
mtu New_Outside 1500
mtu PBX 1500
mtu management 1500
ip local pool ClientVPN 10.10.1.10-10.10.1.50 mask 255.255.255.0
ip local pool VPN2 192.168.20.10-192.168.20.50 mask 255.255.255.0
ip local pool VPN 10.10.1.51-10.10.1.100 mask 255.255.255.0
icmp unreachable rate-limit 1 burst-size 1
asdm image disk0:/asdm-645.bin
no asdm history enable
arp timeout 14400
global (New_Outside) 1 interface
nat (Inside) 0 access-list Inside_nat0_outbound
nat (Inside) 1 0.0.0.0 255.255.255.255
nat (Inside) 1 VPN 255.255.255.0
nat (Inside) 1 0.0.0.0 0.0.0.0
nat (New_Outside) 0 access-list New_Outside_nat0_outbound
nat (New_Outside) 1 VPN 255.255.255.0
static (Inside,PBX) 192.168.10.0 192.168.10.0 netmask 255.255.255.0
static (PBX,Inside) 10.21.5.0 10.21.5.0 netmask 255.255.255.0
access-group Outside_access_in in interface Outside
access-group Inside_access_in in interface Inside
access-group VPN_access_in in interface New_Outside
access-group PBX_access_in in interface PBX
route New_Outside 0.0.0.0 0.0.0.0 218.255.21.161 1
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
dynamic-access-policy-record DfltAccessPolicy
http server enable
http 192.168.1.0 255.255.255.0 management
http 192.168.1.0 255.255.255.0 Inside
http 192.168.10.0 255.255.255.0 Inside
http 192.168.1.0 255.255.255.0 PBX
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart
sysopt noproxyarp Inside
crypto ipsec transform-set ESP-DES-SHA esp-des esp-sha-hmac
crypto ipsec transform-set ESP-DES-MD5 esp-des esp-md5-hmac
crypto ipsec security-association lifetime seconds 28800
crypto ipsec security-association lifetime kilobytes 4608000
crypto map Outside_map interface Outside
crypto isakmp enable Outside
crypto isakmp policy 10
authentication pre-share
encryption des
hash sha
group 2
lifetime 86400
crypto isakmp policy 50
authentication pre-share
encryption des
hash md5
group 2
lifetime 86400
telnet 0.0.0.0 0.0.0.0 Inside
telnet 192.168.1.0 255.255.255.0 PBX
telnet timeout 5
ssh timeout 5
console timeout 0
management-access PBX
dhcpd dns 175.45.33.251 59.152.248.251
!
dhcpd address 192.168.10.50-192.168.10.149 Inside
dhcpd enable Inside
!
dhcpd address 192.168.2.2-192.168.2.254 management
!
threat-detection basic-threat
threat-detection statistics access-list
threat-detection statistics tcp-intercept rate-interval 30 burst-rate 400 average-rate 200
webvpn
enable New_Outside
anyconnect-essentials
svc image disk0:/anyconnect-win-3.1.08009-k9.pkg 1
svc image disk0:/anyconnect-win-2.4.1012-k9.pkg 2
svc image disk0:/anyconnect-linux-2.4.1012-k9.pkg 3 regex "Linux"
svc image disk0:/anyconnect-macosx-i386-3.1.05187-k9.pkg 4
svc profiles VPN_Profile disk0:/vpn_profile.xml
svc enable
tunnel-group-list enable
group-policy SSLVPN internal
group-policy SSLVPN attributes
banner value Welcome to Finsbury SSL VPN
wins-server none
dns-server value 175.45.33.251 59.152.248.251
vpn-tunnel-protocol svc webvpn
split-tunnel-policy tunnelspecified
split-tunnel-network-list value LOCAL_LAN
default-domain none
address-pools value ClientVPN
webvpn
url-list none
svc keep-installer installed
svc profiles value VPN_Profile
svc ask none default svc
group-policy DefaultRAGroup internal
group-policy DefaultRAGroup attributes
banner value Welocme to RLM Finsbury VPN Access
banner value This VPN Access Is For AUTHORIZED USERS Only
dns-server value 8.8.8.8
vpn-tunnel-protocol IPSec l2tp-ipsec
default-domain none
address-pools value ClientVPN
ipv6-address-pools none
tunnel-group DefaultRAGroup general-attributes
address-pool (New_Outside) ClientVPN
default-group-policy DefaultRAGroup
tunnel-group DefaultRAGroup ipsec-attributes
pre-shared-key *****
tunnel-group DefaultRAGroup ppp-attributes
no authentication chap
authentication ms-chap-v2
tunnel-group VPN type remote-access
tunnel-group VPN general-attributes
address-pool ClientVPN
default-group-policy SSLVPN
tunnel-group VPN webvpn-attributes
group-alias SSLVPN enable
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum client auto
message-length maximum 512
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
inspect ip-options
inspect icmp
!
service-policy global_policy global
prompt hostname context
no call-home reporting anonymous
Cryptochecksum:f3b7d327fcb79e77fc18c5276bc75451
: end
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-16-2019 11:59 PM
Hello,
try and remove all NAT configuration except for the three lines below:
global (New_Outside) 1 interface
nat (Inside) 0 access-list Inside_nat0_outbound
nat (Inside) 1 192.168.10.0 255.255.255.0
I think 8.2 has nat-control enabled by default. You might want to enable the command below to bypass the interface access lists:
RFHKASA(config)#sysopt connection permit-vpn
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-17-2019 12:29 AM
Hi Georg,
I checked on the ASDM and confirmed it has been enabled.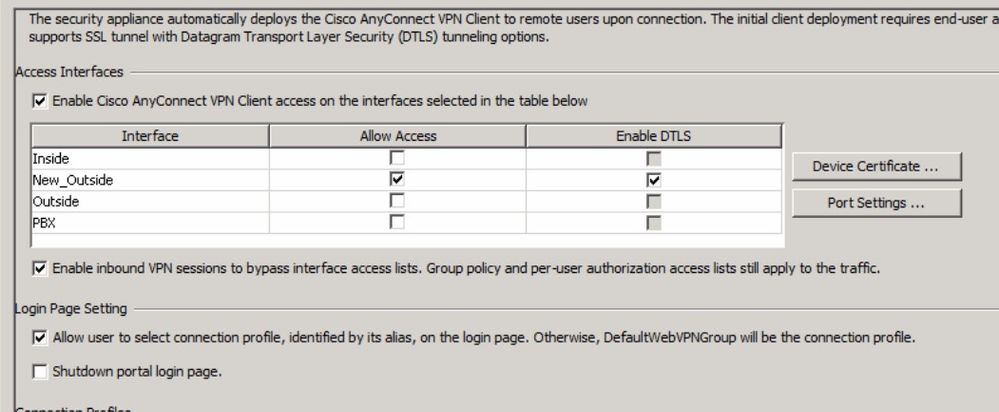
I received the error below when trying to add the nat (Inside) 0 access-list Inside_nat0_outbound
Result of the command: "nat (Inside) 0 access-list Inside_nat0_outbound"
ERROR: Access-list "Inside_nat0_outbound" does not exist
Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-17-2019 01:03 AM
Hello,
you might have inadvertently removed the access list. Re-add it (I would use the actual IP address rather than the alias, for clarity):
access-list Inside_nat0_outbound extended permit ip 192.168.10.0 255.255.255.0 10.10.1.0 255.255.255.0
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-17-2019 02:26 AM
I added the NAT but then I can't access either internal or internet......
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-17-2019 02:58 AM
Hello,
post the full current running configuration again, with the changes you have implemented.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community:
