- Cisco Community
- Technology and Support
- Networking
- Switching
- Re: Catalyst 3750 E slow ping response
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Catalyst 3750 E slow ping response
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-10-2018 03:44 PM - edited 03-08-2019 04:21 PM
I'm not sure if this is expected behaviour or not. I discovered this while troubleshooting an intermittent network issue which I still haven't solved. Until it is solved, anything is suspect and this behaviour seems odd to me. Is there something wrong here, or this this just how the switches work?
We have offices on both sides of the street, the south side subnet is connected to the north side subnet via radio link (600Mbps full duplex). Routing is done on our layer 3 switches (Catalyst 3750E-48TD-S running ipbasek9 IOS 12.2(55)SE12). Each subnet (South and North) have a Netgear firewall/router to connect to the outside world. The equipment on each side of the street has identical configs to their counterparts on the other side (except for which subnet each one belongs to).
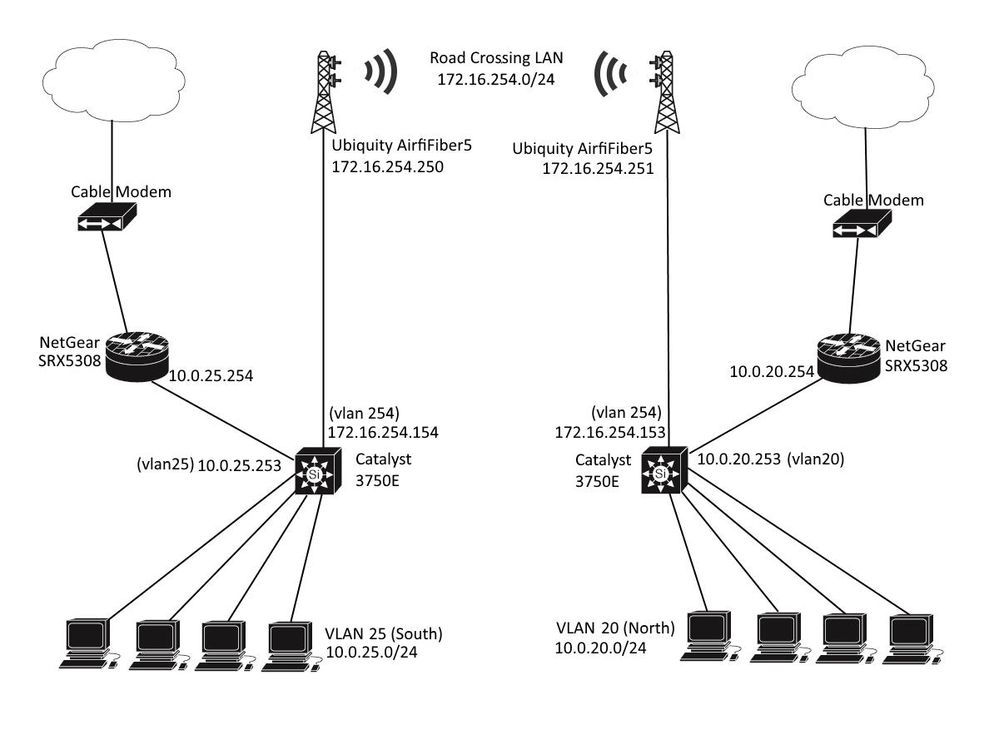
First strange behaviour:
The catalyst 3750Es seem to have a network datagram size limit only on traffic within the local subnets. For instance, from the south side 3750E the biggest ping packet I can send to any host in vlan 25 is 5940 bytes. Anything 5941 or bigger does not make it back. similarly pinging from a host withing vlan 25, the biggest packet that is returned from the South side 3750E is 5912 Bytes. But from any host in vlan 25, including from the South 3750E, I can use significantly larger packets to successfully ping hosts on the other side of the street, including to the North side 3750E.
Second Strange behaviour:
Pings to the Catalyst switches take longer to return than pings to the netgear routers or to Windows hosts. For example, from a windows host on the south side sending 6912 byte ping packets to windows hosts or netgear router on the other side of the road takes on average 1ms but pinging the North side Catalyst switch with the same size packet takes on average 6ms.
Third Strange behaviour
Pinging from any host on the south side of the road to any windows or netgear host on the other side works well up to maximumum packet size of about 6900. Anything over 7000 bytes starts dropping progressively more packets until 8000 bytes where about 90% of packets are lost. But I can ping from Catalyst switch to catalyst switch across the road using the largest supported packet size of 18024 bytes with no losses. I suppose this could be explained by the fact that pinging from windows hosts on side of the road to the other involves routing but pinging from the catalyst to the other catalyst on the other side of the road is not routed. But if I do (from the North side switch) ping 10.0.25.253 repeat 10 size 18024 Source 10.0.20.253, does not that involve routing, to get from the 20. subnet to the road crossing subnet?
Here is config from the south side switch:
! ! Last configuration change at 14:35:22 PDT Sun Apr 22 2018 by bleuze ! NVRAM config last updated at 09:07:01 PDT Mon Apr 23 2018 by bleuze ! version 12.2 no service pad service timestamps debug datetime localtime show-timezone service timestamps log datetime localtime show-timezone service password-encryption ! hostname sw-stone-rtr ! boot-start-marker boot-end-marker ! enable secret 5 $1$52Ab$2XZoY3kXCaLJOUDqRPFW21 ! username bill privilege 15 secret 5 $1$.ja3$6lidw202ZzIAo4u2PsNDV0 username admin privilege 15 secret 5 $1$YboL$AF31tx51SR9kmGMIay3w6. username bleuze privilege 15 secret 5 $1$o5Ck$rhxvt2KYFqxEjlZRHAY3j/ ! ! no aaa new-model clock timezone PST -8 clock summer-time PDT recurring switch 1 provision ws-c3750e-48td system mtu routing 1500 ip routing ! ! no ip domain-lookup ip domain-name colonial.local ip host tftpd 172.16.254.30 ip host ccv-vCenter 172.16.254.30 vtp mode transparent ! ! crypto pki trustpoint TP-self-signed-1885815168 enrollment selfsigned subject-name cn=IOS-Self-Signed-Certificate-1885815168 revocation-check none rsakeypair TP-self-signed-1885815168 ! ! crypto pki certificate chain TP-self-signed-1885815168 certificate self-signed 01 nvram:IOS-Self-Sig#3838.cer archive path tftp://172.16.254.30/sw-stone-rtr/$h-$t write-memory ! spanning-tree mode rapid-pvst spanning-tree portfast default spanning-tree portfast bpduguard default spanning-tree extend system-id ! ! ! errdisable recovery cause bpduguard errdisable recovery interval 360 ! vlan internal allocation policy ascending ! vlan 20 name CCV-Lam ! vlan 25 name CCV-Stone ! vlan 254 name Management ! vlan 500 name Voice ! ! ! interface FastEthernet0 no ip address no ip route-cache cef no ip route-cache no ip mroute-cache shutdown ! interface GigabitEthernet1/0/1 description stone users switchport access vlan 25 switchport mode access ! ! identical interfaces lines removed for brevity... ! interface GigabitEthernet1/0/41 description stone users switchport access vlan 25 switchport mode access ! interface GigabitEthernet1/0/42 description VMware ADD Port2 switchport access vlan 254 switchport mode access ! interface GigabitEthernet1/0/43 description ccv-vCenter mgmt switchport access vlan 254 switchport trunk native vlan 25 ! interface GigabitEthernet1/0/44 description Stone Router switchport access vlan 254 switchport mode access ! interface GigabitEthernet1/0/45 description mgmt port switchport access vlan 254 switchport mode access ! interface GigabitEthernet1/0/46 description stone shop switchport access vlan 25 switchport mode access ! interface GigabitEthernet1/0/47 description Road Xing switchport trunk encapsulation dot1q switchport trunk native vlan 254 switchport mode trunk ! interface GigabitEthernet1/0/48 description to router switchport access vlan 25 switchport mode access ! interface GigabitEthernet1/0/49 ! interface GigabitEthernet1/0/50 ! interface GigabitEthernet1/0/51 ! interface GigabitEthernet1/0/52 ! interface TenGigabitEthernet1/0/1 ! interface TenGigabitEthernet1/0/2 ! interface Vlan1 no ip address shutdown ! interface Vlan20 no ip address ! interface Vlan25 ip address 10.0.25.253 255.255.255.0 ! interface Vlan254 ip address 172.16.254.154 255.255.255.0 ! ip default-gateway 10.0.25.254 ip classless ip route 0.0.0.0 0.0.0.0 10.0.25.254 ip route 10.0.20.0 255.255.255.0 172.16.254.153 no ip http server ip http secure-server ! ! vstack alias exec start-tftp copy startup-config tftp://172.16.254.30/sw-stone-rtr.cfg ! line con 0 exec-timeout 0 0 logging synchronous line vty 0 4 exec-timeout 120 0 login local transport input all line vty 5 15 exec-timeout 30 0 login local transport input all ! ntp clock-period 36029663 ntp server 10.0.20.55 end
- Labels:
-
Other Switches
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-04-2018 11:54 AM
Hi
I share an interesting link regardin MTU on 37xx devices. You can try to enable jumbo frames. Also for traffic between hosts in vlan 25 to hosts in vlan 20 you can test the MTU that Ubiquitys are configured for.
// Cisco Catalyst 3750/3560 Series Switches - Jumbo/Giant Frame Support Configuration
https://support.hpe.com/hpsc/doc/public/display?docId=c03331307
BR
Gaston
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-05-2018 05:37 AM
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide
