- Cisco Community
- Technology and Support
- Networking
- Switching
- Re: Cisco router can't ping to ASA
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-05-2023 02:37 PM
Hi All,
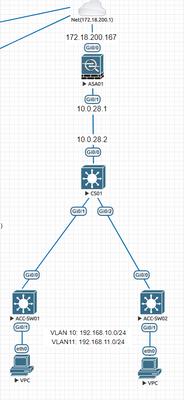
Im trying to create a simple network consisting of an ASA and Core Switch. I can ping outside IP from the ASA firewall, but i can't ping it through the core switch. Is there any configuration that i've missed out?
Here is my configuration:
ASA:
hostname ASA01
enable password ***** pbkdf2
names
no mac-address auto
!
interface GigabitEthernet0/0
nameif OUTSIDE
security-level 0
ip address 172.18.200.167 255.255.255.0
!
interface GigabitEthernet0/1
nameif INSIDE
security-level 100
ip address 10.0.28.1 255.255.255.0
!
interface GigabitEthernet0/2
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet0/3
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet0/4
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet0/5
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet0/6
shutdown
no nameif
no security-level
no ip address
!
interface Management0/0
no nameif
security-level 100
ip address 10.1.50.5 255.255.255.0
!
ftp mode passive
dns domain-lookup OUTSIDE
dns server-group DNS
name-server 1.1.1.1
name-server 1.0.0.1
object network obj_any
subnet 0.0.0.0 0.0.0.0
object network outside
subnet 172.18.200.0 255.255.255.0
object network inside
subnet 10.0.28.0 255.255.255.0
object network LAN
subnet 192.168.0.0 255.255.0.0
pager lines 23
mtu OUTSIDE 1500
mtu INSIDE 1500
no failover
icmp unreachable rate-limit 1 burst-size 1
icmp permit any OUTSIDE
icmp permit any INSIDE
no asdm history enable
arp timeout 14400
no arp permit-nonconnected
arp rate-limit 8192
!
nat (INSIDE,OUTSIDE) after-auto source dynamic any interface
route OUTSIDE 0.0.0.0 0.0.0.0 172.18.200.1 1
route INSIDE 192.168.10.0 255.255.255.0 10.0.28.2 1
route INSIDE 192.168.11.0 255.255.255.0 10.0.28.2 1
timeout xlate 3:00:00
timeout pat-xlate 0:00:30
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
timeout conn-holddown 0:00:15
timeout igp stale-route 0:01:10
user-identity default-domain LOCAL
aaa authentication login-history
no snmp-server location
no snmp-server contact
no validation-usage
crl configure
crypto ca trustpool policy
auto-import
ssh stricthostkeycheck
ssh timeout 5
console timeout 0
console serial
threat-detection basic-threat
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
dynamic-access-policy-record DfltAccessPolicy
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum client auto
message-length maximum 512
no tcp-inspection
policy-map global_policy
class inspection_default
inspect ip-options
inspect netbios
inspect rtsp
inspect sunrpc
inspect tftp
inspect xdmcp
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect esmtp
inspect sqlnet
inspect sip
inspect skinny
policy-map type inspect dns migrated_dns_map_2
parameters
message-length maximum client auto
message-length maximum 512
no tcp-inspection
policy-map type inspect dns migrated_dns_map_1
parameters
message-length maximum client auto
message-length maximum 512
no tcp-inspection
!
service-policy global_policy global
prompt hostname context
no call-home reporting anonymous
call-home
profile License
: end
CORE SWITCH:
hostname CS01
!
boot-start-marker
boot-end-marker
!
!
!
no aaa new-model
!
!
!
!
!
!
ip dhcp excluded-address 192.168.10.1 192.168.10.20
ip dhcp excluded-address 192.168.11.1 192.168.11.20
!
ip dhcp pool VLAN10
network 192.168.10.0 255.255.255.0
default-router 192.168.10.1
dns-server 1.0.0.1
lease 0 8
!
ip dhcp pool VLAN11
network 192.168.11.0 255.255.255.0
default-router 192.168.11.1
dns-server 1.0.0.1
lease 0 8
!
!
no ip domain-lookup
ip cef
no ipv6 cef
!
!
!
spanning-tree mode pvst
spanning-tree extend system-id
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
interface GigabitEthernet0/0
no switchport
ip address 10.0.28.2 255.255.255.0
negotiation auto
!
interface GigabitEthernet0/1
negotiation auto
!
interface GigabitEthernet0/2
negotiation auto
!
interface GigabitEthernet0/3
negotiation auto
!
interface GigabitEthernet1/0
negotiation auto
!
interface GigabitEthernet1/1
negotiation auto
!
interface GigabitEthernet1/2
negotiation auto
!
interface GigabitEthernet1/3
negotiation auto
!
interface Vlan10
ip address 192.168.10.1 255.255.255.0
!
interface Vlan11
ip address 192.168.11.1 255.255.255.0
!
interface Vlan600
ip address 10.1.50.6 255.255.255.0
!
ip default-gateway 10.0.28.1
ip forward-protocol nd
!
ip http server
ip http secure-server
!
ip route 0.0.0.0 0.0.0.0 10.0.28.1
ip ssh server algorithm encryption aes128-ctr aes192-ctr aes256-ctr
ip ssh client algorithm encryption aes128-ctr aes192-ctr aes256-ctr
!
I hope someone can help me fix this issue.
Thank you.
Solved! Go to Solution.
- Labels:
-
Branch Router
-
LAN Switching
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-05-2023 02:43 PM
inspection icmp <<- this need to config under policy-map/inspection-default
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-05-2023 02:43 PM
inspection icmp <<- this need to config under policy-map/inspection-default
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-13-2023 06:17 PM
I already fixed the issue with the devices. Thanks a lot!
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: