- Cisco Community
- Technology and Support
- Networking
- Switching
- Re: How to resolve Native Vlan Mismatch on two switch?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-28-2019 11:35 AM
Hi to all
I have two switch, switch A (C9300) and switch B (C3850).
Switch A has three vlan: vlan 2000, 3000 and 4000.
Switch B has one vlan: vlan 1 (default)
Switch A is displaying log with:
CDP-4-NATIVE_VLAN_MISMATCH : Native VLAN mismatch discovered on GigabitEthernetX/X/X, with C3850#1 GigabitEthernetX/X/X
I precise that i use port-Based VLAN with no trunk (trunk is not usefull for my meaning).
All is working fine expect this message
Does this message is important ? How can i fix it?
Does it is better to define VLAN1 as VLAN2000 on Switch B?
Many thanks for your help.
Solved! Go to Solution.
- Labels:
-
Catalyst 9000
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-29-2019 10:33 AM
Thank you for the additional information and for the config of the 9300. Based on this information we can see that the points in my previous response are supported. There is no trunk on either switch. There is no desire for a trunk on either switch. I do not see any benefit from configuring a trunk on the switches. The additional information makes it clear that the configured vlans are to provide separation between groups of devices and that " each LAN is connected to firewall with a port." and that is almost certainly an access port in the switch vlan to an interface of the firewall (done individually for each vlan).
It would be interesting (but ultimately not important) to know what interface (and therefore what vlan) on 9300 connects to the 3850. If the intent of deploying the 3850 is to increase the number of ports in one of the vlans of the 9300 then it is working just as intended. All Ethernet frames from the 3850 are forwarded into the appropriate vlan of the 9300 and are kept separate from the other vlans on the 9300 and all devices connected on 3850 are functionally members of the vlan on the 9300.
It certainly appears that this network is working as intended. The CDP message is more of a notification than it is a real error. There is no harm in letting it continue as it has been. If you do want to "solve" this then you should configure the vlan on 3850 that matches the connected vlan on 9300 and assign all 3850 access ports to that vlan. This will stop the CDP message.
HTH
Rick
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-28-2019 01:05 PM
Until we see your both side switch configuration, we do not what is configured, pelase both switch config.
show vlan
show run interface x/x - for the both the switch
show trunk config if any configure.
let us know what port connected between these switch to suggest better.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-28-2019 01:48 PM
Native VLAN is that one, which transmitted packets have not been encapsulated by switch with 802.1Q header on trunk ports.
You have connected two switches with trunk port.
Default native VLAN is 1, but it is recommended to change it to another VLAN and do not use VLAN 1.
You can change native VLAN by this command on both ends of trunk same VLAN number:
configure terminal
interface GigabitEthernet x/y/z
switchport trunk native vlan <vlan_number>
Of course, every time VLAN has to exist on both ends of trunk.
configure terminal
vlan <vlan_number>
name <vlan_name>
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-28-2019 03:06 PM
As I understand the original post it is quite clear that there are no trunks on either switch. If I am mistaken then please provide clarification. Based on this there is no need for any suggestions about adjusting trunks to resolve this issue.
It is also plain that the 3850 has only a single vlan and that vlan is vlan 1. The original post says the 9300 has 3 vlans. Not to quibble but that switch really has 4 vlans, since vlan 1 is the default and exists even when no ports are assigned to it. So what is happening is that an access port on 3850 in vlan 1 is connected to an access port on 9300 that is in a different vlan. That is what is causing the CDP message about mismatched vlans. And technically it is sort of a mismatch because vlan 1 on 3850 is connected to not vlan 1 on 9300. This is not necessarily an error.
The original post says things are working and I believe this is quite possible. Ethernet frames from one access port are going to the other access port with no vlan tags. So neither switch realizes that the assigned vlan membership does not match. What is happening is that vlan 1 on 3850 is bridged to vlan 2000 or 3000 or 4000 on the 9300. And at least from the perspective of layer 2 all is well. Hosts in vlan 1 on 3850 can communicate directly with hosts in the connected vlan on 9300 (either 2000 or 3000 or 4000) but would not be able to communicate with hosts in the other 2 vlans.
We do not know whether there is any layer 3 routing involved. And from a layer 3 perspective there could be issues with this implementation. Can the original poster tell us whether there is layer 3 routing? And if so how does it work?
The original post asks a question about how to solve this issue. My first response is to ask whether this is something that needs fixing? The message is more of a diagnostic warning and is not really an error. But if the original poster does want to fix this then the solution is to change the 3850 so that all of its ports are assigned to the connected vlan of the 9300 (2000 or 3000 or 4000).
HTH
Rick
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-29-2019 02:27 AM
Hi to all,
You find below conf of switch A (C9300) :
#show conf Using 8792 out of 2097152 bytes ! ! Last configuration change at 22:01:40 cest Sat Jun 22 2019 ! version 16.6 no service pad service timestamps debug datetime msec service timestamps log datetime msec service password-encryption no platform punt-keepalive disable-kernel-core ! hostname XXXXXXXX ! ! vrf definition Mgmt-vrf ! address-family ipv4 exit-address-family ! address-family ipv6 exit-address-family ! enable secret 5 XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX enable password 7 XXXXXXXXXXXXXXXXXXXXXXXXX ! no aaa new-model --More-- switch 1 provision c9300-48p ! ! ! vtp mode transparent ! crypto pki trustpoint TP-self-signed-XXXXXXXXXXXXXXX enrollment selfsigned subject-name cn=IOS-Self-Signed-Certificate-XXXXXXXXXXXXXXX revocation-check none rsakeypair TP-self-signed-XXXXXXXXXXXXXXXXXXXX ! ! crypto pki certificate chain TP-self-signed-2638186642 certificate self-signed 01 nvram:IOS-Self-Sig#3.cer ! ! ! diagnostic bootup level minimal spanning-tree mode rapid-pvst spanning-tree extend system-id ! username Cisco privilege 15 password 7 XXXXXXXXXXXXXXXXXXXXXXXXXXXXXX ! redundancy mode sso ! ! transceiver type all monitoring ! vlan 2000 name VLAN_MY_LAN ! vlan 3000 name VLAN_DMZ ! vlan 4000 name VLAN_WIFI ! ! class-map match-any system-cpp-police-topology-control description Topology control class-map match-any system-cpp-police-sw-forward description Sw forwarding, L2 LVX data, LOGGING class-map match-any system-cpp-default description DHCP Snooping, EWLC control, EWCL data class-map match-any system-cpp-police-sys-data description Learning cache ovfl, Crypto Control, Exception, EGR Exception, NFL SAMPLED DATA, RPF Failed class-map match-any system-cpp-police-punt-webauth description Punt Webauth class-map match-any system-cpp-police-l2lvx-control description L2 LVX control packets class-map match-any system-cpp-police-forus description Forus Address resolution and Forus traffic class-map match-any system-cpp-police-multicast-end-station description MCAST END STATION class-map match-any system-cpp-police-multicast description Transit Traffic and MCAST Data class-map match-any system-cpp-police-l2-control description L2 control class-map match-any system-cpp-police-dot1x-auth description DOT1X Auth class-map match-any system-cpp-police-data description ICMP redirect, ICMP_GEN and BROADCAST class-map match-any system-cpp-police-stackwise-virt-control description Stackwise Virtual class-map match-any non-client-nrt-class class-map match-any system-cpp-police-routing-control description Routing control class-map match-any system-cpp-police-protocol-snooping description Protocol snooping class-map match-any system-cpp-police-system-critical description System Critical and Gold ! policy-map system-cpp-policy ! ! ! ! ! ! ! ! ! ! ! ! ! ! interface GigabitEthernet0/0 vrf forwarding Mgmt-vrf no ip address shutdown speed 1000 negotiation auto ! interface GigabitEthernet1/0/1 switchport access vlan 4000 switchport mode access ! interface GigabitEthernet1/0/2 switchport access vlan 4000 switchport mode access ! interface GigabitEthernet1/0/3 switchport access vlan 3000 switchport mode access ! interface GigabitEthernet1/0/4 switchport access vlan 3000 switchport mode access ! interface GigabitEthernet1/0/5 switchport access vlan 3000 switchport mode access ! interface GigabitEthernet1/0/6 switchport access vlan 3000 switchport mode access ! interface GigabitEthernet1/0/7 switchport access vlan 3000 switchport mode access ! interface GigabitEthernet1/0/8 switchport access vlan 3000 switchport mode access ! interface GigabitEthernet1/0/9 switchport access vlan 3000 switchport mode access ! interface GigabitEthernet1/0/10 switchport access vlan 3000 switchport mode access ! interface GigabitEthernet1/0/11 switchport access vlan 3000 switchport mode access ! interface GigabitEthernet1/0/12 switchport access vlan 3000 switchport mode access ! interface GigabitEthernet1/0/13 switchport access vlan 2000 switchport mode access ! interface GigabitEthernet1/0/14 switchport access vlan 2000 switchport mode access ! interface GigabitEthernet1/0/15 switchport access vlan 2000 switchport mode access ! interface GigabitEthernet1/0/16 switchport access vlan 2000 switchport mode access ! interface GigabitEthernet1/0/17 switchport access vlan 2000 switchport mode access ! interface GigabitEthernet1/0/18 switchport access vlan 2000 switchport mode access ! interface GigabitEthernet1/0/19 switchport access vlan 2000 switchport mode access ! interface GigabitEthernet1/0/20 switchport access vlan 2000 switchport mode access ! interface GigabitEthernet1/0/21 switchport access vlan 2000 switchport mode access ! interface GigabitEthernet1/0/22 switchport access vlan 2000 switchport mode access ! interface GigabitEthernet1/0/23 switchport access vlan 2000 switchport mode access ! interface GigabitEthernet1/0/24 switchport access vlan 2000 switchport mode access ! interface GigabitEthernet1/0/25 switchport access vlan 2000 switchport mode access ! interface GigabitEthernet1/0/26 switchport access vlan 2000 switchport mode access ! interface GigabitEthernet1/0/27 switchport access vlan 2000 switchport mode access ! interface GigabitEthernet1/0/28 switchport access vlan 2000 switchport mode access ! interface GigabitEthernet1/0/29 switchport access vlan 2000 switchport mode access ! interface GigabitEthernet1/0/30 switchport access vlan 2000 switchport mode access ! interface GigabitEthernet1/0/31 switchport access vlan 2000 switchport mode access ! interface GigabitEthernet1/0/32 switchport access vlan 2000 switchport mode access ! interface GigabitEthernet1/0/33 switchport access vlan 2000 switchport mode access ! interface GigabitEthernet1/0/34 switchport access vlan 2000 switchport mode access ! interface GigabitEthernet1/0/35 switchport access vlan 2000 switchport mode access ! interface GigabitEthernet1/0/36 switchport access vlan 2000 switchport mode access ! interface GigabitEthernet1/0/37 switchport access vlan 2000 switchport mode access ! interface GigabitEthernet1/0/38 switchport access vlan 2000 switchport mode access ! interface GigabitEthernet1/0/39 switchport access vlan 2000 switchport mode access ! interface GigabitEthernet1/0/40 switchport access vlan 2000 switchport mode access ! interface GigabitEthernet1/0/41 switchport access vlan 2000 switchport mode access ! interface GigabitEthernet1/0/42 switchport access vlan 2000 switchport mode access ! interface GigabitEthernet1/0/43 switchport access vlan 2000 switchport mode access ! interface GigabitEthernet1/0/44 switchport access vlan 2000 switchport mode access ! interface GigabitEthernet1/0/45 switchport access vlan 2000 switchport mode access ! interface GigabitEthernet1/0/46 switchport access vlan 2000 switchport mode access ! interface GigabitEthernet1/0/47 switchport access vlan 2000 switchport mode access ! interface GigabitEthernet1/0/48 switchport access vlan 2000 switchport mode access ! interface GigabitEthernet1/1/1 ! interface GigabitEthernet1/1/2 ! interface GigabitEthernet1/1/3 ! interface GigabitEthernet1/1/4 ! interface TenGigabitEthernet1/1/1 switchport access vlan 4000 switchport mode access ! interface TenGigabitEthernet1/1/2 switchport access vlan 3000 switchport mode access ! interface TenGigabitEthernet1/1/3 switchport access vlan 3000 switchport mode access ! interface TenGigabitEthernet1/1/4 switchport access vlan 2000 switchport mode access ! interface TenGigabitEthernet1/1/5 switchport access vlan 2000 switchport mode access ! interface TenGigabitEthernet1/1/6 switchport access vlan 2000 switchport mode access ! interface TenGigabitEthernet1/1/7 switchport access vlan 2000 switchport mode access ! interface TenGigabitEthernet1/1/8 switchport access vlan 2000 switchport mode access ! interface FortyGigabitEthernet1/1/1 ! interface FortyGigabitEthernet1/1/2 ! interface Vlan1 no ip address ! interface Vlan2000 ip address xxx.xxx.xxx.xxx 255.255.255.0 ! interface Vlan3000 ip address xxx.xxx.xxx.xxx 255.255.255.0 ! interface Vlan4000 ip address xxx.xxx.xxx.xxx 255.255.255.0 ! ip forward-protocol nd no ip http server ip http authentication local no ip http secure-server ip http client source-interface Vlan1 ! ! ! control-plane service-policy input system-cpp-policy ! ! line con 0 password 7 XXXXXXXXXXXXXXXXXXXXXXXXX login stopbits 1 line vty 0 4 session-timeout 15 exec-timeout 15 0 password 7 XXXXXXXXXXXXXXXXXXXXXXXXX login transport input none line vty 5 15 password 7 XXXXXXXXXXXXXXXXXXXXXXXXX login transport input none ! ntp server pool.ntp.org ! mac address-table notification mac-move ! end
Switch B is standard conf with just VLAN1.
Many thanks for your advise in advance.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-29-2019 04:14 AM
thank for the config, but i may be over looked, we have not seen any trunk port configured for other switch (Switch B is standard conf with just VLAN1.) ?
can you let us know what is the interface connected between switches. and you need to configured that port as trunk for better recommended.
example : on bot the sides
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-29-2019 07:50 AM
Yes, switch B is standard switch with vlan1 only.
Switch A has 3 VLANs (Port-Based VLAN) to isolate three differents LAN on same device... each LAN is connected to firewall with a port.
I didn't make any trunk port.
So what do you recommand me ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-29-2019 08:43 AM
As suggest we would like to know both the switch configruation if you some high level diagram how they are connected.
still iam not able to visualise your setup. so please provide more important information to suggest better.
or just ignore all working as expected. (this is not recommended,)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-29-2019 10:29 AM
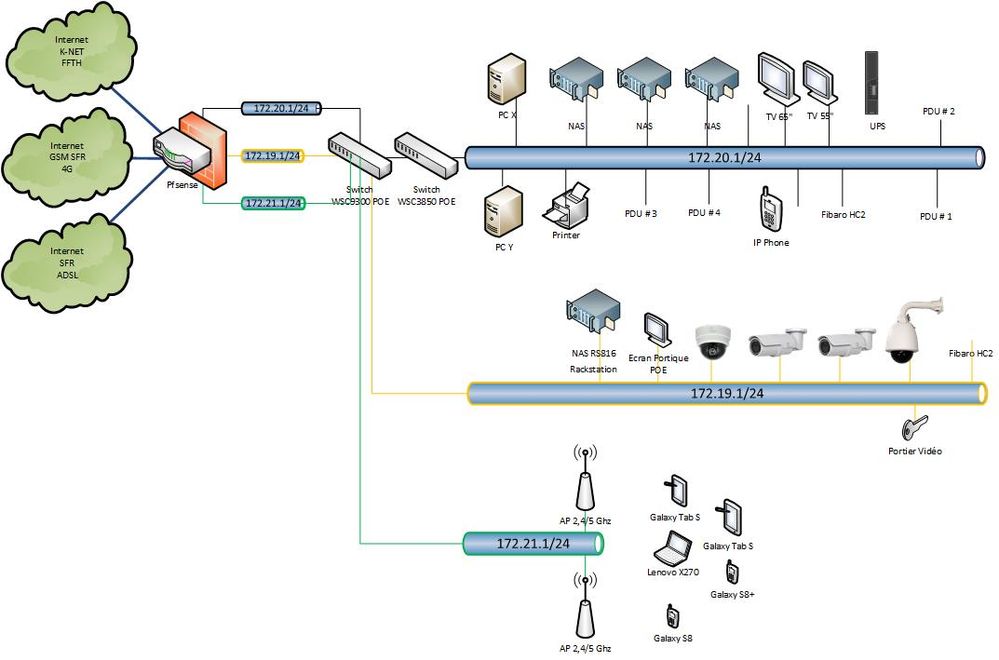
To have more context :
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-29-2019 10:33 AM
Thank you for the additional information and for the config of the 9300. Based on this information we can see that the points in my previous response are supported. There is no trunk on either switch. There is no desire for a trunk on either switch. I do not see any benefit from configuring a trunk on the switches. The additional information makes it clear that the configured vlans are to provide separation between groups of devices and that " each LAN is connected to firewall with a port." and that is almost certainly an access port in the switch vlan to an interface of the firewall (done individually for each vlan).
It would be interesting (but ultimately not important) to know what interface (and therefore what vlan) on 9300 connects to the 3850. If the intent of deploying the 3850 is to increase the number of ports in one of the vlans of the 9300 then it is working just as intended. All Ethernet frames from the 3850 are forwarded into the appropriate vlan of the 9300 and are kept separate from the other vlans on the 9300 and all devices connected on 3850 are functionally members of the vlan on the 9300.
It certainly appears that this network is working as intended. The CDP message is more of a notification than it is a real error. There is no harm in letting it continue as it has been. If you do want to "solve" this then you should configure the vlan on 3850 that matches the connected vlan on 9300 and assign all 3850 access ports to that vlan. This will stop the CDP message.
HTH
Rick
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-29-2019 11:25 AM
This has been an interesting discussion, especially the part about a CDP message that looks like an error message. And in some contexts it would point out a real error in the network. But in this context it is more of a notification and ultimately the network works as intended. Thank you for marking this question as solved. This will help other participants in the community to identify discussions which have helpful information. This community is an excellent place to ask questions and to learn about networking. I hope to see you continue to be active in the community.
HTH
Rick
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-30-2019 11:15 PM - edited 07-01-2019 12:04 AM
I am curious how you can accept a solution with that CDP error and live with that.
Let me do some add-ons:
You can set switchport nonegotiation to disable DTP.
I am missing this DTP disable command on the C9300.
And the Cat3850 IS NOT dummy switch so it has to be configured also.
It talks by STP, DTP, CDP, VTP!
So I recommend configuring C3850 by:
int gig x/y
switchport mode access
switchport nonegotiate
!
vtp mode off (or transparent)
spanning-tree vlan 1 - 4094 priority 64000
Or you can turn off CDP at particular ports on C3850 for a shortcut to eliminating logging notification.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-01-2019 02:05 PM
I believe that your concern "how you can accept a solution with that CDP error and live with that." is a bit exaggerated. We have established that it is really not an error. What it is is that an access port in vlan 1 is connected to an access port that is probably in vlan 2000. Since they are access ports there is no vlan tagging and no vlan information is exchanged. A regular Ethernet frame from one switch is forwarded to the other switch and is forwarded to devices within the particular vlan of the receiving switch. As long as the original poster intended that all ports of 3850 operate in a single broadcast domain that includes all the ports in that particular vlan on 9300 then the network is doing exactly what was intended. No error.
What is interesting is that CDP is smart enough to recognize this nominal mismatch "error". Of the suggestions that you make the one that makes the most sense is the one about disabling CDP. That would certainly stop the logging of this message. From my perspective the loss of visibility incurred by disabling CDP between these switches would not be worth the benefit of suppressing this particular message. But that is a decision for the original poster to make.
HTH
Rick
Rick
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: