- Cisco Community
- Technology and Support
- Networking
- Switching
- ASA5505 - The third VLAN on a base license
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-14-2013 08:57 AM - edited 03-07-2019 02:56 PM
According to this document (http://www.cisco.com/en/US/docs/security/asa/asa72/asdm52/user/guide/ifcs5505.html) I can make the third VLAN to initiate traffic in one direction as depicted in this diagram
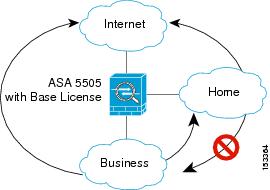
This means that although 'Home' cannot communicate with 'Business' I can still make 'Business' communicate with 'Home'. However I cannot make this work. I have configured the following routes:
C 192.168.1.0 255.255.255.0 is directly connected, Business
C 192.168.100.0 255.255.255.0 is directly connected, Home
C 200.135.171.201 255.255.255.240 is directly connected, Internet (changed IP for security reasons)
show config...
!
interface Vlan1
nameif Business
security-level 100
ip address 192.168.1.1 255.255.255.0
!
interface Vlan2
nameif Internet
security-level 0
ip address
200.135.171.201 255.255.255.240
!
interface Vlan12
no forward interface Vlan1
nameif Home
security-level 100
ip address 192.168.100.254 255.255.255.0
!
..
..
dns domain-lookup Business
dns domain-lookup Internet
dns server-group DefaultDNS
name-server 8.8.8.8
same-security-traffic permit inter-interface
same-security-traffic permit intra-interface
access-list outside_access_in extended permit ip any any
access-list dmz_access_in extended permit ip any any
pager lines 24
logging enable
logging asdm errors
mtu Business 1500
mtu Internet 1500
mtu Home 1500
ipv6 access-list dmz_access_ipv6_in permit ip any any
icmp unreachable rate-limit 1 burst-size 1
no asdm history enable
arp timeout 14400
global (Internet) 1 interface
nat (Business) 1 0.0.0.0 0.0.0.0
nat (Home) 1 0.0.0.0 0.0.0.0
access-group outside_access_in in interface Internet
route Internet 0.0.0.0 0.0.0.0 212.20.173.209
1
route Business 192.168.100.0 255.255.255.0 192.168.100.254 1
Business is the same VLAN where i have the management interface and is able to connect to the internet. Home can communicate to the internet as well. However I cannot get Business to communicate with Home. Some information from a node on the Business VLAN:
[root@localhost ~]# route -n
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
0.0.0.0 192.168.1.1 0.0.0.0 UG 0 0 0 eth0
192.168.1.0 0.0.0.0 255.255.255.0 U 0 0 0 eth0
[root@localhost ~]# ifconfig eth0
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.1.7 netmask 255.255.255.0 broadcast 192.168.1.255
inet6 fe80::a9e:1ff:fe1a:45d0 prefixlen 64 scopeid 0x20<link>
ether 08:9e:01:1a:45:d0 txqueuelen 1000 (Ethernet)
RX packets 32865 bytes 13844097 (13.2 MiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 54711 bytes 9025935 (8.6 MiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
Any ideas?
Solved! Go to Solution.
- Labels:
-
LAN Switching
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-16-2013 06:13 PM
first place this inspeciton policy then check
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum 512
policy-map global_policy
class inspection_default
inspect icmp
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect netbios
inspect rsh
inspect rtsp
inspect skinny
inspect esmtp
inspect sqlnet
inspect sunrpc
inspect tftp
inspect sip
inspect xdmcp
!
service-policy global_policy global
2nd one
What i am assuming
no nat (LAN) 0 access-list LAN-nat0
no nat (LAN) 1 0.0.0.0 0.0.0.0
will work one way only. If removing this work then it will be clearly so u have'nt tried my test.
Jawad
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-15-2013 11:46 PM
you must do nat 0 nat exempt rule and then try
access list Business-nat0 extended permit ip 192.168.1.0 255.255.255.0 192.168.100.0 255.255.255.0
nat (Business) 0 access-list Business-nat0
same for Home
access list Home-nat0 extended permit ip 192.168.100.0 255.255.255.0 192.168.1.0 255.255.255.0
nat (Home) 0 access-list Home-nat0
Jawad
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-16-2013 07:41 AM
I added the two exempt rules but did not fix the problem...
show conf:
..
access-list home-nat0 extended permit ip 192.168.100.0 255.255.255.0 192.168.1.0 255.255.255.0
access-list business-nat0 extended permit ip 192.168.1.0 255.255.255.0 192.168.100.0 255.255.255.0
..
nat (business) 0 access-list business-nat0
nat (business) 1 0.0.0.0 0.0.0.0
nat (home) 0 access-list home-nat0
nat (home) 1 0.0.0.0 0.0.0.0
..
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-16-2013 07:46 AM
also add this
nat (Business) 0 access-list Business-nat0
if still not working
post recent config....
Jawad
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-16-2013 07:50 AM
Updated previous post with latest show config.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-16-2013 08:06 AM
route Business 192.168.100.0 255.255.255.0 192.168.100.254 1
this route is not needed
and are u pinging iterface ip or host
ping host of other vlan
Jawad
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-16-2013 08:19 AM
I am trying to ping the hosts...
[root@localhost ~]# ifconfig
eth0: flags=4163
inet 192.168.1.7 netmask 255.255.255.0 broadcast 192.168.1.255
inet6 fe80::a9e:1ff:fe1a:45d0 prefixlen 64 scopeid 0x20
ether 08:9e:01:1a:45:d0 txqueuelen 1000 (Ethernet)
RX packets 20722 bytes 10508439 (10.0 MiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 19668 bytes 2757750 (2.6 MiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
[root@localhost ~]# ping 192.168.100.13
PING 192.168.100.13 (192.168.100.13) 56(84) bytes of data.
^C
--- 192.168.100.13 ping statistics ---
3 packets transmitted, 0 received, 100% packet loss, time 1999ms
[root@localhost ~]# ping 192.168.100.106
PING 192.168.100.106 (192.168.100.106) 56(84) bytes of data.
^C
--- 192.168.100.106 ping statistics ---
2 packets transmitted, 0 received, 100% packet loss, time 999ms
The firewall syslog messages is displaying portmap errors:
3 Aug 16 2013 16:26:31 192.168.100.13 22 portmap translation creation failed for tcp src mgmt:192.168.1.7/40418 dst LAN:192.168.100.13/22
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-16-2013 08:45 AM
I HAVE verfied it on my side on GNS it working with this config
kindly check name characters should be same which u mentioned under Interface
nat (Business) 0 access-list business-nat0
nat (Business) 1 0.0.0.0 0.0.0.0
nat (Home) 0 access-list home-nat0
nat (Home) 1 0.0.0.0 0.0.0.0
interface Ethernet0/0
nameif Business
security-level 100
ip address 192.168.1.1 255.255.255.0
!
interface Ethernet0/1
nameif Home
security-level 100
ip address 192.168.100.254 255.255.255.0
!
interface Ethernet0/2
shutdown
no nameif
no security-level
no ip address
!
interface Ethernet0/3
shutdown
nameif INTERNET
security-level 0
no ip address
!
interface Ethernet0/4
shutdown
no nameif
no security-level
no ip address
!
interface Ethernet0/5
shutdown
no nameif
no security-level
no ip address
!
passwd 2KFQnbNIdI.2KYOU encrypted
boot config disk0:/.private/startup-config
ftp mode passive
same-security-traffic permit inter-interface
same-security-traffic permit intra-interface
access-list home-nat0 extended permit ip 192.168.100.0 255.255.255.0 192.168.1.0 255.255.255.0
access-list business-nat0 extended permit ip 192.168.1.0 255.255.255.0 192.168.100.0 255.255.255.0
access-list outside_access_in extended permit ip any any
access-list dmz_access_in extended permit ip any any
pager lines 24
no logging message 402128
mtu Business 1500
mtu Home 1500
mtu INTERNET 1500
no failover
icmp unreachable rate-limit 1 burst-size 1
no asdm history enable
arp timeout 14400
global (INTERNET) 1 interface
nat (Business) 0 access-list business-nat0
nat (Business) 1 0.0.0.0 0.0.0.0
nat (Home) 0 access-list home-nat0
nat (Home) 1 0.0.0.0 0.0.0.0
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout uauth 0:05:00 absolute
dynamic-access-policy-record DfltAccessPolicy
http server enable
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart
no crypto isakmp nat-traversal
telnet timeout 5
ssh timeout 5
console timeout 0
threat-detection basic-threat
threat-detection statistics access-list
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum 512
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect netbios
inspect rsh
inspect rtsp
inspect skinny
inspect esmtp
inspect sqlnet
inspect sunrpc
inspect tftp
inspect sip
inspect xdmcp
!
service-policy global_policy global
prompt hostname context
Cryptochecksum:07ff3d35209eb408587278c7e51f7756
: end
ciscoasa#
ciscoasa#
ciscoasa# show run
: Saved
:
ASA Version 8.0(2)
!
hostname ciscoasa
enable password 8Ry2YjIyt7RRXU24 encrypted
names
!
interface Ethernet0/0
nameif Business
security-level 100
ip address 192.168.1.1 255.255.255.0
!
interface Ethernet0/1
nameif Home
security-level 100
ip address 192.168.100.254 255.255.255.0
!
interface Ethernet0/2
shutdown
no nameif
no security-level
no ip address
!
interface Ethernet0/3
shutdown
nameif INTERNET
security-level 0
no ip address
!
interface Ethernet0/4
shutdown
no nameif
no security-level
no ip address
!
interface Ethernet0/5
shutdown
no nameif
no security-level
no ip address
!
passwd 2KFQnbNIdI.2KYOU encrypted
boot config disk0:/.private/startup-config
ftp mode passive
same-security-traffic permit inter-interface
same-security-traffic permit intra-interface
access-list home-nat0 extended permit ip 192.168.100.0 255.255.255.0 192.168.1.0 255.255.255.0
access-list business-nat0 extended permit ip 192.168.1.0 255.255.255.0 192.168.100.0 255.255.255.0
access-list outside_access_in extended permit ip any any
access-list dmz_access_in extended permit ip any any
pager lines 24
no logging message 402128
mtu Business 1500
mtu Home 1500
mtu INTERNET 1500
no failover
icmp unreachable rate-limit 1 burst-size 1
no asdm history enable
arp timeout 14400
global (INTERNET) 1 interface
nat (Business) 0 access-list business-nat0
nat (Business) 1 0.0.0.0 0.0.0.0
nat (Home) 0 access-list home-nat0
nat (Home) 1 0.0.0.0 0.0.0.0
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout uauth 0:05:00 absolute
dynamic-access-policy-record DfltAccessPolicy
http server enable
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart
no crypto isakmp nat-traversal
telnet timeout 5
ssh timeout 5
console timeout 0
threat-detection basic-threat
threat-detection statistics access-list
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum 512
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect netbios
inspect rsh
inspect rtsp
inspect skinny
inspect esmtp
inspect sqlnet
inspect sunrpc
inspect tftp
inspect sip
inspect xdmcp
!
service-policy global_policy global
prompt hostname context
Cryptochecksum:07ff3d35209eb408587278c7e51f7756
Jawad
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-16-2013 08:47 AM
connect Windows PC sometimes i feel same issue with linux not able to ping remote server need to restart linux
Jawad
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-16-2013 08:51 AM
Post you whole config
check your vlans are under accurate interfaces
check vlan 192.168.1.x can ping its gateway 192.168.1.1
check vlan 192.168.100.x can ping its gateway 192.168.100.254
Jawad
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-16-2013 09:05 AM
Both VLANs can connect to their own gateways. I recreated the setup from scratch just to be sure but I'm still in the same situation. Here's the whole conf:
Result of the command: "show conf"
: Saved
: Written by james at 17:39:37.084 CEDT Fri Aug 16 2013
!
ASA Version 8.2(5)
!
hostname testasa
enable password xxx encrypted
passwd xxx.xxx encrypted
names
!
interface Ethernet0/0
switchport access vlan 2
!
interface Ethernet0/1
switchport access vlan 12
!
interface Ethernet0/2
switchport access vlan 12
!
interface Ethernet0/3
switchport access vlan 12
!
interface Ethernet0/4
switchport access vlan 12
!
interface Ethernet0/5
switchport access vlan 12
!
interface Ethernet0/6
!
interface Ethernet0/7
!
interface Vlan1
nameif mgmt
security-level 100
ip address 192.168.1.1 255.255.255.0
!
interface Vlan2
nameif Internet
security-level 0
ip address 212.20.173.209 255.255.255.240
!
interface Vlan12
no forward interface Vlan1
nameif LAN
security-level 100
ip address 192.168.100.254 255.255.255.0
!
ftp mode passive
clock timezone CEST 1
clock summer-time CEDT recurring last Sun Mar 2:00 last Sun Oct 3:00
dns domain-lookup mgmt
dns domain-lookup Internet
dns server-group DefaultDNS
name-server 8.8.8.8
same-security-traffic permit inter-interface
same-security-traffic permit intra-interface
access-list outside_access_in extended permit ip any any
access-list dmz_access_in extended permit ip any any
access-list LAN-nat0 extended permit ip 192.168.100.0 255.255.255.0 192.168.1.0 255.255.255.0
access-list LAN-nat0 extended permit ip 10.250.0.0 255.255.0.0 any
access-list LAN-nat0 extended permit ip 192.168.100.0 255.255.255.0 192.168.100.0 255.255.255.128
access-list mgmt-nat0 extended permit ip 192.168.1.0 255.255.255.0 192.168.100.0 255.255.255.0
access-list mgmt-nat0 extended permit ip 10.250.0.0 255.255.0.0 any
pager lines 24
logging enable
logging asdm errors
mtu mgmt 1500
mtu Internet 1500
mtu LAN 1500
ipv6 access-list dmz_access_ipv6_in permit ip any any
icmp unreachable rate-limit 1 burst-size 1
no asdm history enable
arp timeout 14400
global (Internet) 1 interface
nat (mgmt) 0 access-list mgmt-nat0
nat (mgmt) 1 0.0.0.0 0.0.0.0
nat (LAN) 0 access-list LAN-nat0
nat (LAN) 1 0.0.0.0 0.0.0.0
access-group outside_access_in in interface Internet
route Internet 0.0.0.0 0.0.0.0 212.20.173.209 1
route mgmt 192.168.100.0 255.255.255.0 192.168.100.254 1
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
dynamic-access-policy-record DfltAccessPolicy
http server enable
http 192.168.1.0 255.255.255.0 mgmt
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart
telnet timeout 5
ssh timeout 5
console timeout 0
dhcpd auto_config Internet
dhcpd update dns both override
!
dhcpd address 192.168.1.5-192.168.1.132 mgmt
dhcpd dns 8.8.8.8 interface mgmt
dhcpd enable mgmt
!
dhcpd address 192.168.100.50-192.168.100.60 LAN
dhcpd dns 8.8.8.8 interface LAN
dhcpd update dns both override interface LAN
dhcpd enable LAN
!
threat-detection basic-threat
threat-detection statistics access-list
threat-detection statistics tcp-intercept rate-interval 30 burst-rate 400 average-rate 200
!
!
prompt hostname context
no call-home reporting anonymous
Cryptochecksum:xxx
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-16-2013 09:41 AM
Post result of
show switch vlan
show switch vlan
show switch vlan
show switch vlan
Jawad
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-16-2013 10:15 AM
Result of the command: "show switch vlan"
VLAN Name Status Ports
---- -------------------------------- --------- -----------------------------
1 mgmt up Et0/6, Et0/7
2 Internet up Et0/0
12 LAN up Et0/1, Et0/2, Et0/3, Et0/4
Et0/5
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-16-2013 11:51 AM
Lastly
Verify bohat host IP's their gateway must be FW mgmt and LAN interface IP's
r u still recieving that error
portmap translation creation failed for tcp src mgmt:192.168.1.7/40418 dst LAN:192.168.100.13/22
remote nat and then check
no global (Internet) 1 interface
no nat (mgmt) 0 access-list mgmt-nat0
no nat (mgmt) 1 0.0.0.0 0.0.0.0
no nat (LAN) 0 access-list LAN-nat0
no nat (LAN) 1 0.0.0.0 0.0.0.0
Jawad
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-16-2013 01:59 PM
But if on both interfaces I can access the Internet, I cannot understand why I cannot access the other VLAN...
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community:
