- Cisco Community
- Technology and Support
- Networking
- Switching
- Re: Help on configuration of PBR on Cisco 3850 Switch
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-03-2018 11:13 PM - edited 03-08-2019 01:42 PM
Hello Community,
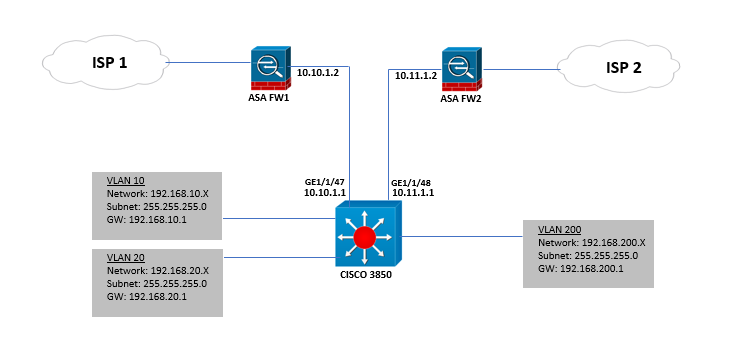
We have this network design:
Could you please help me how to configure PBR on our Cisco 3850 switch.
We have VLANs 10 and 20 and added a Guest Wifi network on VLAN 200. Also we have two ISP and two firewalls. Right now all traffic to internet is routed on ISP1 and works well.
We need to achieve the following:
- VLAN 10 and 20 traffic going to internet should utilize the ISP1.
- VLAN 200 traffic going to internet should utilize the ISP2.
Thank you in advance.
Solved! Go to Solution.
- Labels:
-
Other Switching
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-14-2018 12:33 PM
Thanks for this information. What version of code is this 3850 running?
In looking at the release notes it appears that the implementation of PBR for the 3850 is not full featured in comparison to IOS routers. I wonder if it would make any difference if you remove the parameters for verify-availability and for track from your route ma.
HTH
Rick
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-04-2018 12:10 AM
Hello,
provided you have at least IPBase installed on the switch, the below should work:
access-list 101 permit ip 192.168.10.x 0.0.0.255 any
access-list 101 permit ip 192.168.20.x 0.0.0.255 any
!
access-list 102 permit ip 192.168.200.x 0.0.0.255 any
!
route-map _TO_ISP_1 permit 10
match ip address 101
set ip next-hop 10.10.1.1
!
route-map _TO_ISP_1 permit 20
!
route-map _TO_ISP_2 permit 10
match ip address 102
set ip next-hop 10.11.1.1
!
route-map _TO_ISP_2 permit 20
!
interface Vlan10
ip policy route-map TO_ISP_1
!
interface Vlan20
ip policy route-map TO_ISP_1
!
interface Vlan200
ip policy route-map TO_ISP_2
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-04-2018 12:16 AM - edited 02-04-2018 12:20 AM
Hello
As the default is ISP1 then you just need to PBR towards ISP2 for vlan 200 and apply some sla tracking in case ISP2 becomes unreachable otherwise you may blackhole vlan 200 traffic.
ip sla 5
icmp-echo 10.11.1.2 source 10.11.1.1
ip sla schedule 5 life forever start-time now
track 10 sla 5 reachability
access-list 100 permit ip 192.168.200.0 0.0.0.255
route-map PBR
match ip address 100
set ip next-hop verify-availability 10.11.1.2 1 track 10
int vlan 200
ip policy route-map PBR
res
Paul
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-10-2018 08:03 AM - edited 02-10-2018 08:25 AM
Hi Paul,
Thank you for helping and the commands provided.
I tried the commands and how can I verify on the core switch that the internet traffic from VLAN 200 is going to my ISP 2?
Thank you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-10-2018 10:43 AM
Hello,
the command 'show route-map' should show you if packets are policy routed...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-10-2018 09:09 PM - edited 02-10-2018 09:21 PM
Thanks Georg.
Some users are on VLAN 200 and accessing the internet and I check with the commands but it showing no packets:
C3850-Core-SW#show route-map
route-map PBR, permit, sequence 10
Match clauses:
ip address (access-lists): 100
Set clauses:
ip next-hop verify-availability 10.11.1.2 1 track 10 [up]
Policy routing matches: 0 packets, 0 bytes
By the way, i have a static route to ISP 1
0.0.0.0 0.0.0.0 10.10.1.2
Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-11-2018 02:12 AM
Hello
Hum....
from the core switch traceroute to the internet 8.8.8.8 sourced from vlan 200
seew hat parth it takes - also check your acces-list
res
paul
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-11-2018 08:53 AM
Hi Paul,
Why the traceroute results shows like this?
C3850-Core-SW#tRaceroute
Protocol [ip]:
Target IP address: 8.8.8.8
Source address: 192.168.200.1
Numeric display [n]:
Timeout in seconds [3]:
Probe count [3]:
Minimum Time to Live [1]:
Maximum Time to Live [30]:
Port Number [33434]:
Loose, Strict, Record, Timestamp, Verbose[none]:
Type escape sequence to abort.
Tracing the route to 8.8.8.8
VRF info: (vrf in name/id, vrf out name/id)
1 * * *
2 * * *
3 * * *
4 * * *
5 * * *
6 * * *
7 * * *
8 * * *
9 * * *
10 * * *
11 * * *
12 * * *
13 * * *
14 * * *
15 * * *
16 * * *
17 * * *
18 * * *
19 * * *
20 * * *
21 * * *
22 * * *
23 * * *
24 * * *
25 * * *
26 * * *
27 * * *
28 * * *
29 * * *
30 * * *
C3850-Core-SW#
For the access-list:
C3850-Core-SW#sh access-lists
Extended IP access list 100
10 permit ip 192.168.200.0 0.0.0.255 any
Extended IP access list CISCO-CWA-URL-REDIRECT-ACL
100 deny udp any any eq domain
101 deny tcp any any eq domain
102 deny udp any eq bootps any
103 deny udp any any eq bootpc
104 deny udp any eq bootpc any
105 permit tcp any any eq www
Extended IP access list preauth_ipv4_acl (per-user)
10 permit udp any any eq domain
20 permit tcp any any eq domain
30 permit udp any eq bootps any
40 permit udp any any eq bootpc
50 permit udp any eq bootpc any
60 deny ip any any
IPv6 access list preauth_ipv6_acl (per-user)
permit udp any any eq domain sequence 10
permit tcp any any eq domain sequence 20
permit icmp any any nd-ns sequence 30
permit icmp any any nd-na sequence 40
permit icmp any any router-solicitation sequence 50
permit icmp any any router-advertisement sequence 60
permit icmp any any redirect sequence 70
permit udp any eq 547 any eq 546 sequence 80
permit udp any eq 546 any eq 547 sequence 90
deny ipv6 any any sequence 100
C3850-Core-SW#
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-11-2018 09:31 AM
1) traffic isn’t getting it next hop of isp2 so it sounds like normal rib routing is taking place
2) can you ping your isp2 next hop for the core switch
3) have you applied the route- map to vlan 200 svi correctly
Res
Paul
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-11-2018 11:04 AM - edited 02-11-2018 11:13 AM
Hi Paul,
I can ping the next hop 10.11.1.2 from Core switch.
C3850-Core-SW#ping 10.11.1.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.11.1.2, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
C3850-Core-SW#
Also I have this configuration PBR route-map to VLAN 200:
ip sla 5
icmp-echo 10.11.1.2 source-ip 10.11.1.1
ip sla schedule 5 life forever start-time now
access-list 100 permit ip 192.168.200.0 0.0.0.255 any
!
route-map PBR permit 10
match ip address 100
set ip next-hop verify-availability 10.11.1.2 1 track 10
!
interface vlan 200
ip policy route-map PBR
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-11-2018 11:09 AM
Do you have NAT enabled
Also try
oute-map PBR permit 10
match ip address 10
set ip next-hop 10.11.1.2
set ip next-hop verify-availability 10.11.1.2 1 track 10
!
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-11-2018 09:46 PM - edited 02-12-2018 09:19 AM
I can ping the source from int VLAN 200:
C3850-Core-SW#ping
Protocol [ip]:
Target IP address: 192.168.200.48
Repeat count [5]:
Datagram size [100]:
Timeout in seconds [2]:
Extended commands [n]: y
Source address or interface: 192.168.200.1
Type of service [0]:
Set DF bit in IP header? [no]:
Validate reply data? [no]:
Data pattern [0xABCD]:
Loose, Strict, Record, Timestamp, Verbose[none]:
Sweep range of sizes [n]:
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.200.48, timeout is 2 seconds:
Packet sent with a source address of 192.168.200.1
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/6/10 ms
C3850-Core-SW#
NAT is not enabled on switch.
I tried the commands but still same result.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-12-2018 07:00 AM - edited 02-12-2018 09:32 AM
Hello,
The packets that are generate from the Switch are non policy routed, you must test the PBR from the clients that use the SVI as Gateway.
Regards.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-12-2018 08:50 AM
I do not agree with the suggestion that the original poster should have a default route for each ISP. And I agree with the statement from Paul that you do not need two route maps. Default routing for ISP 1 and PBR for ISP 2 should produce the desired results (and having tracking and the verify-availability are good improvements on the basic functionality).
But this most recent post does have one very important suggestion. You need to test from a client connected in vlan 200. If you want to try to test from the switch then you would also need to configure ip local policy. When you configure policy routing on an interface then PBR acts on traffic arriving on that interface but would not act on traffic generated from the switch itself.
HTH
Rick
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-14-2018 08:43 AM - edited 02-14-2018 08:45 AM
Hi Richard,
Thank you for the additional information.
The PBR is not applying on int vlan 200. What i need to check?
C3850-Core-SW#sh run interface vlan 200
Building configuration...
Current configuration : 80 bytes
!
interface Vlan200
ip address 192.168.200.1 255.255.255.0
ip nat inside
end
C3850-Core-SW#
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide