- Cisco Community
- Technology and Support
- Networking
- Switching
- Re: Connect 2 3560Gs to be "one"
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Connect 2 3560Gs to be "one"
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-29-2013 10:07 PM - edited 03-07-2019 02:39 PM
Hello to All,
I'm really having difficulty trying to find an solution to what seems to be an easy task - probably that's because I really didn't have any formal networking training, yet I've been assigned to complete such networking task. I hope our good friends here can give us some advice how to:
1. Connect two 3560Gs to be "one"
2. Provide instructions how to go about doing this.
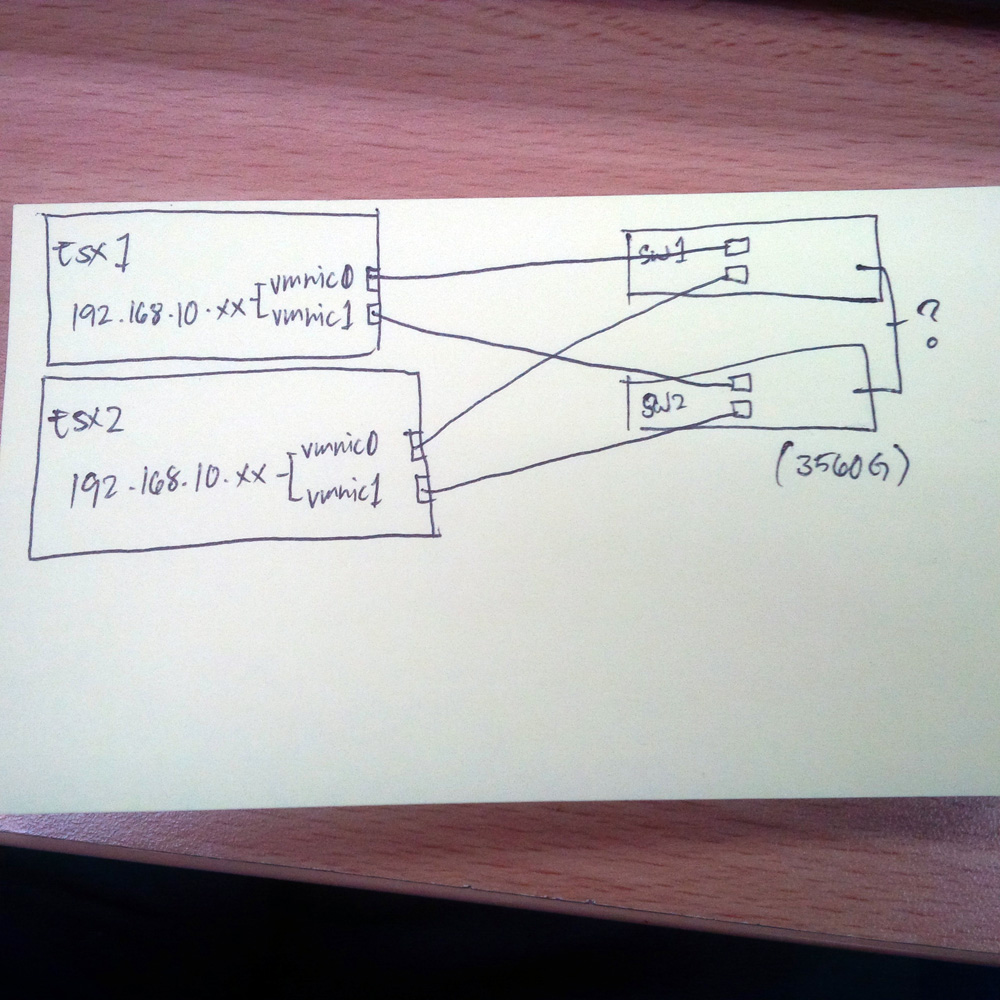
Basically what I'm trying to do is connect 2 ESX hosts, each with 2 ethernet ports available - which are teamed in a standard vSwitch (one IP per team), that will connect to the two 3560G switches. These connections will be the connections to the datastore, and by having 2 switches we try to get switch level redundancy. Hopefully the punny diagram attached would help explain what i'm trying to say.
Please help!
- Labels:
-
Other Switching
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-30-2013 01:07 AM
Hi Edwin, the 3560G series switch cannot be stacked, so cannot be connected as 'one', as you say. The 3750G series switch is the equivalent 'stackable' version of the 3560G. Both are now End-of-Life.
If you were to link your pair of 3560G switches together (as illustrated with the ? link) and you were to configure this as a layer-2 link that spans VLANs between the switches (as opposed to a layer-3 routed link), then you will create a layer-2 loop. This is bad. So you must rely on Spanning Tree Protocol to actively block one uplink for you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-30-2013 01:38 AM
Thank you for the feedback, Shillings. We are in the business of selling storage solutions, and setting them up for our customers. But for some reason, we had to take this task of setting up these switches, from scratch, for one particular client (and these are the only switches we can use). I would say that it's not in our JD to configure switches day in and out, but after taking up this challenge, having to know how to configure them (basic), I would say it caught my fancy and I'm interested to learn more of the network side of infra.
However, my deadline is fast approaching. That goes to say I don't have the luxury of time to master the foundation, and then catch up with what I need to do here. I understand that the setup illustrated above will cause L2 loop, and that i'll have to make sure STP is in place. Unfotunately, they are all theories in my head which doesn't conjure to the actual config that I can put in switch.
For now, I'm required to do whatever it takes to get this setup to work. I would really appreciate it if someone would spare some of their precious time to paste in here the config for those 4ports on the switch (and SFP if needed).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-30-2013 01:57 AM
I understand Edwin.
Is this a live customer site? If so, what would happen if you take down the customer's entire network due to Spanning Tree misconfiguration? Whilst it's all basic networking, there is always the potential to cause a lot of damage. Is it worth the risk? Is it worth losing this customer? How will you feel when all eyes are looking at you to fix it? How will you feel when the customer is frantic with worry (or worse) due to loss of business. Perhaps hiring a reputable CCNP contractor for the day is money well spent. You can lean over his/her shoulder and learn, without risk. Sorry, I know it's not the answer you wanted.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-30-2013 02:27 AM
@ Shillings - totally understand what you mean, and I agree. But, it's not my call.
Any other option?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-30-2013 02:35 AM
Swapping the 3560Gs for a pair of stacked 3750s will make your life easier.
If that's not feasible, and you need help with configuration, then I'll have to bow out at this point.
I hope it all works out well.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-30-2013 02:47 AM
We are in the business of selling storage solutions, and setting them up for our customers.
Can I say something?
If you are indeed going to connect ESX storage to 3560/3750/3850 then DON'T. The continuous bandwidth required by the servers cannot be guaranteed by the 3560/3750/3850 series switches.
If you want a hit-less solution, you should be looking at the Nexus 5K/6K, as end-of-row, and Nexus 2K as top-of-rack.
Nice posts, Simon!
& Rated!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-30-2013 05:49 AM
From working with Vmware and Network Infrastructure, I'll give you the following advise
1) You can't stack 3560Gs, and they shouldn't be used in a Vmware environment (you can but I wouldn't do it)
2) As a previous post suggested go with a 2960-s or 3750X series. I would just configure it with a native vlan, and have those switches ONLY connected to the Hosts/SAN. Remember the data is ONLY going to come FROM the ESXi/ESX hosts and the SAN. You will configure additional LAN ports on each HOST for LAN ports, which should go to a different switch.
3) Configure Jumbo Frames (9000+ MTU) between your hosts and SAN, and make sure the SAN, Servers(ESX/ESXi hosts) support it, and switch. MAKE SURE, everyone in between is set at Jumbo frames and the SAME exact MTU.
4) You can also include specific LAN features, as flow-control etc.
5) Also, if you can, I recommend using 10gig fiber uplinks. Remember, between ESX/ESXi and your SAN enviornment, Faster is ALWAYS better if it's supported and configured correctly.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-30-2013 05:54 AM
John,
A question:
I would just configure it with a native vlan
For security and stability reasons, it is recommended to avoid using VLAN1 and the native VLAN. Would you personally agree to use a different VLAN for the attached devices, leaving the VLAN1 alone?
Best regards,
Peter
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-30-2013 09:16 AM
Peter, think of it this way. You have let's say 2 2960-s, stacked for redundancy, for the sole purpose of SAN switching. So this stack of two 2960-s, will be put in the middle, between a SAN, and let's say 4 ESXi hosts. For this example, let's say, two ports are used for SAN traffic on the ESXi hosts, with each port going to a different 2960-s. From there, there are let's say multiple connections to the SAN, depending on Active/Passive, Active/Active, and how many ports the SAN has.
The only two devices physically touching these 2960-s switches, are the SAN and hosts. Both ends will be configured as access links so to speak, and no trunking.
I've read numerous articles, about vlan hopping not working. I've read one from the head guy at packetlife, and several other people.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-30-2013 09:25 AM
Hi John,
I've read numerous articles, about vlan hopping not working. I've read one from the head guy at packetlife, and several other people.
With 2950 and 3550, I can do VLAN hopping at will. Trust me - done that many times. With 2960 and 3560 (and I suppose 3750 as well), I admit, it is not possible out of the box because on these platforms, you have to allow a voice VLAN (doesn't matter which) on the switchport to allow it to process tagged frames even in access mode. Though not relevant to this particular setup, as soon as you configure a voice VLAN on a 2960/3560/3750 access port, I can do VLAN hopping again instantly. I do this routinely on my CCNP:SWITCH trainings So rather than speculate when the VLAN hopping works and when it does not, better stay away from VLAN 1 for good.
I have another reason to leave VLAN1 on its own - the fact that many inter-switch protocols are carried in VLAN1, I consider it better to isolate stations from VLAN1.
What would be your opinion?
Best regards,
Peter
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-30-2013 09:49 AM
Should I cry uncle now or later?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-30-2013 10:27 AM
John,
You know what thay say... "We are Borg. We will add your biological and technological distinctiveness to our own. Resistance is futile!"
Best regards,
Peter
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-30-2013 07:19 PM
@Leo, JTP, and Peter - Thank you very much for your input! I will sure consider all of the points you've laid out here if I come across such project again.
But for now, as I scratch my head, I still need to make do with what's given. BTW, their environment is quite small and forgiving on the network bandwith, 10VMs running at most that aren't so noisy.
Any last minute help with the config would be really appreciated!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-30-2013 08:01 PM
10VMs running at most that aren't so noisy.
It's got nothing to do with "noise" from the machine. It's the amount of SUSTAINED throughput required by each VM server which can overflow the buffer of a Catalyst switch like the 2960S/X, 3560G/X, 3750G/X or 3850.
Think of it as drinking water from a fire hydrant. You'll see alot of output drops and there's nothing you can do about it unless you consider the Nexus strategy.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community:

