- Cisco Community
- Technology and Support
- Networking
- Switching
- lan to lan with asa5506 on the same phisical network
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-30-2017 05:43 AM - edited 03-08-2019 12:56 PM
Hi,
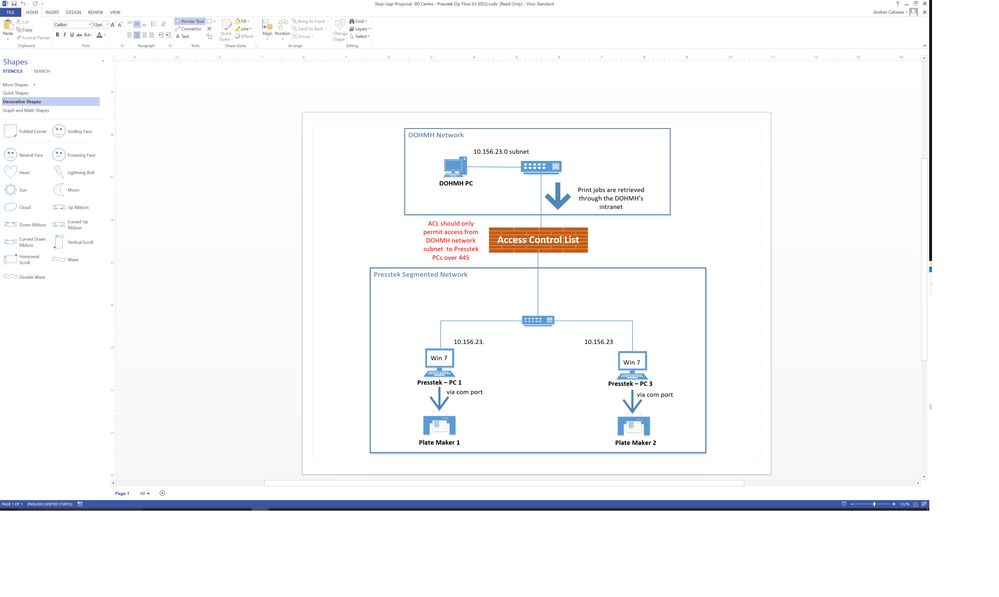
I am a newbie at configuring ASA's and trying to setup a Cisco ASA 5506 for the work flow on the attached image. If anyone could please recommend the best way to setup this ASA to Deny all traffic from LAN PC to Presstek PCs with the exception of port 445 for SMB file transfer. The Presstek computers will have static IP's on the same LAN subnet but they will be connected to the ASA ports and not LAN switch. If you need further info or need me to clarify certain things please let me know. Thanks
Solved! Go to Solution.
- Labels:
-
Other Switching
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-30-2017 08:24 AM
You should keep this:
access-group outside_access_in in interface outside
And you dont need BVI for this.
-If I helped you somehow, please, rate it as useful.-
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-30-2017 08:51 AM
ok so I can remove the BVI group. Also do I need to put the firewall transparent mode?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-30-2017 01:24 PM
Ok so I tried out what you suggested for me on the ASA config. It didn't seem to work for me. I have the ASA setup off the network currently. The outside interface (10.156.23.126) is connected to a offline switch with IP 10.156.23.125. I have a laptop connected to switch with IP (10.156.23.120) to mimic the DOHMH PC and then I have another laptop connected to ASA port 4 with static IP (10.156.23.33) to mimic one of the Presstek computers. Attached are my results with the connectivity described.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-30-2017 01:33 PM
Ping is a different situation.
You was trying to permit port 445 and deny everything else. What about that?
You can test this using telnet on windows or linux machine by issuing:
telnet "destination server'' 445
Telnet need to be enable on windows machine.
Ping need to be permitted independently and you need to add inspection on firewall.
access-list outside_access_in extended permit icmp any any
class inspection_default
inspect dns preset_dns_map
inspect icmp
-If I helped you somehow, please, rate it as useful.-
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-01-2017 06:01 AM
I added the commands you said for icmp permit and also tested the telnet to port 445 from laptop with IP 10.156.23.120 to 10.156.23.33 on port 445. Both did not work for me and on the other machine I have the windows firewall off so I know its not blocking the request. See below for how my config looks like on the ASA. Thanks
80Centre-FL-ASA-1# sh run
: Saved
:
: Serial Number: JAD21260FF5
: Hardware: ASA5506, 4096 MB RAM, CPU Atom C2000 series 1250 MHz, 1 CPU (4 cores)
:
ASA Version 9.7(1)4
!
hostname 80Centre-FL-ASA-1
domain-name health.dohmh.nycnet
enable password $sha512$5000$614vemnZqQcfOfmiKv+YsQ==$4oqF99AoyBNdRBqxtB/e3Q== pbkdf2
names
!
interface GigabitEthernet1/1
nameif outside
security-level 0
ip address 10.156.23.126 255.255.255.128
!
interface GigabitEthernet1/2
nameif inside_1
security-level 100
no ip address
!
interface GigabitEthernet1/3
nameif inside_2
security-level 100
no ip address
!
interface GigabitEthernet1/4
nameif inside_3
security-level 100
no ip address
!
interface GigabitEthernet1/5
nameif inside_4
security-level 100
no ip address
!
interface GigabitEthernet1/6
nameif inside_5
security-level 100
no ip address
!
interface GigabitEthernet1/7
nameif inside_6
security-level 100
no ip address
!
interface GigabitEthernet1/8
nameif inside_7
security-level 100
no ip address
!
interface Management1/1
management-only
no nameif
no security-level
no ip address
!
ftp mode passive
clock timezone EST -5
dns server-group DefaultDNS
domain-name health.dohmh.nycnet
same-security-traffic permit inter-interface
same-security-traffic permit intra-interface
object network obj_any1
subnet 0.0.0.0 0.0.0.0
object network obj_any2
subnet 0.0.0.0 0.0.0.0
object network obj_any3
subnet 0.0.0.0 0.0.0.0
object network obj_any4
subnet 0.0.0.0 0.0.0.0
object network obj_any5
subnet 0.0.0.0 0.0.0.0
object network obj_any6
subnet 0.0.0.0 0.0.0.0
object network obj_any7
subnet 0.0.0.0 0.0.0.0
object network outside-network
subnet 10.156.23.0 255.255.255.128
object network DOHMH
host 10.156.23.120
description DOHMH
object network 10.156.23.33
host 10.156.23.33
description Presstek PC1
object network 10.156.23.88
host 10.156.23.88
description Presstek PC3
object network ASA-IP
host 10.156.23.126
object-group network Presstek_PCs
description Presstek PCs
network-object object 10.156.23.33
network-object object 10.156.23.88
object-group service DM_INLINE_TCP_2 tcp
port-object eq 445
port-object eq ftp
port-object eq netbios-ssn
port-object eq 137
port-object eq 138
access-list outside_access_in extended permit tcp object DOHMH object-group Presstek_PCs object-group DM_INLINE_TCP_2
access-list outside_access_in extended permit icmp any any
pager lines 24
logging asdm informational
mtu outside 1500
mtu inside_1 1500
mtu inside_2 1500
mtu inside_3 1500
mtu inside_4 1500
mtu inside_5 1500
mtu inside_6 1500
mtu inside_7 1500
icmp unreachable rate-limit 1 burst-size 1
icmp permit any outside
icmp permit any inside_1
icmp permit any inside_2
icmp permit any inside_3
icmp permit any inside_4
icmp permit any inside_5
icmp permit any inside_6
icmp permit any inside_7
no asdm history enable
arp timeout 14400
no arp permit-nonconnected
arp rate-limit 16384
access-group outside_access_in in interface outside
route outside 0.0.0.0 0.0.0.0 10.156.23.1 1
timeout xlate 3:00:00
timeout pat-xlate 0:00:30
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 sctp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
timeout conn-holddown 0:00:15
timeout igp stale-route 0:01:10
user-identity default-domain LOCAL
http server enable
http 0.0.0.0 0.0.0.0 outside
http 0.0.0.0 0.0.0.0 inside_1
http 0.0.0.0 0.0.0.0 inside_2
http 0.0.0.0 0.0.0.0 inside_3
http 0.0.0.0 0.0.0.0 inside_4
http 0.0.0.0 0.0.0.0 inside_5
http 0.0.0.0 0.0.0.0 inside_6
http 0.0.0.0 0.0.0.0 inside_7
no snmp-server location
no snmp-server contact
service sw-reset-button
crypto ipsec security-association pmtu-aging infinite
crypto ca trustpool policy
telnet timeout 5
ssh stricthostkeycheck
ssh 10.242.184.0 255.255.255.0 outside
ssh 10.151.16.128 255.255.255.128 outside
ssh 10.227.255.128 255.255.255.128 outside
ssh 10.242.127.240 255.255.255.240 outside
ssh timeout 5
ssh version 2
ssh key-exchange group dh-group1-sha1
console timeout 0
dhcpd auto_config outside
!
threat-detection basic-threat
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
dynamic-access-policy-record DfltAccessPolicy
username dohadmin password $sha512$5000$/HmhJRWXvFcwjEZLMQmSig==$NFSV9Tv26wr9Q6CteB5w8Q== pbkdf2
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum client auto
message-length maximum 512
no tcp-inspection
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect esmtp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
inspect ip-options
inspect icmp
!
service-policy global_policy global
prompt hostname context
no call-home reporting anonymous
Cryptochecksum:77f38bdba2d87784a40262de50b80d2f
: end
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-01-2017 06:13 AM
Please, run the following command:
packet-tracer input outside protocol 10.156.23.120 1030 10.156.23.33 445 detailed
Share the output.
-If I helped you somehow, please, rate it as useful.-
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-01-2017 06:27 AM
Please see below for packet tracer.
80Centre-FL-ASA-1# packet-tracer input outside tcp 10.156.23.120 1030 10.156.2$
Phase: 1
Type: ACCESS-LIST
Subtype:
Result: ALLOW
Config:
Implicit Rule
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7fbef5dd7cf0, priority=1, domain=permit, deny=false
hits=75, user_data=0x0, cs_id=0x0, l3_type=0x8
src mac=0000.0000.0000, mask=0000.0000.0000
dst mac=0000.0000.0000, mask=0100.0000.0000
input_ifc=outside, output_ifc=any
Phase: 2
Type: ROUTE-LOOKUP
Subtype: Resolve Egress Interface
Result: ALLOW
Config:
Additional Information:
found next-hop 10.156.23.33 using egress ifc outside
Phase: 3
Type: ACCESS-LIST
Subtype: log
Result: ALLOW
Config:
access-group outside_access_in in interface outside
access-list outside_access_in extended permit tcp object DOHMH object-group Presstek_PCs object-group DM_INLINE_TCP_2
object-group network Presstek_PCs
description: Presstek PCs
network-object object 10.156.23.33
network-object object 10.156.23.88
object-group service DM_INLINE_TCP_2 tcp
port-object eq 445
port-object eq ftp
port-object eq netbios-ssn
port-object eq 137
port-object eq 138
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7fbef6086110, priority=13, domain=permit, deny=false
hits=0, user_data=0x7fbeeed1f2c0, cs_id=0x0, use_real_addr, flags=0x0, protocol=6
src ip/id=10.156.23.120, mask=255.255.255.255, port=0, tag=any
dst ip/id=10.156.23.33, mask=255.255.255.255, port=445, tag=any, dscp=0x0
input_ifc=outside, output_ifc=any
Phase: 4
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7fbef51ced20, priority=0, domain=nat-per-session, deny=false
hits=351, user_data=0x0, cs_id=0x0, reverse, use_real_addr, flags=0x0, protocol=6
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0
input_ifc=any, output_ifc=any
Phase: 5
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7fbef5de01b0, priority=0, domain=inspect-ip-options, deny=true
hits=75, user_data=0x0, cs_id=0x0, reverse, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0
input_ifc=outside, output_ifc=any
Phase: 6
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Reverse Flow based lookup yields rule:
in id=0x7fbef51ced20, priority=0, domain=nat-per-session, deny=false
hits=353, user_data=0x0, cs_id=0x0, reverse, use_real_addr, flags=0x0, protocol=6
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0
input_ifc=any, output_ifc=any
Phase: 7
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Reverse Flow based lookup yields rule:
in id=0x7fbef5de01b0, priority=0, domain=inspect-ip-options, deny=true
hits=77, user_data=0x0, cs_id=0x0, reverse, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0
input_ifc=outside, output_ifc=any
Phase: 8
Type: FLOW-CREATION
Subtype:
Result: ALLOW
Config:
Additional Information:
New flow created with id 711, packet dispatched to next module
Module information for forward flow ...
snp_fp_tracer_drop
snp_fp_inspect_ip_options
snp_fp_tcp_normalizer
snp_fp_translate
snp_fp_adjacency
snp_fp_fragment
snp_ifc_stat
Module information for reverse flow ...
snp_fp_tracer_drop
snp_fp_inspect_ip_options
snp_fp_translate
snp_fp_tcp_normalizer
snp_fp_adjacency
snp_fp_fragment
snp_ifc_stat
Result:
input-interface: outside
input-status: up
input-line-status: up
output-interface: outside
output-status: up
output-line-status: up
Action: allow
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-01-2017 06:32 AM
As you can see, everything is pretty much ok with Firewall config.
Make sure the server is responding on port 445. And make sure server is properly configured in terms of routing. It must have a default gateway pointed to Firewall.
Try to permit port 445 also for UDP and you may need 137,138 and 139 as well.
-If I helped you somehow, please, rate it as useful.-
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-01-2017 06:38 AM
You know after I ran the packet tracer and saw that everything passed I did at netstat -a on PC 10.156.23.120 and see that its listening on port 445. I ran the telnet to 445 again and it connected perfectly fine with no issues and I was also now able to ping from DOHMH PC to Presstek PC. Seems like all is working now as it should be with all the ports and access we configured on the firewall. I will be putting this into production next week and will test with the real machines at the site. Thanks for all your help and I will email you then with my results.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-01-2017 06:51 AM
That´s good to hear.
Please, change this to answered and help others to find solution and rate this as helpful as well.
We are here if you need more help.
-If I helped you somehow, please, rate it as useful.-
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-01-2017 06:50 AM
Disregard it only worked because I had my laptop also connected to the Wifi LAN and it was pinging the PC at the site with IP 10.156.23.33
So at this point still not able to telnet or ping from 10.156.23.120 (DOHMH) to Presstek (10.156.23.33)
So you are saying that the Presstek PC's which are connected to the ASA should have its default gateway be the IP of the firewall?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-01-2017 06:54 AM
Yeah, make sure you have proper routing config on server so that it can reply the packets. I don't know exactly your environment but looks like the firewall should be the gateway.
-If I helped you somehow, please, rate it as useful.-
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-01-2017 08:38 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-01-2017 09:04 AM
No. Looks ok.
What you can do is run some capture on ASA and make sure real packets are going on. As per the packet tracer ACL and routing is ok.
You can run the command capture and put ? To see the options.
-If I helped you somehow, please, rate it as useful.-
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-01-2017 11:20 AM
Ok so the below is a capture on ASA while running a ping -t from DOHMH PC to Presstek PC 10.156.23.33
80Centre-FL-ASA-1# sh cap cap1
43 packets captured
1: 07:16:36.605940 10.156.23.120.137 > 10.156.23.127.137: udp 50
2: 07:16:37.366069 10.156.23.120.137 > 10.156.23.127.137: udp 50
3: 07:16:38.130410 10.156.23.120.137 > 10.156.23.127.137: udp 50
4: 07:16:38.889983 10.156.23.120.137 > 10.156.23.127.137: udp 50
5: 07:16:39.635663 10.156.23.120.137 > 10.156.23.127.137: udp 50
6: 07:16:40.393641 10.156.23.120.137 > 10.156.23.127.137: udp 50
7: 07:16:41.162497 10.156.23.120.137 > 10.156.23.127.137: udp 50
8: 07:16:41.922468 10.156.23.120.137 > 10.156.23.127.137: udp 50
9: 07:16:42.686960 10.156.23.120.137 > 10.156.23.127.137: udp 50
10: 07:16:47.463385 10.156.23.120.137 > 10.156.23.127.137: udp 50
11: 07:16:48.225009 10.156.23.120.137 > 10.156.23.127.137: udp 50
12: 07:16:48.989328 10.156.23.120.137 > 10.156.23.127.137: udp 50
13: 07:16:49.505100 arp who-has 10.156.23.1 tell 10.156.23.120
14: 07:16:50.424614 arp who-has 10.156.23.1 tell 10.156.23.120
15: 07:16:51.423012 arp who-has 10.156.23.1 tell 10.156.23.120
16: 07:16:52.515033 arp who-has 10.156.23.1 tell 10.156.23.120
17: 07:16:53.419823 arp who-has 10.156.23.1 tell 10.156.23.120
18: 07:16:54.418267 arp who-has 10.156.23.1 tell 10.156.23.120
19: 07:16:58.521320 arp who-has 10.156.23.1 tell 10.156.23.120
20: 07:16:59.410302 arp who-has 10.156.23.1 tell 10.156.23.120
21: 07:17:00.424416 arp who-has 10.156.23.1 tell 10.156.23.120
22: 07:17:14.417779 arp who-has 10.156.23.33 tell 10.156.23.120
23: 07:17:15.418832 arp who-has 10.156.23.33 tell 10.156.23.120
24: 07:17:16.414666 arp who-has 10.156.23.33 tell 10.156.23.120
25: 07:17:17.413140 arp who-has 10.156.23.33 tell 10.156.23.120
26: 07:17:18.412652 arp who-has 10.156.23.33 tell 10.156.23.120
27: 07:17:19.409906 arp who-has 10.156.23.33 tell 10.156.23.120
28: 07:17:20.423974 arp who-has 10.156.23.33 tell 10.156.23.120
29: 07:17:21.424508 arp who-has 10.156.23.33 tell 10.156.23.120
30: 07:17:22.420800 arp who-has 10.156.23.33 tell 10.156.23.120
31: 07:17:23.419228 arp who-has 10.156.23.33 tell 10.156.23.120
32: 07:17:24.418923 arp who-has 10.156.23.33 tell 10.156.23.120
33: 07:17:25.416085 arp who-has 10.156.23.33 tell 10.156.23.120
34: 07:17:26.414498 arp who-has 10.156.23.33 tell 10.156.23.120
35: 07:17:27.414330 arp who-has 10.156.23.33 tell 10.156.23.120
36: 07:17:28.411309 arp who-has 10.156.23.33 tell 10.156.23.120
37: 07:17:29.425240 arp who-has 10.156.23.33 tell 10.156.23.120
38: 07:17:30.425957 arp who-has 10.156.23.33 tell 10.156.23.120
39: 07:17:31.422188 arp who-has 10.156.23.33 tell 10.156.23.120
40: 07:17:32.420586 arp who-has 10.156.23.33 tell 10.156.23.120
41: 07:17:33.420586 arp who-has 10.156.23.33 tell 10.156.23.120
42: 07:17:34.417428 arp who-has 10.156.23.33 tell 10.156.23.120
43: 07:17:35.415872 arp who-has 10.156.23.33 tell 10.156.23.120
43 packets shown
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide