- Cisco Community
- Technology and Support
- Networking
- Switching
- Re: Local VLANs and VoIP
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-21-2019 06:18 AM - edited 03-08-2019 05:05 PM
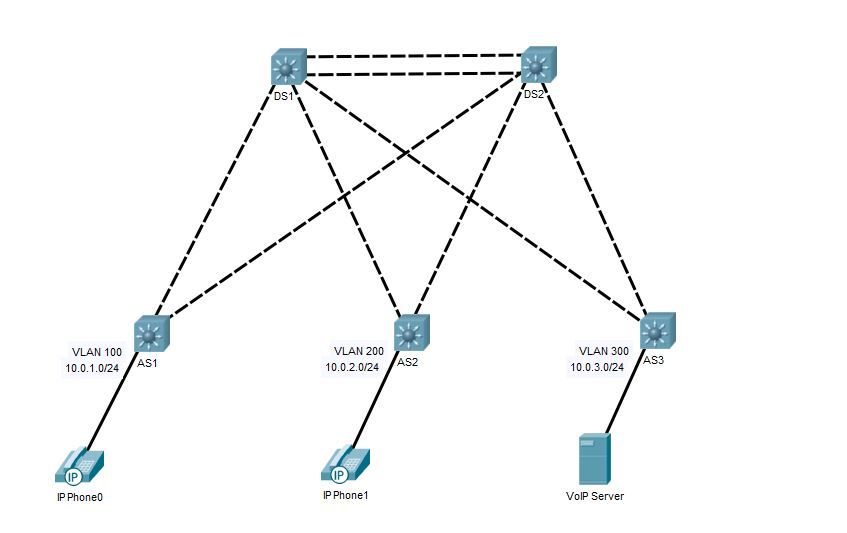
I'm currently studying for the CCNP Switch exam and am on the topic of local VLANs. It is recommended by Cisco to not span a VLAN across multiple switches but rather create local VLANs per access-switch/IDF. I understand how this helps with convergence and loop prevention, using L3 routing instead of relying on STP for redundant links, but it seems like it would be a nightmare for VoIP. I must be missing something.
So phones in different areas around the building (wherever your access layer switches are), would be on different subnets. Not only that, they would be on subnets different than the VoIP server itself. Is this really preferred over having all phones on their own (same) VLAN? The same applies to WAPs and a WLC. The WAPs around the building would be on different subnets from each other AND the controller. I just want to make sure I am understanding this correctly.
Solved! Go to Solution.
- Labels:
-
LAN Switching
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-21-2019 08:17 AM
Yes, for the data traffic. A route link loss, though, is generally a control plane (i.e. software) function. Routed ECMP "fastness" often has most to do with software being notified of an interface drop. If that doesn't happen, by default, half your traffic might be routed to a "black hole" until the IGP times detects the path failure (often for multiple seconds).
BTW, for L2 with stack's or VSS or VPC, their Etherchannel link drop detection was invisible to STP, which incidentally if using a "fast" STP variant, on a small L2 topology, is often quick enough that a "hit" might not drop a VoIP connection.
Network designs often entails trade-offs in cost vs. potential impact of a hardware failure. For VoIP, if you don't break the connection for more than a quarter to half second, that's often "good enough".
Also BTW, there other considerations when choosing L2 vs. L3, like when dealing with multicast, which raises its own set of issues when dealing with link failure.
Cisco recommendations tend to be both "safe" and "forward looking", but they can be expensive and possibly (for your company) never, or at least in the near future, not really needed. I.e. don't get hung up on reading a design guide that you "must" do what Cisco suggests. Do, though, study what they suggest and be prepared to adopt it, if it's really beneficial to your company's goals. Also understand, there's a difference of what you need to know to pass a Cisco certification exam, what what's really necessary for your company's network.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-21-2019 06:24 AM
Use 1 vlan for voice ours is a /22 or /23 , spread across whole layer 2 network of user access switches, then we route at layer3 on the distribution and core switches , but all user access is layer 2 , core-dist -user
then plan and manage your STP correctly with correct protections in place and understand how it will work when a link or switch fails , that will minimize any outage
the layer 3 vlan for the voice would be on the distribution switch and that vlan just trunked to all user access where the phones would be connected 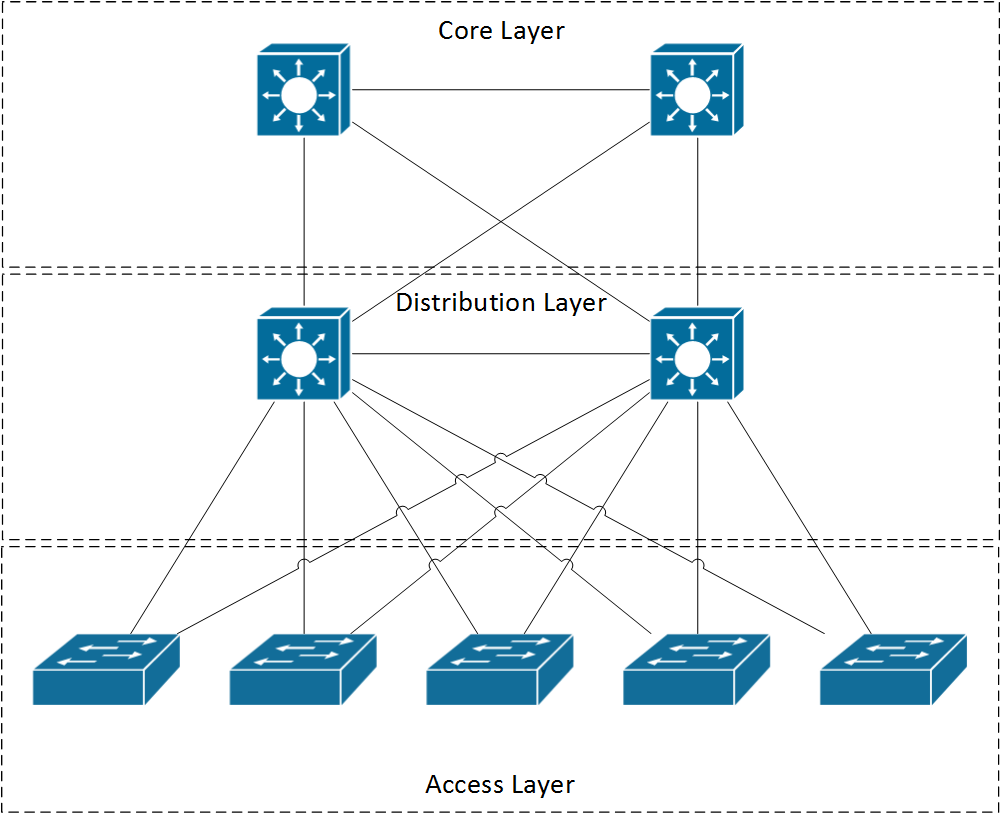
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-21-2019 06:30 AM
If you were to use a collapsed core like your picture then it would be the same only the L3vlan would be on the core as there's no dist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-21-2019 06:38 AM
The setup you describe is what I am familiar with, and it works great. My question was more so geared towards the fact that Cisco would RATHER you have L3 routing between distribution and access switches, limiting VLANs to the access layer switch, as I pictured in my original post.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-21-2019 06:45 AM
I only went through this a year ago with Cisco and there professional services companies and we broke our collapsed core of VSS 6509Es and put in a dist setup of 4500x VSS to mtch our other regions
Its all about cost and budget though but if you can afford it the campus design docs recommend 3 tier setup for that reason of L2 and L3 traffic
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-21-2019 06:59 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-21-2019 07:07 AM
Yes the majority of switches used for the access layer today are L2 switches. It expensive to replace all of these with L3 switches but best-practices says if you have the money, it is better to replace these with L3 switches and do routing between distribution and access layers. Routing failover is quicker than STP. This would require local VLANs that do not leave the access layer switch, which again Cisco recommends, if possible. It just seems like that would create problems at the access layer for things like VoIP and wireless.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-21-2019 07:25 AM
could you provide the documentation your seeing this in please where it states to use l3 at access layer
From campus design docs
VLAN Trunk Design Recommendations
In a typical campus network design, a single access switch is deployed with more than a single VLAN, such as a data VLAN and a voice VLAN. The Layer 2 network connection between the distribution and access device is a trunk interface. A VLAN tag is added to maintain logical separation between VLANs across the trunk.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-21-2019 07:39 AM
That actually depends on the platform. Many platforms, like L3 switches, support hardware supported routing at about the same speed as hardware based switching. The L3 hardware is more complex which is one reason L3 switches are more expensive.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-21-2019 07:47 AM - edited 01-21-2019 07:48 AM
Most (if not all) L3 switches route using hardware, not software. This is why it is preferred over STP. You would be doing equal cost load balancing between the two paths so there would virtually be no fail over.
Refer to this documentation regarding routed access design.
https://www.cisco.com/c/dam/en/us/td/docs/nsite/campus/ha_campus_routed_access_cvd_ag.pdf
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-21-2019 08:17 AM
Yes, for the data traffic. A route link loss, though, is generally a control plane (i.e. software) function. Routed ECMP "fastness" often has most to do with software being notified of an interface drop. If that doesn't happen, by default, half your traffic might be routed to a "black hole" until the IGP times detects the path failure (often for multiple seconds).
BTW, for L2 with stack's or VSS or VPC, their Etherchannel link drop detection was invisible to STP, which incidentally if using a "fast" STP variant, on a small L2 topology, is often quick enough that a "hit" might not drop a VoIP connection.
Network designs often entails trade-offs in cost vs. potential impact of a hardware failure. For VoIP, if you don't break the connection for more than a quarter to half second, that's often "good enough".
Also BTW, there other considerations when choosing L2 vs. L3, like when dealing with multicast, which raises its own set of issues when dealing with link failure.
Cisco recommendations tend to be both "safe" and "forward looking", but they can be expensive and possibly (for your company) never, or at least in the near future, not really needed. I.e. don't get hung up on reading a design guide that you "must" do what Cisco suggests. Do, though, study what they suggest and be prepared to adopt it, if it's really beneficial to your company's goals. Also understand, there's a difference of what you need to know to pass a Cisco certification exam, what what's really necessary for your company's network.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-21-2019 07:50 AM
They do, but also remember they are a hardware sales company. Personally, I believe the benefits of L3 on the edge device is often oversold except in a few special cases.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-21-2019 07:47 AM - edited 01-21-2019 07:53 AM
". . . using L3 routing . . . but it seems like it would be a nightmare for VoIP. "
Why do you think/believe that?
I recently worked for company that had a 100,000 employees (most in USA, but some international too), using VoIP. We routed VoIP like any other traffic. At the edge, we had L2 or L3, although when using a L2 edge, we did avoid spanning VLANs beyond the distribution L3 switch(es) trunk(s) that controlled them.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-21-2019 07:52 AM
Honestly...I don't know haha! I guess I've just only seen networks where there was a single VLAN for voice and one for data per location. The idea of a routed access layer and local VLANs is just a very new concept to me. The same goes for wireless. I guess APs are fine to communicate to a controller on another VLAN, it just goes against what I've seen! I've come to the conclusion that I just need to lab this up and see it function, ha!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-21-2019 08:00 AM - edited 01-22-2019 08:32 AM
Ah, well for branches where we had less than 200 some hosts, generally we only had a /24 for data and one for VoIP. "Branches" with hundreds to thousands of employees, had a corresponding number of /24s.
You mention wireless, we used controllers. For controlled WLANs, as they don't have the broadcast issues of wired LANs, often had a single functional/logical LAN for a whole region (possible using something like a /20). The WLAPs physically had a foot in whatever local data VLAN they were physically connected to. Traffic between wireless hosts (rare) would be on the controller. Traffic between wireless hosts and wired hosts would be to/from controller. (Of course, traffic between controller and WLAPs was [routed] tunnel traffic.)
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: