- Cisco Community
- Technology and Support
- Networking
- Switching
- Managed switch. Can this be done?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-12-2012 05:54 PM - edited 03-07-2019 09:26 AM
I have a SG-300-20 Managed switch. I attached a picture of what I want to do. Is this possible to do? How would I go about doing it?
Thanks
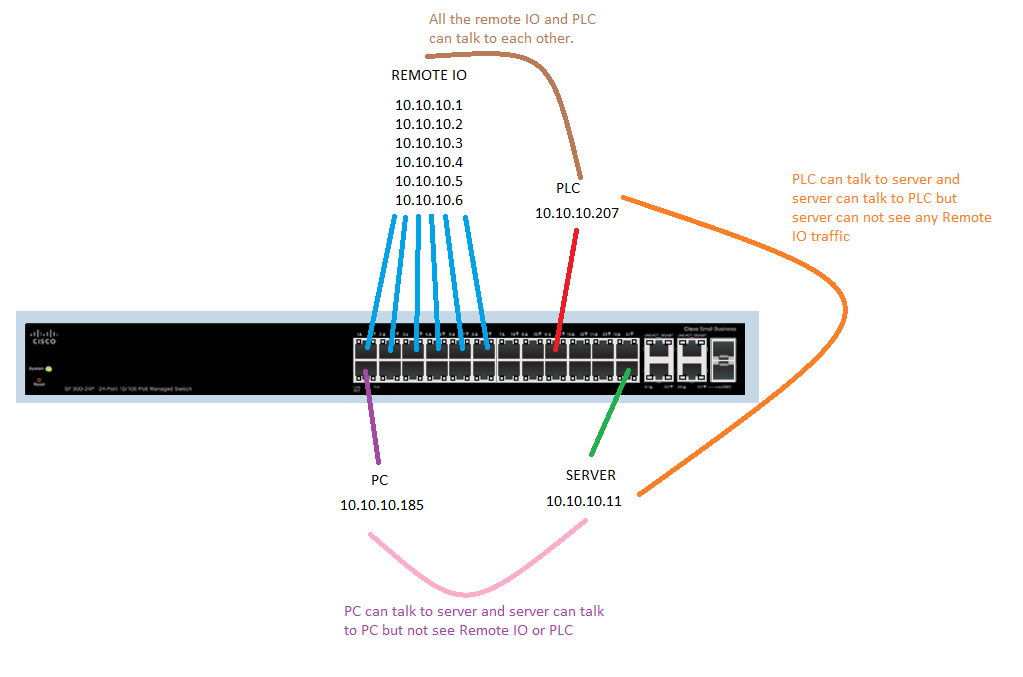
Solved! Go to Solution.
- Labels:
-
Other Switching
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-15-2012 06:52 AM
You can use port acl's to accomplish this although your model switch may or may not support this as I believe that is a lower end cisco switch. Check the documentation. . If you are dealing with a large amount of ports it becomes kind of pain implementing all those but realistically in your case in that drawing i would think you just need port acl's on the pc and server ports allowing access to each other , everything else is denied.
Port ACLs
You can also apply ACLs to Layer 2 interfaces on a switch. Port ACLs are supported on physical interfaces and EtherChannel interfaces.
The following access lists are supported on Layer 2 interfaces:
•![]() Standard IP access lists using source addresses
Standard IP access lists using source addresses
•![]() Extended IP access lists using source and destination addresses and optional protocol type information
Extended IP access lists using source and destination addresses and optional protocol type information
•![]() MAC extended access lists using source and destination MAC addresses and optional protocol type information
MAC extended access lists using source and destination MAC addresses and optional protocol type information
As with router ACLs, the switch examines ACLs associated with features configured on a given interface and permits or denies packet forwarding based on how the packet matches the entries in the ACL. In the example in Figure 37-1, if all workstations were in the same VLAN, ACLs applied at the Layer 2 input would allow Host A to access the Human Resources network, but prevent Host B from accessing the same network.
When you apply a port ACL to a trunk port, the ACL filters traffic on all VLANs present on the trunk port. When you apply a port ACL to a port with voice VLAN, the ACL filters traffic on both data and voice VLANs.
With port ACLs, you can filter IP traffic by using IP access lists and non-IP traffic by using MAC addresses. You can filter both IP and non-IP traffic on the same Layer 2 interface by applying both an IP access list and a MAC access list to the interface.

Note ![]() You cannot apply more than one IP access list and one MAC access list to a Layer 2 interface. If an IP access list or MAC access list is already configured on a Layer 2 interface and you apply a new IP access list or MAC access list to the interface, the new ACL replaces the previously configured one.
You cannot apply more than one IP access list and one MAC access list to a Layer 2 interface. If an IP access list or MAC access list is already configured on a Layer 2 interface and you apply a new IP access list or MAC access list to the interface, the new ACL replaces the previously configured one.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-13-2012 03:15 AM
Hi,
With my very limited knowledge , I think what you trying to do is very much possible.
Put each of these groups into seperate VLANs and configure Access list , configure Access group in interface VLANs and bind them according to your traffic requirement. But I am not sure if it 's possible in SMB Switches. I have a SMB SF300-24P in the infrastructure , I will check and get back to you on that !
Anup
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-13-2012 03:21 AM
I have just checked and there are ACL /ACE configurations available by which you can accomplish this
Please refer to this thread on the community which will sure help you in understanding how it's done.
https://supportforums.cisco.com/thread/2152247
Regards,
Anup
Anup
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-14-2012 02:12 AM
Hi,
all the devices seem to be in the same subnet?
In that case, Private VLAN feature might be a solution for you?
See
You need to check if supported by your switch, but according to
it seems so.
HTH,
Milan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-14-2012 07:05 AM
Hey,
like I see the switch supports
PVE (also known as protected ports) provides Layer 2 isolation between devices in the same VLAN, supports multiple uplinks
maybe you should take a closer look at this features.
Otherwise the ideas above are also fine..you could also create 4 subnetworks and work with ACL. I'm not sure if the switch supports VACLs and you can work with only one VLAN.
regards,
Sebastian
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-15-2012 06:52 AM
You can use port acl's to accomplish this although your model switch may or may not support this as I believe that is a lower end cisco switch. Check the documentation. . If you are dealing with a large amount of ports it becomes kind of pain implementing all those but realistically in your case in that drawing i would think you just need port acl's on the pc and server ports allowing access to each other , everything else is denied.
Port ACLs
You can also apply ACLs to Layer 2 interfaces on a switch. Port ACLs are supported on physical interfaces and EtherChannel interfaces.
The following access lists are supported on Layer 2 interfaces:
•![]() Standard IP access lists using source addresses
Standard IP access lists using source addresses
•![]() Extended IP access lists using source and destination addresses and optional protocol type information
Extended IP access lists using source and destination addresses and optional protocol type information
•![]() MAC extended access lists using source and destination MAC addresses and optional protocol type information
MAC extended access lists using source and destination MAC addresses and optional protocol type information
As with router ACLs, the switch examines ACLs associated with features configured on a given interface and permits or denies packet forwarding based on how the packet matches the entries in the ACL. In the example in Figure 37-1, if all workstations were in the same VLAN, ACLs applied at the Layer 2 input would allow Host A to access the Human Resources network, but prevent Host B from accessing the same network.
When you apply a port ACL to a trunk port, the ACL filters traffic on all VLANs present on the trunk port. When you apply a port ACL to a port with voice VLAN, the ACL filters traffic on both data and voice VLANs.
With port ACLs, you can filter IP traffic by using IP access lists and non-IP traffic by using MAC addresses. You can filter both IP and non-IP traffic on the same Layer 2 interface by applying both an IP access list and a MAC access list to the interface.

Note ![]() You cannot apply more than one IP access list and one MAC access list to a Layer 2 interface. If an IP access list or MAC access list is already configured on a Layer 2 interface and you apply a new IP access list or MAC access list to the interface, the new ACL replaces the previously configured one.
You cannot apply more than one IP access list and one MAC access list to a Layer 2 interface. If an IP access list or MAC access list is already configured on a Layer 2 interface and you apply a new IP access list or MAC access list to the interface, the new ACL replaces the previously configured one.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-22-2012 12:41 PM
ACL's worked great. Thanks for the info.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide