- Cisco Community
- Technology and Support
- Networking
- Switching
- how to configure routing on asa 5505
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
how to configure routing on asa 5505
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-05-2011 11:49 PM - edited 03-07-2019 03:45 AM
Hi
I am totaly newbie to cisco routing, but i have some basic knowledge about routing
how do i configure the new asa 5505 to be as a router as shown in the diagram
note: the isps' routers placed in head office. but i cannot change the configurations of the isp's routers.
thanks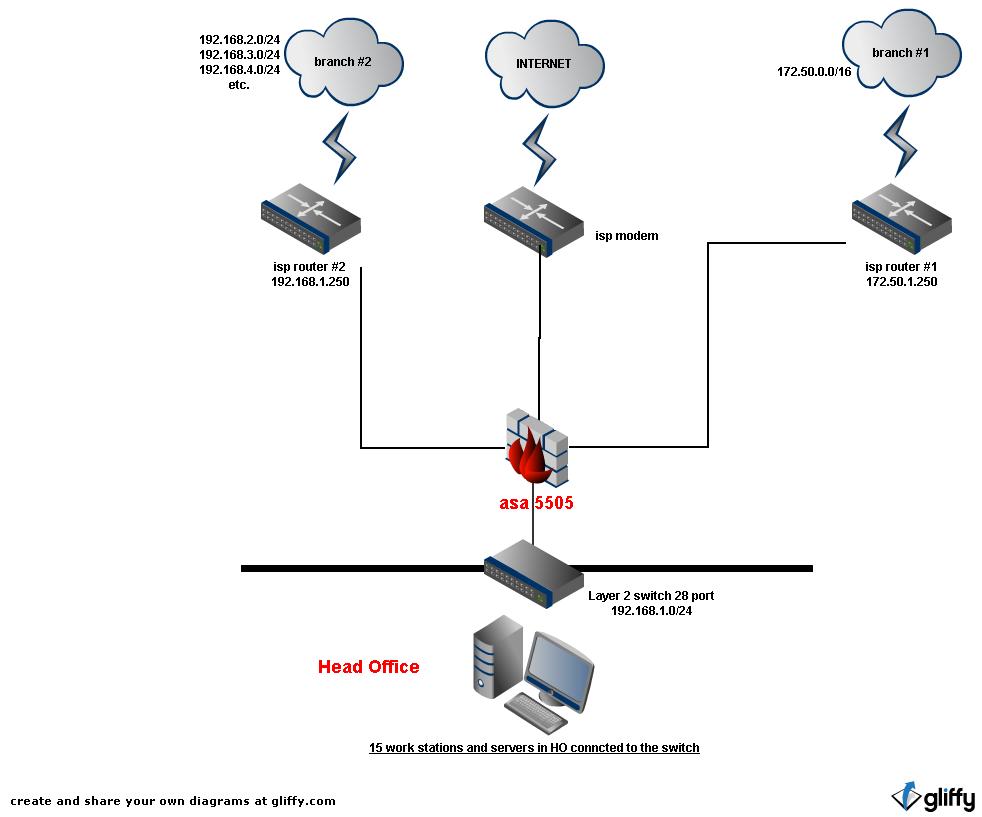
- Labels:
-
Other Switching
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-06-2011 12:05 AM
Hi,
Look at the following link will help you.
http://www.cisco.com/en/US/docs/security/asa/asa84/configuration/guide/route_ospf.html#wp1104550
Please rate the helpfull posts.
Regards,
Naidu.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-06-2011 07:54 AM
please correct me if i am wrong,
as much as i know, since i have no access to other routers i cannot deploy here ospf (these router are very dumb)
can it be done with static routing? if yes, how?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-06-2011 08:22 AM
Hi,
which licence have you got ? and which OS version on your ASA ?
Regards.
Alain
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-06-2011 08:42 AM
i bought it two weeks ago. new.
it is ASA5505-50-BUN-K9
os ver 8.2
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-07-2011 07:35 AM
i will appreciate any help here...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-07-2011 03:29 PM
pp rr wrote:
Hi
I am totaly newbie to cisco routing, but i have some basic knowledge about routing
how do i configure the new asa 5505 to be as a router as shown in the diagram
note: the isps' routers placed in head office. but i cannot change the configurations of the isp's routers.
Damn, I hate web browsers. Mine crashed with a reply already half written - oh well, here we go again.
First thing I'd look at is changing your IP addressing scheme if possible. You have 192.168.1.0/24 inside your firewall, and 192.168.1.250 as the remoter router IP at branch #2 - this will be pretty difficult to route via your ASA as the IP adderss ranges overlap inside and outside, and the ASA won't like it. Also, I'd use a smaller subnet on the link to branch #1 - you're using an IP address in a range of 65536, which makes it a bit awkward to route - I usually use a /30 on point to point links (or a /29 if HSRP or redundancy is required).
Do you have separate links to site #1 and site #2, or are they VPN's out the DSL service? Your drawing looks like you have separate links, but it's difficult to be sure.
If you have separate links, and assuming one link is conencted to each port, routing is pretty simple - just add statements similar to the following to your configuration
route site2 192.168.2.0 255.255.255.0 192.168.20.2
The format is
route
My example assumes you have a nameif of "site2" on the interface connected to the link to site 2, configured with an IP address of 192.168.20.1/30 and that you change the link IP address of the router at the other end to 192.168.20.2/30.
You'll also have to make sure the router at site 2 has a route (either a default or subnet-specific) route back to the asa - something like
ip route 0.0.0.0 0.0.0.0 192.168.20.1
if it's a Cisco IOS router.
Hope this helps.
Cheers.
(Please rate helpful posts.)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-07-2011 08:08 PM
Whups, I just re-read your original and saw the bit about not being able to change the configuration of the ISP routers.
Which means you're going to need to change the inside configurations (in your head office) so you don't get an overlapping IP range.
Still need to know how you connect to those remote sites, though. Are they dedicated links? And are the IP addresses you quote at your head office end, or the remote end?
Extrapolating a bit, I'd go for a config something like this.
On the ASA
Interface f0/0 - nameif inside, IP address 192.168.0.254/24
Interface f0/1 - nameif site1, IP address 172.50.1.249
Interface f0/2, nameif site2, IP address 192.168.1.249
Interface f0/3, nameif outside, IP adress whatever works with your Internet router.
Then just do this for your routing table
route site1 172.50.0.0 255.255.0.0 172.50.1.250
route site2 192.168.2.0 255.255.255.0 192.168.1.250
route site2 192.168.3.0 255.255.255.0 192.168.1.250
route site2 192.168.4.0 255.255.255.0 192.168.1.250
route outside 0.0.0.0 0.0.0.0
You'll need to do NAT for Internet access, and NAT exemptions for connecting to your remote sites, but that's your basic layout on what you've drawn - with one minor change, which is your 'inside' IP range.
Hope that's clearer - sorry for my bad in not reading your original post properly.
Cheers.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-08-2011 07:38 AM
dear darren.g
thank you so much for the detailed explantion!
1. connections to branches go trough seperate dedicated lines. (different routers, isp's etc.)
2. the routers (192.168.1.250 & 172.50.1.250) are inside the head office connected to the same switch as the work stations
I still missing the NAT configuration but i will leave it right now because i will not be able to configue the asa till next thursday....
so please wait and I will updated you next week
many many thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-08-2011 02:35 PM
pp rr wrote:
dear darren.g
thank you so much for the detailed explantion!
1. connections to branches go trough seperate dedicated lines. (different routers, isp's etc.)
2. the routers (192.168.1.250 & 172.50.1.250) are inside the head office connected to the same switch as the work stations
I still missing the NAT configuration but i will leave it right now because i will not be able to configue the asa till next thursday....
so please wait and I will updated you next week
many many thanks
I can see one immediate problem with your setup - if you have the site routers connected to the same switch as your workstations - is it just a layer 2 switch, or does it have some layer 3 capabilities?
If it's a layer two switch, you need both links in different VLAN's - and then you have nothing to route between them, so the sites won't be able to talk to one another (well, head office will be able to talk to site 2 since the link IP is in the same subnet - but you'll still need to have some additional routing on your workstations for this to work, since your default route would want to be your firewall).
You'd be better putting yout "site" links on physical ports on the ASA rather than your "inside' switch, and changing the "inside' IP address range - unless you want to get into trunking into your ASA and using it to do the routing between the 192.168.1.0/24 and 172.50.0.0/16 networks. Which you could do, but it'd make security a bit tricky.
Looking at what you've got, the scenario I described above would be the way I would do it - but there are no doubt other ways, and YMMV when it comes to configuring the ASA - I don't really know your level of experience - if it's low, I can suggest only one thing - make SURE you enable ASDM - doing this kind of configuration is *way* easier via the GUI than it is via the OS's still unbelievable obscure command line syntax. :-)
Cheers.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide

